Agentic AI-powered Dark Web Monitoring
Deep & Dark Web Monitoring
Powered by KnyX Dark Web AI
Gain early visibility into leaked credentials, internal documents, cloud API keys and secrets across the dark web. KnyX Dark Web AI connects every exposure to linked assets, access points, and external risks, enabling decisive, informed remediation.

Trusted by 500+ enterprises
Recognized by
Industry Leaders

4.8/5

4.8 out of 5 stars

Best Ease of Use
2024
Proactive
Dark Web Intelligence
See Critical Exposures, In Real-Time
Gain continuous visibility into cybercriminal ecosystems with agentic AI-powered monitoring across the dark web, deep web, and underground forums.

Agentic Dark Web Intelligence
KnyX Dark Web AI aggregates dark web intelligence from stealer logs, underground forums, and hidden marketplaces. Automated clustering, enrichment, and prioritization identify exposures by exploitability, enabling focused and rapid mitigation.

AI - Correlated Threat Context
Connect leaked assets and creds to your threat signals, vendor risks, and external exposures using agentic AI analytics. Gain impact scores, timelines, and recommended actions with identity/asset mapping that help analysts contain threats early.

Integrated Threat Signals
Share high-priority exposure alerts in real-time via Slack, Jira, ServiceNow, etc. With intelligent prioritization and automated routing, urgent alerts reach the right teams instantly, accelerating response workflows and reducing the window of exploitation.

Why
Dark Web Monitoring
is Critical to Your Defense Strategy
KnyX Dark Web AI continuously analyzes the deep & dark web, detects malicious mentions, and prioritizes exposures based on impact, exploitability, and potential attack paths.
Identify Leaked Credentials before They’re Weaponized
KnyX Dark Web AI detects compromised credentials from combolists, stealer logs, and breach dumps, providing exploitability scoring and context so teams can quickly isolate high-risk accounts and prevent misuse or account takeover.
Detect Targeted Threats and Malicious Campaigns
Receive real-time alerts when your organization, executives, or assets appear in dark-web forums. KnyX Dark Web AI identifies targeting, recon activity, and potential targets before adversaries gain access or cause systematic damage.
Prevent Account Takeover
RiskProfiler uncovers compromised passwords, session tokens, and device fingerprints in dark web datasets, enabling teams to prevent account takeovers, session hijacking, and enforce MFA early for proactive threat preparedness.
Scale Threat Detection Across
Dark Web Data
Exposures on onion forums, Telegram groups, and malware ecosystems provide attackers with opportunity;
RiskProfiler turns those hidden signals into actionable defense.

