Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


What is a Data Breach? Major Causes & Mitigation in 2025
What is a Data Breach? Major Causes & Mitigation in 2025
Do you think password and MFA make your organization’s security impenetrable? Then, it is time for you to think again!
Read Time
7 min read
Posted On
Aug 22, 2025
Social Media
Do you think password and MFA make your organization’s security impenetrable? Then, it is time for you to think again! Data breaches are a primary security concern for the finance, retail, healthcare, hospitality, and telecom sectors worldwide. With sophisticated tools and AI integrations, such security incidents have become increasingly difficult to detect, resulting in a wider blast radius and significant damage. According to the IBM Cost of a Data Breach Report 2025, the average cost of a data breach in the US is 10.22 million USD, which reflects a 9% rise from the previous year. Although organizations continue to invest in different enterprise data breach detection systems, firewalls, multi-factor authentication, and compliance audits, the attackers have broadened their limitation barrier to customers through these barriers easily. Modern phishing tools can use leaked credentials, deliver spoofed MFA codes, and gain access to your sensitive database, all the while confirming your belief in your security system even as they bypass your defenses.
The sophistication of external threats and data breach mechanisms complicates enterprise data breach detection. For leaders responsible for protecting organizational data, CISOs, security engineers, and CXOs, the challenge is not limited to preventing breaches. After being compromised, the most dangerous breaches are those that are unknown.
What are the major causes of data breaches?
These causes of data breaches may include credential leaks, misconfigured digital assets, unsecured login practices, shadow IT issues, security gaps in supply chains, unsecured endpoints, etc. When left unsecured without proper threat vigilance, cyber attackers can detect and exploit these endpoints to gain system access.
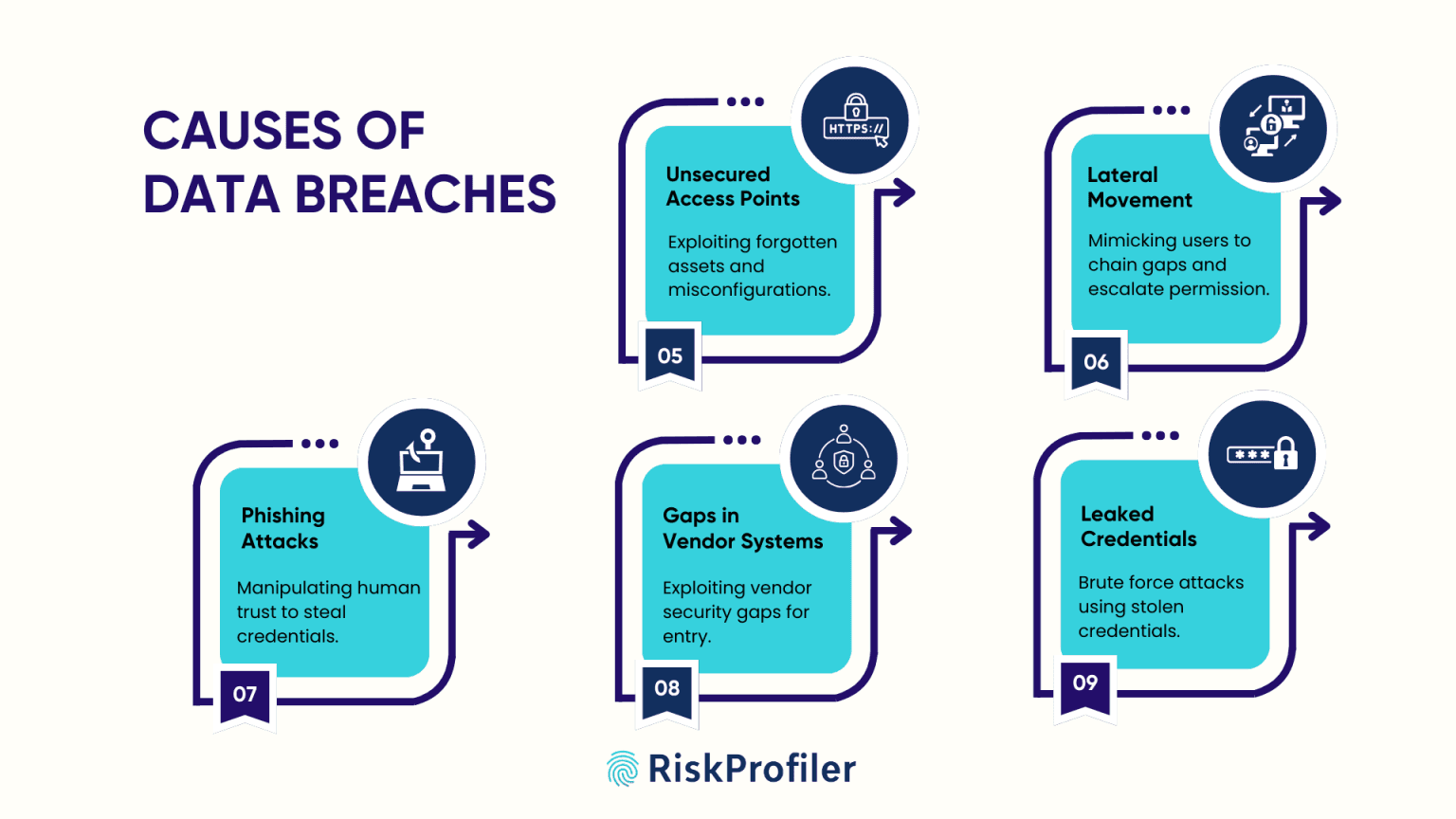
Unsecured Access Points
Most major data breaches often begin with seemingly benign access through a forgotten subdomain, a misconfigured cloud storage bucket, or an abandoned test environment that was not disposed of properly. Attackers discover these entry points during passive reconnaissance and can exploit these vulnerabilities to enter your system. To avoid such exposures and curb the threats at the root, security teams need continuous vigilance and the smart analysis power of cyber threat intelligence tools like RiskProfiler.
Whether it’s an abandoned subdomain pointing to exposed infrastructure, a forgotten third-party marketing tool still collecting customer data, or a misconfigured cloud storage bucket, shadow IT introduces several critical business risks. They act as unguarded entry points on your digital ecosystem.
Lateral Movement Attacks
Once the attackers build a baseline of usual interactions by monitoring keystrokes and other interaction patterns, they initiate the attack by mimicking interactions and escalating access permissions across different accounts, databases, and internal systems.
