Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


What is Shadow IT in Cybersecurity? A Guide to Mitigate Risks
What is Shadow IT in Cybersecurity? A Guide to Mitigate Risks
Picture this: an organization’s internal data suddenly appears on a dark web marketplace. The internal SOC team scrambles for missed alerts, only to recover nothing. The firewall is intact.
Read Time
7 min read
Posted On
Aug 28, 2025
Social Media
Picture this: an organization’s internal data suddenly appears on a dark web marketplace. The internal SOC team scrambles for missed alerts, only to recover nothing. The firewall is intact. No vulnerability scans show abnormalities. Then what went wrong? A deeper, more extensive investigation unveils a single abandoned dev environment or an exposed GitHub code repository that was left unmonitored, unpatched, and forgotten. This is the reality of Shadow IT assets in 2025.
For organizations worldwide, the mandate to protect their digital environment from breaches has become far more complex. It’s no longer limited to what is visible on a dashboard. It’s about what slips through the traditional detection and security protocols. Unknown assets, misconfigured storage units, forgotten subdomains, and unmanaged cloud services have become the primary targets for cybercriminals. As the organizations scale, with every new digital project, marketing campaign, or third-party integration, shadow IT risks multiply, expanding the attack surface along with the corresponding threats.
What is Shadow IT Asset in Cybersecurity?
Shadow IT assets are the cloud, SaaS, API, and other related integrations added to an organization’s environment with the permission or knowledge of the institutional tech or security team. Due to its unknown status, these cloud assets remain excluded from regular patches, updates, or security audits, leaving them vulnerable to external threats and exposures. In today’s advanced cybercrime scenario, such exposures are easily detected with sophisticated scans and threat detection tools. Once identified, attackers manipulate these shadow IT assets to gain access to your system, implant stealth spyware, and escalate permissions, which results in major security incidents.
Why Do Shadow IT Assets Pose Critical Business Risks in 2025?
In the rapidly growing cloud space, several integrations can be added to the environment ecosystem without ever needing IT assistance. It is a matter of allowing email access and a cloud sign-in, and another productivity tool or gen AI platform is connected to your organization’s system.
Whether it’s an abandoned subdomain pointing to exposed infrastructure, a forgotten third-party marketing tool still collecting customer data, or a misconfigured cloud storage bucket, shadow IT introduces several critical business risks. They act as unguarded entry points on your digital ecosystem.
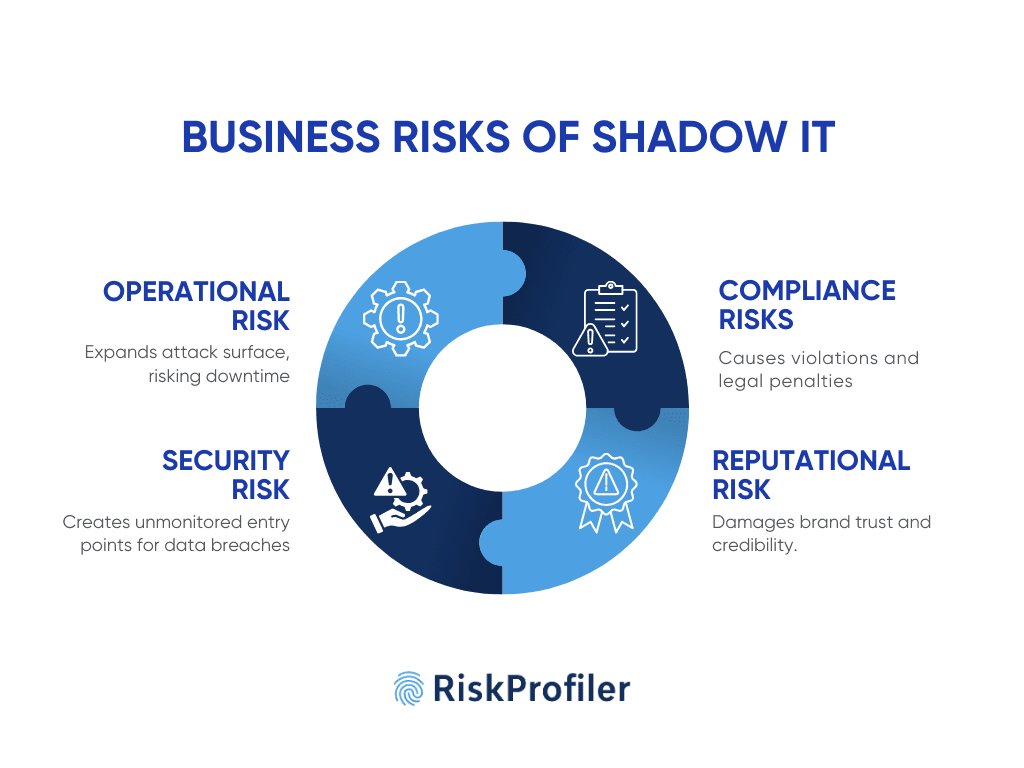
Operational Risk
Unapproved cloud assets, applications, or integrations expand the organization’s attack surface without the knowledge of the tech team. As such assets lie outside the scope of regular updates and security reviews, suspicious activities surrounding these tools can go unnoticed. Such threats often damage the operation’s integrity, result in downtime, or can escalate to a large-scale DDoS attack.
