Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


External Cybersecurity for Startups: Importance in 2025
External Cybersecurity for Startups: Importance in 2025
As startups race to innovate, attract investors, and acquire customers, cybersecurity for startups and small businesses can feel like a back-burner issue-until it’s not.
Read Time
7 min read
Posted On
Apr 25, 2025
Social Media
As startups race to innovate, attract investors, and acquire customers, cybersecurity for startups and small businesses can feel like a back-burner issue—until it’s not. Startups or fast-growing small to medium-sized businesses are becoming the prime target of cyber attackers and hacking groups. According to Verizon’s 2025 DBIR Data Breach Report, small and medium-sized businesses and startups face cyberattacks four times more than large organizations.
Today, cybersecurity is no longer a luxury reserved for enterprises. It’s a foundational component of trust, continuity, and brand resilience. For startups, especially those scaling fast with limited security infrastructure, external threats pose a silent yet growing danger.
“Startups and small businesses are attractive targets not because they’re weak, but because they’re valuable and projects fast growth.”
-Setu Parimi, CTO, RiskProfiler
Startups and small businesses in their growth stage may not need an elaborate security team with red teaming professionals, they surely do need the support that can scan and detect the exposures in their sprawling systems for effective external exposure management.
Understanding The Importance of External Exposure Management
The 2025 Verizon data breach report also brings the spotlight to another major threat: External Cyber Threats. The report highlighted that 98% of cyber attacks faced by SMBs are from External Threats, which amounts to about 75% of total cybersecurity attacks in the case of large businesses.
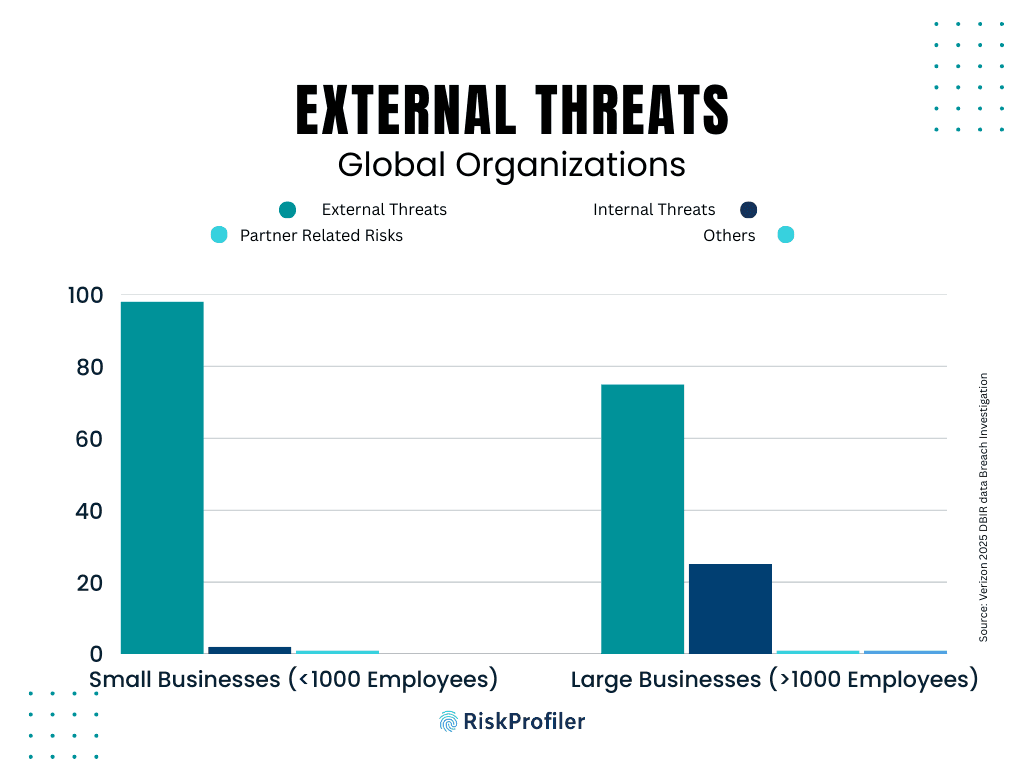
This report is a testament to the importance of External exposure management for small businesses and high-growth startups. External threat management refers to monitoring, assessing, and mitigating cybersecurity threats that originate outside of an organization’s internal environment.