Malware Hash & C2 Correlation
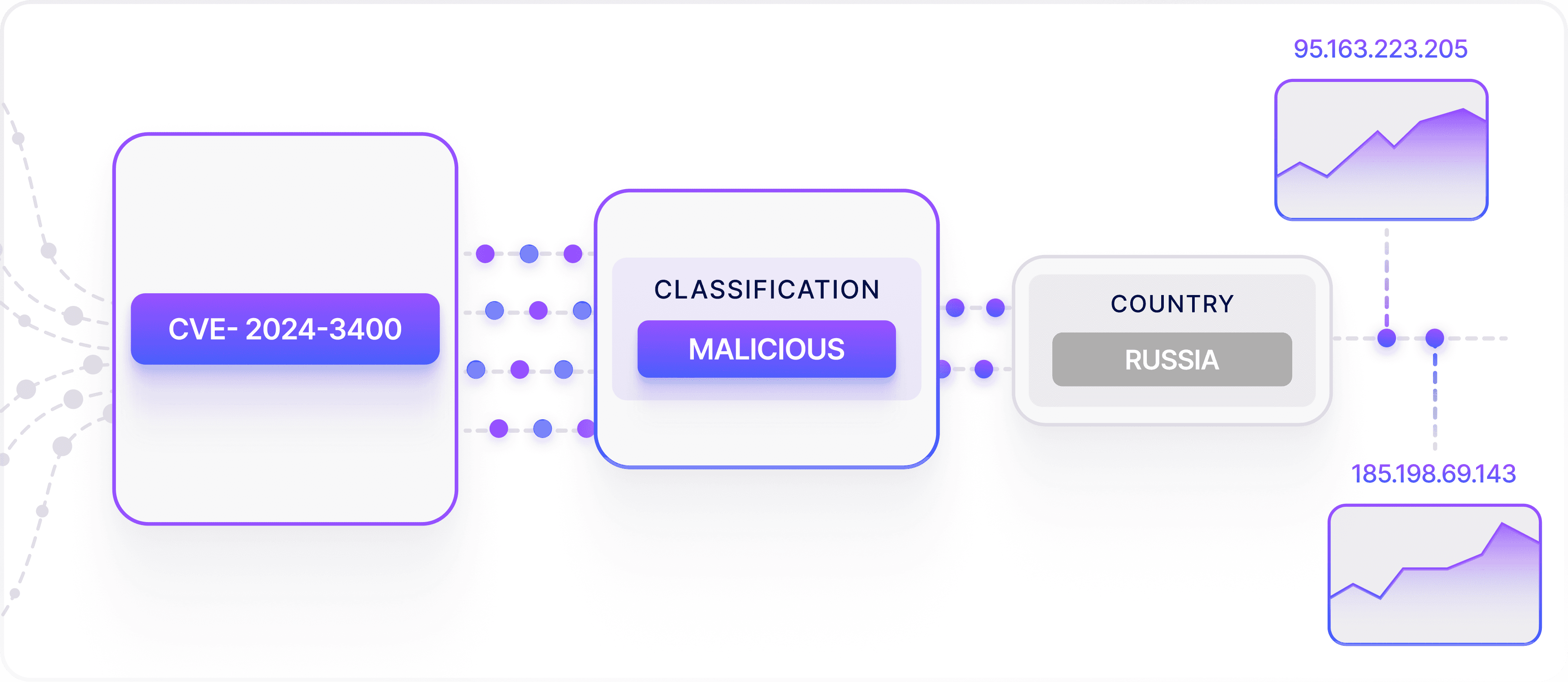
Identify malware hashes and C2 infrastructure tied to your leaked data. Correlate underground malware activity with internal telemetry for faster incident response.
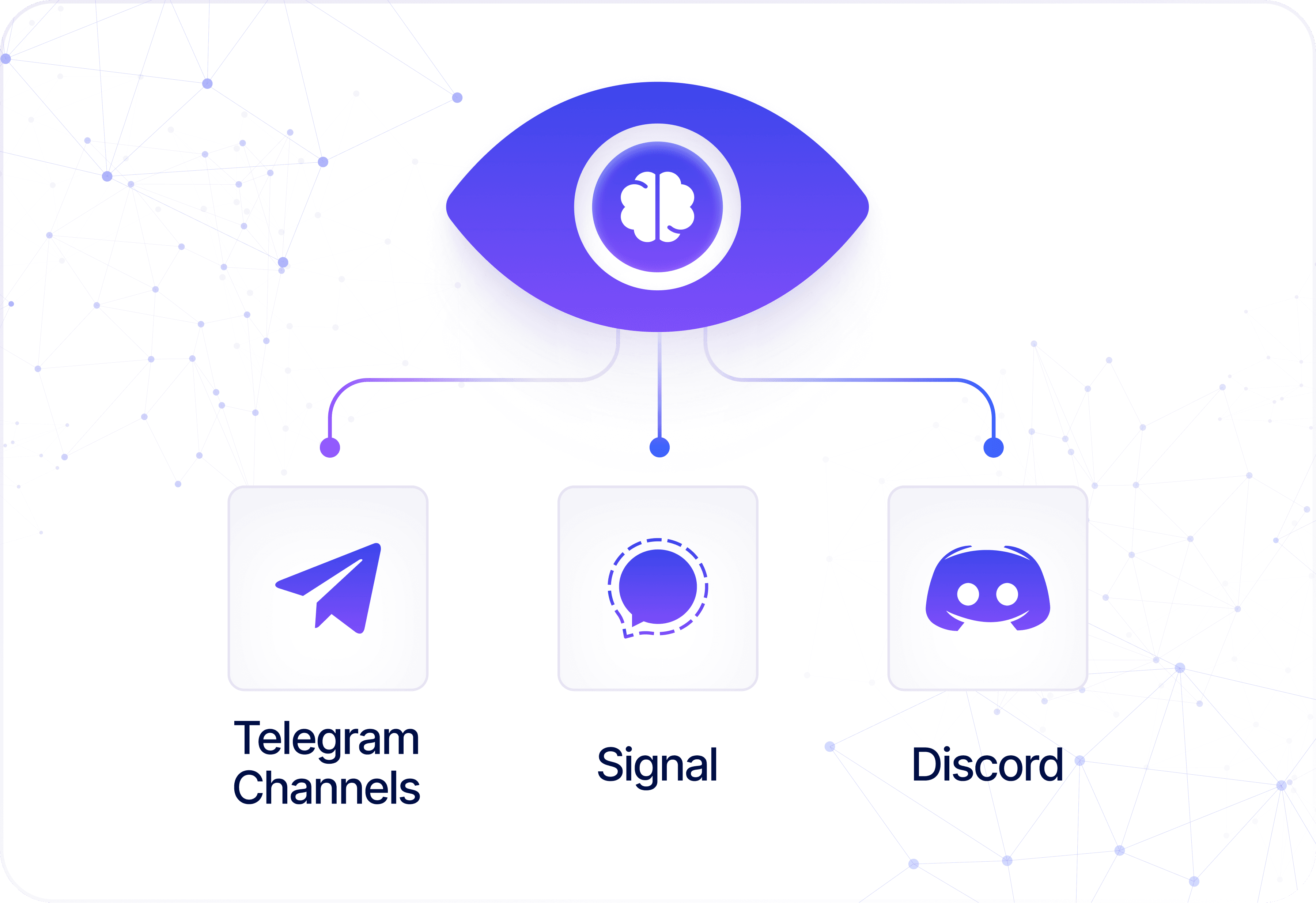
Threat Channel Surveillance
Gain continuous visibility into high-risk Telegram, Discord, and Signal channels. Detect mentions, stolen-data drops, and exploit chatter tied to your brand.