Security Risk
Shadow IT assets and abandoned cloud integrations often operate outside pre-defined IT and security oversight. As a result, these assets lack critical updates, access controls, and credential hygiene practices otherwise monitored across the business. These system blind spots become primary entry points for attackers to infiltrate networks, share phishing kits, implement malware tools, or move laterally across systems by bridging vulnerabilities, compromising sensitive data, and escalating breaches before detection is even possible.
Reputational Risk
When cyberattacks originate from forgotten domains or abandoned IT assets, stakeholders consider this a sign of negligence, even if the breach arises from third or fourth-party systems. Such incidents erode trust, damage brand credibility, and raise concerns about governance, especially when outdated tools remain publicly accessible or unmonitored for a long time.
Compliance Risks
Shadow IT and abandoned digital assets often fall outside of regulatory oversight and compliance analysis. This can lead to violations of data protection laws, industry regulations, and contractual obligations. Unmonitored integration, approved SaaS tools, or unpatched third-party integrations can mishandle sensitive data or lack audit trails, exposing organizations to penalties, legal action, and scrutiny from regulators, especially in sectors like healthcare, energy, finance, etc., that are governed by strict compliance mandates.
How Should MSSPs and MTDRs Evolve to Guard the External Attack Surface?
Managed Security Service Providers and Managed Threat Detection and Response solutions need to evolve their threat detection, analysis, and response methods to fit the demands of the fast-moving cloud scenario. The SaaS tools or a browser extension can be integrated in a moment, do not require tech oversight, and thus can broaden the attack perimeter without notice.
This is why, to truly support business resilience without risking security exposure, they need to stay ahead of risks by maintaining clear visibility into:
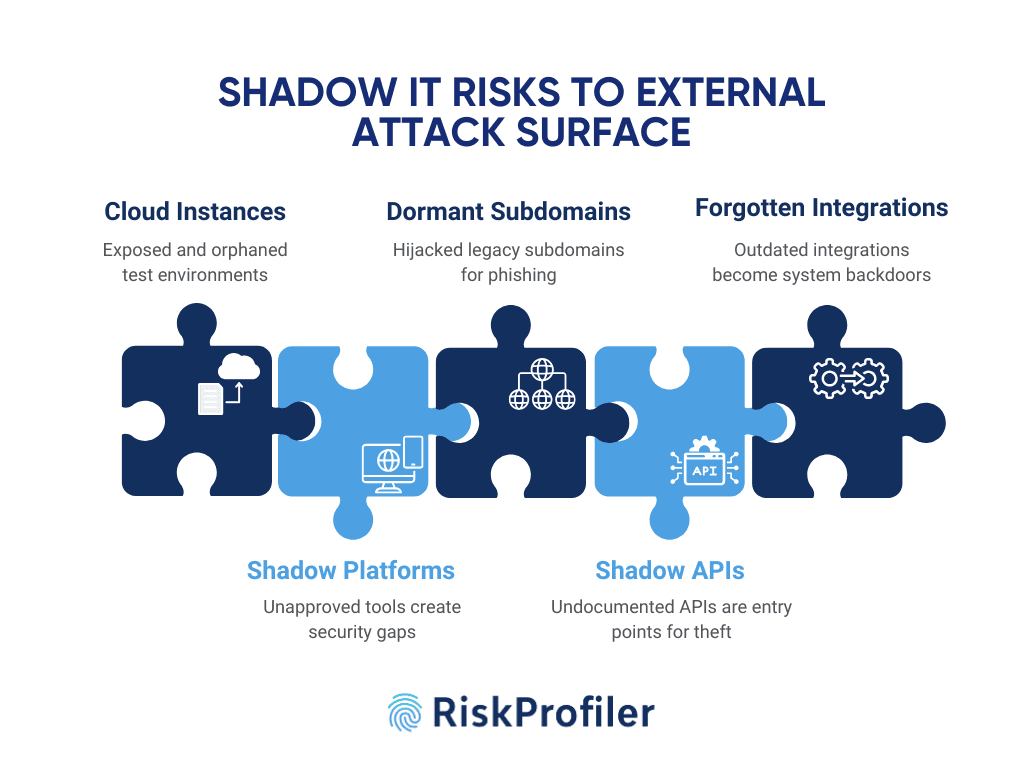
Public Cloud Instances: Organizations often spin up new environments for testing, development, or temporary projects, without following proper decommissioning protocol once they serve their purpose. These orphaned instances can remain exposed, unmonitored, and vulnerable to exploitation.
