Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


CloudFrontier - An Open Source Tool for Internet Attack Surface Mapping
CloudFrontier - An Open Source Tool for Internet Attack Surface Mapping
They bring to you a host of beautifully created infographics that contain the latest digital marketing.
Read Time
7 min read
Posted On
Mar 29, 2023
Social Media
CloudFrontier is an open-source cloud security tool that enables you to identify and inventory your web-facing assets and map your organization’s multi-cloud internet attack surface. The assets discovered can then be scanned for security vulnerabilities against a set of predefined rules.
With an increasing number of organizations adopting cloud-hosted applications for all kinds of business functions, cloud security is now a bigger concern than ever before. It is essential for companies across industry verticals to choose their SaaS, PaaS and IaaS applications carefully, and make sure these are securely configured.
While cloud-hosted software is quick and easy to install and use, and is designed to make a range of tasks easier for employees, it can also expose an organization to a number of new security risks. Because cloud apps are not a part of a company’s traditional IT environment, and run outside the on-premise network perimeter, controlling and monitoring them becomes tricky for the security team.
The first step towards securing cloud assets is to get complete visibility into them. Because cloud-hosted apps are so easy to install, employees often start using them without the knowledge of their IT department.
This introduces hidden attack vectors and security loopholes into an organization and provides easy access points to hackers. A growing number of data leaks are a result of completely preventable configuration errors like exposed AWS S3 buckets or unsecured Elasticsearch servers. In most such cases, if the IT department had known about these resources and set the right access controls, the breaches would never have happened. This is why visibility into internet-facing assets is so important.
More and more organizations are now leveraging automated solutions to discover their hidden cloud assets as a step towards strengthening their cybersecurity posture. CloudFrontier, which is available for free use on Github, is just such a tool.
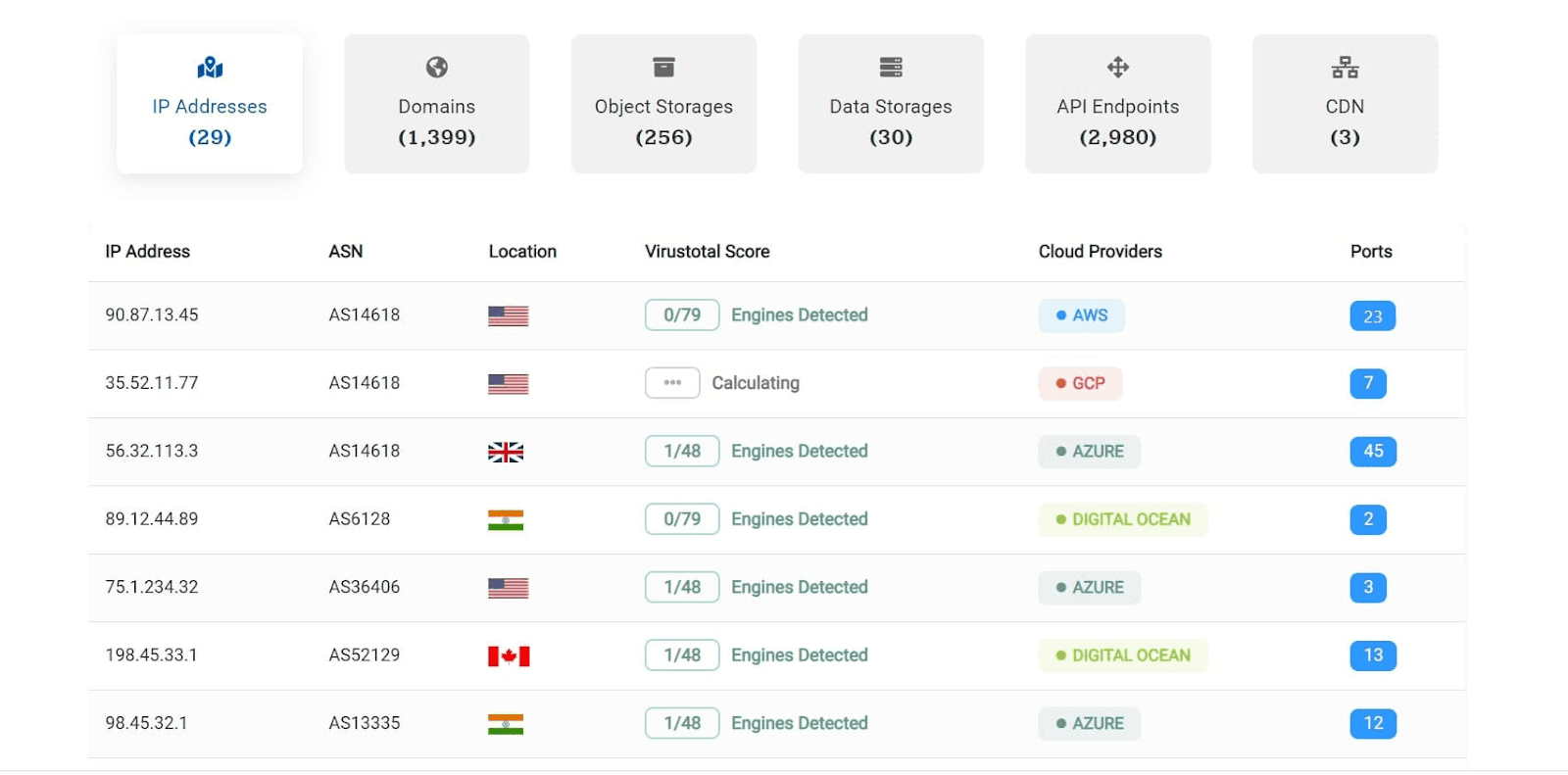
Any organization can plug the tool’s source code into its environment and run it to identify its cloud-based assets and internet attack surface. Businesses using AWS, Google Cloud, Azure or Digital Ocean can use the tool to get complete visibility into their cloud environments and track their public IPs, domains, API endpoints and cloud-hosted data. The assets discovered can then be scanned against a set of security rules to find, prioritize and remediate vulnerabilities.