Stealer Log Intelligence
Extract compromised credentials, session tokens, and device fingerprints from RedLine, Vidar, Raccoon, Lumma, and other stealer malware logs affecting employees or vendors.
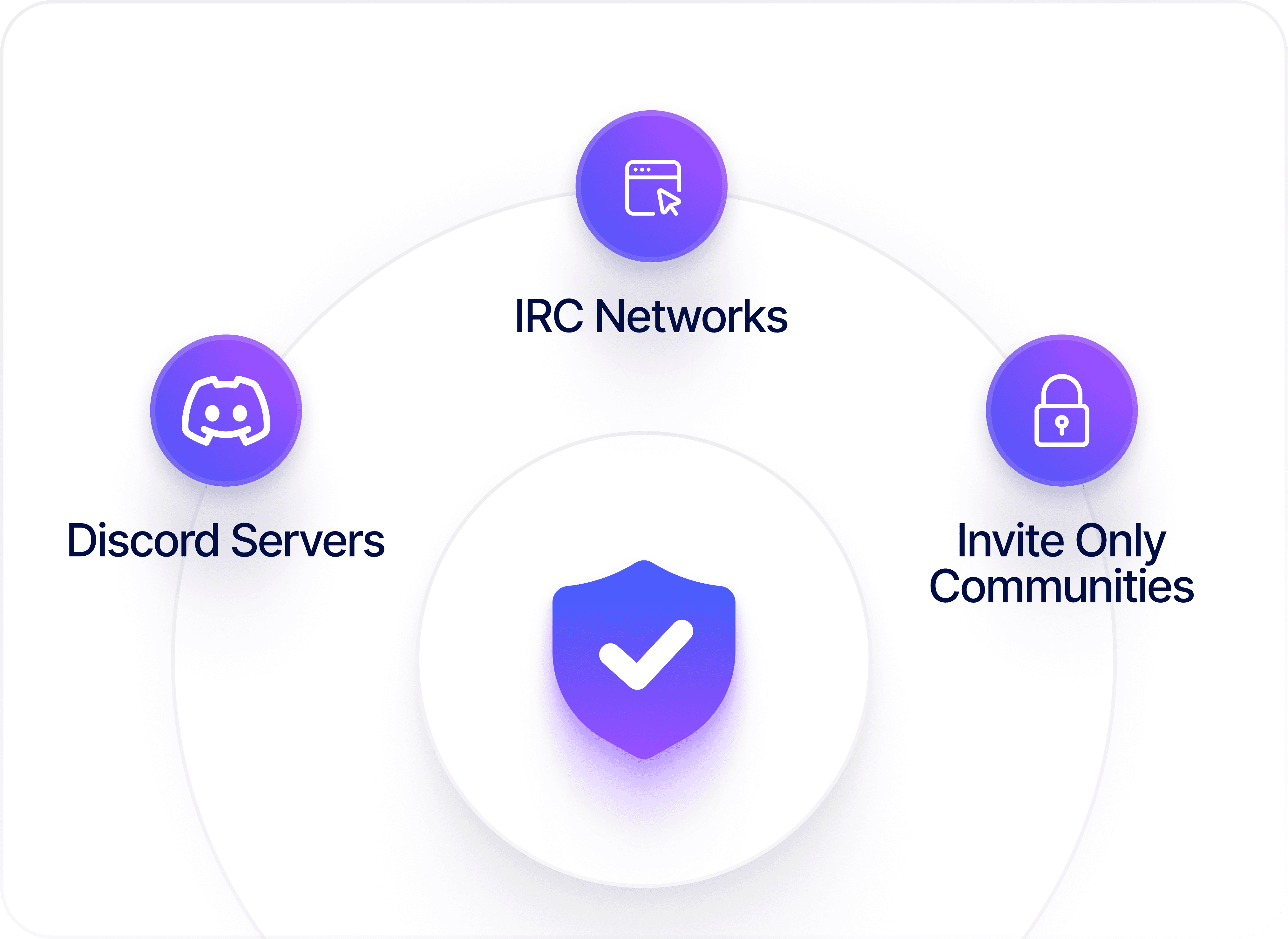
Encrypted Forum & IRC Monitoring
Collect intelligence from encrypted IRC networks, Discord servers, and invite-only communities where attackers trade exploits and breached data.