The lateral movements and gradual access acceleration take longer to be detected, increasing exposures, system vulnerabilities, and data leaks. Security tools like RiskProfiler that enable attack path simulation help you visualize these potential vulnerability chains and address the risks effectively.
Credential Breach and Harvesting Attacks
Credential breaches are widespread in today’s digital world, where stolen login details from SaaS tools, cloud platforms, and subscription-based services are traded across illegal forums and chat rooms. Login credentials are commonly compromised by weak passwords, phishing schemes, and large-scale harvesting attacks. By implementing proper password hygiene and monitoring access compromises with threat intelligence platforms, organizations can stay ahead of these security risks.
Security Gaps in Third-Party Systems
Your supply chain ecosystem is not a detached entity. Your organization’s security is entirely dependent upon the reliability of your vendor’s system in an interconnected digital ecosystem. Exposures, misconfigurations, leaked credentials, or security breaches in the vendor environment can expose your system if not detected on time. Incorporating a smart and proactive third-party risk management tool like RiskProfiler with your security protocols can help you with data breach detection in your supply chain before it becomes a threat to your operations and reputation.
Phishing and Social Engineering Attacks
Credential leaks and abuse remain one of the primary vehicles for cyberattacks against organizations across industries, according to the Verizon Data Breach Investigations Report, 2025. Phishing and social engineering attacks, the most commonly used tools behind credential harvesting, rely on manipulating human trust and urgency rather than exploiting a technical flaw, making data breach detection more difficult in these cases.
Furthermore, cyber threat actors commonly share proven phishing kits, spoofed login pages, and social engineering scripts across dark web forums. It allows malicious actors to transfer or steal your organization’s data, take over accounts, and compromise networks of interconnected systems.
Early Warning: Data Breach Signals You Might Be Missing
Organizations tend to characterize data breach signals as something rogue. Perhaps a syslog mistake or other emphasis on systems creation as part of their operating profile. Unless the indications of intrusions are seen in context, organizations can completely miss the initial signals of a potentially catastrophic breach, or mistakenly conclude that what’s happening is part of the normal, business-as-usual operations. An increase of failed logins from foreign IP addresses, requests for access to data from non-usual points of origin, abnormally high outbound traffic, or identified events of unusual privilege elevation might simply be seen as isolated signals unless it is confirmed with other incident reports.
Such warnings can get lost in the flood of data generated by modern enterprise systems or get ignored due to a lack of collaborative workflows between security silos. Without correlation and intelligent prioritization, threat symbols are ignored by your security team, leading to avoidable escalation and breach scenarios.