Unlike internal cybersecurity, which focuses on endpoint protection, device hygiene, or employee access, external threat management scans the broader digital ecosystem. Leveraging External threat intelligence, you can gain a comprehensive view of your digital footprint, asset exposures, vendor-related risks, phishing intelligence, brand protection, and data on cloud exposure, in one place.
External Exposure Management Platforms help you gather contextual intelligence against:
Scammers and phishing sites are trying to lure your clients, employees, or customers with enticing offers
Duplicate entities using fraudulent domains, IPs, applications, or social media apps to dupe your audience
Presence of any open or exposed digital assets, such as unsecured AWS S3 buckets, shadow API, unregistered SaaS tool/integrations, cloud exposures, etc.
Potential underlying or unknown vulnerabilities hidden in the vendor’s system
Sales of sensitive business data, customer details, PII details, or any other sensitive information on deep or dark web forums and marketplaces
Targeted attacks or malicious campaigns created on social media to damage your brand identity
Why Are Startups the Prime Targets of External Attacks?
Startups and small to medium businesses (SMBs) have extreme growth potential. The expanding businesses require support from technology and software to match their operations with supply and demand. With limited resources and manpower, teams focused on cybersecurity for startups are not often proactive and versatile, leading to unintentional exposures or gaps in security protocols. In this section, we will focus on the top reason for the growing cyberattacks on small businesses.
1. Constrained Budgets and Scarcity of Security Expertise
Startups often function under tight financial constraints, channeling most of their resources toward product development, marketing efforts, or scaling operations. As a result, cybersecurity infrastructure for startups frequently takes a backseat. Without the means to hire full-time security professionals, the responsibility for managing cybersecurity often falls to founders or IT generalists who may lack the necessary expertise. This can leave critical gaps in threat detection and incident response.
Moreover, budget limitations typically restrict access to advanced security tools. Instead, startups resort to free or basic-tier solutions that are ill-equipped to detect complex or evolving threats. Compounding the problem, employees are rarely given formal cybersecurity training, making the organization more vulnerable to phishing, social engineering, and other common attack vectors.
2. Rapid Digital Expansion and Uncontrolled Asset Growth
The scaling requirements often push startups to frequently adopt cloud services, APIs, microservices, and a variety of third-party platforms. However, this digital expansion often occurs without a clear asset inventory or visibility into what’s being deployed due to a lack of oversight. The rise of shadow IT assets, where teams independently adopt tools or spin up environments with IT team oversight, makes it even more difficult to track and manage assets and cyber hygiene effectively.
With asset management decentralized or overlooked, outdated systems and poorly configured cloud resources begin to accumulate. This leads to an expanded and fragmented attack surface that small IT teams struggle to monitor. These overlooked vulnerabilities provide an ideal entry point for attackers seeking to exploit vulnerabilities in the infrastructure.
3. Overreliance on Vendors and SaaS Platforms
To remain agile and cost-efficient, startups lean heavily on third-party SaaS providers for core functions like customer relationship management, payroll, and communications. While convenient, this heavy reliance introduces significant risk. A simple supply chain risk or a hidden vulnerability in a vendor’s ecosystem can have a ripple effect, compromising the startup’s data and operations.
The vetting and monitoring of vendors are often limited or inconsistent, allowing hidden vulnerabilities to persist over time. Additionally, integrations like single sign-on (SSO) and the use of shared credentials, if not properly secured, can significantly amplify the risk by creating single points of failure within the security ecosystem.
4. Lack of Formal Security Leadership
The absence of a Chief Information Security Officer (CISO) or equivalent role is another key vulnerability for many startups. Without a centralized leader to guide strategy and oversee execution, security initiatives can become fragmented and reactive. Decision-making in the face of a threat is often delayed, as it falls to multiple stakeholders with competing priorities.
This lack of formal leadership results in a security posture that is largely reactive rather than proactive. Without a unified vision or roadmap, the organization struggles to implement consistent policies, anticipate threats, or build resilience into its systems and processes.
5. Attractive Targets for High-Value IP and Customer Data
Startups, despite their small size, are increasingly attractive targets for cybercriminals. Many possess valuable intellectual property, especially in high-stakes sectors such as biotech, fintech, and SaaS. Early-stage companies also tend to collect sensitive customer data during product testing and launches, which can be exploited for financial gain or competitive advantage.