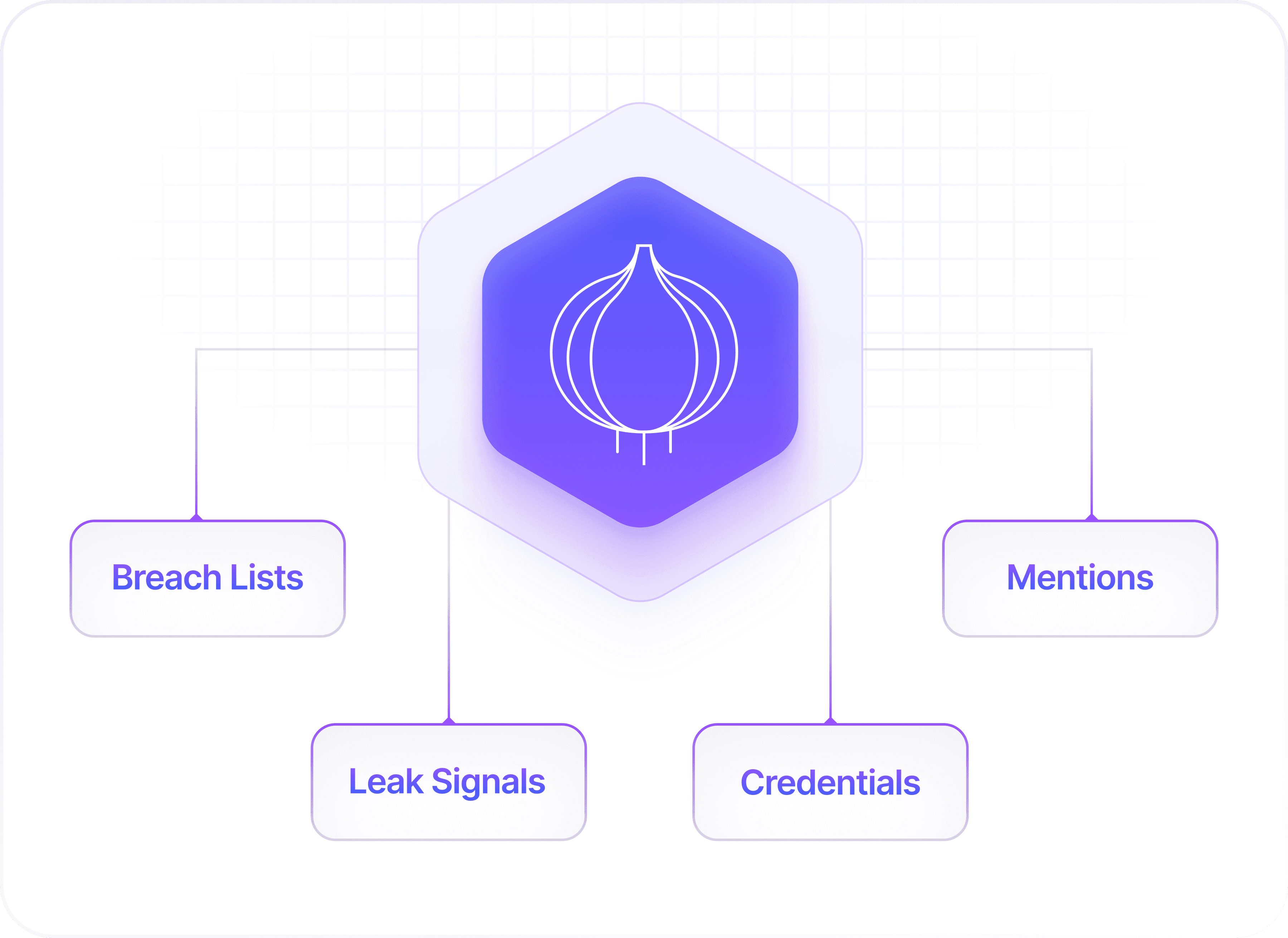
TOR & Onion Service Monitoring
KnyX Dark Web AI maps activities on TOR and onion to your footprint, surfacing exposed data and threat actor signals in real-time.
Integrated
Dark Web Risk
Exposure Visibility
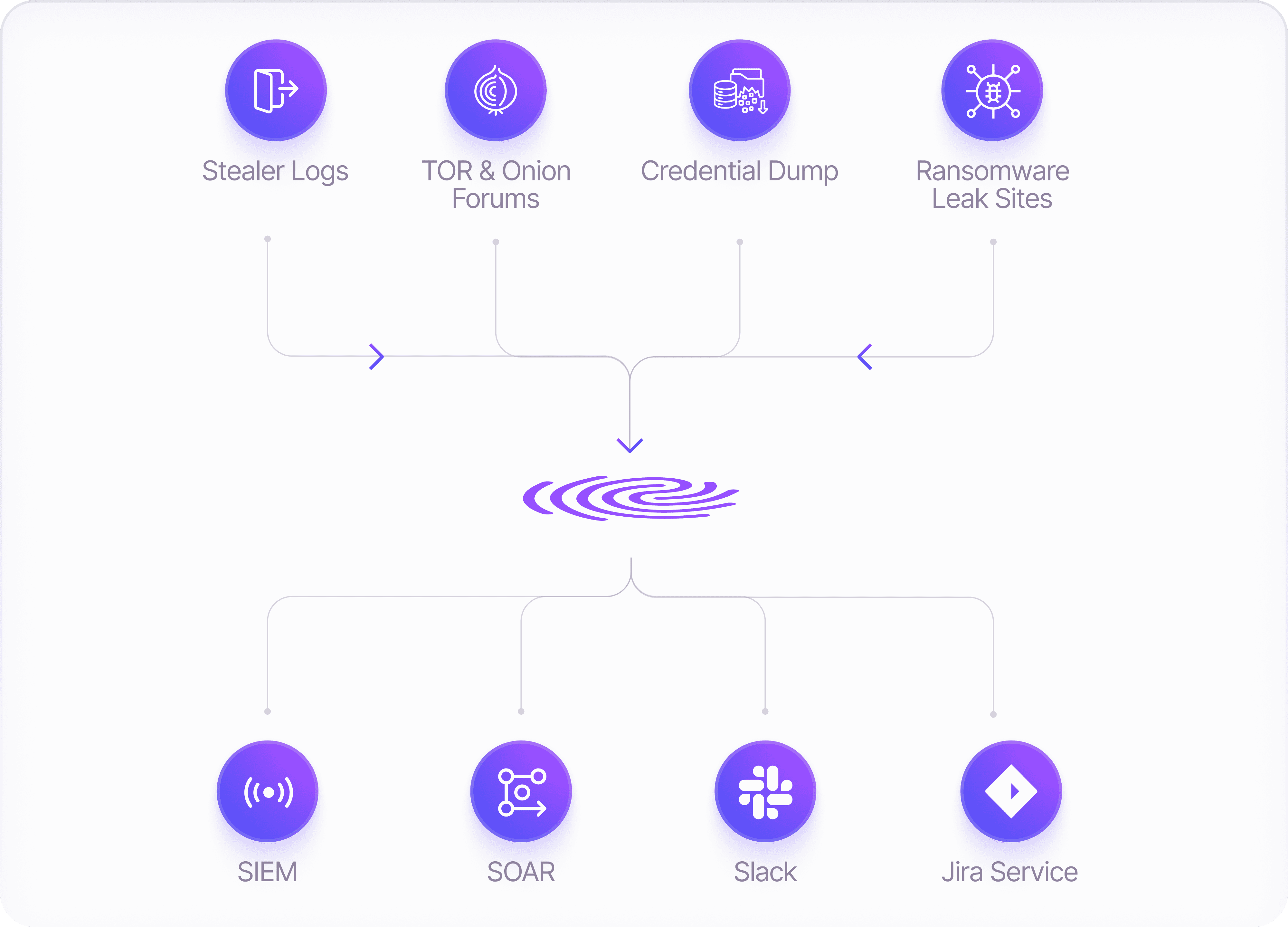
RiskProfiler consolidates discoveries from Stealer logs to TOR forums into your existing detection and response stack, giving analysts actionable insight without context switching.
Enrich SIEM alerts with leaked credentials and exposure metadata
Map dark web signals to affected identities, systems, or cloud assets
Integrate seamlessly with Slack, Jira, Splunk, and SOAR tools
Book a Demo

