Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Cisco SNMP Zero-Day: What Security Teams Need to Know
Cisco SNMP Zero-Day: What Security Teams Need to Know
Cisco IOS XE SNMP Zero Day CVE-2025-20352: exposure-led response steps to prevent disruption, footholds, and traffic interception.
Read Time
7 min read
Posted On
Feb 6, 2026
Social Media
Active exploitation of CVE-2025-20352 poses an immediate business risk to organizations running Cisco IOS and IOS XE routers and switches. The SNMP flaw can drive network outages, and if administrative SNMPv3 access is compromised, it enables remote code execution, turning network devices into footholds for lateral movement and traffic interception. With CISA adding the CVE to the Known Exploited Vulnerabilities (KEV) catalog, it is clear that the issue is being exploited in the wild, and remediation timelines are limited.
This advisory reinforces the foundational reality that organizations cannot secure assets they cannot see. External threat intelligence continues to discover internet-facing SNMP exposure across thousands of devices, many absent from internal inventories, creating blind spots where attackers can move faster than defenders. External Attack Surface Management platforms like RiskProfiler help teams discover unknown internet-exposed network assets, isolate risky management services like SNMP, and prioritize patching based on real exposure, asset criticality, and attack-path impact.
Vulnerability Overview: CVE-2025-20352
The Cisco IOS SNMP Zero Day (CVE-2025-20352) impacts the SNMP subsystem in Cisco IOS and IOS XE, where crafted SNMP input can trigger unsafe memory handling. The technical details below break down how the flaw is reached in practice and why the outcome differs between disruption and full compromise.
Technical Details
Cisco Security Advisory
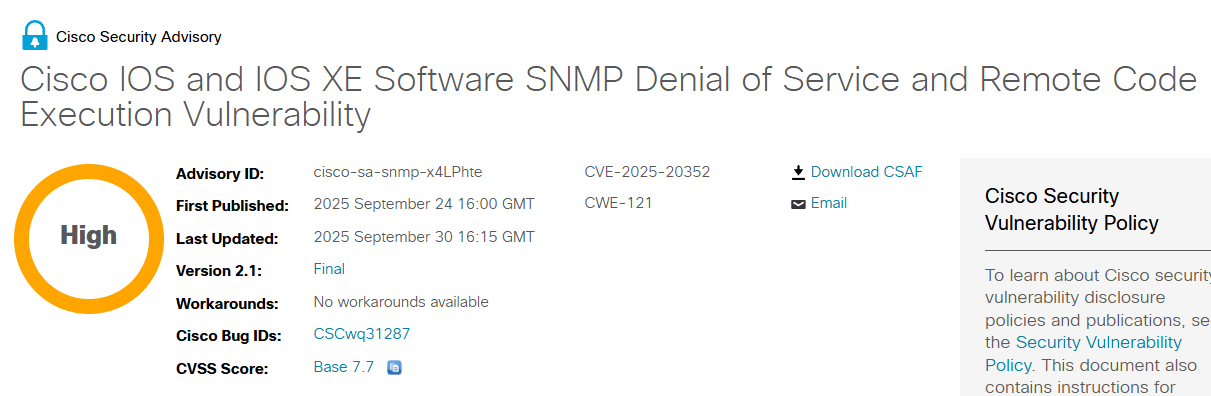
CVE-2025-20352 is a stack-based buffer overflow in the SNMP subsystem of Cisco IOS and Cisco IOS XE Software. The vulnerability enables two distinct attack paths depending on the attacker's privileges:
Attack Scenario | Prerequisites | Impact | MITRE ATT&CK |
Denial of Service | Valid SNMPv2c read-only community string OR SNMPv3 user credentials | Device reload; network disruption | T1498 (Network DoS), T1190 (Exploit Public-Facing Application) |
Remote Code Execution | Administrative SNMPv3 credentials (administrative or privilege level 15) | Arbitrary code execution; full device compromise | T1190, T1078 (Valid Accounts), T1602.002 (Network Device Config Dump) |
Affected Products
Cisco IOS Software (cpe:2.3:o:cisco:ios:12.2\(33\)sxi:*:*:*:*:*:*:*)
Cisco IOS XE Software (cpe:2.3:o:cisco:ios_xe_sd-wan:16.9.1:*:*:*:*:*:*:*)
All SNMP protocol versions (SNMPv1, SNMPv2c, SNMPv3)
Not Vulnerable:
Cisco IOS XR Software
Cisco NX-OS Software
CVSS Metrics:
Base Score: 7.7
Severity: High
Vendor: Cisco Systems
Exploited in the wild: Yes (confirmed by Cisco)
Exposure Analysis: The Internet-Facing SNMP Problem
Security teams can identify potentially exposed Cisco IOS and IOS XE devices by enumerating internet-facing hosts running SNMP on standard management ports and correlating service banners, protocol responses, and network fingerprints associated with Cisco network operating systems.
