Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


10 Reasons Dynamic Vendor Risk Assessment Is Critical in 2025
10 Reasons Dynamic Vendor Risk Assessment Is Critical in 2025
Global businesses today operate in a hyperconnected digital field, where an organization’s digital ecosystem is intricately fused with its vendors’ systems.
Read Time
7 min read
Posted On
Sep 2, 2025
Social Media
Global businesses today operate in a hyperconnected digital field, where an organization’s digital ecosystem is intricately fused with its vendors’ systems. Every time an organization onboards a new vendor, it risks exposing itself to potential threats lurking beyond its visibility zone. In 2025, relying on static, scheduled, questionnaire-based vendor assessments will no longer be enough to ensure third-party security. Organizations need intelligent, automated vendor risk assessments powered by AI-led cyber threat intelligence and real-time insights. These questionnaires are automated, streamlining the data collection and analysis process with an industry-specific assessment process.
Evolution of Third-Party Risks
Modern business operations are highly reliant on several SaaS tools, cloud services, and software programs to deliver comprehensive service benefits to clients. These may be the HR tools to keep track of employee data, productivity tools, hosting services, or payment applications linked to your website. All these external tools and applications expand your external attack surface and create an alternate pathway for attackers. Any risk or vulnerability in these ecosystems can lead threat actors to your infrastructure, causing severe damage.
Traditional methods like annual audits or spreadsheets are simply inadequate in this fast-evolving landscape. Threat posture evolves with every new connection or interaction, changing continuously, every day. To stay ahead, companies need smart, agile, and continuous ways to assess and monitor vendor risk. The answer lies in automation, AI, and actionable threat intelligence.
10 Reasons Smart Vendor Risk Assessments Are Essential in 2025
Smart vendor risk assessment workflows like RiskProfiler Vendor Risk Questionnaire make monitoring the supply chain risks comprehensive, continuous, and streamlined. The questionnaires can automate threat detection, verification, and initiate a collaboration process to remediate the hidden risks and exposures.
Continuous Monitoring Post-Onboarding
The vendor risk assessments are automated and integrated for continuous monitoring. Thus, these modules continue tracking the vendor attack surface as you onboard and integrate the vendor profile on the tool, allowing proactive surveillance.
Real-Time Risk Detection
Static, scheduled review processes miss these live updates on emerging threats. AI vendor risk assessments integrated with third-party risk management tools continuously monitor and surveil the third and fourth party ecosystem. Thus, it updates the risk scores dynamically as new vulnerabilities or threat activity is discovered, keeping the internal security team informed on threats in real-time.
Behavioral Anomaly Detection
AI vendor assessments monitor and detect suspicious activities on vendor threat posture with proactive modules and identification capabilities. In the event of deviation from the normal behavioral baseline, the questionnaire modules get activated and distribute a new assessment to the vendor in order to collect real-time intel and also alert the supplier of potential threats.
Threat Intelligence Integration
AI vendor risk assessments are integrated with sophisticated third-party risk management, external attack surface management, brand risk protection, and dark web threat monitoring protocols. Such collaboration allows the tool to collect comprehensive data on all possible vendor threat concerns and help them discern the cause and origin of the related threats.
Vendor Tiering & Prioritization
The vendor risk assessments collect data on your third and fourth party security postures, analyze the data against real-life industry standards and compliance frameworks. This allows it to prepare a baseline and determine the vendor’s risk threshold. This data provides the internal security team with a clear visual of each vendor’s security posture, risk status, and prepares a risk tiering with high, moderate, and low-risk vendors for simplified prioritization, onboarding, and decision-making process.