With attacks on cloud-hosted applications rising each year and the knowledgebase and news coverage around such incidents becoming wider, organizations can no longer ignore cloud security. Data breaches can lead to heavy penalties, financial losses, shrinking of customer bases and, in the longer term, permanent damage to the reputations of the companies affected. If businesses do not secure their cloud environments, it is only a matter of time before malicious actors find an entry into these environments and exploit unpatched vulnerabilities and misconfigurations to cause lasting damage.
CloudFrontier can be a good starting point for any organization wanting to map its internet-facing assets in a multi-cloud environment. Discovering hidden cloud assets is critical to the success of modern security programs that cover cloud computing, and CloudFrontier allows companies to find their cloud assets at no cost. This initial internet inventory and visibility into the attack surface can form the basis of a comprehensive incident prevention plan, provide insight into the scale of cyber risks to an organization, and inform the direction it needs to take to effectively manage these risks.
CloudFrontier is an open-source cloud security tool that enables you to identify and inventory your web-facing assets and map your organization’s multi-cloud internet attack surface. The assets discovered can then be scanned for security vulnerabilities against a set of predefined rules.
With an increasing number of organizations adopting cloud-hosted applications for all kinds of business functions, cloud security is now a bigger concern than ever before. It is essential for companies across industry verticals to choose their SaaS, PaaS and IaaS applications carefully, and make sure these are securely configured.
While cloud-hosted software is quick and easy to install and use, and is designed to make a range of tasks easier for employees, it can also expose an organization to a number of new security risks. Because cloud apps are not a part of a company’s traditional IT environment, and run outside the on-premise network perimeter, controlling and monitoring them becomes tricky for the security team.
The first step towards securing cloud assets is to get complete visibility into them. Because cloud-hosted apps are so easy to install, employees often start using them without the knowledge of their IT department.
This introduces hidden attack vectors and security loopholes into an organization and provides easy access points to hackers. A growing number of data leaks are a result of completely preventable configuration errors like exposed AWS S3 buckets or unsecured Elasticsearch servers. In most such cases, if the IT department had known about these resources and set the right access controls, the breaches would never have happened. This is why visibility into internet-facing assets is so important.
More and more organizations are now leveraging automated solutions to discover their hidden cloud assets as a step towards strengthening their cybersecurity posture. CloudFrontier, which is available for free use on Github, is just such a tool.
Any organization can plug the tool’s source code into its environment and run it to identify its cloud-based assets and internet attack surface. Businesses using AWS, Google Cloud, Azure or Digital Ocean can use the tool to get complete visibility into their cloud environments and track their public IPs, domains, API endpoints and cloud-hosted data. The assets discovered can then be scanned against a set of security rules to find, prioritize and remediate vulnerabilities.

With attacks on cloud-hosted applications rising each year and the knowledgebase and news coverage around such incidents becoming wider, organizations can no longer ignore cloud security. Data breaches can lead to heavy penalties, financial losses, shrinking of customer bases and, in the longer term, permanent damage to the reputations of the companies affected. If businesses do not secure their cloud environments, it is only a matter of time before malicious actors find an entry into these environments and exploit unpatched vulnerabilities and misconfigurations to cause lasting damage.
CloudFrontier can be a good starting point for any organization wanting to map its internet-facing assets in a multi-cloud environment. Discovering hidden cloud assets is critical to the success of modern security programs that cover cloud computing, and CloudFrontier allows companies to find their cloud assets at no cost. This initial internet inventory and visibility into the attack surface can form the basis of a comprehensive incident prevention plan, provide insight into the scale of cyber risks to an organization, and inform the direction it needs to take to effectively manage these risks.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