Data Breach Detection Practices for Early Response
When security teams function in silos, responsible for their discreet portion of infrastructure or data, they lack meaningful context that would connect correlation with causation. Modern cyber threat intelligence solutions like RiskProfiler aim to solve this communication problem and provide expansive visibility into the entire ecosystem, revealing vital context about adversary origin, intent, and behavior, with applicable insights to prevent attack or compromise. The following are some examples of practices to display threat detection and consequently understand cyberattacks in a more immediate and relevant manner.
External Attack Surface Management (EASM)
Your entire digital footprint is a part of your external attack surface. In such a large and expanding environment, assets can be overlooked or lost over time, resulting in security gaps. External attack surface management platforms, like RiskProfiler, constantly scan this massive external attack surface to detect all such abandoned, unlisted, or forgotten access points and give you a comprehensive threat view.
Additionally, they also help you discover suspicious DNS activities, uncharacteristic IP logins, certification status, misconfigured assets, and exposed code structures for holistic security. The tools help you detect threats on time, enabling you to respond to them before they escalate.
User and Entity Behavior Analytics (UEBA)
UEBA platforms create behavioral baselines based on user interactions analyzed over time to see the eventual patterns across teams, devices, applications, and regions. For example, when a user logs in from a location where he’s never logged in before, with the added anomaly that he has logged in at an unusual time, or a service account is making access requests that have no relation to his job duties, UEBA reports and isolates the atypical activity. On its own, this indicator is meaningless; it is the ability of UEBA to associate indicators of attack to determine the patterns of attacks that can often pinpoint insider attack, compromised credentials, or lateral stealth movement in the early steps of an attack.
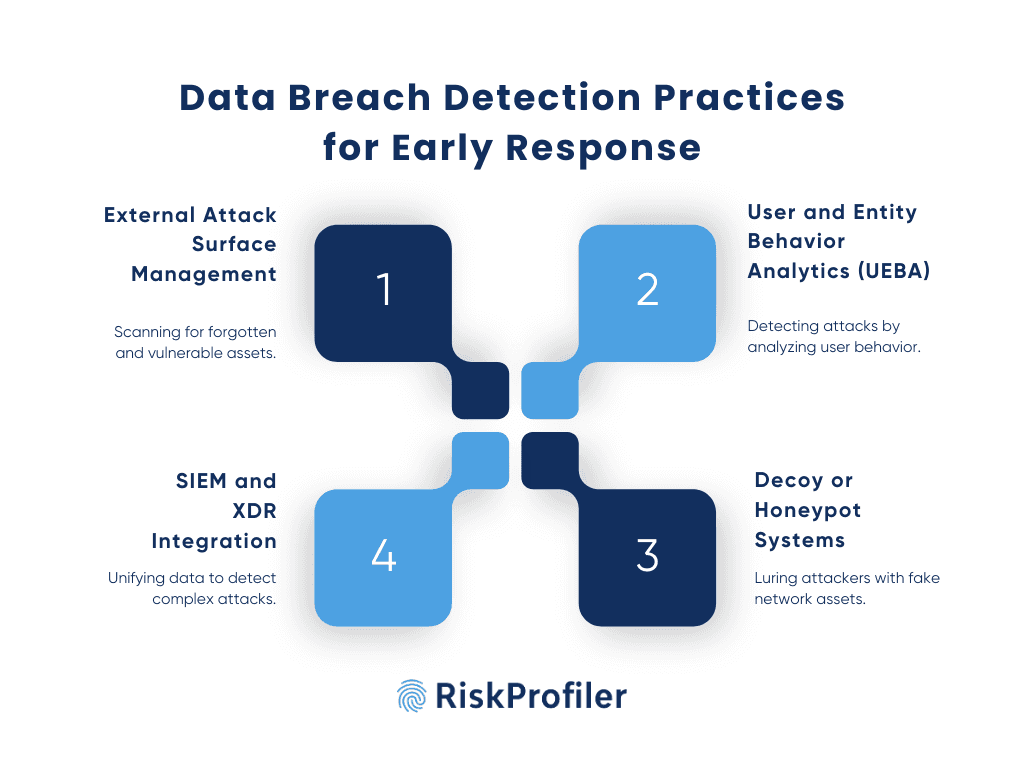
Decoy or Honeypot Systems
Deception technology creates and manages essentially fake assets in an organization’s network that have attributes of seemingly real, but false, credentials, databases, endpoints, and services dispersed across the organization. The decoys are designed to engage with cyber attackers and enable security teams to observe attack patterns and identify malicious actions in the network.
