fortify your
attack surface
On Demand Product Tour Free Trial










Analyzing
Third Party
Exposures
Explore Our Portfolio

Cyber RiskProfiler
Cyber RiskProfiler’s state-of-the-art global bot network uses hacker-like techniques to gather open source intelligence, identify security threats before they impact your business and monitors third-party vendor risk in real-time.

Brand RiskProfiler
Brand RiskProfiler protects your digital reputation across the surface, deep and dark web. We scrape billions of pages every day, extract your brand mentions, perform sentiment analysis and logo abuse detection, and take down fake domains/apps

Enterprise RiskProfiler
Enterprise RiskProfiler provides unified open source and human intelligence data to understand an organization’s internet attack surface. Detecting security misconfigurations, threat intelligence and dark web monitoring help enterprises prevent breaches.

Vendor RiskProfiler
Orchestrate your third party vendor risk assessments with real time validation of questionnaire responses at scale. Vendor RiskProfiler complements Cyber RiskProfiler by providing an holistic view of Third Party vendors internal security controls.

Cloud Risk
Gain visibility and control over your cloud attack surface with Cloud RISK. Using advanced analytics and graph data models, identify assets, prioritize risks, and proactively mitigate threats to secure your cloud environment.

Explore Our Portfolio
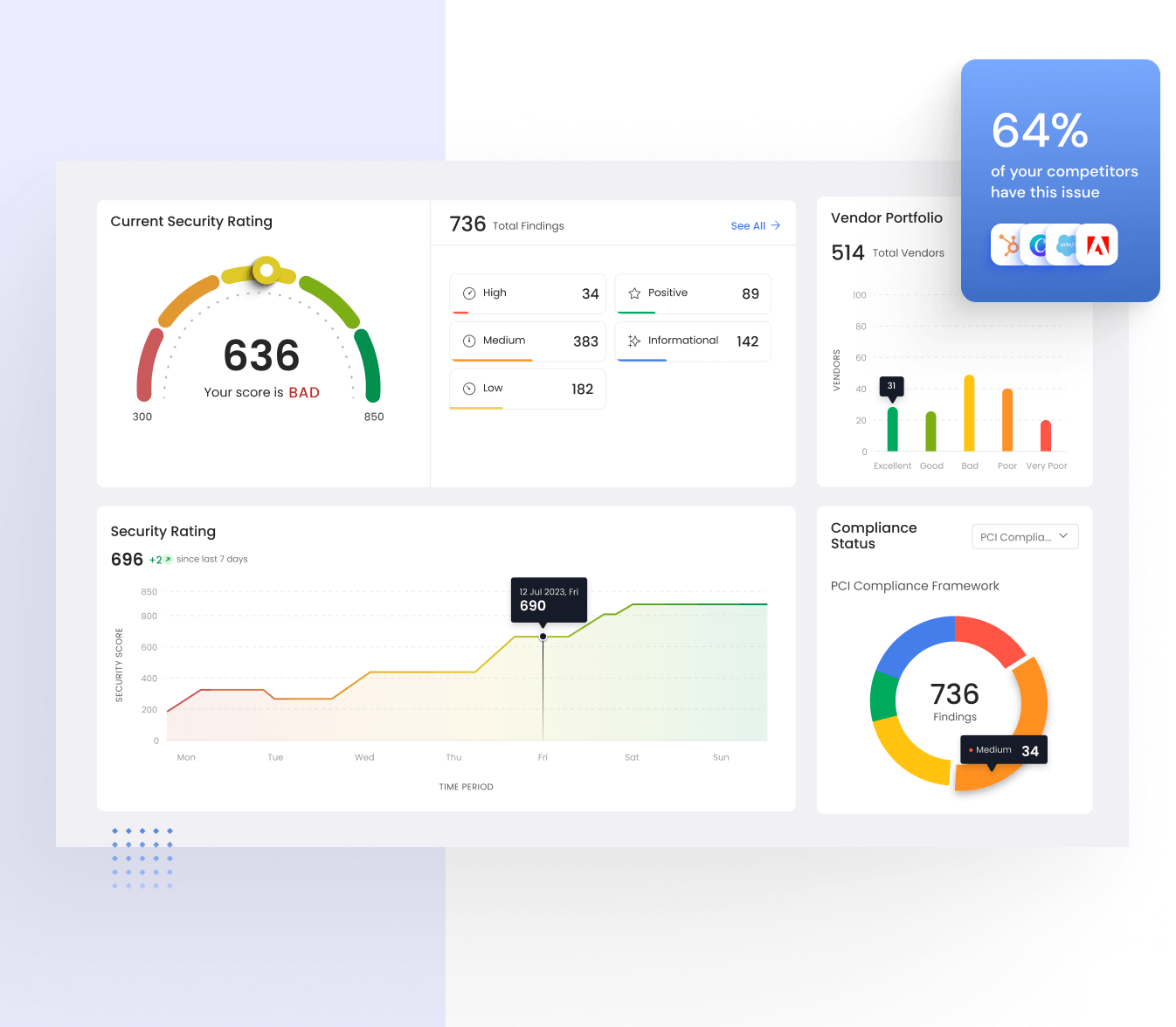
Continuous cybersecurity ratings with automated risk analysis.
Inadequate cybersecurity measures leave organizations vulnerable.
- Cyber Risk Ratings
- Third-Party Security Portfolio
- Centralized Issues Management
- Mergers & Acquisitions
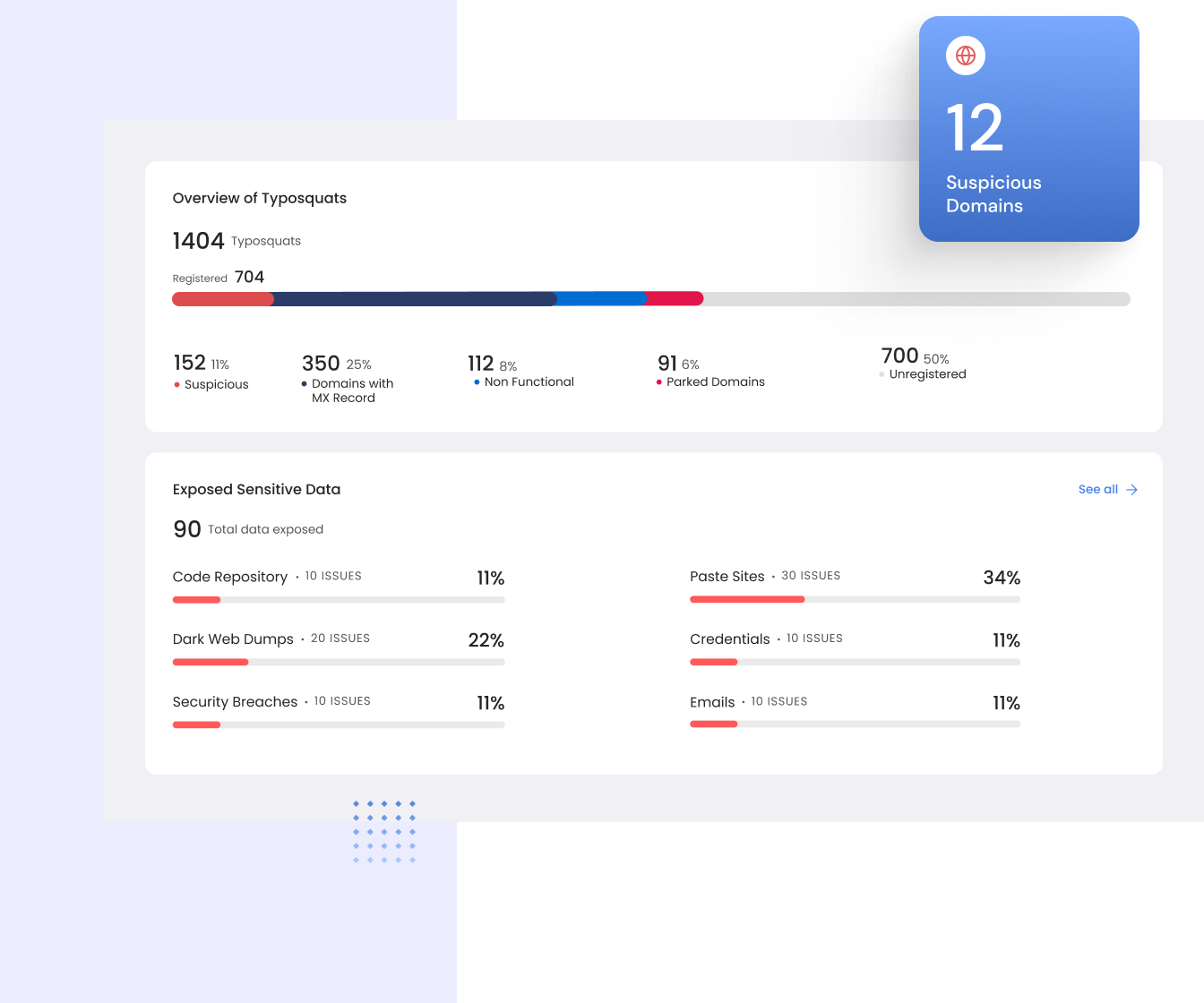
Identifying brand risks through proactive surface and dark web monitoring
Unidentified Digital Brand Risks: A Problem of Limited Visibility
- Takedown as a Service
- Fake Apps Detection
- Logo Abuse
- Digital Presence Feed
Streamlined questionnaires for real time third-party risk assessments.
