Agentic AI-powered Cyber Threat Intelligence
Cyber Threat Intelligence, by Knyx Intel AI
Cyber Threat Intelligence,
by
Before They Strike
Knyx Intel AI
Gain full visibility into your external cloud and uncover hidden risks before they strike. Continuously monitor assets, assess vulnerabilities by criticality, and take proactive action to strengthen your security posture.
Unified threat intelligence enriched with WHOIS, TLS, and DNS data — extended across dark web and paste sites, mapped to MITRE ATT&CK for precision containment.


Trusted by 500+ enterprises
Trusted by 500+ enterprises
Recognized by
Trusted by
Global Firms
Industry Leaders
Gain trust and credibility with KnyX’s advanced reasoning layer, recognized by industry leaders for its clarity, accuracy, and ease of use.
Gain trust and credibility with KnyX’s advanced reasoning layer, recognized by industry leaders for its clarity, accuracy, and ease of use.


4.8/5
4.8/5


4.8 out of 5 stars
4.8 out of 5 stars

Best Ease of Use
2024
Your SOC’s
Your SOC’s
AI Security Assistant
AI Security Assistant
See Critical Threats, In Real-Time
Assistant
From real-time IOCs to adversary patterns, Knyx Intel AI reveals risks across your digital footprint with unmatched precision, to help you stay ahead of emerging threat infrastructure.
Real-time IOCs and threat patterns to reveal risks across your footprint.
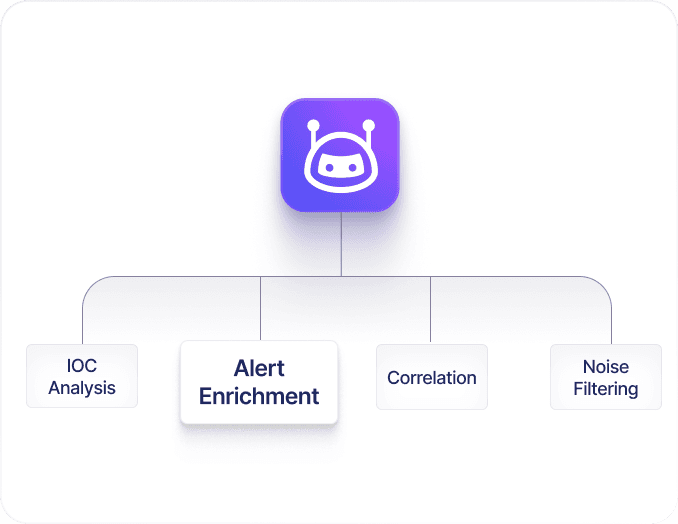


Automate SOC Workflows
RiskProfiler’s agentic AI automates IOC analysis, alert enrichment, correlation, and noise filtering, giving your analysts more time to focus on real incidents instead of repetitive manual triage.
Agentic AI automates IOC analysis and noise filtering so analysts focus on real incidents.
Threat Data
Incident Detection
Noise Filtering
IOC Analysis



Reduce MTTR
Accelerate investigations with real-time context, AI-driven recommendations, and pre-approved playbooks that help your SOC resolve critical threats faster and with greater confidence.
Accelerate incident resolution with AI-driven analysis that cuts noise and surfaces real threats instantly.
Instant Insights
Quick Remediation
Efficient Workflows
Rapid Triage
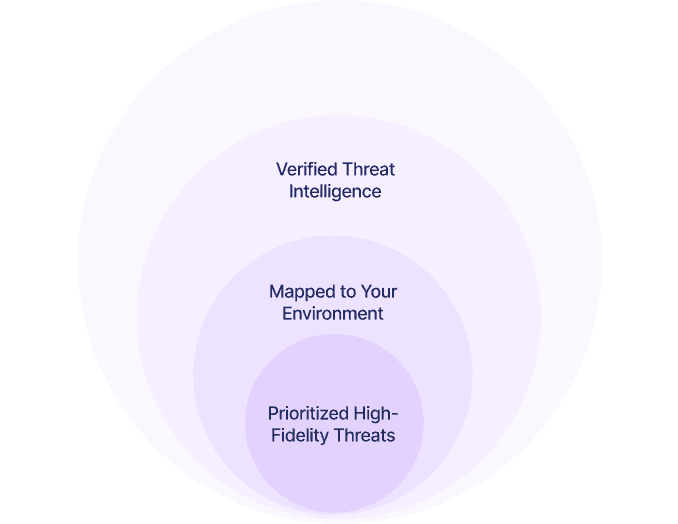


Prioritize High-Fidelity Threats
KnyX Intel AI highlights verified, high-impact threats mapped to your assets, cloud footprint, users, and vendors, ensuring your team always acts on what matters most.
Identify and elevate the most critical, high-confidence threats so your team focuses on what truly matters.
Threat Prioritization
Critical Threat Focus
High-Signal Alerts
Priority Scoring
Instant Threat Detection