Unregistered SaaS and IaaS Platforms: Employees from different departments and diverse work portfolios frequently adopt SaaS tools without IT oversight. These platforms, without proper oversight, are given access to organizational data, may lack proper identity controls, creating gaps in compliance and security posture.
Dormant but Active Subdomains: Subdomains tied to legacy campaigns or expired services often remain live, even if unused. Attackers can hijack these assets to host phishing pages or malware, leveraging the trust of the parent domain.
Shadow APIs and Unauthenticated Web Assets: APIs are the connective tissue of modern applications. However, when left undocumented or unauthenticated, APIs can become silent entry points for data exfiltration or lead to service disruption.
Forgotten Third-party Integrations and Redirects: Integrations with vendors, partners, or marketing platforms may remain live long after their relevance. If left unchecked, they can serve as backdoors into sensitive systems or expose user data.
By incorporating continuous attack surface monitoring into their service offerings, MSSPs and MTDRs can deliver measurable reductions in dwell time and improve incident readiness. Shadow IT is not just hard to see; it is the first thing that must be seen.
Closing The Visibility Gap: From Shadow IT Asset Discovery to Threat Prevention
Most organizations feel confident in their threat visibility and firewall defenses. Yet research consistently shows that nearly 30% of externally exposed assets remain invisible to internal teams. These aren’t obscure or irrelevant; they’re often active, accessible, and vulnerable.
For example, consider the login pages of legacy tools still accessible online, or marketing microsites hosted on third-party CDNs that were never properly decommissioned. Additionally, the growing number of shadow SaaS platforms quietly integrated via 0Auth or SSO, and cloud services spun up by developers without security sign-off, only expands the problem. These assets live outside the regular SOC monitoring but quietly expand the attack surface.
Traditional vulnerability scanners and CSPM tools can only assess what they are actively scanning for. However, these undisclosed, abandoned, or forgotten assets do not make the audit list. That’s why MSSPs must evolve their approach and partner with platforms that offer:
Automated Asset Inventory Across All Subsidiaries and Domains
AI-driven Discovery of Lookalike Domains and Typo Squatting
DNS, Certificate, and IP Block Monitoring
Prioritized Alerts on Newly Discovered Public-Facing Endpoints
Integration with Cyber Threat Intelligence Tools for Preemptive Risk Remediation
Bridging the visibility gap isn’t just about better tools; it is about implementing a smarter strategy. The shadow IT assets you do not know about are the ones attackers count on.
Case Study: What Happens When Shadow IT Assets Go Active
In Q2 2025, a mid-sized financial services firm was targeted through a staging server that their development team had deployed via a cloud provider in South America. The server, forgotten and misconfigured, was later indexed by search engines. Threat actors leveraged it for credential harvesting by cloning the login page and distributing phishing links to customers. The root cause? Shadow IT visibility failure.
This is no longer a hypothetical threat. It’s a recurring pattern across industries.
RiskProfiler: Turning Shadow IT Risks into Strategic Visibility
Shadow IT assets such as unmonitored domains, unsanctioned SaaS tools, rogue cloud endpoints, etc., pose one of the most persistent external security risks to modern organizations. For CISOs, MSSPs, and MTDR providers, these blind spots not only expand the external attack surface but also create compliance, brand, and operational exposures.
RiskProfiler’s cyber threat intelligence platform delivers a unified solution dedicated to uncover, analyze, and remediate Shadow IT, transforming fragmented visibility into actionable intelligence.