Challenges of Inefficient Third-Party Risk Assessments
- Standard Questionnaires
- Real-time Validation
- Accurate Assessments
- Fast, collaborative assessments
Automated reconnaissance for uncovering digital shadow risks.
The Challenge of Visibility and Control
- External Assets Discovery
- Assets Contextualization
- Attack Surface Reduction
- Passive Phishing Detection
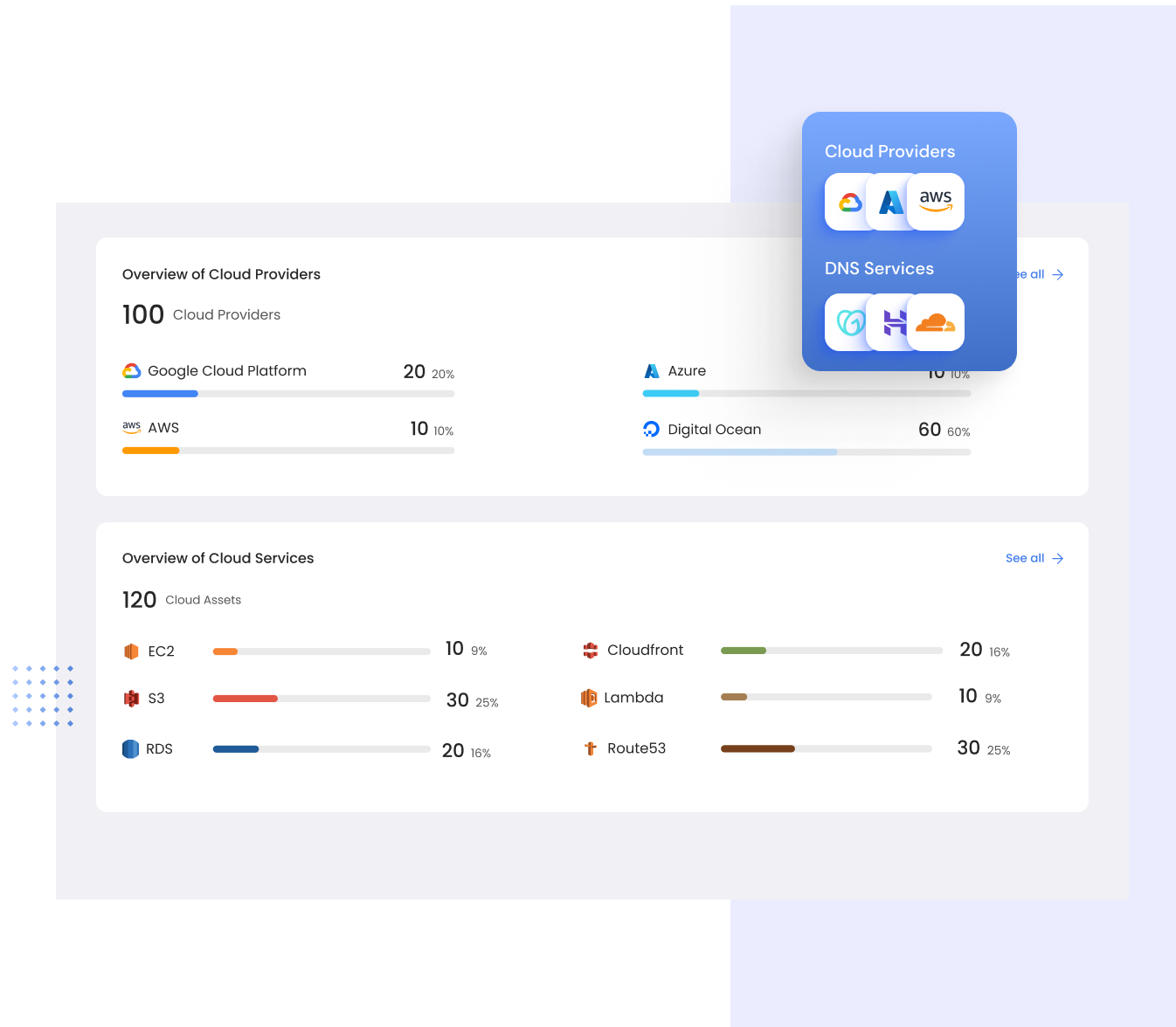
Securing Your Cloud External Assets
Shadow Assets in the Cloud
- Supports all Major Cloud Providers
- Cleaner DNS Records
- Cloud Attack Surface Management
- One Click Onboarding
Monitor all your cloud environments