A representative exposure identification approach includes:
Discovery Logic
Internet-reachable hosts responding on:
- UDP/161 (SNMP queries)- UDP/162 (SNMP traps)
SNMP service detected with:
- Cisco-specific sysObjectID values
- IOS / IOS XE–associated SNMP engine IDs
- Responses indicating SNMPv1, SNMPv2c, or SNMPv3 support
Device characteristics consistent with:
- Cisco routing or switching platforms
- IOS or IOS XE software families
Risk Qualification
Devices meeting the above conditions should be considered high-priority for validation if:
SNMP is reachable from non-trusted IP ranges
SNMPv1 or SNMPv2c is enabled
Community strings are reused or weak
The device is absent from internal inventories or CMDB records
This exposure pattern mirrors the reconnaissance techniques used by attackers to identify candidate devices during automated scanning campaigns and should be treated as an actionable signal for immediate review and remediation.
Detection & Threat Hunting
Detection for CVE-2025-20352 should be driven by network telemetry, as SNMP exploitation often manifests first as abnormal UDP/161–162 traffic rather than endpoint signals. Prioritize hunts for SNMP volume spikes, OIDs being enumerated at scale, and management-plane access from non-approved IPs, especially on edge/SD-WAN devices.
Detection Rule 1: Abnormal SNMP Request Volume
Microsoft Sentinel / Azure Monitor (KQL):
// Detect reconnaissance or exploitation attempts via volume spike
CommonSecurityLog
| where DeviceVendor == "Cisco"
| where DestinationPort == 161 and Protocol == "UDP"
| summarize RequestCount=count(), UniqueOIDs=dcount(RequestContext)
by SourceIP, DestinationIP, bin(TimeGenerated, 5m)
| where RequestCount > 100 or UniqueOIDs > 50
| project TimeGenerated, SourceIP, DestinationIP, RequestCount, UniqueOIDs
| extend ThreatIndicator = "Possible CVE-2025-20352 reconnaissance or exploitation"
Tuning Notes: Adjust thresholds based on legitimate monitoring tool activity. Baseline normal SNMP request rates per device over 7 days, then set alerts at 3σ above mean. Whitelist known SNMP management system IPs.
Detection Rule 2: Default Community String Usage
Splunk SPL:
index=firewall OR index=network
dest_port=161 protocol=UDP
| regex _raw="(public|private)"
| stats count by src_ip, dest_ip
| where count > 5
| eval severity="critical",
description="Default SNMP community string detected - immediate rotation required"
| table _time, src_ip, dest_ip, count, severity
Requirements: Deep packet inspection (DPI) enabled on firewalls or SNMP trap logging configured on network devices. Note that encrypted SNMPv3 will not reveal community strings; this rule targets SNMPv1/v2c.
Hardening & Remediation
Given that no workaround fully mitigates CVE-2025-20352, the primary risk-reduction lever is to upgrade Cisco IOS and IOS XE to fixed software versions. As a first step in triage, confirm whether specific releases in your environment are affected. Cisco’s Software Checker provides the most direct way to validate exposure at the version level.
In parallel, run a targeted SNMP exposure audit across all network segments and edge deployments, then reconcile results against the CMDB. Any SNMP-enabled device discovered outside inventory should be treated as an ownership and patch-status gap until verified. Finally, assume credential hygiene will be tested at scale: remove default community strings immediately and rotate to strong, unique values that are not reused across devices or environments.