In some cases, startups store prototype or confidential project data that could be of interest to competitors or even nation-state actors. These digital assets, while vital to the startup’s growth, also make them a prime target for espionage, ransomware, and data exfiltration.
6. Links to Enterprise Clients Create Supply Chain Risks
Many startups operate as technology partners or vendors to large enterprises, which opens another avenue for cyber threats. Cybercriminals increasingly target startups as a gateway into larger corporate ecosystems, exploiting their typically minimal security protections. For example, in a recent cyber attack, the hospitality management software Otelier experienced a major cybersecurity breach. In the breach, threat actors exfiltrated 7.8 TB of data from their Amazon Cloud storage in an attempt to steal data belonging to the global hotel chain, Marriott.
By compromising a startup’s systems, attackers can use them as a foothold to inject malware or harvest credentials that provide access to enterprise networks. If successful, such breaches not only disrupt operations but can also trigger serious regulatory repercussions for both the startup and its enterprise clients, especially if sensitive data is exposed or services are interrupted.
Cybersecurity for Startups: How Can A Lack of Guardrails be Dangerous?
Early-stage businesses and startups are often the most vulnerable due to their limited resources and evolving security protocols. These gaps and a lack of proper external exposure management protocols leave them vulnerable to attacks.
Take, for instance, a fintech startup that accidentally left its staging environment exposed online. It wasn’t a sophisticated breach. A routine scan by a malicious actor revealed the vulnerability. But the consequences were as simple as the attack.
The attacker managed to steal customer credentials, triggering a chain of events that included a full-scale investigation, regulatory scrutiny, and ultimately, a significant funding delay that set the company back by six months. This is not just a cautionary tale; it’s a real-world reminder that the cost of inaction can be steep, often the final nail to your dream and progress.
The Repercussions of External Attacks on Startups and Small Businesses
The impact of external threats can hit a startup from multiple angles. Financially, businesses may face direct losses due to fraud or ransom demands, and indirectly through legal settlements and incident response costs. Operationally, an attack can grind development to a halt, disrupt key service-level agreements, and erode team productivity at critical moments.
However, till now, we have only discussed the direct consequences of an attack on a startup. As a result of a serious cybersecurity attack, their reputation also takes a severe hit, particularly in sensitive industries like B2B software or financial technology. Trust is a core part of the value proposition when operating in these sensitive industries. A single breach can make customers and clients question the reliability of your brand, resulting in loss of partners, investors, and valued clients. On top of that, legal and regulatory obligations are not scaled down for small companies. Whether it’s GDPR in Europe or CCPA in California, startups are just as accountable as large enterprises when it comes to protecting user data.
Early Wins: Building an External Threat Exposure Management Strategy
Building a fully functional and diverse security team may be impractical for a startup or small-scale business. However, there are practical, effective steps that can be taken to integrate threat visibility into your existing operations without significant overhead.
Start with awareness and prioritization. Know where your vulnerabilities lie, understand the nature of the threats you face, and establish protocols that align with your risk tolerance and compliance requirements. From there, even modest investments in threat detection and response can yield major dividends in resilience and credibility.
Cybersecurity for Startups: A To-Do List for External Exposure Management
The first step toward ensuring stronger cybersecurity for startups and small businesses is to map out your digital footprint and conduct effective external attack surface analysis. That includes not just your core infrastructure, but also unlisted IT assets, test environments, and any third-party services connected to your systems. These often-overlooked areas can become major entry points for attackers, crippling your systems in minutes.
IAM policies and brand threat monitoring are some invaluable components that also should be established to detect leaked credentials and impersonation attempts, like fake phishing domains. It’s essential to catch these signs early before they’re used to run damaging campaigns or gain access to your system.
Another area of focus is cloud security. Misconfigured storage buckets or exposed APIs are some of the most common causes of data exposure. In a multi-cloud system, navigating threats spread across the entangled network can be difficult in the absence of a reliable CASM tool. Regular scans with the help of attack surface analysis and cloud monitoring tools can help identify and fix these gaps quickly.
Finally, invest in external threat intelligence tools. These can provide insight into emerging risks and help your team take proactive steps before threats turn into incidents. With the right approach, cybersecurity becomes not just a defensive measure but a strategic advantage that supports long-term growth.