For instance, if attackers engage with a decoy by logging into a nonexistent admin panel or attempting to extract data from a baited database, it initiates alerts. The product leads to low-noise, high-fidelity threat detection that can, in most cases, alert the security team before they reach critical systems.
SIEM and XDR Integration
Security Information and Event Management (SIEM) systems are central to an enterprise’s monitoring strategy by collecting logs across networks, servers, applications, and cloud environments. Caught in this context is the growing diversity of modern cyberthreats, which often originate in vendor infrastructure and create attack paths through insecure endpoints by manipulating misconfigured assets.
To detect such multi-stage attacks, organizations are turning to Extended Detection and Response (XDR). XDR platforms integrate with SIEMs but go further by correlating findings across endpoints, identity providers, network traffic, and more. They provide a unified timeline of events, allowing analysts to trace attacks from origin to impact. Combined with automation and threat intelligence, SIEM + XDR integration becomes a powerful mechanism for early breach detection and faster incident response.
Why is proactive detection important for data breach prevention?
To secure your organization against digital adversaries and strengthen data breach prevention policies, you will need to discover exposures before attackers do, recognize their attack patterns, and fortify your ecosystem against their intrusion methods.
Red teaming and attack path simulations expose how a breach could unfold from an attacker’s perspective, revealing weaknesses that may go unnoticed during routine checks. Unified cyber threat intelligence tools like RiskProfiler also help you correlate security compromises across different operational areas to build a complete picture with correlation and context. Breach and attack simulation platforms reinforce this process by continuously emulating real-world attack scenarios to test and improve defenses.
By implementing these proactive threat monitoring, analysis, and detection methods with your security strategy, your organization can stay ahead of industry breach trends and cyber adversaries.
How Does RiskProfiler Enhance Enterprise Data Breach Detection?
RiskProfiler’s unified cyber threat intelligence tool is precisely engineered to proactively close the visibility and intelligence gaps that allow breaches to persist undetected. It integrates with existing security infrastructure to deliver contextual, real-time exposure intelligence that empowers faster decision-making and threat mitigation.
Effortless Integration with SIEM & XDR Systems
RiskProfiler integrates into your SIEM and XDR platforms easily to provide contextual intelligence from external and internal sources. Because it maps threat signals to assets and associated behavior, the platform provides specific, exposure-linked insights instead of generic indicators to drive defensible action. This enrichment of visibility allows better correlations, faster triage, and accurate detection of threats in your environment.
Monitoring for Brand Threats and Credential Exposures
Impersonated identities, credential breaches, and suspicious login behavior are precursory evidence of compromise. RiskProfiler’s brand threat intelligence provides continuous monitoring and gathers information on leaks, stolen or breached credentials, or any mention of an organization on the surface web, social media platforms, dark web, data dumps, and illegal chat room sites to create contextual evidence to prepare threat alerts. This helps security teams identify threats and remediate risks before the information can be leveraged by adversaries to gain unauthorized access to the system.
Asset Inventory and Endpoint Exposure Identification
RiskProfiler’s attack surface management tool continuously crawls your digital footprint and inventories everything, including unknown subdomains, unused APIs, exposed endpoints, and third-party integrations. It scores each asset based on exposure, patch status, and exploitability, for security teams to prioritize their response efforts in securing the exposures based on their financial and technical impact.