How AI-Powered
Cyber Threat Intelligence
Works
Bridge the gap between threat intelligence and your attack surface with KnyX AI, highlighting attacker intent, IOC relevance, and potential breaches.
Identify Active Adversary Behavior
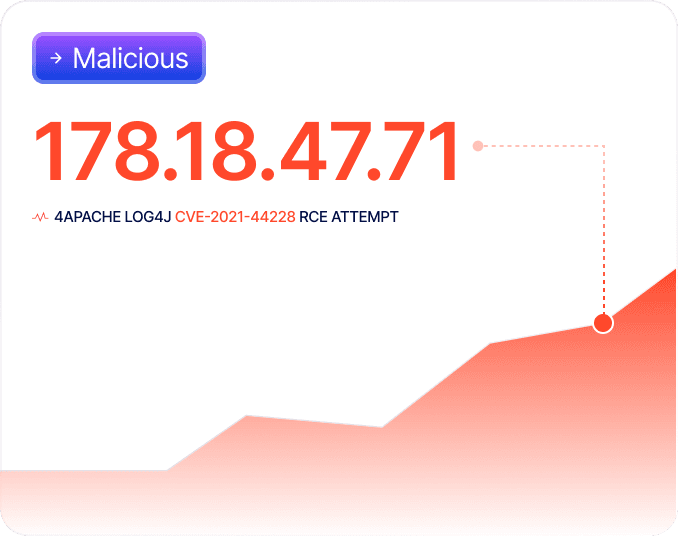
KnyX Intel AI continuously tracks malicious IPs, botnets, scanners, and exploit kits to curate attacker profiles actively probing vulnerabilities across your industry.
Map Prioritized IOCs to Attack Surface
Surface high-confidence indicators linked to active exploitation, command-and-control infrastructure, and known attacker clusters so your team can act decisively.
Spot Potential Perimeter Breaches
Track early signals of compromise by identifying malicious IP scanning ports, probing services, or testing credentials, allowing SOC teams to investigate threats before they become incidents.
Why is
Why is
Cyber Threat Intelligence
Cyber Threat Intelligence
Important for Your Business?
Important for Your Business?
From real-time IOCs to adversary patterns, Knyx Intel AI reveals risks across your digital footprint with unmatched precision, to help you stay ahead of emerging threat infrastructure.
KnyX Intel AI reveals risks across your footprint with real-time IOCs and adversary patterns.

Receive Live IOC & Exposure Updates
Stay ahead of cyber adversaries by identifying critical threats based on active exploitation patterns and Indicators of Compromise (IOC) impacting your environment.
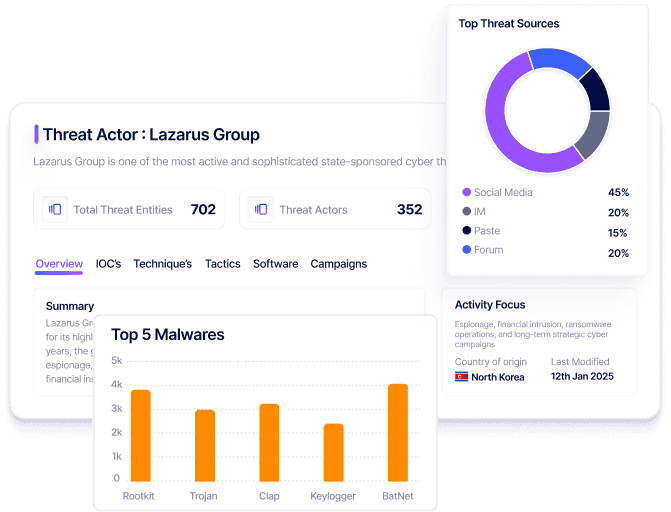

Adversary Attribution
Agentic AI links threats to attacker groups, tools, and malware, clarifying intent, strategy, and likely actions.
Step 2
Contextual Threat Validation
Verify threats in context to reduce false positives and improve response accuracy.
Step 3
Receive Live IOC & Exposure Updates
Identify critical threats by tracking active exploits and IOCs impacting your environment.


Contextual Threat Validation
KnyX Intel AI helps teams determine whether a threat is part of broad, opportunistic scanning or a focused attempt against your assets by analyzing trends.

Block Malicious Scanners
Block malicious IPs probing for vulnerabilities autonomously, reducing the risk of mass scanning or unauthorized access attempts across your systems.