How Does RiskProfiler Help with Cybersecurity for Startups?
Modern cybersecurity doesn’t need to be bulky, overly complex, or financially out of reach. RiskProfiler is built on the belief that early-stage companies deserve enterprise-grade protection with startup-ready flexibility. Our platform offers a range of lightweight, modular solutions that scale with your business growth and provide robust defense from day one. Here’s how:
External Attack Surface Management
Startups are constantly evolving, from new web services to sudden infrastructure changes with multi-cloud systems and SaaS upgrades. RiskProfiler’s External Attack Surface Management platform provides continuous asset discovery and classification. It identifies exposed IPs, subdomains, ports, cloud assets, and even forgotten dev environments for complete external exposure management. The real-time visibility with fast detection ensures that you’re always aware of what’s connected to the internet and how it could be targeted by attackers.
“We built EASM with startup speed in mind, automated scans, contextual alerts, and zero configuration overhead.”
- Setu Parimi, CTO, RiskProfiler
Brand Protection and Counterfeit Domain Detection
Cybercriminals love impersonating brands to trick customers or employees. RiskProfiler’s Brand Protection module continuously monitors for typosquatting domains, logo misuse, fake social profiles, and fraudulent mobile apps. When a lookalike threat is found, you receive actionable intelligence and takedown workflows with automation to ensure minimal manual effort and proactive action.
Dark Web Monitoring for Leaked Credentials
Your employees’ reused or breached credentials are often the weakest link, as observed in the Colonial Pipeline Attack (2021). RiskProfiler’s Dark Web Monitoring scans criminal forums, breach databases, and marketplaces for stolen email-password combos, private API keys, or leaked source code. If your company data appears in these places, you’ll know immediately before threat actors weaponize it, enabling proactive mitigation.
Third-Party Risk Management for Vendor Security
Startups rely heavily on SaaS tools, dev platforms, and outsourced services. This hyper-reliance on third-party services makes them vulnerable to vendor breaches and third-party attacks. RiskProfiler’s Third-Party Risk Management module assesses your extended attack surface. The platform’s supply chain risk intelligence tool tracks the vendor ecosystem for known vulnerabilities, security incidents, and compliance gaps, helping you make informed decisions and avoid supply chain blind spots.
Attack Path Analysis to Predict Breach Scenarios
Understanding how an attacker could move through your environment is crucial. RiskProfiler’s Attack Path Analysis capability maps out potential breach vectors using your real-world data. It shows how an exposed credential might lead to cloud takeover or how a phishing domain could result in lateral movement. This clarity empowers better prioritization and patching.
Ad Hoc Reconnaissance
Sometimes you need a quick scan, whether for a pitch meeting, board update, compliance audit, or to fend off a surprise knocking on your door. RiskProfiler’s recon tools let you generate on-demand security snapshots, run targeted scans, or investigate a sudden anomaly. This enables faster and targeted threat response, especially against time-sensitive threats, preventing escalation.
8. Conclusion: Making External Exposure Management a Strategic Priority
As your startup grows, so does your exposure to external threats. Threat actors do not wait for you to hire a security team; they start scanning for probable vulnerabilities the moment your brand appears online. The upside is that effective protection doesn’t require a massive budget or a dedicated SOC. By adopting a security-first mindset and leveraging the right tools, startups can build a strong, scalable foundation for resilience.
Start with visibility. Maintain continuous monitoring and implement attack surface analysis protocols to stay up-to-date with threat posture. And above all, view cybersecurity not as overhead but as a driver of trust, stability, and long-term growth.
As startups race to innovate, attract investors, and acquire customers, cybersecurity for startups and small businesses can feel like a back-burner issue—until it’s not. Startups or fast-growing small to medium-sized businesses are becoming the prime target of cyber attackers and hacking groups. According to Verizon’s 2025 DBIR Data Breach Report, small and medium-sized businesses and startups face cyberattacks four times more than large organizations.
Today, cybersecurity is no longer a luxury reserved for enterprises. It’s a foundational component of trust, continuity, and brand resilience. For startups, especially those scaling fast with limited security infrastructure, external threats pose a silent yet growing danger.
“Startups and small businesses are attractive targets not because they’re weak, but because they’re valuable and projects fast growth.”