Seamlessly integrate RiskProfiler with your cloud environments using our cloud connectors. Achieve real-time visibility and continuous monitoring of your external cloud attack surface, enhancing your cloud security posture.
- Amazon Web Services
- Google Cloud
- Microsoft Azure
- Digital Ocean
- Cloudflare
- Oracle Cloud

Automated Vendor Risk Management
Enhance your vendor security assessment process to gain a holistic understanding of your vendors’ security status.
- Advanced Security Ratings
- Vendor Portfolio
- Custom Risk Ratings
- Compliance Mapping
- Peer Benchmarking
- Fourth Party Risk Management
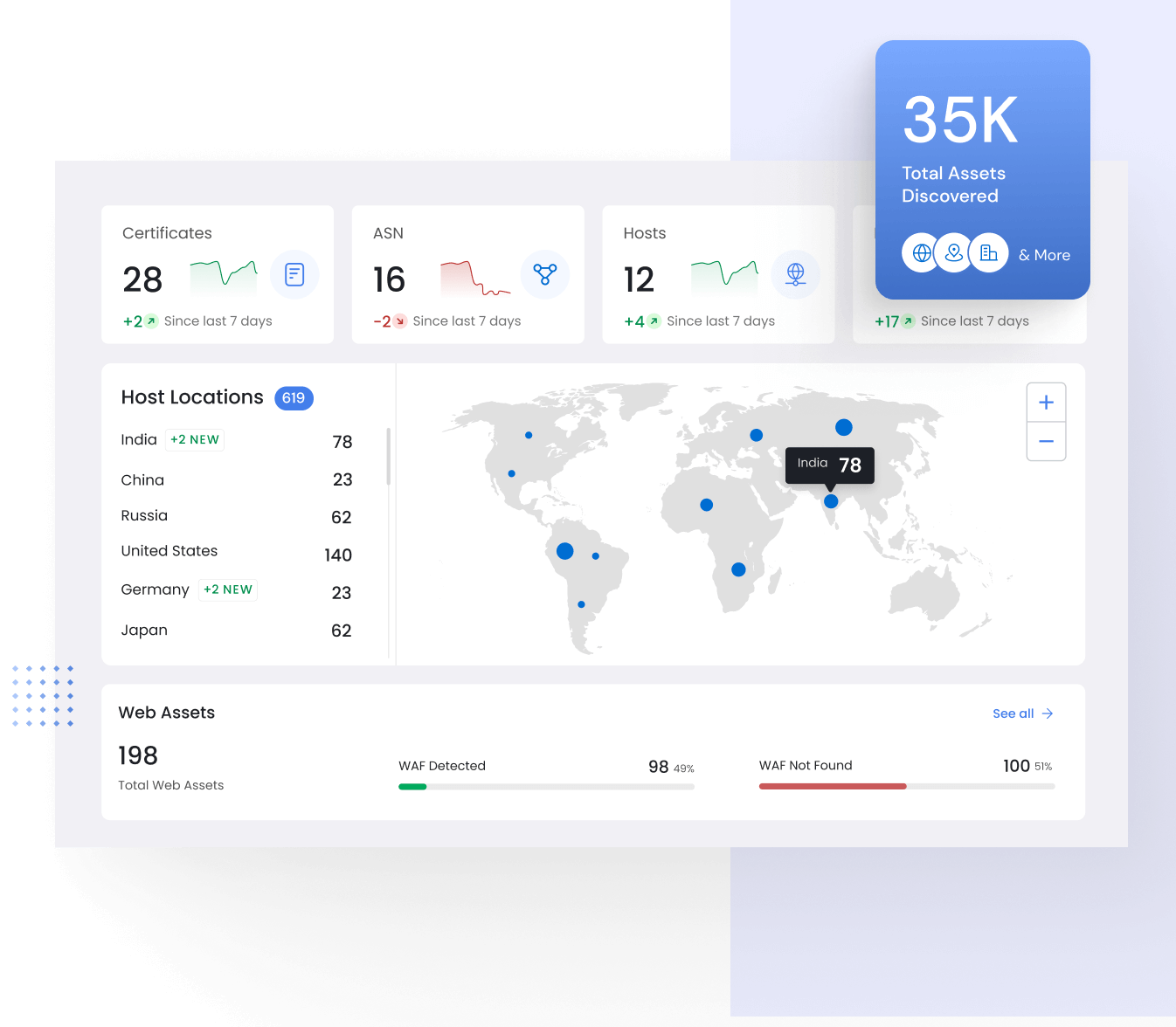
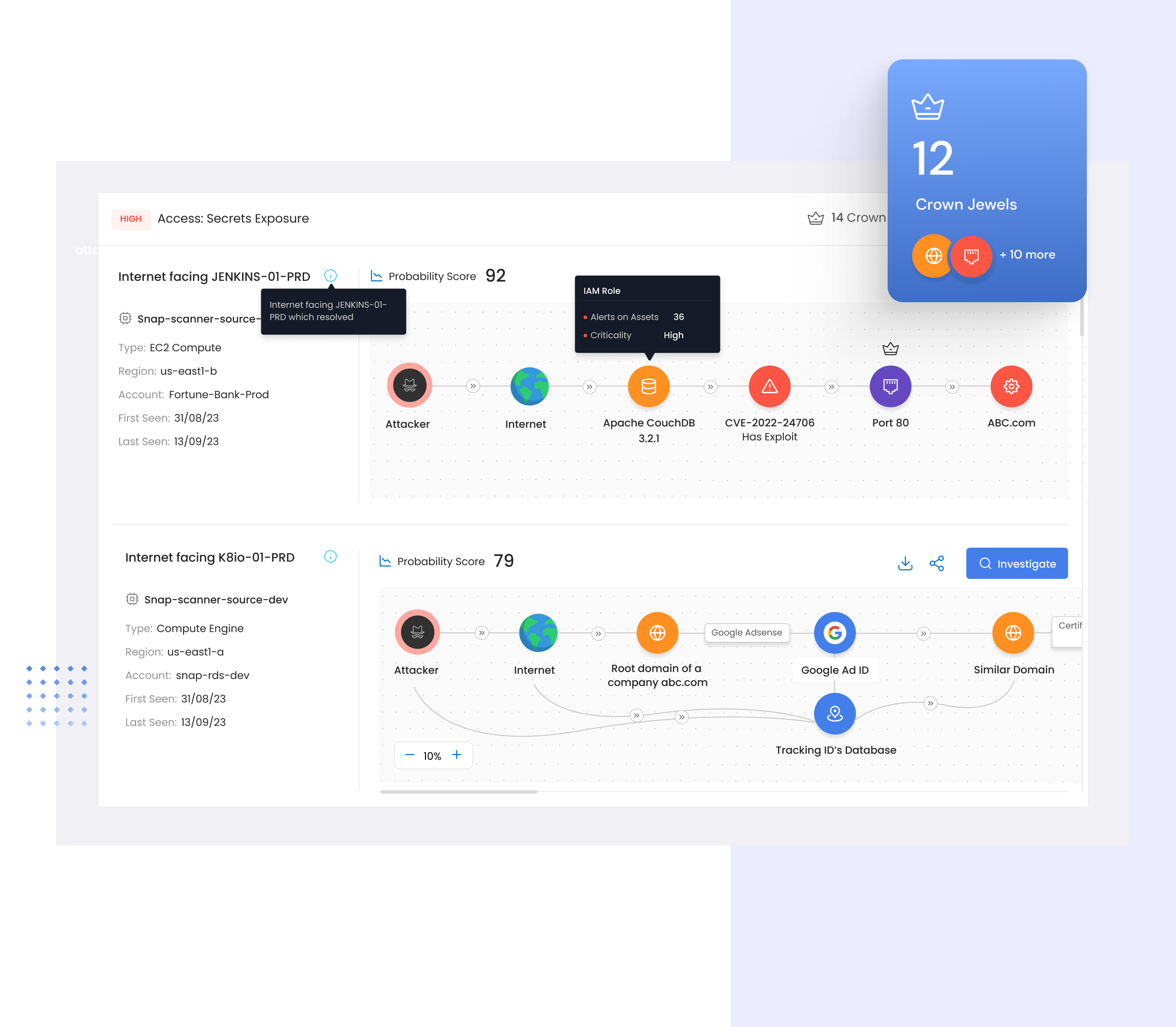
See Your external attack surface like a hacker
Amidst digital transformation’s rapid expansion, Recon RISK offers continuous visibility into your organization’s digital infrastructure, aiding in the identification and management of potential security risks and vulnerabilities.
- External Assets Inventory
- DNS Registrar Connectors
- Attack Path Analysis
- Recon Security Graph
- Risks Register
- Email Breach Monitoring
Bulletproof Your Brand Against External Threats
RiskProfiler equips you with actionable insights to preemptively tackle threats to your brand and stakeholders. Our real-time monitoring keeps you ahead of potential risks, enabling swift counteractions.