Comprehensive Shadow IT Risk Discovery Across External Attack Surface
Through External Attack Surface Management, Cloud Threat Exposure Management, and Third-Party Risk Management Modules, RiskProfiler continuously maps all known and unknown internet-facing assets, including shadow domains, rogue servers, and unmanaged SaaS instances. This covers not only the attack surface of your enterprise but also subsidiaries, supply chain partners, and vendor ecosystems. The result is a complete threat landscape view, enabling rapid detection, AI-driven risk scoring, and automated mitigation.
Continuous Shadow IT Risks Monitoring
With its Cloud Threat Exposure Management and Access Intelligence modules, RiskProfiler ensures continuous, round-the-clock surveillance of emerging Shadow IT risks. It actively monitors for newly exposed domains and subdomains, detects unauthorized or unregistered SaaS applications, and identifies misconfigured access points as well as leaked credentials. Additionally, it keeps a close watch on the misconfigured cloud-native storage units and APIs, areas often overlooked but highly vulnerable to external attacks and breaches. The platform also provides real-time alerts with contextual information on the concerned threats, allowing for fast response and mitigation of the risks.
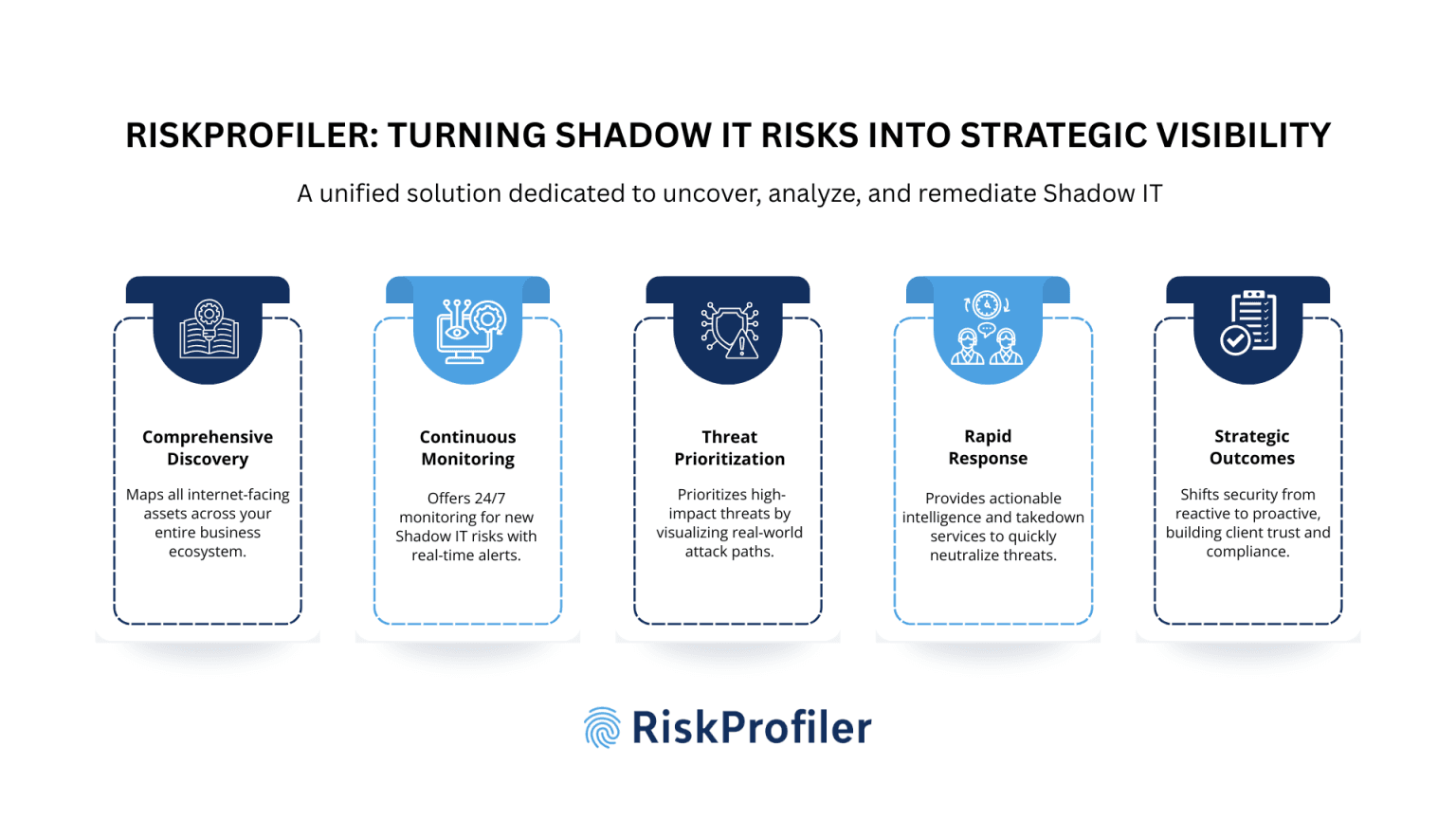
Prioritized Shadow IT Risks Context
Using Attack Path Analysis, RiskProfiler correlates shadow assets with real-world exploitation trends. This context enables security leaders to quickly separate low-risk anomalies from high-impact threats tied to phishing kits, data leakage, and malware infrastructure. It also helps security engineers visualize the paths of lateral movements, involved attack chains, and asset exposures in real-time, enabling focused mitigation and preventing escalation.