Configuration Hardening
Where operational constraints delay full upgrade coverage, tighten SNMP controls to reduce reachable attack surface. Deprecate SNMPv1/v2c in favor of SNMPv3 with authentication and encryption to eliminate plaintext community exposure and reduce interception risk (MITRE ATT&CK T1040). If interim controls are necessary, restrict access to the specific OIDs associated with the vulnerable path to limit an attacker’s ability to reach the affected code while patching is in progress.
Constrain SNMP access to trusted management systems and approved administrative workflows only. Use show snmp host to review trap and notification destinations and validate that no default identifiers (such as “public” or “private”) remain in active configuration; if present, remove or replace them immediately.
How RiskProfiler Helps Teams Stay Ahead of Exposure-Driven Network Breaches
Understanding where vulnerable devices exist externally is the difference between reactive patching and proactive risk reduction. Exposure-driven incidents like CVE-2025-20352 repeatedly show that “patching fast” is not enough when teams lack continuous visibility into their external attack surface and internet-facing assets. In many environments, SNMP-enabled routers and switches exist outside the CMDB, inherited through acquisitions, legacy provider handoffs, or unmanaged edge deployments. When those devices are invisible to operators, attackers gain the advantage and discover and probe infrastructure faster than defenders can inventory it.
RiskProfiler helps teams stay ahead of exploits like CVE-2025-20352 by continuously monitoring an organization’s external attack surface for the exact conditions attackers look for, like Internet-facing network devices, exposed management services (including SNMP), leaked access artifacts, and vulnerabilities mapped to real, attributable assets. Powered by its proprietary agentic AI module, KnyX AI, RiskProfiler performs outside-in discovery to surface unknown or unmanaged infrastructure that may not exist in internal inventories, then correlates exposures with vulnerability and threat intelligence to determine whether the organization is realistically at risk. The platform helps SOC teams discover CVEs relevant to their security posture, the exploitation routes, and their severity, ensuring contextual analysis and faster threat response.
Beyond detection, RiskProfiler helps security teams move faster by mapping the attack paths, their blast radius, and what a compromise could impact based on asset criticality and external connectivity. It helps security analysts prioritize remediation based on what matters most. This streamlines patching or isolation workflows for high-risk exposures, reduces blind spots in network infrastructure, and shortens the window between “exposed” and “fixed” before adversaries can operationalize it.
Conclusion
Network infrastructure is now part of the external attack surface and must be monitored accordingly. This Vulnerability in Cisco products highlights the importance of continuous monitoring of external assets, infrastructure, and cloud integrations running on vulnerable versions of software exposed to the internet. Shadow IT tools, unmonitored network devices, legacy configurations, and forgotten SNMP services expand an organization’s digital footprint in ways that traditional vulnerability management alone cannot address. By continuously discovering, classifying, and validating all Internet-facing assets, security teams can reduce blind spots, accelerate remediation, and stay ahead of both opportunistic and targeted threats.
Continuous external attack surface scans of management interfaces can pre-empt such exposure-driven exploits. Enabling regular assessment using External Attack Surface Management tools like RiskProfiler helps you discover and maintain an updated inventory of all unknown external assets, analyze them, map vulnerabilities to your digital ecosystem, and prioritize threat response based on their scope of impact.
Explore how RiskProfiler maps your external attack surface. Book a personalized demo with our experts today.
References
Active exploitation of CVE-2025-20352 poses an immediate business risk to organizations running Cisco IOS and IOS XE routers and switches. The SNMP flaw can drive network outages, and if administrative SNMPv3 access is compromised, it enables remote code execution, turning network devices into footholds for lateral movement and traffic interception. With CISA adding the CVE to the Known Exploited Vulnerabilities (KEV) catalog, it is clear that the issue is being exploited in the wild, and remediation timelines are limited.
This advisory reinforces the foundational reality that organizations cannot secure assets they cannot see. External threat intelligence continues to discover internet-facing SNMP exposure across thousands of devices, many absent from internal inventories, creating blind spots where attackers can move faster than defenders. External Attack Surface Management platforms like RiskProfiler help teams discover unknown internet-exposed network assets, isolate risky management services like SNMP, and prioritize patching based on real exposure, asset criticality, and attack-path impact.
Vulnerability Overview: CVE-2025-20352
The Cisco IOS SNMP Zero Day (CVE-2025-20352) impacts the SNMP subsystem in Cisco IOS and IOS XE, where crafted SNMP input can trigger unsafe memory handling. The technical details below break down how the flaw is reached in practice and why the outcome differs between disruption and full compromise.