Alerts for CVEs & Exploitation
Receive instantaneous notification of any known CVE being exploited, helping you patch or mitigate potential breaches before they escalate.
Step 1
Block Malicious Scanners
Autonomously block malicious IPs to stop scans and unauthorized access attempts.
Smart Threat Insight
SOC Intelligence
Integrated SOC Intelligence
Integrated
Unify threat intelligence across your SIEM, SOAR, and ticketing systems to accelerate triage, strengthen decisions, and eliminate unnecessary investigation overhead.
Unify threat intelligence across your SIEM, SOAR, and ticketing systems to accelerate triage
Unified SOC Intelligence
Enrich SIEM alerts with attacker context and real-world exploit insight Trigger SOAR actions based on high-confidence intelligence signals Integrate with Slack, Jira, ServiceNow, etc for faster coordinated response
Learn More



Enrich Alerts With Deep Attacker & Asset Context
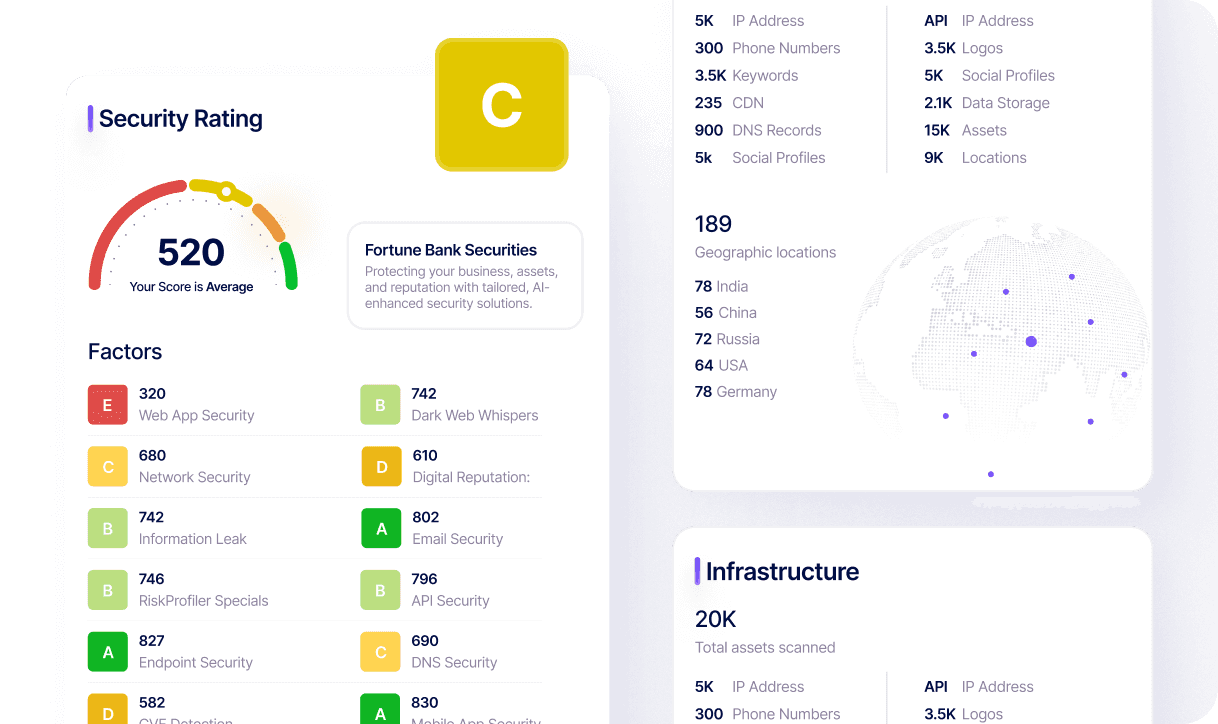
Benefits of RiskProfiler
Benefits of RiskProfiler
Cyber Threat Intelligence
Cyber Threat Intelligence
Stay vigilant across your external digital ecosystem 24X7 with proactive threat intelligence.
Stay vigilant across your external digital ecosystem 24X7 with proactive threat intelligence.
Proactive Cyber Intelligence
Enhanced SOC Efficiency
Reduce False Positives
Seamless Investigation Workflow
Integrated Threat Hunting
Reduce False Positives
Boost team productivity with automated workflows and intelligent data processing.
Enhanced SOC Efficiency
Boost team productivity with automated workflows and intelligent data processing.
Seamless Investigation Workflow
Boost team productivity with automated workflows and intelligent data processing.
Integrated Threat Hunting
Boost team productivity with automated workflows and intelligent data processing.