-Setu Parimi, CTO, RiskProfiler
Startups and small businesses in their growth stage may not need an elaborate security team with red teaming professionals, they surely do need the support that can scan and detect the exposures in their sprawling systems for effective external exposure management.
Understanding The Importance of External Exposure Management
The 2025 Verizon data breach report also brings the spotlight to another major threat: External Cyber Threats. The report highlighted that 98% of cyber attacks faced by SMBs are from External Threats, which amounts to about 75% of total cybersecurity attacks in the case of large businesses.

This report is a testament to the importance of External exposure management for small businesses and high-growth startups. External threat management refers to monitoring, assessing, and mitigating cybersecurity threats that originate outside of an organization’s internal environment.
Unlike internal cybersecurity, which focuses on endpoint protection, device hygiene, or employee access, external threat management scans the broader digital ecosystem. Leveraging External threat intelligence, you can gain a comprehensive view of your digital footprint, asset exposures, vendor-related risks, phishing intelligence, brand protection, and data on cloud exposure, in one place.
External Exposure Management Platforms help you gather contextual intelligence against:
Scammers and phishing sites are trying to lure your clients, employees, or customers with enticing offers
Duplicate entities using fraudulent domains, IPs, applications, or social media apps to dupe your audience
Presence of any open or exposed digital assets, such as unsecured AWS S3 buckets, shadow API, unregistered SaaS tool/integrations, cloud exposures, etc.
Potential underlying or unknown vulnerabilities hidden in the vendor’s system
Sales of sensitive business data, customer details, PII details, or any other sensitive information on deep or dark web forums and marketplaces
Targeted attacks or malicious campaigns created on social media to damage your brand identity
Why Are Startups the Prime Targets of External Attacks?
Startups and small to medium businesses (SMBs) have extreme growth potential. The expanding businesses require support from technology and software to match their operations with supply and demand. With limited resources and manpower, teams focused on cybersecurity for startups are not often proactive and versatile, leading to unintentional exposures or gaps in security protocols. In this section, we will focus on the top reason for the growing cyberattacks on small businesses.
1. Constrained Budgets and Scarcity of Security Expertise
Startups often function under tight financial constraints, channeling most of their resources toward product development, marketing efforts, or scaling operations. As a result, cybersecurity infrastructure for startups frequently takes a backseat. Without the means to hire full-time security professionals, the responsibility for managing cybersecurity often falls to founders or IT generalists who may lack the necessary expertise. This can leave critical gaps in threat detection and incident response.
Moreover, budget limitations typically restrict access to advanced security tools. Instead, startups resort to free or basic-tier solutions that are ill-equipped to detect complex or evolving threats. Compounding the problem, employees are rarely given formal cybersecurity training, making the organization more vulnerable to phishing, social engineering, and other common attack vectors.
2. Rapid Digital Expansion and Uncontrolled Asset Growth
The scaling requirements often push startups to frequently adopt cloud services, APIs, microservices, and a variety of third-party platforms. However, this digital expansion often occurs without a clear asset inventory or visibility into what’s being deployed due to a lack of oversight. The rise of shadow IT assets, where teams independently adopt tools or spin up environments with IT team oversight, makes it even more difficult to track and manage assets and cyber hygiene effectively.
With asset management decentralized or overlooked, outdated systems and poorly configured cloud resources begin to accumulate. This leads to an expanded and fragmented attack surface that small IT teams struggle to monitor. These overlooked vulnerabilities provide an ideal entry point for attackers seeking to exploit vulnerabilities in the infrastructure.
3. Overreliance on Vendors and SaaS Platforms
To remain agile and cost-efficient, startups lean heavily on third-party SaaS providers for core functions like customer relationship management, payroll, and communications. While convenient, this heavy reliance introduces significant risk. A simple supply chain risk or a hidden vulnerability in a vendor’s ecosystem can have a ripple effect, compromising the startup’s data and operations.
The vetting and monitoring of vendors are often limited or inconsistent, allowing hidden vulnerabilities to persist over time. Additionally, integrations like single sign-on (SSO) and the use of shared credentials, if not properly secured, can significantly amplify the risk by creating single points of failure within the security ecosystem.