Technical Details

Cisco Security Advisory
CVE-2025-20352 is a stack-based buffer overflow in the SNMP subsystem of Cisco IOS and Cisco IOS XE Software. The vulnerability enables two distinct attack paths depending on the attacker's privileges:
Attack Scenario | Prerequisites | Impact | MITRE ATT&CK |
Denial of Service | Valid SNMPv2c read-only community string OR SNMPv3 user credentials | Device reload; network disruption | T1498 (Network DoS), T1190 (Exploit Public-Facing Application) |
Remote Code Execution | Administrative SNMPv3 credentials (administrative or privilege level 15) | Arbitrary code execution; full device compromise | T1190, T1078 (Valid Accounts), T1602.002 (Network Device Config Dump) |
Affected Products
Cisco IOS Software (cpe:2.3:o:cisco:ios:12.2\(33\)sxi:*:*:*:*:*:*:*)
Cisco IOS XE Software (cpe:2.3:o:cisco:ios_xe_sd-wan:16.9.1:*:*:*:*:*:*:*)
All SNMP protocol versions (SNMPv1, SNMPv2c, SNMPv3)
Not Vulnerable:
Cisco IOS XR Software
Cisco NX-OS Software
CVSS Metrics:
Base Score: 7.7
Severity: High
Vendor: Cisco Systems
Exploited in the wild: Yes (confirmed by Cisco)
Exposure Analysis: The Internet-Facing SNMP Problem
Security teams can identify potentially exposed Cisco IOS and IOS XE devices by enumerating internet-facing hosts running SNMP on standard management ports and correlating service banners, protocol responses, and network fingerprints associated with Cisco network operating systems.
A representative exposure identification approach includes:
Discovery Logic
Internet-reachable hosts responding on:
- UDP/161 (SNMP queries)- UDP/162 (SNMP traps)
SNMP service detected with:
- Cisco-specific sysObjectID values
- IOS / IOS XE–associated SNMP engine IDs
- Responses indicating SNMPv1, SNMPv2c, or SNMPv3 support
Device characteristics consistent with:
- Cisco routing or switching platforms
- IOS or IOS XE software families
Risk Qualification
Devices meeting the above conditions should be considered high-priority for validation if:
SNMP is reachable from non-trusted IP ranges
SNMPv1 or SNMPv2c is enabled
Community strings are reused or weak
The device is absent from internal inventories or CMDB records
This exposure pattern mirrors the reconnaissance techniques used by attackers to identify candidate devices during automated scanning campaigns and should be treated as an actionable signal for immediate review and remediation.
Detection & Threat Hunting
Detection for CVE-2025-20352 should be driven by network telemetry, as SNMP exploitation often manifests first as abnormal UDP/161–162 traffic rather than endpoint signals. Prioritize hunts for SNMP volume spikes, OIDs being enumerated at scale, and management-plane access from non-approved IPs, especially on edge/SD-WAN devices.
Detection Rule 1: Abnormal SNMP Request Volume
Microsoft Sentinel / Azure Monitor (KQL):
// Detect reconnaissance or exploitation attempts via volume spike
CommonSecurityLog
| where DeviceVendor == "Cisco"
| where DestinationPort == 161 and Protocol == "UDP"
| summarize RequestCount=count(), UniqueOIDs=dcount(RequestContext)
by SourceIP, DestinationIP, bin(TimeGenerated, 5m)
| where RequestCount > 100 or UniqueOIDs > 50
| project TimeGenerated, SourceIP, DestinationIP, RequestCount, UniqueOIDs
| extend ThreatIndicator = "Possible CVE-2025-20352 reconnaissance or exploitation"
Tuning Notes: Adjust thresholds based on legitimate monitoring tool activity. Baseline normal SNMP request rates per device over 7 days, then set alerts at 3σ above mean. Whitelist known SNMP management system IPs.
Detection Rule 2: Default Community String Usage
Splunk SPL:
index=firewall OR index=network
dest_port=161 protocol=UDP
| regex _raw="(public|private)"
| stats count by src_ip, dest_ip
| where count > 5
| eval severity="critical",
description="Default SNMP community string detected - immediate rotation required"
| table _time, src_ip, dest_ip, count, severity
Requirements: Deep packet inspection (DPI) enabled on firewalls or SNMP trap logging configured on network devices. Note that encrypted SNMPv3 will not reveal community strings; this rule targets SNMPv1/v2c.