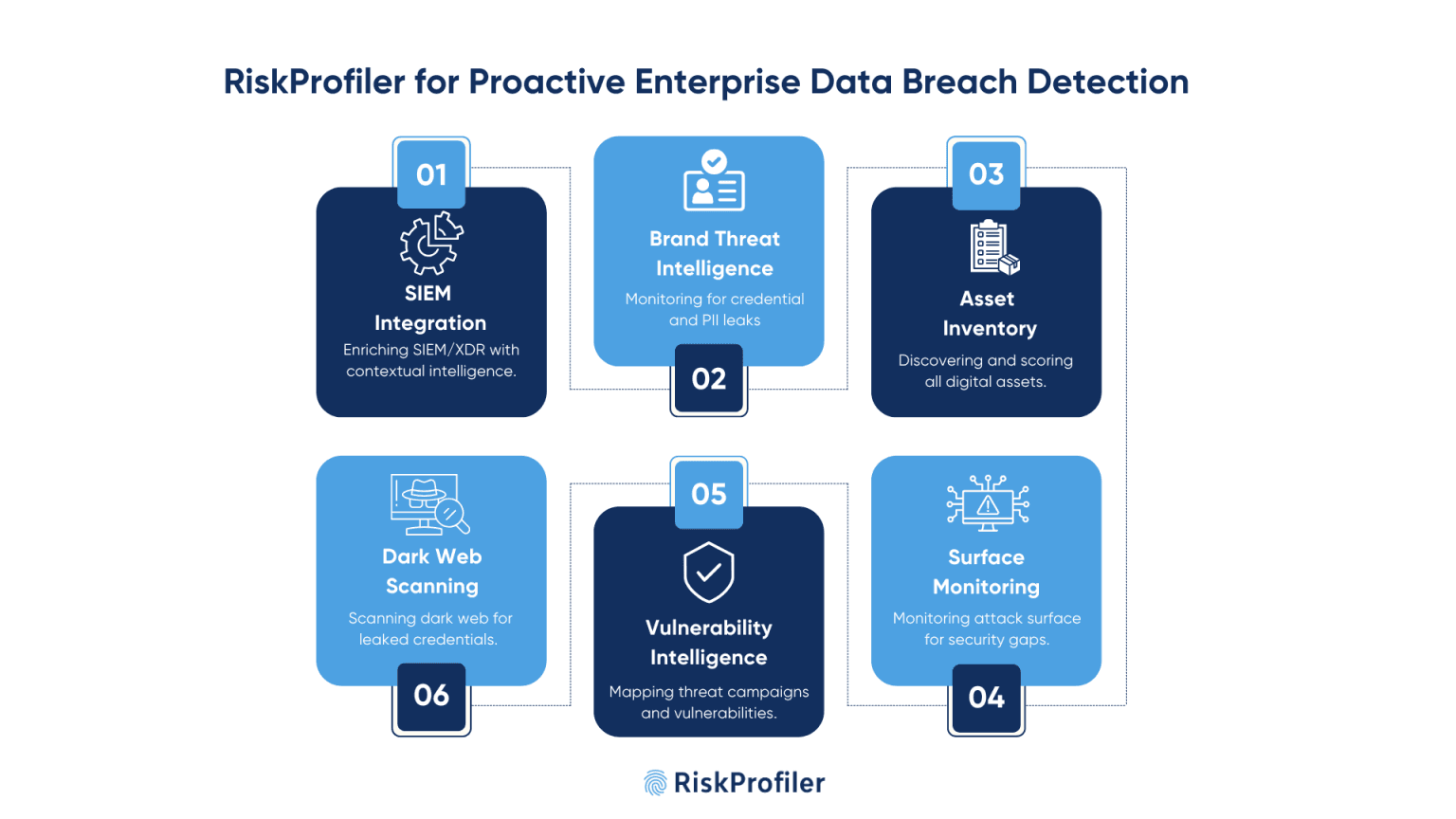
External Attack Surface Monitoring
RiskProfiler’s external threat intelligence constantly monitors your digital attack surface and cloud assets for misconfigurations, exposures, suspicious IP activity, and unusual traffic patterns, including the timeline, source, and context around that traffic. It will also monitor certificate validity, DNS records, integrity of cloud resources, vulnerabilities across domains, and application vulnerabilities to allow you to find and fix security gaps before attackers take advantage of them.
Vulnerability Intelligence and Campaign Mapping
RiskProfiler’s vulnerability intelligence connects infrastructure exposure patterns, phishing campaigns, malware kits, and adversary behaviors into unified campaigns. This enables security teams to follow industry threat trends with details on attack patterns and possible prevention methods.
Additionally, its CVE tracker and URL analyzers provide you with information on hidden weaknesses and anomalies to strengthen security in advance.
Dark Web Scanning for Credential and PII Leaks
RiskProfiler’s dark web intelligence continually scans dark web forums, paste sites, and marketplaces for leaked credentials, customer data, and sensitive IP associated with your organization. As an early-warning mechanism, it enables teams to revoke access, notify affected users, and mitigate the impacts of the leak before it causes serious damage.
The Road Ahead: AI, Automation, and Learning Post-Breach Actions
In terms of the future, AI’s influence will only solidify regarding both attack and defense. Automated spear phishing, polymorphic malware, and social engineering attacks that leverage deep fake technologies are presenting challenges to many traditional defenses. However, AI can be utilized to strengthen data breach detection as well. Machine Learning models can analyze and surface patterns from millions of data points; determine areas of risk and prioritize alerts, and even provide options for remediation of a threat, within just hours.
Organizations that invest in automated threat detection and response, promote continuous learning, and foster a culture of readiness are especially well-suited to detect and incapacitate breaches quickly, even those that hide in plain sight.