4. Lack of Formal Security Leadership
The absence of a Chief Information Security Officer (CISO) or equivalent role is another key vulnerability for many startups. Without a centralized leader to guide strategy and oversee execution, security initiatives can become fragmented and reactive. Decision-making in the face of a threat is often delayed, as it falls to multiple stakeholders with competing priorities.
This lack of formal leadership results in a security posture that is largely reactive rather than proactive. Without a unified vision or roadmap, the organization struggles to implement consistent policies, anticipate threats, or build resilience into its systems and processes.
5. Attractive Targets for High-Value IP and Customer Data
Startups, despite their small size, are increasingly attractive targets for cybercriminals. Many possess valuable intellectual property, especially in high-stakes sectors such as biotech, fintech, and SaaS. Early-stage companies also tend to collect sensitive customer data during product testing and launches, which can be exploited for financial gain or competitive advantage.
In some cases, startups store prototype or confidential project data that could be of interest to competitors or even nation-state actors. These digital assets, while vital to the startup’s growth, also make them a prime target for espionage, ransomware, and data exfiltration.
6. Links to Enterprise Clients Create Supply Chain Risks
Many startups operate as technology partners or vendors to large enterprises, which opens another avenue for cyber threats. Cybercriminals increasingly target startups as a gateway into larger corporate ecosystems, exploiting their typically minimal security protections. For example, in a recent cyber attack, the hospitality management software Otelier experienced a major cybersecurity breach. In the breach, threat actors exfiltrated 7.8 TB of data from their Amazon Cloud storage in an attempt to steal data belonging to the global hotel chain, Marriott.
By compromising a startup’s systems, attackers can use them as a foothold to inject malware or harvest credentials that provide access to enterprise networks. If successful, such breaches not only disrupt operations but can also trigger serious regulatory repercussions for both the startup and its enterprise clients, especially if sensitive data is exposed or services are interrupted.
Cybersecurity for Startups: How Can A Lack of Guardrails be Dangerous?
Early-stage businesses and startups are often the most vulnerable due to their limited resources and evolving security protocols. These gaps and a lack of proper external exposure management protocols leave them vulnerable to attacks.
Take, for instance, a fintech startup that accidentally left its staging environment exposed online. It wasn’t a sophisticated breach. A routine scan by a malicious actor revealed the vulnerability. But the consequences were as simple as the attack.
The attacker managed to steal customer credentials, triggering a chain of events that included a full-scale investigation, regulatory scrutiny, and ultimately, a significant funding delay that set the company back by six months. This is not just a cautionary tale; it’s a real-world reminder that the cost of inaction can be steep, often the final nail to your dream and progress.
The Repercussions of External Attacks on Startups and Small Businesses
The impact of external threats can hit a startup from multiple angles. Financially, businesses may face direct losses due to fraud or ransom demands, and indirectly through legal settlements and incident response costs. Operationally, an attack can grind development to a halt, disrupt key service-level agreements, and erode team productivity at critical moments.
However, till now, we have only discussed the direct consequences of an attack on a startup. As a result of a serious cybersecurity attack, their reputation also takes a severe hit, particularly in sensitive industries like B2B software or financial technology. Trust is a core part of the value proposition when operating in these sensitive industries. A single breach can make customers and clients question the reliability of your brand, resulting in loss of partners, investors, and valued clients. On top of that, legal and regulatory obligations are not scaled down for small companies. Whether it’s GDPR in Europe or CCPA in California, startups are just as accountable as large enterprises when it comes to protecting user data.
Early Wins: Building an External Threat Exposure Management Strategy
Building a fully functional and diverse security team may be impractical for a startup or small-scale business. However, there are practical, effective steps that can be taken to integrate threat visibility into your existing operations without significant overhead.
Start with awareness and prioritization. Know where your vulnerabilities lie, understand the nature of the threats you face, and establish protocols that align with your risk tolerance and compliance requirements. From there, even modest investments in threat detection and response can yield major dividends in resilience and credibility.
Cybersecurity for Startups: A To-Do List for External Exposure Management
The first step toward ensuring stronger cybersecurity for startups and small businesses is to map out your digital footprint and conduct effective external attack surface analysis. That includes not just your core infrastructure, but also unlisted IT assets, test environments, and any third-party services connected to your systems. These often-overlooked areas can become major entry points for attackers, crippling your systems in minutes.