Enhanced SOC Efficiency
Accelerate triaging with enriched alerts that highlight the critical threat signals, improving the efficiency and productivity of your SOC teams.
Reduce False Positives
Increase detection confidence with contextualized AI-powered insights, which correlates potential threats, reducing false positives.
Seamless Investigation Workflow
Streamline investigations by integrating real-time threat intelligence into your existing SOAR/SIEM workflows, accelerating response times.
Integrated Threat Hunting
Transform threat hunting from guesswork into guided analysis with contextual intelligence that highlights meaningful adversary activity.
What
What
Security Leaders
Security Leaders
Think
Think
About RiskProfiler CTI?
About RiskProfiler CTI?
See what real users are saying about RiskProfiler - across
G2, Trustpilot, and X. We don't filter. We just ship.
See what real users are saying about RiskProfiler - across G2, Trustpilot, and X. We don't filter. We just ship.
Voices of Security Leaders


4.8/5
4.8/5


4.8 out of 5 stars
4.8 out of 5 stars

Best Ease of Use
2024
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
It’s refreshing to have a platform that cuts through noise instead of adding more of it. RiskProfiler's unified insights have been consistently reliable and easy for the team to trust.

Leif Dreizler
Sr Engineering Manager, Semgrep
The shift from scattered alerts to a structured, contextual threat picture has been a big improvement. RiskProfiler's helped us skip the guesswork.

Travis McPeak
CEO Resourcely, Ex - Netflix & Databricks
RiskProfiler helped us keep up with breaches across our massive supply chain and cloud posture. Now, our team doesn't need to manually move through spreadsheets to find vendor security risks. It just gets done in minutes.

Lucas Nelson
Partner, Lytical Ventures
RiskProfiler not only shows us alerts, but it also communicates the problem it can cause and how. It shows how separate signals relate, which helps us move faster during investigations.

Nick Galbreath
GP at Aviso Ventures
RiskProfiler has made it easier to prioritize alerts with confidence. The platform’s correlation engine highlights the few issues that actually pose risk, not the dozens that look urgent but aren’t.

Andrew Peterson
GP at Aviso Ventures
RiskProfiler is a value-for-money tool. It’s fast, reduces overhead from multiple tools, and centralizes data for maximum efficiency—perfect for achieving meaningful outcomes quickly

Joe Schreiber
CEO, Appnovi
The unified dashboard has become an integral part of our security workflow. It’s straightforward, easy to use, and gives our analysts a clear view without the usual clutter. The best part is the platform scales as we need without any glitches or trouble.

Nikhil S.
Synack Red Team Legend
With RiskProfiler, noisy alerts drop off quickly. What’s left is a clean, reliable picture of the risks that truly matter. This clarity has transformed our workflow, driving efficiency and enhancing analyst productivity.

Praveen Nallasamy
Head of Product Security, BlackRock
The correlated insights and the attack path mapping of RiskProfiler are incredibly helpful. Instead of juggling separate tools, we now see exactly how issues connect across modules and can narrow down exactly where we need to focus.

Kelly Castriotta
Global Cyber Underwriting Officer, Markel
RiskProfiler gives us one unified platform to understand what’s happening across our entire threat surface. The contextual view takes a lot of guesswork out of prioritizing what to fix first.

Gary Merry
Board Member & Chief Growth Officer
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform Your Threat Management?
Join hundreds of security teams who trust NYX to cut through the noise and focus on what matters most.



Ready to Transform
Your Threat Management
Ready to Transform
Your Threat Management
Join hundreds of security teams who trust NYX to cut through the noise and focus on what matters most.
Join hundreds of security teams who trust NYX to cut through the noise and focus on what matters most.
Book a Demo Today
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Curious About AI Threat Intelligence?
Let Us Break It Down.
Explore our FAQ to learn more about how RiskProfiler can help safeguard your digital assets and manage risks efficiently.
What is RiskProfiler Cyber Threat Intelligence?
RiskProfiler Cyber Threat Intelligence delivers analyzed, contextualized agentic AI-powered insights on emerging threats, attacker behavior, and vulnerabilities, helping security teams proactively detect risks, prioritize responses, and strengthen overall cyber resilience.
Why is AI-powered threat intelligence more effective?
How does RiskProfiler correlate IOCs from multiple sources?
How does CTI integrate with our SIEM or SOAR?
What is RiskProfiler Cyber Threat Intelligence?
RiskProfiler Cyber Threat Intelligence delivers analyzed, contextualized agentic AI-powered insights on emerging threats, attacker behavior, and vulnerabilities, helping security teams proactively detect risks, prioritize responses, and strengthen overall cyber resilience.
Why is AI-powered threat intelligence more effective?
How does RiskProfiler correlate IOCs from multiple sources?
How does CTI integrate with our SIEM or SOAR?
Schedule a Live
Agentic AI Security
Walkthrough
In a 30-minute session, see how Knyx AI continuously detects external threats, correlates risk signals, and reduces investigation noise - using real-world security scenarios.
External attack surface visibility
Autonomous threat correlation
Faster, clearer security decisions

4.8/5

4.8 out of 5 stars

Best Ease of Use
2024

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.










© 2025 RiskProfiler | All Rights Reserved










© 2025 RiskProfiler | All Rights Reserved










© 2025 RiskProfiler | All Rights Reserved
Take a Product Tour
Take a Product Tour









