Conclusion: Don’t Just Prevent Your Breach; Proactively Detect It
In the cybersecurity ecosystem of 2025, silence is not golden; it is dangerous. The most insidious type of breach is an incident that occurs without knowledge.
However, silence can be pierced. If organizations develop the tools, processes, and mindset, they can differentiate between passive monitoring and active defense. They can expose elements hidden in their attack surface, react before an attack unfolds, and transition from breach victims to breach survivors.
Preparation can only occur on your terms. The breach you do not see is the breach that ultimately is the most damaging. Hence, it is important to establish proper enterprise data breach detection protocols in your organization to prevent otherwise avoidable damages. RiskProfiler’s unified cyber threat intelligence platform helps you establish a defense that can predict vulnerability and identify gaps well before any incident.
Explore how we strengthen your security against external threats and breach indicators by booking a demo with our experts today!
Do you think password and MFA make your organization’s security impenetrable? Then, it is time for you to think again! Data breaches are a primary security concern for the finance, retail, healthcare, hospitality, and telecom sectors worldwide. With sophisticated tools and AI integrations, such security incidents have become increasingly difficult to detect, resulting in a wider blast radius and significant damage. According to the IBM Cost of a Data Breach Report 2025, the average cost of a data breach in the US is 10.22 million USD, which reflects a 9% rise from the previous year. Although organizations continue to invest in different enterprise data breach detection systems, firewalls, multi-factor authentication, and compliance audits, the attackers have broadened their limitation barrier to customers through these barriers easily. Modern phishing tools can use leaked credentials, deliver spoofed MFA codes, and gain access to your sensitive database, all the while confirming your belief in your security system even as they bypass your defenses.
The sophistication of external threats and data breach mechanisms complicates enterprise data breach detection. For leaders responsible for protecting organizational data, CISOs, security engineers, and CXOs, the challenge is not limited to preventing breaches. After being compromised, the most dangerous breaches are those that are unknown.
What are the major causes of data breaches?
These causes of data breaches may include credential leaks, misconfigured digital assets, unsecured login practices, shadow IT issues, security gaps in supply chains, unsecured endpoints, etc. When left unsecured without proper threat vigilance, cyber attackers can detect and exploit these endpoints to gain system access.
Unsecured Access Points
Most major data breaches often begin with seemingly benign access through a forgotten subdomain, a misconfigured cloud storage bucket, or an abandoned test environment that was not disposed of properly. Attackers discover these entry points during passive reconnaissance and can exploit these vulnerabilities to enter your system. To avoid such exposures and curb the threats at the root, security teams need continuous vigilance and the smart analysis power of cyber threat intelligence tools like RiskProfiler.
Whether it’s an abandoned subdomain pointing to exposed infrastructure, a forgotten third-party marketing tool still collecting customer data, or a misconfigured cloud storage bucket, shadow IT introduces several critical business risks. They act as unguarded entry points on your digital ecosystem.
Lateral Movement Attacks
Once the attackers build a baseline of usual interactions by monitoring keystrokes and other interaction patterns, they initiate the attack by mimicking interactions and escalating access permissions across different accounts, databases, and internal systems.
The lateral movements and gradual access acceleration take longer to be detected, increasing exposures, system vulnerabilities, and data leaks. Security tools like RiskProfiler that enable attack path simulation help you visualize these potential vulnerability chains and address the risks effectively.
Credential Breach and Harvesting Attacks
Credential breaches are widespread in today’s digital world, where stolen login details from SaaS tools, cloud platforms, and subscription-based services are traded across illegal forums and chat rooms. Login credentials are commonly compromised by weak passwords, phishing schemes, and large-scale harvesting attacks. By implementing proper password hygiene and monitoring access compromises with threat intelligence platforms, organizations can stay ahead of these security risks.

Security Gaps in Third-Party Systems
Your supply chain ecosystem is not a detached entity. Your organization’s security is entirely dependent upon the reliability of your vendor’s system in an interconnected digital ecosystem. Exposures, misconfigurations, leaked credentials, or security breaches in the vendor environment can expose your system if not detected on time. Incorporating a smart and proactive third-party risk management tool like RiskProfiler with your security protocols can help you with data breach detection in your supply chain before it becomes a threat to your operations and reputation.
Phishing and Social Engineering Attacks
Credential leaks and abuse remain one of the primary vehicles for cyberattacks against organizations across industries, according to the Verizon Data Breach Investigations Report, 2025. Phishing and social engineering attacks, the most commonly used tools behind credential harvesting, rely on manipulating human trust and urgency rather than exploiting a technical flaw, making data breach detection more difficult in these cases.
Furthermore, cyber threat actors commonly share proven phishing kits, spoofed login pages, and social engineering scripts across dark web forums. It allows malicious actors to transfer or steal your organization’s data, take over accounts, and compromise networks of interconnected systems.
Early Warning: Data Breach Signals You Might Be Missing
Organizations tend to characterize data breach signals as something rogue. Perhaps a syslog mistake or other emphasis on systems creation as part of their operating profile. Unless the indications of intrusions are seen in context, organizations can completely miss the initial signals of a potentially catastrophic breach, or mistakenly conclude that what’s happening is part of the normal, business-as-usual operations. An increase of failed logins from foreign IP addresses, requests for access to data from non-usual points of origin, abnormally high outbound traffic, or identified events of unusual privilege elevation might simply be seen as isolated signals unless it is confirmed with other incident reports.
Such warnings can get lost in the flood of data generated by modern enterprise systems or get ignored due to a lack of collaborative workflows between security silos. Without correlation and intelligent prioritization, threat symbols are ignored by your security team, leading to avoidable escalation and breach scenarios.
Data Breach Detection Practices for Early Response
When security teams function in silos, responsible for their discreet portion of infrastructure or data, they lack meaningful context that would connect correlation with causation. Modern cyber threat intelligence solutions like RiskProfiler aim to solve this communication problem and provide expansive visibility into the entire ecosystem, revealing vital context about adversary origin, intent, and behavior, with applicable insights to prevent attack or compromise. The following are some examples of practices to display threat detection and consequently understand cyberattacks in a more immediate and relevant manner.
External Attack Surface Management (EASM)
Your entire digital footprint is a part of your external attack surface. In such a large and expanding environment, assets can be overlooked or lost over time, resulting in security gaps. External attack surface management platforms, like RiskProfiler, constantly scan this massive external attack surface to detect all such abandoned, unlisted, or forgotten access points and give you a comprehensive threat view.
Additionally, they also help you discover suspicious DNS activities, uncharacteristic IP logins, certification status, misconfigured assets, and exposed code structures for holistic security. The tools help you detect threats on time, enabling you to respond to them before they escalate.
User and Entity Behavior Analytics (UEBA)
UEBA platforms create behavioral baselines based on user interactions analyzed over time to see the eventual patterns across teams, devices, applications, and regions. For example, when a user logs in from a location where he’s never logged in before, with the added anomaly that he has logged in at an unusual time, or a service account is making access requests that have no relation to his job duties, UEBA reports and isolates the atypical activity. On its own, this indicator is meaningless; it is the ability of UEBA to associate indicators of attack to determine the patterns of attacks that can often pinpoint insider attack, compromised credentials, or lateral stealth movement in the early steps of an attack.

Decoy or Honeypot Systems
Deception technology creates and manages essentially fake assets in an organization’s network that have attributes of seemingly real, but false, credentials, databases, endpoints, and services dispersed across the organization. The decoys are designed to engage with cyber attackers and enable security teams to observe attack patterns and identify malicious actions in the network.
For instance, if attackers engage with a decoy by logging into a nonexistent admin panel or attempting to extract data from a baited database, it initiates alerts. The product leads to low-noise, high-fidelity threat detection that can, in most cases, alert the security team before they reach critical systems.
SIEM and XDR Integration
Security Information and Event Management (SIEM) systems are central to an enterprise’s monitoring strategy by collecting logs across networks, servers, applications, and cloud environments. Caught in this context is the growing diversity of modern cyberthreats, which often originate in vendor infrastructure and create attack paths through insecure endpoints by manipulating misconfigured assets.
To detect such multi-stage attacks, organizations are turning to Extended Detection and Response (XDR). XDR platforms integrate with SIEMs but go further by correlating findings across endpoints, identity providers, network traffic, and more. They provide a unified timeline of events, allowing analysts to trace attacks from origin to impact. Combined with automation and threat intelligence, SIEM + XDR integration becomes a powerful mechanism for early breach detection and faster incident response.
Why is proactive detection important for data breach prevention?
To secure your organization against digital adversaries and strengthen data breach prevention policies, you will need to discover exposures before attackers do, recognize their attack patterns, and fortify your ecosystem against their intrusion methods.
Red teaming and attack path simulations expose how a breach could unfold from an attacker’s perspective, revealing weaknesses that may go unnoticed during routine checks. Unified cyber threat intelligence tools like RiskProfiler also help you correlate security compromises across different operational areas to build a complete picture with correlation and context. Breach and attack simulation platforms reinforce this process by continuously emulating real-world attack scenarios to test and improve defenses.