IAM policies and brand threat monitoring are some invaluable components that also should be established to detect leaked credentials and impersonation attempts, like fake phishing domains. It’s essential to catch these signs early before they’re used to run damaging campaigns or gain access to your system.
Another area of focus is cloud security. Misconfigured storage buckets or exposed APIs are some of the most common causes of data exposure. In a multi-cloud system, navigating threats spread across the entangled network can be difficult in the absence of a reliable CASM tool. Regular scans with the help of attack surface analysis and cloud monitoring tools can help identify and fix these gaps quickly.
Finally, invest in external threat intelligence tools. These can provide insight into emerging risks and help your team take proactive steps before threats turn into incidents. With the right approach, cybersecurity becomes not just a defensive measure but a strategic advantage that supports long-term growth.
How Does RiskProfiler Help with Cybersecurity for Startups?
Modern cybersecurity doesn’t need to be bulky, overly complex, or financially out of reach. RiskProfiler is built on the belief that early-stage companies deserve enterprise-grade protection with startup-ready flexibility. Our platform offers a range of lightweight, modular solutions that scale with your business growth and provide robust defense from day one. Here’s how:
External Attack Surface Management
Startups are constantly evolving, from new web services to sudden infrastructure changes with multi-cloud systems and SaaS upgrades. RiskProfiler’s External Attack Surface Management platform provides continuous asset discovery and classification. It identifies exposed IPs, subdomains, ports, cloud assets, and even forgotten dev environments for complete external exposure management. The real-time visibility with fast detection ensures that you’re always aware of what’s connected to the internet and how it could be targeted by attackers.
“We built EASM with startup speed in mind, automated scans, contextual alerts, and zero configuration overhead.”
- Setu Parimi, CTO, RiskProfiler
Brand Protection and Counterfeit Domain Detection
Cybercriminals love impersonating brands to trick customers or employees. RiskProfiler’s Brand Protection module continuously monitors for typosquatting domains, logo misuse, fake social profiles, and fraudulent mobile apps. When a lookalike threat is found, you receive actionable intelligence and takedown workflows with automation to ensure minimal manual effort and proactive action.
Dark Web Monitoring for Leaked Credentials
Your employees’ reused or breached credentials are often the weakest link, as observed in the Colonial Pipeline Attack (2021). RiskProfiler’s Dark Web Monitoring scans criminal forums, breach databases, and marketplaces for stolen email-password combos, private API keys, or leaked source code. If your company data appears in these places, you’ll know immediately before threat actors weaponize it, enabling proactive mitigation.
Third-Party Risk Management for Vendor Security
Startups rely heavily on SaaS tools, dev platforms, and outsourced services. This hyper-reliance on third-party services makes them vulnerable to vendor breaches and third-party attacks. RiskProfiler’s Third-Party Risk Management module assesses your extended attack surface. The platform’s supply chain risk intelligence tool tracks the vendor ecosystem for known vulnerabilities, security incidents, and compliance gaps, helping you make informed decisions and avoid supply chain blind spots.
Attack Path Analysis to Predict Breach Scenarios
Understanding how an attacker could move through your environment is crucial. RiskProfiler’s Attack Path Analysis capability maps out potential breach vectors using your real-world data. It shows how an exposed credential might lead to cloud takeover or how a phishing domain could result in lateral movement. This clarity empowers better prioritization and patching.
Ad Hoc Reconnaissance
Sometimes you need a quick scan, whether for a pitch meeting, board update, compliance audit, or to fend off a surprise knocking on your door. RiskProfiler’s recon tools let you generate on-demand security snapshots, run targeted scans, or investigate a sudden anomaly. This enables faster and targeted threat response, especially against time-sensitive threats, preventing escalation.
8. Conclusion: Making External Exposure Management a Strategic Priority
As your startup grows, so does your exposure to external threats. Threat actors do not wait for you to hire a security team; they start scanning for probable vulnerabilities the moment your brand appears online. The upside is that effective protection doesn’t require a massive budget or a dedicated SOC. By adopting a security-first mindset and leveraging the right tools, startups can build a strong, scalable foundation for resilience.
Start with visibility. Maintain continuous monitoring and implement attack surface analysis protocols to stay up-to-date with threat posture. And above all, view cybersecurity not as overhead but as a driver of trust, stability, and long-term growth.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