Hardening & Remediation
Given that no workaround fully mitigates CVE-2025-20352, the primary risk-reduction lever is to upgrade Cisco IOS and IOS XE to fixed software versions. As a first step in triage, confirm whether specific releases in your environment are affected. Cisco’s Software Checker provides the most direct way to validate exposure at the version level.
In parallel, run a targeted SNMP exposure audit across all network segments and edge deployments, then reconcile results against the CMDB. Any SNMP-enabled device discovered outside inventory should be treated as an ownership and patch-status gap until verified. Finally, assume credential hygiene will be tested at scale: remove default community strings immediately and rotate to strong, unique values that are not reused across devices or environments.
Configuration Hardening
Where operational constraints delay full upgrade coverage, tighten SNMP controls to reduce reachable attack surface. Deprecate SNMPv1/v2c in favor of SNMPv3 with authentication and encryption to eliminate plaintext community exposure and reduce interception risk (MITRE ATT&CK T1040). If interim controls are necessary, restrict access to the specific OIDs associated with the vulnerable path to limit an attacker’s ability to reach the affected code while patching is in progress.
Constrain SNMP access to trusted management systems and approved administrative workflows only. Use show snmp host to review trap and notification destinations and validate that no default identifiers (such as “public” or “private”) remain in active configuration; if present, remove or replace them immediately.
How RiskProfiler Helps Teams Stay Ahead of Exposure-Driven Network Breaches
Understanding where vulnerable devices exist externally is the difference between reactive patching and proactive risk reduction. Exposure-driven incidents like CVE-2025-20352 repeatedly show that “patching fast” is not enough when teams lack continuous visibility into their external attack surface and internet-facing assets. In many environments, SNMP-enabled routers and switches exist outside the CMDB, inherited through acquisitions, legacy provider handoffs, or unmanaged edge deployments. When those devices are invisible to operators, attackers gain the advantage and discover and probe infrastructure faster than defenders can inventory it.
RiskProfiler helps teams stay ahead of exploits like CVE-2025-20352 by continuously monitoring an organization’s external attack surface for the exact conditions attackers look for, like Internet-facing network devices, exposed management services (including SNMP), leaked access artifacts, and vulnerabilities mapped to real, attributable assets. Powered by its proprietary agentic AI module, KnyX AI, RiskProfiler performs outside-in discovery to surface unknown or unmanaged infrastructure that may not exist in internal inventories, then correlates exposures with vulnerability and threat intelligence to determine whether the organization is realistically at risk. The platform helps SOC teams discover CVEs relevant to their security posture, the exploitation routes, and their severity, ensuring contextual analysis and faster threat response.
Beyond detection, RiskProfiler helps security teams move faster by mapping the attack paths, their blast radius, and what a compromise could impact based on asset criticality and external connectivity. It helps security analysts prioritize remediation based on what matters most. This streamlines patching or isolation workflows for high-risk exposures, reduces blind spots in network infrastructure, and shortens the window between “exposed” and “fixed” before adversaries can operationalize it.
Conclusion
Network infrastructure is now part of the external attack surface and must be monitored accordingly. This Vulnerability in Cisco products highlights the importance of continuous monitoring of external assets, infrastructure, and cloud integrations running on vulnerable versions of software exposed to the internet. Shadow IT tools, unmonitored network devices, legacy configurations, and forgotten SNMP services expand an organization’s digital footprint in ways that traditional vulnerability management alone cannot address. By continuously discovering, classifying, and validating all Internet-facing assets, security teams can reduce blind spots, accelerate remediation, and stay ahead of both opportunistic and targeted threats.
Continuous external attack surface scans of management interfaces can pre-empt such exposure-driven exploits. Enabling regular assessment using External Attack Surface Management tools like RiskProfiler helps you discover and maintain an updated inventory of all unknown external assets, analyze them, map vulnerabilities to your digital ecosystem, and prioritize threat response based on their scope of impact.
Explore how RiskProfiler maps your external attack surface. Book a personalized demo with our experts today.
References
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved