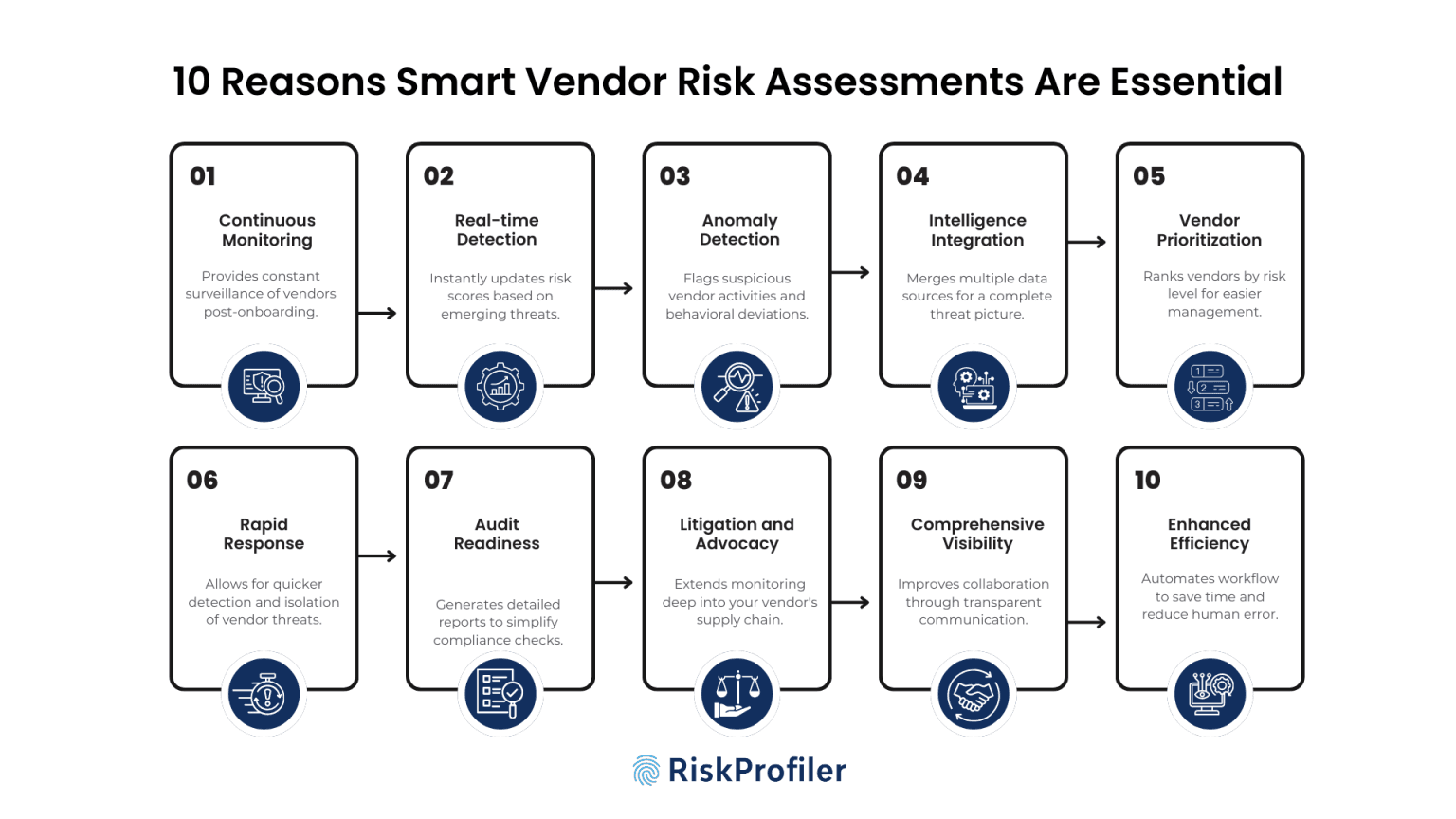
Faster Incident Response
Third-party risk questionnaires allow for fast detection as a threat emerges on a vendor system. These continuous monitoring capabilities provide organizations with the benefit of detecting vendor risk as it occurs, giving them crucial time to isolate and quarantine the system before the threat can reach their system.
Improved Audit Readiness
This questionnaire collects contextual data on threat origin, behavior, attack patterns, and targets with a timeline. This helps generate a detailed, structured threat report for identifying potential security gaps in third-party infrastructure and addressing them promptly.
Extended Third-Party Risks Visibility
Vendor risk questionnaires not only grant you visibility into your vendors. It allows continuous monitoring across your vendor’s supply chain simultaneously. This strengthens your security posture, offers truly comprehensive alertness against cyber attacks, and keeps you ahead of all potential attack vectors.
Strategic Vendor Relationships
The comprehensive visibility, threat preparedness, and streamlined compliance management allow organizations to maintain a transparent collaboration between suppliers and partners. It also allows fast communication with streamlined threat response, for proactive protection against vulnerabilities and malicious elements.
Enhance Efficiency & Reduce Human Error
AI vendor questionnaires streamline vendor attack surface monitoring, threat posture verification, compliance assessment, and the review process with automation. It reduces the time required for manual data collection, saves time otherwise wasted in scheduling and coordination, and removes the chances of human error.
Key Components of Third-Party Risk Assessments
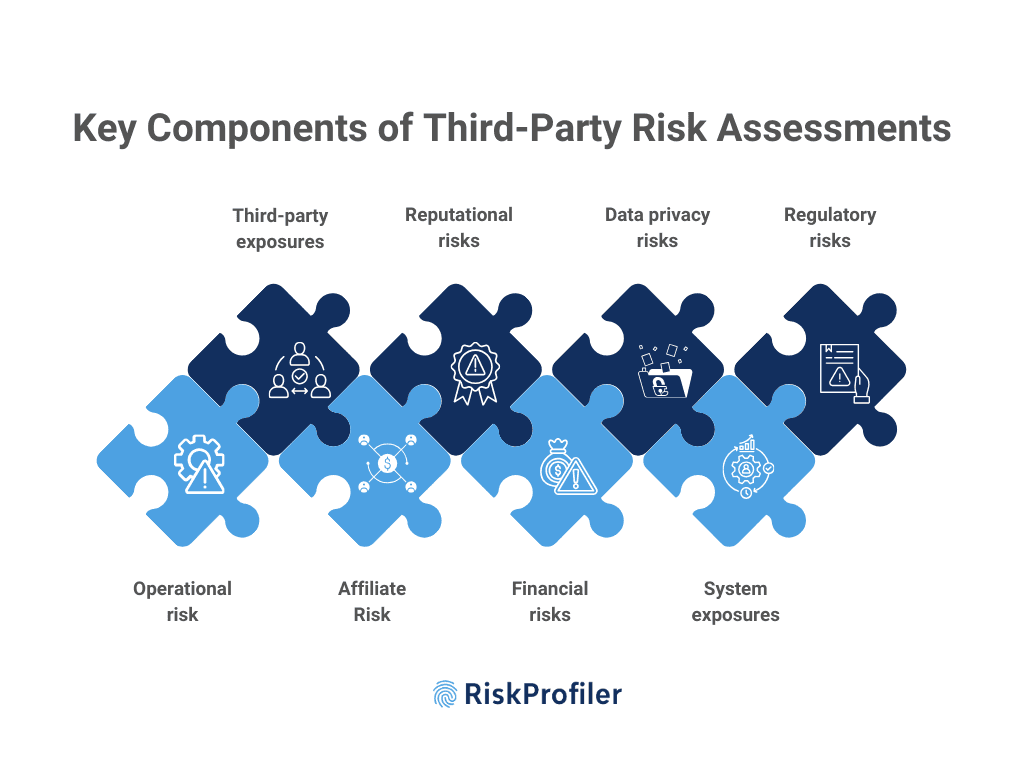
Third-party risk assessments or vendor risk assessments are conducted to study and analyze the underlying risk thresholds across multiple sectors in a vendor ecosystem. The key components of such risk vectors include operational risk, third-party exposures, risk introduced through partners and subsidiaries, reputational risks, financial risks, data privacy risks, system exposures, and regulatory risks.
As part of the third-party risk assessments, the security tools monitor the breach vectors, security gaps, and risk elements that can pose threats or allow unauthorized access. In the context of the detection and analysis protocols, the tools measure the IT network and systems, access privileges, and operational protocols to detect and analyze the security exposures and exposure severity in their ecosystem.
However, it is important to ensure that the results of vendor risk assessments are updated at all times for them to be reliable and not a relic. This is why it is essential to choose a smart, dynamic questionnaire like RiskProfiler VRA, which gets activated with the slightest changes to the vendor’s security posture. It ensures your security team is updated on exposures emerging on the supply chain in advance, allowing immediate response and remediation before the threats can reach your organization.
Managing Dynamic Vendor Risk Assessment: A RiskProfiler Guide
A third-party risk assessment framework like RiskProfiler integrates multiple threat modules and security practices to accurately monitor, analyze, and detect vendor threats lurking in one’s supply chain ecosystem. Here, we will show you how the RiskProfiler Vendor Risk Questionnaire streamlines the threat management process.
1. External Attack Surface Mapping
RiskProfiler offers you complete visibility into a vendor’s public-facing digital assets, such as domains, IP ranges, and cloud infrastructure. It monitors all external assets, tools, and exposures for comprehensive threat mapping.
With the initiation of an external attack surface monitoring, it crawls the internet and passive DNS records to catalogue all associated digital assets of a vendor. These digital assets include:
Primary and shadow domains
Subdomains
Exposed IP addresses
Public cloud buckets (e.g., AWS S3, Azure Blob)
Email servers and other network entry points
Example: Using tools like RiskProfiler Third-Party Risk Management, a security team uncovered 12 new subdomains linked to a vendor’s primary domain in 24 hours that weren’t disclosed during onboarding.
2. Risk Scoring & Tiering
The vendor risk triaging helps an organization prioritize vendors based on business impact, data access level, and threat exposure. It also takes into account their historical threat data, security practices, and attack trends to assess the vendor risk status.
RiskProfiler AI cyber threat intelligence framework analyzes signals such as external exposure, attack history, data criticality, and vendor function to auto-generate a risk score and assign vendors into tiers such as high, moderate, and low risk. It helps organizations prioritize threat response and allocate resources to handle threats.
Example: A marketing analytics vendor receives a high risk score due to its access to PII, multiple exposed cloud assets, and past breaches, placing it in the “high risk” tier. This triggers mandatory audits and enhanced controls.
3. Track History of Data Leaks and Security Breaches
RiskProfiler vendor risk assessment scans the security posture to detect the vendor’s history with security compromises and previous attack history. It allows organizations to get a complete insight into their threat exposure, level of compromise, and overall security preparedness.
RiskProfiler leverages its Dark Web Monitoring and Threat Intelligence APIs to collect all relevant data from deep and dark websites. It uses dark web scraping methods to scan underground forums, paste sites, and breach repositories for vendor mentions. Additionally, the cyber threat intelligence platform also cross-references vendor domains or emails in credential dumps or exploit kits.
Example: Dark web intel tools flag leaked credentials tied to a vendor’s CFO, discovered in a ransomware gang’s post on a popular forum. This insight leads to a proactive review of the vendor’s incident response posture.
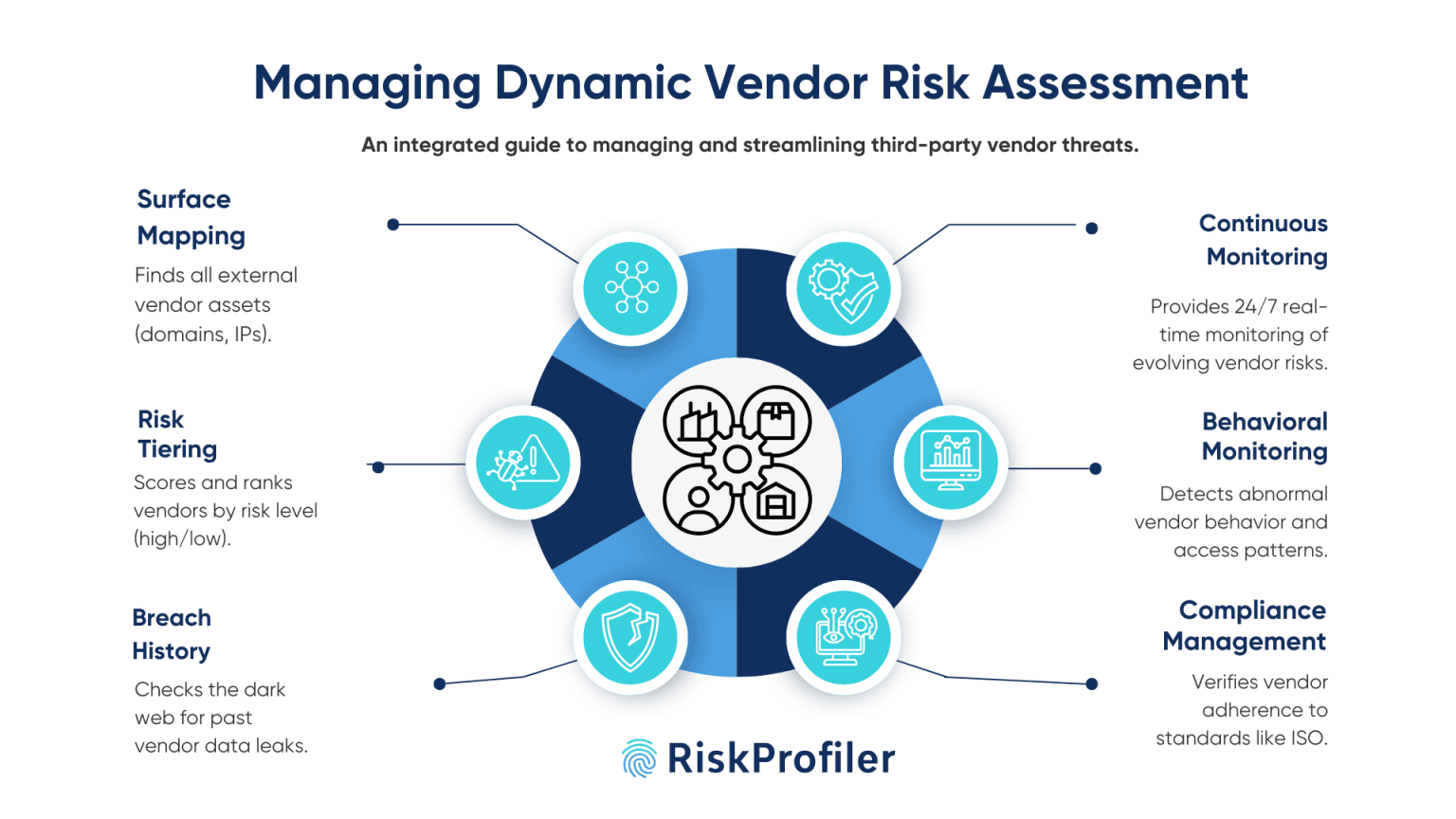
4. Regulatory Compliance Management
RiskProfiler assesses a vendor’s compliance status against industry-specific regulatory frameworks. It allows the business to evaluate the robustness of the vendor’s internal security measures and governance. The automated compliance management workflows also reduce the need for manual intervention, expedite the audit process, and keep the reports reliable at all times with continuous monitoring and updates.
To monitor your vendor’s compliance status, the tool allows you to send an automated vendor risk questionnaire integrated with frameworks like ISO 27001, SOC 2, HIPAA, NIST CSF, PCI DSS, or GDPR to collect accurate information on their encryption policies, patch management records, endpoint protection logs, and data security policies.
Example: A vendor’s responses indicate data encryption at rest, but the linked evidence reveals an outdated AES-128 implementation. This triggers a remediation workflow and adds conditional approval for short-term use.
5. Behavioral Monitoring
The cyber threat intelligence tool continuously monitors your vendor’s interactions with your system and creates a baseline of usual behavior. Any deviation from these regular behavioral or interaction patterns would activate the distribution of the risk questionnaire.
To monitor vendors’ interaction patterns, RiskProfiler uses User and Entity Behavior Analytics (UEBA). It helps the risk management platform monitor and identify irregular login times or geographies, unusual IP addresses requesting specific access, unusual volume of data exports, changes in service usage patterns, or email or message patterns uncharacteristic of usual activities.
Example: UEBA flags abnormal midnight access from an offshore IP to internal ticketing systems by a vendor support representative, violating the time-based access policy. In such instances, an investigation may reveal a compromised credential used for lateral movement.
6. Continuous Monitoring
RiskProfiler enables enterprises to maintain real-time visibility on evolving vendor risks post-onboarding. It is not limited only to the organization’s immediate vendors but also to fourth and fifth-party ecosystems.
To maintain continuous visibility across the ecosystem, it offers you automated monitoring dashboards allowing continuous visuals on attack surface scans, threat intelligence feeds, cloud compliance updates, and policy violation alerts. To enhance the accuracy and monitoring capabilities, Riskprofiler integrates with SIEM/SOAR platforms for escalation workflows.
Example: A previously approved low-risk HR vendor gets flagged due to new subdomain exposures with outdated SSL and a mention in a fresh breach dataset. The dashboard auto-generates a review ticket in Jira for the risk team.
Assessment Criteria | Description | Tool/Automation Example |
Digital Footprint Mapping | Discover vendor domains, IPs, and cloud assets | External Attack Surface Discovery |
Risk Scoring & Tiering | Calculate risk based on criticality & exposure | AI-Driven Risk Engine |
Threat Intelligence Check | Scan for breaches, leaks, or mentions in threat forums | Dark Web Monitoring Integration |
Security Controls Assessment | Validate vendor’s security policies and protocols | Automated Questionnaire + Evidence Pull |
Behavioral Monitoring | Detect unusual activities or traffic from vendor access | User & Entity Behavior Analytics (UEBA) |
Continuous Monitoring | Ongoing watch for changes in exposure or risk | Automated Monitoring Dashboards |
Final Thoughts,
In today’s threat landscape, a single blind spot in your vendor ecosystem can jeopardize your operations, data, and reputation. As cyber threats grow more advanced and regulatory scrutiny intensifies, businesses can no longer afford outdated approaches to third-party risk management.
Smart vendor risk assessment powered by automation and threat intelligence is not just a technological upgrade but a strategic necessity. It empowers teams to respond faster, comply better, and collaborate with vendors more securely.
By embedding intelligence into every stage of your vendor lifecycle, you move from reactive defense to proactive governance. In 2025 and beyond, this shift will define the difference between companies that merely survive and those that thrive.
It’s time to assess smarter, monitor continuously, and secure your supply chain with confidence. Enable a dynamic vendor risk assessment and compliance management protocols to stay ahead of all emerging supply chain risks.
Book a demo with a RiskProfiler expert today.
Global businesses today operate in a hyperconnected digital field, where an organization’s digital ecosystem is intricately fused with its vendors’ systems. Every time an organization onboards a new vendor, it risks exposing itself to potential threats lurking beyond its visibility zone. In 2025, relying on static, scheduled, questionnaire-based vendor assessments will no longer be enough to ensure third-party security. Organizations need intelligent, automated vendor risk assessments powered by AI-led cyber threat intelligence and real-time insights. These questionnaires are automated, streamlining the data collection and analysis process with an industry-specific assessment process.
Evolution of Third-Party Risks
Modern business operations are highly reliant on several SaaS tools, cloud services, and software programs to deliver comprehensive service benefits to clients. These may be the HR tools to keep track of employee data, productivity tools, hosting services, or payment applications linked to your website. All these external tools and applications expand your external attack surface and create an alternate pathway for attackers. Any risk or vulnerability in these ecosystems can lead threat actors to your infrastructure, causing severe damage.
Traditional methods like annual audits or spreadsheets are simply inadequate in this fast-evolving landscape. Threat posture evolves with every new connection or interaction, changing continuously, every day. To stay ahead, companies need smart, agile, and continuous ways to assess and monitor vendor risk. The answer lies in automation, AI, and actionable threat intelligence.
10 Reasons Smart Vendor Risk Assessments Are Essential in 2025
Smart vendor risk assessment workflows like RiskProfiler Vendor Risk Questionnaire make monitoring the supply chain risks comprehensive, continuous, and streamlined. The questionnaires can automate threat detection, verification, and initiate a collaboration process to remediate the hidden risks and exposures.
Continuous Monitoring Post-Onboarding
The vendor risk assessments are automated and integrated for continuous monitoring. Thus, these modules continue tracking the vendor attack surface as you onboard and integrate the vendor profile on the tool, allowing proactive surveillance.
Real-Time Risk Detection
Static, scheduled review processes miss these live updates on emerging threats. AI vendor risk assessments integrated with third-party risk management tools continuously monitor and surveil the third and fourth party ecosystem. Thus, it updates the risk scores dynamically as new vulnerabilities or threat activity is discovered, keeping the internal security team informed on threats in real-time.
Behavioral Anomaly Detection
AI vendor assessments monitor and detect suspicious activities on vendor threat posture with proactive modules and identification capabilities. In the event of deviation from the normal behavioral baseline, the questionnaire modules get activated and distribute a new assessment to the vendor in order to collect real-time intel and also alert the supplier of potential threats.
Threat Intelligence Integration
AI vendor risk assessments are integrated with sophisticated third-party risk management, external attack surface management, brand risk protection, and dark web threat monitoring protocols. Such collaboration allows the tool to collect comprehensive data on all possible vendor threat concerns and help them discern the cause and origin of the related threats.
Vendor Tiering & Prioritization
The vendor risk assessments collect data on your third and fourth party security postures, analyze the data against real-life industry standards and compliance frameworks. This allows it to prepare a baseline and determine the vendor’s risk threshold. This data provides the internal security team with a clear visual of each vendor’s security posture, risk status, and prepares a risk tiering with high, moderate, and low-risk vendors for simplified prioritization, onboarding, and decision-making process.

Faster Incident Response
Third-party risk questionnaires allow for fast detection as a threat emerges on a vendor system. These continuous monitoring capabilities provide organizations with the benefit of detecting vendor risk as it occurs, giving them crucial time to isolate and quarantine the system before the threat can reach their system.
Improved Audit Readiness
This questionnaire collects contextual data on threat origin, behavior, attack patterns, and targets with a timeline. This helps generate a detailed, structured threat report for identifying potential security gaps in third-party infrastructure and addressing them promptly.
Extended Third-Party Risks Visibility
Vendor risk questionnaires not only grant you visibility into your vendors. It allows continuous monitoring across your vendor’s supply chain simultaneously. This strengthens your security posture, offers truly comprehensive alertness against cyber attacks, and keeps you ahead of all potential attack vectors.
Strategic Vendor Relationships
The comprehensive visibility, threat preparedness, and streamlined compliance management allow organizations to maintain a transparent collaboration between suppliers and partners. It also allows fast communication with streamlined threat response, for proactive protection against vulnerabilities and malicious elements.
Enhance Efficiency & Reduce Human Error
AI vendor questionnaires streamline vendor attack surface monitoring, threat posture verification, compliance assessment, and the review process with automation. It reduces the time required for manual data collection, saves time otherwise wasted in scheduling and coordination, and removes the chances of human error.
Key Components of Third-Party Risk Assessments

Third-party risk assessments or vendor risk assessments are conducted to study and analyze the underlying risk thresholds across multiple sectors in a vendor ecosystem. The key components of such risk vectors include operational risk, third-party exposures, risk introduced through partners and subsidiaries, reputational risks, financial risks, data privacy risks, system exposures, and regulatory risks.
As part of the third-party risk assessments, the security tools monitor the breach vectors, security gaps, and risk elements that can pose threats or allow unauthorized access. In the context of the detection and analysis protocols, the tools measure the IT network and systems, access privileges, and operational protocols to detect and analyze the security exposures and exposure severity in their ecosystem.
However, it is important to ensure that the results of vendor risk assessments are updated at all times for them to be reliable and not a relic. This is why it is essential to choose a smart, dynamic questionnaire like RiskProfiler VRA, which gets activated with the slightest changes to the vendor’s security posture. It ensures your security team is updated on exposures emerging on the supply chain in advance, allowing immediate response and remediation before the threats can reach your organization.
Managing Dynamic Vendor Risk Assessment: A RiskProfiler Guide
A third-party risk assessment framework like RiskProfiler integrates multiple threat modules and security practices to accurately monitor, analyze, and detect vendor threats lurking in one’s supply chain ecosystem. Here, we will show you how the RiskProfiler Vendor Risk Questionnaire streamlines the threat management process.
1. External Attack Surface Mapping
RiskProfiler offers you complete visibility into a vendor’s public-facing digital assets, such as domains, IP ranges, and cloud infrastructure. It monitors all external assets, tools, and exposures for comprehensive threat mapping.
With the initiation of an external attack surface monitoring, it crawls the internet and passive DNS records to catalogue all associated digital assets of a vendor. These digital assets include:
Primary and shadow domains
Subdomains
Exposed IP addresses
Public cloud buckets (e.g., AWS S3, Azure Blob)
Email servers and other network entry points
Example: Using tools like RiskProfiler Third-Party Risk Management, a security team uncovered 12 new subdomains linked to a vendor’s primary domain in 24 hours that weren’t disclosed during onboarding.
2. Risk Scoring & Tiering
The vendor risk triaging helps an organization prioritize vendors based on business impact, data access level, and threat exposure. It also takes into account their historical threat data, security practices, and attack trends to assess the vendor risk status.
RiskProfiler AI cyber threat intelligence framework analyzes signals such as external exposure, attack history, data criticality, and vendor function to auto-generate a risk score and assign vendors into tiers such as high, moderate, and low risk. It helps organizations prioritize threat response and allocate resources to handle threats.
Example: A marketing analytics vendor receives a high risk score due to its access to PII, multiple exposed cloud assets, and past breaches, placing it in the “high risk” tier. This triggers mandatory audits and enhanced controls.
3. Track History of Data Leaks and Security Breaches
RiskProfiler vendor risk assessment scans the security posture to detect the vendor’s history with security compromises and previous attack history. It allows organizations to get a complete insight into their threat exposure, level of compromise, and overall security preparedness.
RiskProfiler leverages its Dark Web Monitoring and Threat Intelligence APIs to collect all relevant data from deep and dark websites. It uses dark web scraping methods to scan underground forums, paste sites, and breach repositories for vendor mentions. Additionally, the cyber threat intelligence platform also cross-references vendor domains or emails in credential dumps or exploit kits.
Example: Dark web intel tools flag leaked credentials tied to a vendor’s CFO, discovered in a ransomware gang’s post on a popular forum. This insight leads to a proactive review of the vendor’s incident response posture.

4. Regulatory Compliance Management
RiskProfiler assesses a vendor’s compliance status against industry-specific regulatory frameworks. It allows the business to evaluate the robustness of the vendor’s internal security measures and governance. The automated compliance management workflows also reduce the need for manual intervention, expedite the audit process, and keep the reports reliable at all times with continuous monitoring and updates.
To monitor your vendor’s compliance status, the tool allows you to send an automated vendor risk questionnaire integrated with frameworks like ISO 27001, SOC 2, HIPAA, NIST CSF, PCI DSS, or GDPR to collect accurate information on their encryption policies, patch management records, endpoint protection logs, and data security policies.
Example: A vendor’s responses indicate data encryption at rest, but the linked evidence reveals an outdated AES-128 implementation. This triggers a remediation workflow and adds conditional approval for short-term use.
5. Behavioral Monitoring
The cyber threat intelligence tool continuously monitors your vendor’s interactions with your system and creates a baseline of usual behavior. Any deviation from these regular behavioral or interaction patterns would activate the distribution of the risk questionnaire.
To monitor vendors’ interaction patterns, RiskProfiler uses User and Entity Behavior Analytics (UEBA). It helps the risk management platform monitor and identify irregular login times or geographies, unusual IP addresses requesting specific access, unusual volume of data exports, changes in service usage patterns, or email or message patterns uncharacteristic of usual activities.
Example: UEBA flags abnormal midnight access from an offshore IP to internal ticketing systems by a vendor support representative, violating the time-based access policy. In such instances, an investigation may reveal a compromised credential used for lateral movement.
6. Continuous Monitoring
RiskProfiler enables enterprises to maintain real-time visibility on evolving vendor risks post-onboarding. It is not limited only to the organization’s immediate vendors but also to fourth and fifth-party ecosystems.
To maintain continuous visibility across the ecosystem, it offers you automated monitoring dashboards allowing continuous visuals on attack surface scans, threat intelligence feeds, cloud compliance updates, and policy violation alerts. To enhance the accuracy and monitoring capabilities, Riskprofiler integrates with SIEM/SOAR platforms for escalation workflows.
Example: A previously approved low-risk HR vendor gets flagged due to new subdomain exposures with outdated SSL and a mention in a fresh breach dataset. The dashboard auto-generates a review ticket in Jira for the risk team.
Assessment Criteria | Description | Tool/Automation Example |
Digital Footprint Mapping | Discover vendor domains, IPs, and cloud assets | External Attack Surface Discovery |
Risk Scoring & Tiering | Calculate risk based on criticality & exposure | AI-Driven Risk Engine |
Threat Intelligence Check | Scan for breaches, leaks, or mentions in threat forums | Dark Web Monitoring Integration |
Security Controls Assessment | Validate vendor’s security policies and protocols | Automated Questionnaire + Evidence Pull |
Behavioral Monitoring | Detect unusual activities or traffic from vendor access | User & Entity Behavior Analytics (UEBA) |
Continuous Monitoring | Ongoing watch for changes in exposure or risk | Automated Monitoring Dashboards |
Final Thoughts,
In today’s threat landscape, a single blind spot in your vendor ecosystem can jeopardize your operations, data, and reputation. As cyber threats grow more advanced and regulatory scrutiny intensifies, businesses can no longer afford outdated approaches to third-party risk management.
Smart vendor risk assessment powered by automation and threat intelligence is not just a technological upgrade but a strategic necessity. It empowers teams to respond faster, comply better, and collaborate with vendors more securely.
By embedding intelligence into every stage of your vendor lifecycle, you move from reactive defense to proactive governance. In 2025 and beyond, this shift will define the difference between companies that merely survive and those that thrive.
It’s time to assess smarter, monitor continuously, and secure your supply chain with confidence. Enable a dynamic vendor risk assessment and compliance management protocols to stay ahead of all emerging supply chain risks.
Book a demo with a RiskProfiler expert today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



