Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


The Importance of Monitoring and Securing Publicly Exposed Cloud Infrastructure
The Importance of Monitoring and Securing Publicly Exposed Cloud Infrastructure
In growing tech risk factors, public cloud security plays a crucial role as it covers a broad landscape. Get to know more insights here.
Read Time
7 min read
Posted On
Dec 5, 2023
Social Media
Introduction
The rapid evolution of cloud computing has significantly enhanced organizational agility and scalability. However, this shift has also introduced complex security challenges, particularly concerning publicly exposed cloud infrastructure. In this context, tools like RiskProfiler are pivotal. They offer a suite of products for Continuous Threat Exposure Management, addressing external attack surfaces, including cloud assets.
Understanding the Risks of Exposed Cloud Infrastructure
The Expanding Attack Surface
Cloud infrastructure is accessible over the internet presents a broad attack surface. Public exposure of cloud resources can lead to vulnerabilities, making them a target for cyber attacks. This exposure necessitates robust monitoring and securing mechanisms to protect sensitive data and maintain operational integrity.
The Need for Continuous Threat Exposure Management
Continuous Threat Exposure Management is essential in the dynamic cloud environment. It involves ongoing monitoring and analysis to detect and mitigate risks promptly. As a result, tools like Cloud RiskProfiler are vital here, employing context-enriched graph data models to identify and prioritize exposed assets.
Key Strategies for Securing Cloud Infrastructure
Cloud Attack Path Analysis
Understanding and analyzing potential attack paths in cloud environments is crucial. This involves assessing how an attacker could penetrate the cloud infrastructure. It also helps in identifying vulnerable points, and implementing measures to mitigate these risks.
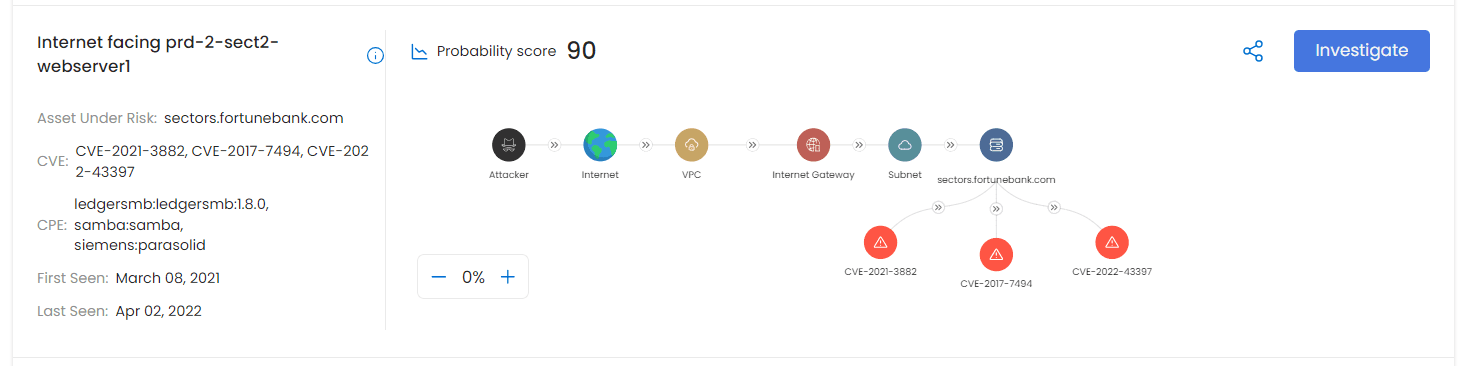
Integrating EASM and CASM
The integration of EASM and CASM solutions provides a holistic view of the external attack surface. However, this approach enables organizations to manage and secure their cloud infrastructure effectively.
Emphasizing Continuous Monitoring and Improvement
Continuous monitoring and regular updates to security protocols are essential to adapt to emerging threats and vulnerabilities in cloud environments.
Deep Dive into Cloud Infrastructure Vulnerabilities
Analyzing External Attack Surfaces
The external attack surface of cloud infrastructure comprises all the accessible points that interact with the external environment. These include APIs, web services, and storage endpoints. The management of these surfaces requires a comprehensive understanding of the cloud topology and the potential entry points for attackers.
Graph Data Models in Vulnerability Assessment
Advanced solutions employ enriched graph data models to map out cloud assets, creating a visual representation of connections and dependencies. This approach is pivotal in identifying isolated vulnerabilities. Also, this approach helps in understanding the interconnected risk landscape.
Continuous Threat Exposure Management Techniques for Cloud Environments
Cloud Attack Path Analysis
This involves a systematic approach to identifying potential pathways that an attacker might exploit to compromise cloud assets. Techniques include:
Automated Penetration Testing: Employing AI-driven tools to simulate attacks on cloud infrastructure to identify weaknesses.
Threat Modeling: Analyzing cloud infrastructure from an attacker’s perspective to anticipate potential attack vectors.
CASM – Cloud Attack Surface Management
CASM focuses on identifying, assessing, and managing the security of all cloud-based assets exposed to potential attackers. It involves:
Automated Asset Discovery: Continuously scanning for new or altered cloud assets.