- Domain Take Down as a Service
- Monitor for Domain Typosquats
- Fake Mobile Apps Detection
- Detect Logo Impersonations
- Detect Phishing Sites
- Dark Web Data Leaks
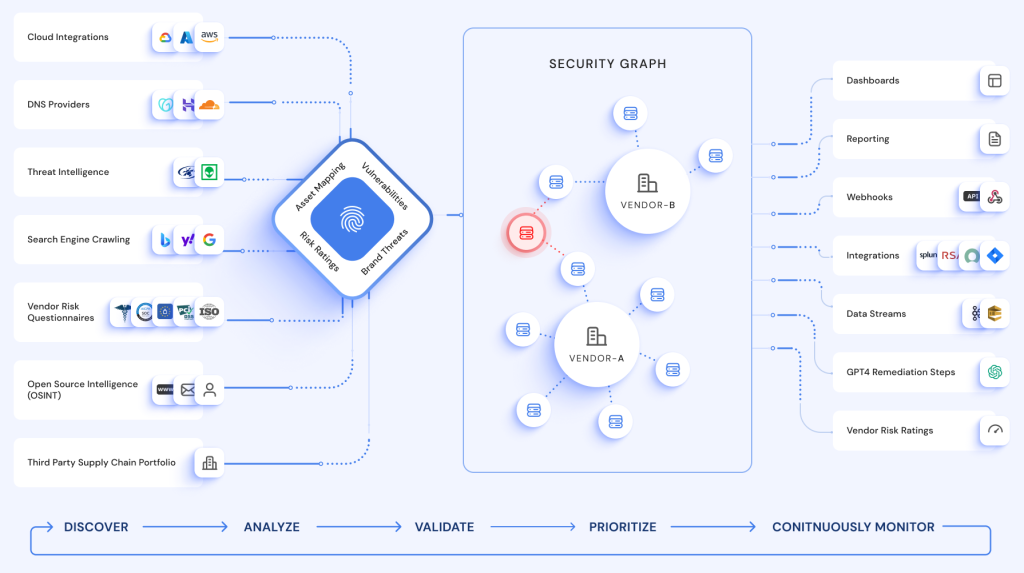
Visualize Context based High Risk attack paths
RiskProfiler combines all of the data about your external facing assets, third-party vendors, vendor risk assessment results, and brand risks into a single graph, making it possible to correlate related issues that create attack paths.
- Single Graph for Assets & Risks
- Shadow External Assets in Cloud
- Context aware Attack Paths
- Visualize Assets and their Risks
- Up-To-Date Real time inventory
- Better Risk Prioritization
See RiskProfiler in action.
Schedule time with our technical experts for a product deep dive.
WHAT OUR USERS SAY ABOUT US

With its capacity to amalgamate a plethora of tools into one comprehensive package, RiskProfiler offers unparalleled potential in a singular solution. It’s more than a tool, it’s a game-changer.

Edward M. Hinchey,
Sr. Director of IT & Security
RiskProfiler is not merely a tool, but a value proposition that considerably enhances the cybersecurity maturity of organizations as well as their supply chains. It’s a game-changer in the world of data security and risk management.
Matt Johnson,
CEO
Stretching the boundaries of typical cybersecurity solutions, RiskProfiler extends its protective shield well beyond organizational limits. The visibility it offers is a rare commodity in today’s cybersecurity landscape.
Shantanoo Govilkar,
Vice President
RiskProfiler stands tall in the cybersecurity market, thanks to its competitive pricing and feature-rich interface. Coupled with its user-friendly design and remarkable visibility capabilities, it sets a high bar in cybersecurity solutions.
Casey Corcoran,
CISOLatest From RiskProfiler's Blog
We hope the previous blogs around AWS security series offered valuable insights into the latest releases of AWS Security features/services. Ending the series, Part-6 on features around Generative AI & ML in AWS that were released in the last quarter. Gaining technological advantage keeps your business at scale, making it more agile. To the inconsistent market […]
We hope the previous blogs around AWS security series offered valuable insights into the latest releases of AWS Security features/services. Continuing the series, Part-5 on features around Incident Response in AWS that were released in the last quarter. To bring a sophisticated approach to your security standards in the increased threat vectors, AWS has introduced a […]
We hope the last 3 blogs around AWS security series offered valuable insights into the latest releases of AWS Security features/services, particularly in the IAM domain, detective controls and Infrastructure Protection . Continuing the series, Part-4 around data Protection in AWS that were released in the last quarter.As part of data protection protocols, Amazon has […]