Actionable Intelligence & Rapid Response
RiskProfiler’s cyber threat intelligence platform empowers rapid detection with contextual insights and strategic mitigation plans. With integrated takedown services, DNS hardening recommendations, and access policy insights, organizations and MSSPs can quickly neutralize Shadow IT exposures. This ensures faster remediation, reduced dwell time, and minimized business impact.
Strategic Outcomes for CISOs & MSSPs
By integrating RiskProfiler’s unified threat intelligence platform into their workflows, MSSPs and MTDR solution providers can shift from reactive incident handling to proactive external threat surface management. This strengthens client trust, enhances compliance alignment, and unlocks new service offerings that directly address Shadow IT exposures.
Conclusion
Shadow IT risks are a growing concern for the security leaders, CISOs, MSSPs, and MTDR service providers. Organizations and SOC teams can not secure assets that are invisible to their scans and do not appear on audit reports. In most cases, they are discovered in post-breach investigations, when it is too late to rectify.
This is why it is important to implement a proactive strategy that can discover shadow IT assets before they are known to attackers or can be used in a breach as an entry point. RiskProfiler’s cyber threat intelligence platform discovers all unknown assets, including abandoned domains, unapproved SaaS tools, unpatched integrations, and misconfigured API or cloud storage units.
Discover how RiskProfiler uncovers hidden Shadow IT exposures before attackers do. Book a Demo today and see your external attack surface in real-time.
Picture this: an organization’s internal data suddenly appears on a dark web marketplace. The internal SOC team scrambles for missed alerts, only to recover nothing. The firewall is intact. No vulnerability scans show abnormalities. Then what went wrong? A deeper, more extensive investigation unveils a single abandoned dev environment or an exposed GitHub code repository that was left unmonitored, unpatched, and forgotten. This is the reality of Shadow IT assets in 2025.
For organizations worldwide, the mandate to protect their digital environment from breaches has become far more complex. It’s no longer limited to what is visible on a dashboard. It’s about what slips through the traditional detection and security protocols. Unknown assets, misconfigured storage units, forgotten subdomains, and unmanaged cloud services have become the primary targets for cybercriminals. As the organizations scale, with every new digital project, marketing campaign, or third-party integration, shadow IT risks multiply, expanding the attack surface along with the corresponding threats.
What is Shadow IT Asset in Cybersecurity?
Shadow IT assets are the cloud, SaaS, API, and other related integrations added to an organization’s environment with the permission or knowledge of the institutional tech or security team. Due to its unknown status, these cloud assets remain excluded from regular patches, updates, or security audits, leaving them vulnerable to external threats and exposures. In today’s advanced cybercrime scenario, such exposures are easily detected with sophisticated scans and threat detection tools. Once identified, attackers manipulate these shadow IT assets to gain access to your system, implant stealth spyware, and escalate permissions, which results in major security incidents.
Why Do Shadow IT Assets Pose Critical Business Risks in 2025?
In the rapidly growing cloud space, several integrations can be added to the environment ecosystem without ever needing IT assistance. It is a matter of allowing email access and a cloud sign-in, and another productivity tool or gen AI platform is connected to your organization’s system.