By implementing these proactive threat monitoring, analysis, and detection methods with your security strategy, your organization can stay ahead of industry breach trends and cyber adversaries.
How Does RiskProfiler Enhance Enterprise Data Breach Detection?
RiskProfiler’s unified cyber threat intelligence tool is precisely engineered to proactively close the visibility and intelligence gaps that allow breaches to persist undetected. It integrates with existing security infrastructure to deliver contextual, real-time exposure intelligence that empowers faster decision-making and threat mitigation.
Effortless Integration with SIEM & XDR Systems
RiskProfiler integrates into your SIEM and XDR platforms easily to provide contextual intelligence from external and internal sources. Because it maps threat signals to assets and associated behavior, the platform provides specific, exposure-linked insights instead of generic indicators to drive defensible action. This enrichment of visibility allows better correlations, faster triage, and accurate detection of threats in your environment.
Monitoring for Brand Threats and Credential Exposures
Impersonated identities, credential breaches, and suspicious login behavior are precursory evidence of compromise. RiskProfiler’s brand threat intelligence provides continuous monitoring and gathers information on leaks, stolen or breached credentials, or any mention of an organization on the surface web, social media platforms, dark web, data dumps, and illegal chat room sites to create contextual evidence to prepare threat alerts. This helps security teams identify threats and remediate risks before the information can be leveraged by adversaries to gain unauthorized access to the system.
Asset Inventory and Endpoint Exposure Identification
RiskProfiler’s attack surface management tool continuously crawls your digital footprint and inventories everything, including unknown subdomains, unused APIs, exposed endpoints, and third-party integrations. It scores each asset based on exposure, patch status, and exploitability, for security teams to prioritize their response efforts in securing the exposures based on their financial and technical impact.

External Attack Surface Monitoring
RiskProfiler’s external threat intelligence constantly monitors your digital attack surface and cloud assets for misconfigurations, exposures, suspicious IP activity, and unusual traffic patterns, including the timeline, source, and context around that traffic. It will also monitor certificate validity, DNS records, integrity of cloud resources, vulnerabilities across domains, and application vulnerabilities to allow you to find and fix security gaps before attackers take advantage of them.
Vulnerability Intelligence and Campaign Mapping
RiskProfiler’s vulnerability intelligence connects infrastructure exposure patterns, phishing campaigns, malware kits, and adversary behaviors into unified campaigns. This enables security teams to follow industry threat trends with details on attack patterns and possible prevention methods.
Additionally, its CVE tracker and URL analyzers provide you with information on hidden weaknesses and anomalies to strengthen security in advance.
Dark Web Scanning for Credential and PII Leaks
RiskProfiler’s dark web intelligence continually scans dark web forums, paste sites, and marketplaces for leaked credentials, customer data, and sensitive IP associated with your organization. As an early-warning mechanism, it enables teams to revoke access, notify affected users, and mitigate the impacts of the leak before it causes serious damage.
The Road Ahead: AI, Automation, and Learning Post-Breach Actions
In terms of the future, AI’s influence will only solidify regarding both attack and defense. Automated spear phishing, polymorphic malware, and social engineering attacks that leverage deep fake technologies are presenting challenges to many traditional defenses. However, AI can be utilized to strengthen data breach detection as well. Machine Learning models can analyze and surface patterns from millions of data points; determine areas of risk and prioritize alerts, and even provide options for remediation of a threat, within just hours.
Organizations that invest in automated threat detection and response, promote continuous learning, and foster a culture of readiness are especially well-suited to detect and incapacitate breaches quickly, even those that hide in plain sight.
Conclusion: Don’t Just Prevent Your Breach; Proactively Detect It
In the cybersecurity ecosystem of 2025, silence is not golden; it is dangerous. The most insidious type of breach is an incident that occurs without knowledge.
However, silence can be pierced. If organizations develop the tools, processes, and mindset, they can differentiate between passive monitoring and active defense. They can expose elements hidden in their attack surface, react before an attack unfolds, and transition from breach victims to breach survivors.
Preparation can only occur on your terms. The breach you do not see is the breach that ultimately is the most damaging. Hence, it is important to establish proper enterprise data breach detection protocols in your organization to prevent otherwise avoidable damages. RiskProfiler’s unified cyber threat intelligence platform helps you establish a defense that can predict vulnerability and identify gaps well before any incident.
Explore how we strengthen your security against external threats and breach indicators by booking a demo with our experts today!
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