Security Posture Analysis: Assessing the security configurations against best practices and compliance standards.
EASM – External Attack Surface Management
EASM extends beyond the cloud, encompassing the entire digital footprint of an organization. Key aspects include:
Digital Footprint Mapping: Identifying all external-facing IT assets, including cloud infrastructure.
Risk Scoring: Prioritizing vulnerabilities based on potential impact and exploitability.
Integrating Threat Intelligence
Incorporating real-time threat intelligence feeds into the security framework enhances the ability to predict and mitigate emerging threats. It involves analyzing patterns and behaviors in cyber threats and updating defense mechanisms accordingly.
Conclusion
In an era where cloud infrastructure forms the backbone of many organizations, the importance of monitoring and public cloud security cannot be overstated.
Tools like RiskProfiler with their comprehensive suite for Continuous Threat Exposure Management, play a crucial role in safeguarding against cyber threats. It also maintains operational resilience. Emphasizing strategies such as Cloud Attack Path Analysis, integrating EASM and CASM, and maintaining continuous vigilance is crucial. These drive organizations to effectively manage their external attack surfaces and protect their digital assets.
Introduction
The rapid evolution of cloud computing has significantly enhanced organizational agility and scalability. However, this shift has also introduced complex security challenges, particularly concerning publicly exposed cloud infrastructure. In this context, tools like RiskProfiler are pivotal. They offer a suite of products for Continuous Threat Exposure Management, addressing external attack surfaces, including cloud assets.
Understanding the Risks of Exposed Cloud Infrastructure
The Expanding Attack Surface
Cloud infrastructure is accessible over the internet presents a broad attack surface. Public exposure of cloud resources can lead to vulnerabilities, making them a target for cyber attacks. This exposure necessitates robust monitoring and securing mechanisms to protect sensitive data and maintain operational integrity.
The Need for Continuous Threat Exposure Management
Continuous Threat Exposure Management is essential in the dynamic cloud environment. It involves ongoing monitoring and analysis to detect and mitigate risks promptly. As a result, tools like Cloud RiskProfiler are vital here, employing context-enriched graph data models to identify and prioritize exposed assets.
Key Strategies for Securing Cloud Infrastructure
Cloud Attack Path Analysis
Understanding and analyzing potential attack paths in cloud environments is crucial. This involves assessing how an attacker could penetrate the cloud infrastructure. It also helps in identifying vulnerable points, and implementing measures to mitigate these risks.

Integrating EASM and CASM
The integration of EASM and CASM solutions provides a holistic view of the external attack surface. However, this approach enables organizations to manage and secure their cloud infrastructure effectively.
Emphasizing Continuous Monitoring and Improvement
Continuous monitoring and regular updates to security protocols are essential to adapt to emerging threats and vulnerabilities in cloud environments.
Deep Dive into Cloud Infrastructure Vulnerabilities
Analyzing External Attack Surfaces
The external attack surface of cloud infrastructure comprises all the accessible points that interact with the external environment. These include APIs, web services, and storage endpoints. The management of these surfaces requires a comprehensive understanding of the cloud topology and the potential entry points for attackers.
Graph Data Models in Vulnerability Assessment
Advanced solutions employ enriched graph data models to map out cloud assets, creating a visual representation of connections and dependencies. This approach is pivotal in identifying isolated vulnerabilities. Also, this approach helps in understanding the interconnected risk landscape.
Continuous Threat Exposure Management Techniques for Cloud Environments
Cloud Attack Path Analysis
This involves a systematic approach to identifying potential pathways that an attacker might exploit to compromise cloud assets. Techniques include:
Automated Penetration Testing: Employing AI-driven tools to simulate attacks on cloud infrastructure to identify weaknesses.
Threat Modeling: Analyzing cloud infrastructure from an attacker’s perspective to anticipate potential attack vectors.
CASM – Cloud Attack Surface Management
CASM focuses on identifying, assessing, and managing the security of all cloud-based assets exposed to potential attackers. It involves:
Automated Asset Discovery: Continuously scanning for new or altered cloud assets.
Security Posture Analysis: Assessing the security configurations against best practices and compliance standards.
EASM – External Attack Surface Management
EASM extends beyond the cloud, encompassing the entire digital footprint of an organization. Key aspects include:
Digital Footprint Mapping: Identifying all external-facing IT assets, including cloud infrastructure.
Risk Scoring: Prioritizing vulnerabilities based on potential impact and exploitability.
Integrating Threat Intelligence
Incorporating real-time threat intelligence feeds into the security framework enhances the ability to predict and mitigate emerging threats. It involves analyzing patterns and behaviors in cyber threats and updating defense mechanisms accordingly.
Conclusion
In an era where cloud infrastructure forms the backbone of many organizations, the importance of monitoring and public cloud security cannot be overstated.
Tools like RiskProfiler with their comprehensive suite for Continuous Threat Exposure Management, play a crucial role in safeguarding against cyber threats. It also maintains operational resilience. Emphasizing strategies such as Cloud Attack Path Analysis, integrating EASM and CASM, and maintaining continuous vigilance is crucial. These drive organizations to effectively manage their external attack surfaces and protect their digital assets.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