Whether it’s an abandoned subdomain pointing to exposed infrastructure, a forgotten third-party marketing tool still collecting customer data, or a misconfigured cloud storage bucket, shadow IT introduces several critical business risks. They act as unguarded entry points on your digital ecosystem.

Operational Risk
Unapproved cloud assets, applications, or integrations expand the organization’s attack surface without the knowledge of the tech team. As such assets lie outside the scope of regular updates and security reviews, suspicious activities surrounding these tools can go unnoticed. Such threats often damage the operation’s integrity, result in downtime, or can escalate to a large-scale DDoS attack.
Security Risk
Shadow IT assets and abandoned cloud integrations often operate outside pre-defined IT and security oversight. As a result, these assets lack critical updates, access controls, and credential hygiene practices otherwise monitored across the business. These system blind spots become primary entry points for attackers to infiltrate networks, share phishing kits, implement malware tools, or move laterally across systems by bridging vulnerabilities, compromising sensitive data, and escalating breaches before detection is even possible.
Reputational Risk
When cyberattacks originate from forgotten domains or abandoned IT assets, stakeholders consider this a sign of negligence, even if the breach arises from third or fourth-party systems. Such incidents erode trust, damage brand credibility, and raise concerns about governance, especially when outdated tools remain publicly accessible or unmonitored for a long time.
Compliance Risks
Shadow IT and abandoned digital assets often fall outside of regulatory oversight and compliance analysis. This can lead to violations of data protection laws, industry regulations, and contractual obligations. Unmonitored integration, approved SaaS tools, or unpatched third-party integrations can mishandle sensitive data or lack audit trails, exposing organizations to penalties, legal action, and scrutiny from regulators, especially in sectors like healthcare, energy, finance, etc., that are governed by strict compliance mandates.
How Should MSSPs and MTDRs Evolve to Guard the External Attack Surface?
Managed Security Service Providers and Managed Threat Detection and Response solutions need to evolve their threat detection, analysis, and response methods to fit the demands of the fast-moving cloud scenario. The SaaS tools or a browser extension can be integrated in a moment, do not require tech oversight, and thus can broaden the attack perimeter without notice.
This is why, to truly support business resilience without risking security exposure, they need to stay ahead of risks by maintaining clear visibility into:

Public Cloud Instances: Organizations often spin up new environments for testing, development, or temporary projects, without following proper decommissioning protocol once they serve their purpose. These orphaned instances can remain exposed, unmonitored, and vulnerable to exploitation.
Unregistered SaaS and IaaS Platforms: Employees from different departments and diverse work portfolios frequently adopt SaaS tools without IT oversight. These platforms, without proper oversight, are given access to organizational data, may lack proper identity controls, creating gaps in compliance and security posture.
Dormant but Active Subdomains: Subdomains tied to legacy campaigns or expired services often remain live, even if unused. Attackers can hijack these assets to host phishing pages or malware, leveraging the trust of the parent domain.
Shadow APIs and Unauthenticated Web Assets: APIs are the connective tissue of modern applications. However, when left undocumented or unauthenticated, APIs can become silent entry points for data exfiltration or lead to service disruption.
Forgotten Third-party Integrations and Redirects: Integrations with vendors, partners, or marketing platforms may remain live long after their relevance. If left unchecked, they can serve as backdoors into sensitive systems or expose user data.
By incorporating continuous attack surface monitoring into their service offerings, MSSPs and MTDRs can deliver measurable reductions in dwell time and improve incident readiness. Shadow IT is not just hard to see; it is the first thing that must be seen.
Closing The Visibility Gap: From Shadow IT Asset Discovery to Threat Prevention
Most organizations feel confident in their threat visibility and firewall defenses. Yet research consistently shows that nearly 30% of externally exposed assets remain invisible to internal teams. These aren’t obscure or irrelevant; they’re often active, accessible, and vulnerable.
For example, consider the login pages of legacy tools still accessible online, or marketing microsites hosted on third-party CDNs that were never properly decommissioned. Additionally, the growing number of shadow SaaS platforms quietly integrated via 0Auth or SSO, and cloud services spun up by developers without security sign-off, only expands the problem. These assets live outside the regular SOC monitoring but quietly expand the attack surface.