Accelerated
Dark Web
Threat Resolution
RiskProfiler streamlines threat resolution by enriching every dark web exposure with verified context, enabling analysts to assess severity, prioritize quickly, and respond decisively without losing investigative continuity.
Identify breach origin, exposure depth, and affected systems
Access AI-powered remediation steps aligned with the threat’s severity
Immediately escalate enriched alerts to IR, SecOps, or SOAR pipelines
Book a Demo
Benefits of RiskProfiler
Dark Web Monitoring
Leverage agentic AI-powered dark web intelligence to stay ahead of evolving adversaries.


Enhanced SOC Efficiency
Identify compromised employee or customer details by analyzing malware artifacts, session tokens, browser fingerprints, and anomalies across underground sources.

Covert Network Intelligence
KnyX Dark Web AI monitors Onion and TOR services, encrypted forums, Discord Servers, and restricted Telegram channels, revealing threats that would otherwise remain undiscoverable.

Supply Chain Exposures
RiskProfiler’s Agentic AI module tracks third-party credentials, vendor exposures, data leaks, and partner breaches across the dark web, exposing cascading risks that most traditional tools cannot detect.

Integrated Threat Hunting
Enable proactive threat hunting by correlating dark web exposures, identity artifacts, and underground activity with access paths to surface hidden risks, enabling rapid response.
Trusted by
Security Leaders

4.8/5

4.8 out of 5 stars

Best Ease of Use
2024
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer

Ready to Transform Deep & Dark Web Monitoring?
Join hundreds of security teams who trust KnyX Dark Web AI to cut through the noise and focus on what matters most.
Book a Demo Today
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Curious About How Dark Web Monitoring Works?
We’ve Got You Covered!
Get clear answers on how Knyx Dark Web AI enhances detection accuracy, reduces noise, and uncovers threats before attackers strike.
How quickly will RiskProfiler detect a leaked credential or data exposure?
RiskProfiler performs real-time ingestion of stealer logs, breach dumps, and underground postings. When a password, token, browser fingerprint, cloud key, or internal hostname is detected in a monitored source, KnyX AI automatically: Normalizes and hashes the exposed artifact Validates its authenticity and source provenance Correlates it with the identity or system it belongs to Assigns severity based on privilege depth and exploitability This enables high-confidence alerts to be delivered within minutes of the exposure appearing online.
How does AI improve dark web intelligence accuracy?
Agentic AI continuously interprets underground data, autonomously filtering noise, clustering linked exposures, identifying attack patterns, and attributing activity to actors. It correlates signals to your identities and assets, reducing false positives and enabling faster, high-confidence decisions.
Can RiskProfiler help us validate potential breaches?
Yes. RiskProfiler traces leaked data to underground sources, identifies whether it belongs to your organization, and provides severity, origin, and impacted asset details used for incident validation.
Does RiskProfiler monitor for impersonation or brand abuse?
Yes. It detects phishing kits, spoof domains, fraudulent listings, and cloned profiles circulating across underground ecosystems targeting your brand or customers.
Schedule a Live
Dark
Web Monitoring
Demo
In a 30-minute session, see how KnyX AI continuously detects external threats, correlates risk signals, and reduces investigation noise - using real-world security scenarios.
External attack surface visibility
Autonomous threat correlation
Faster, clearer security decisions

4.8/5

4.8 out of 5 stars

Best Ease of Use
2024

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved
Take a Product Tour
Agentic AI-powered Dark Web Monitoring
Dark Web Monitoring,
by
KnyX Dark Web AI
KnyX Dark Web AI connects every exposure to linked assets, access points, and external exposures, enabling decisive, informed remediation.


Trusted by 500+ enterprises
Trusted by
Industry Leaders


4.8/5


4.8 out of 5 stars
Scan underground ecosystems with agentic AI-powered monitoring for contextual threat insights.
Instant Threat Detection
See Critical
Dark Web
In Real-Time
Exposures,
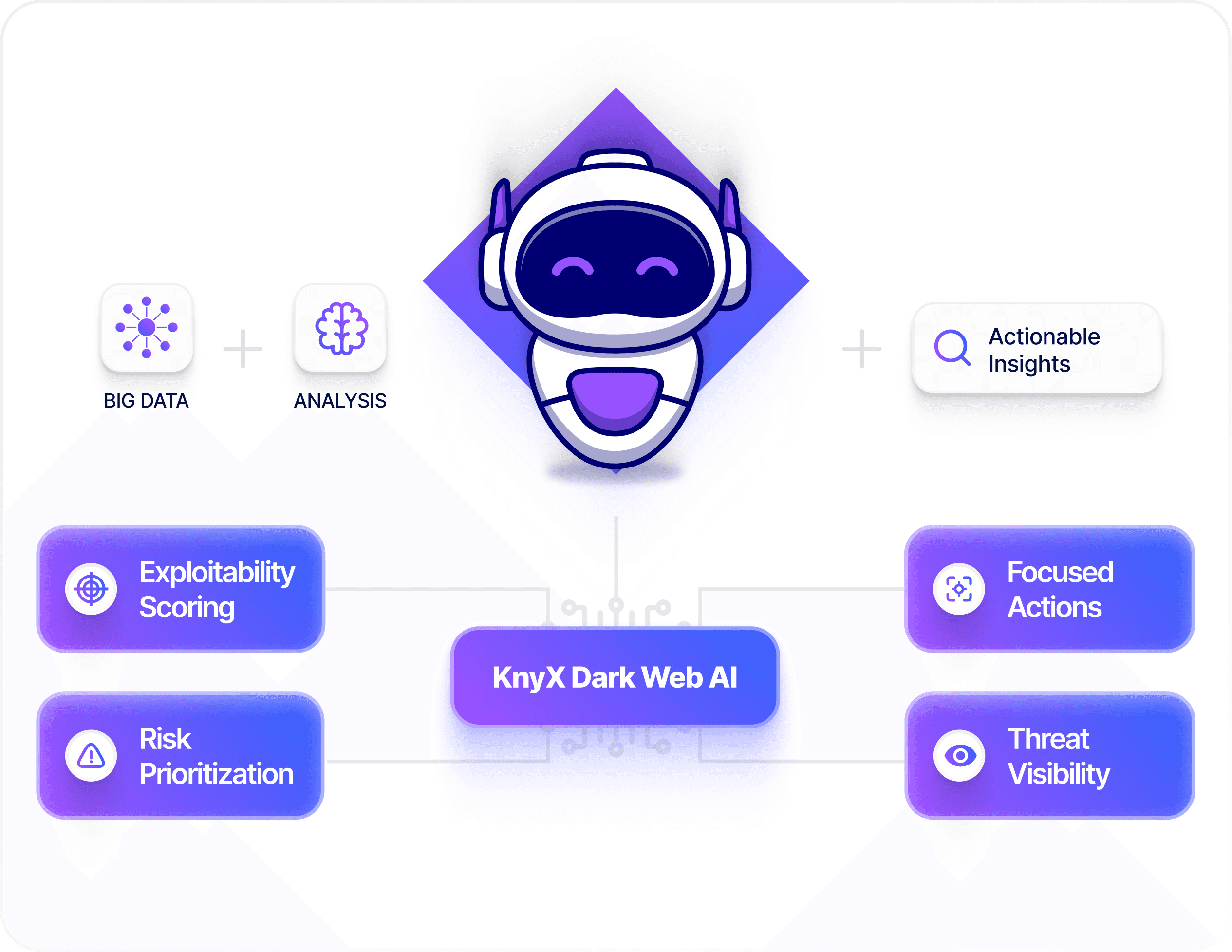

Agentic Dark Web Intelligence
Agentic AI enriches dark web exposures, surfacing the highest-impact, most exploitable risks first.
Stealer Logs
Auto Clustering
Exploitability Prioritization
Comprehensive Threat Intel


AI-Correlated Theat Context
Turn leaked creds into actionable insights by correlating signals and exposure paths with response playbooks.
Impact Scoring
Threat Timelines
Recommended Actions
Contextual Insights
Integrated Threat Signals
Send high-priority exposure alerts to Slack, Jira, and Servicenow instantly, for faster updates, accelerated response workflows, and reduced exploitation window.
Flexible Integration
Rapid Updates
Faster Containment
Integrated Workflow

Step 2
Telegram & Threat Surveillance
KnyX Dark Web AI scans Telegram and ransomware groups for mentions, stolen data, exploit chatter.

Step 3
Malware Hash & C2 Correlation
Identify malware hashes, C2 infrastructure, and correlate them with internal telemetry for faster incident response.

Step 1
TOR & Onion Service Monitoring
Detect leaked data and threat actor posts on Tor, Onion, and Ransomware Leak sites tied to your environment before they propagate.

Smart Threat Insight
Scale
Across
Threat Detection
Underground Forums
RiskProfiler turns silent exposures and threat signals into actionable defense with Agentic AI.


Unified SOC Intelligence
Integrated
Dark Web
Management
RiskProfiler consolidates underground discoveries into your existing detection and response stack for uniform insights.
Identity Threat Discovery
Identify compromised employee or customer details using malware artifacts, tokens, and underground anomalies.
Covert Network Intelligence
KnyX Dark Web AI scans TOR, encrypted forums, and Telegram to surface hidden threats.
Supply Chain Exposures
Agentic AI tracks third-party credentials, exposures, and partner breaches to reveal cascading risk.
Integrated Threat Hunting
Automated crawlers, powered by KnyX AI collect dark web threat intel, surfacing hidden threats and powering mitigation.


Proactive Threat Monitoring
Benefits of RiskProfiler
Dark Web Monitoring
Leverage dark web intelligence to stay ahead of data leaks and evolving adversary tactics.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved
Trusted by
Security Leaders
See what real users are saying about RiskProfiler. We don't filter. We just ship.


4.8/5


4.8 out of 5 stars
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
Voices of Security Leaders
Ready to Transform
Your Threat Management
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today
















