Traditional vulnerability scanners and CSPM tools can only assess what they are actively scanning for. However, these undisclosed, abandoned, or forgotten assets do not make the audit list. That’s why MSSPs must evolve their approach and partner with platforms that offer:
Automated Asset Inventory Across All Subsidiaries and Domains
AI-driven Discovery of Lookalike Domains and Typo Squatting
DNS, Certificate, and IP Block Monitoring
Prioritized Alerts on Newly Discovered Public-Facing Endpoints
Integration with Cyber Threat Intelligence Tools for Preemptive Risk Remediation
Bridging the visibility gap isn’t just about better tools; it is about implementing a smarter strategy. The shadow IT assets you do not know about are the ones attackers count on.
Case Study: What Happens When Shadow IT Assets Go Active
In Q2 2025, a mid-sized financial services firm was targeted through a staging server that their development team had deployed via a cloud provider in South America. The server, forgotten and misconfigured, was later indexed by search engines. Threat actors leveraged it for credential harvesting by cloning the login page and distributing phishing links to customers. The root cause? Shadow IT visibility failure.
This is no longer a hypothetical threat. It’s a recurring pattern across industries.
RiskProfiler: Turning Shadow IT Risks into Strategic Visibility
Shadow IT assets such as unmonitored domains, unsanctioned SaaS tools, rogue cloud endpoints, etc., pose one of the most persistent external security risks to modern organizations. For CISOs, MSSPs, and MTDR providers, these blind spots not only expand the external attack surface but also create compliance, brand, and operational exposures.
RiskProfiler’s cyber threat intelligence platform delivers a unified solution dedicated to uncover, analyze, and remediate Shadow IT, transforming fragmented visibility into actionable intelligence.
Comprehensive Shadow IT Risk Discovery Across External Attack Surface
Through External Attack Surface Management, Cloud Threat Exposure Management, and Third-Party Risk Management Modules, RiskProfiler continuously maps all known and unknown internet-facing assets, including shadow domains, rogue servers, and unmanaged SaaS instances. This covers not only the attack surface of your enterprise but also subsidiaries, supply chain partners, and vendor ecosystems. The result is a complete threat landscape view, enabling rapid detection, AI-driven risk scoring, and automated mitigation.
Continuous Shadow IT Risks Monitoring
With its Cloud Threat Exposure Management and Access Intelligence modules, RiskProfiler ensures continuous, round-the-clock surveillance of emerging Shadow IT risks. It actively monitors for newly exposed domains and subdomains, detects unauthorized or unregistered SaaS applications, and identifies misconfigured access points as well as leaked credentials. Additionally, it keeps a close watch on the misconfigured cloud-native storage units and APIs, areas often overlooked but highly vulnerable to external attacks and breaches. The platform also provides real-time alerts with contextual information on the concerned threats, allowing for fast response and mitigation of the risks.

Prioritized Shadow IT Risks Context
Using Attack Path Analysis, RiskProfiler correlates shadow assets with real-world exploitation trends. This context enables security leaders to quickly separate low-risk anomalies from high-impact threats tied to phishing kits, data leakage, and malware infrastructure. It also helps security engineers visualize the paths of lateral movements, involved attack chains, and asset exposures in real-time, enabling focused mitigation and preventing escalation.
Actionable Intelligence & Rapid Response
RiskProfiler’s cyber threat intelligence platform empowers rapid detection with contextual insights and strategic mitigation plans. With integrated takedown services, DNS hardening recommendations, and access policy insights, organizations and MSSPs can quickly neutralize Shadow IT exposures. This ensures faster remediation, reduced dwell time, and minimized business impact.
Strategic Outcomes for CISOs & MSSPs
By integrating RiskProfiler’s unified threat intelligence platform into their workflows, MSSPs and MTDR solution providers can shift from reactive incident handling to proactive external threat surface management. This strengthens client trust, enhances compliance alignment, and unlocks new service offerings that directly address Shadow IT exposures.
Conclusion
Shadow IT risks are a growing concern for the security leaders, CISOs, MSSPs, and MTDR service providers. Organizations and SOC teams can not secure assets that are invisible to their scans and do not appear on audit reports. In most cases, they are discovered in post-breach investigations, when it is too late to rectify.
This is why it is important to implement a proactive strategy that can discover shadow IT assets before they are known to attackers or can be used in a breach as an entry point. RiskProfiler’s cyber threat intelligence platform discovers all unknown assets, including abandoned domains, unapproved SaaS tools, unpatched integrations, and misconfigured API or cloud storage units.
Discover how RiskProfiler uncovers hidden Shadow IT exposures before attackers do. Book a Demo today and see your external attack surface in real-time.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



