Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Executive Protection: Integrating Physical and Cybersecurity
Executive Protection: Integrating Physical and Cybersecurity
The rapidly evolving technical and AI advancements are making digital impersonation easier, while the detection process becomes harder.
Read Time
7 min read
Posted On
Aug 20, 2025
Social Media
The rapidly evolving technical and AI advancements are making digital impersonation easier, while the detection process becomes harder. While traditional physical security remains essential, the surge in AI-powered digital threats has made C-suite leaders prime targets across both virtual and real-world domains. Threat actors are deploying generative AI to clone voices, forge identities, launch precision-targeted phishing campaigns, and track executives in real time across platforms. Today, protecting high-profile executives demands far more than firewalls or security personnel; it requires a layered, real-time, intelligence-led monitoring strategy that bridges the gap between physical and digital security. From CFOs facing spear-phishing targeting wire transfers to CEOs being impersonated in deepfake videos, the era of executive risk management is no longer a niche concern but a strategic necessity. Thus, it is now of paramount importance to incorporate executive protection and executive security monitoring protocols for complete threat control and management against hybrid threat signals.
What is Digital Executive Protection?
Executive security monitoring refers to the comprehensive framework for protecting high-profile individuals and stakeholders, especially those in C-suite roles, against both physical and digital threats. This includes proactive cybersecurity practices, physical security protocols, and real-time monitoring to guard against impersonation, espionage, data breaches, and personal safety risks.
It’s a multidimensional discipline that monitors beyond what traditional bodyguards and firewalls can cover. It now integrates threat intelligence, secure communications, and reputation defense to counter adversaries using both traditional methods and modern AI-driven tactics.
Why is Digital Executive Protection Important in 2025?
An executive’s role, which includes board communications, public appearances, and thought leadership, naturally creates a visible and recognizable online presence. Thus, their digital identity becomes one of the important targets for malicious threat actors and fraudulent identities. Executive security monitoring ensures that your executive’s cyber presence remains uncompromised.
Ensure Safety of Personal and Corporate Data
Executives have access to sensitive business data, trade secrets, and high-value access points. A successful breach could result in significant data theft or ransomware attacks. Cybercriminals often take advantage of weak personal device security or use social engineering tactics to obtain this information. Poor password practices, lack of proper authentication, and leaked credential details can heighten various online threats, resulting in unauthorized access, phishing scams, and impersonation attacks on digital platforms. To protect against cyber threats and identity misuse, your brand executives need to understand the importance of cyber hygiene, implement secure access protocols, and use multi-factor authentication (MFA).

Enable Complete PII Protection and Online Reputation
AI technology trains itself using a vast database of open-source information available on the internet. This database includes all types of content, such as social media posts, public relations materials, webinars, and interviews published by companies. As a result, attackers can easily imitate executive speech patterns, recreate public bios, and even hijack their video presence using AI and machine learning tools. These digital identities can then be exploited for targeted scams, fraudulent campaigns, or stock manipulation.
To protect an executive’s digital identity, it is crucial to monitor social media platforms, automatically flag impersonators, and implement rapid take-down protocols. This ensures that the executive’s online presence remains authentic and secure.
Avoid Compliance and Legal Risks
Executive impersonation can lead to a barrage of exposures and privacy losses, including unauthorized access to sensitive customer data, unsanctioned wire transfers, and confidentiality breaches. Such violations of privacy and customer trust can lead to consequences with several regulatory mandates, such as GDPR, CCPA, SOC, ISO, HIPAA, etc. The legal consequences can be dire if an impersonation or breach leads to leaked client data or misinformation.
Comprehensive executive security minimizes this exposure by maintaining compliance-ready digital hygiene and audit trails. Having a proactive executive security monitoring tool helps your team identify impersonation or uncharacteristic behavior, allowing you to take down the malicious campaigns before they can lead to compliance violations.
An attack on an executive is no longer a personal issue. It’s a company-wide event with potential legal, financial, and PR consequences.
Setu Parimi, CTO of RiskProfiler
The Rise of AI-Driven Phishing and Executive Impersonation
AI-powered phishing, executive impersonation, and malicious hate campaigns are rising in the current scenario. With convenient access to AI tools, cybercriminals can synthesize voices, automate spear-phishing, and replicate writing styles even of well-trained staff and customers.
Building Executive Protection against Spear Phishing Campaigns
Executives are vulnerable to targeted phishing campaigns due to their public visibility and high-level access. A single compromised email can result in massive financial losses or credential leaks. In a more direct attack, spear phishing can target a business’s investors and major stakeholders, causing severe damage during the funding or M&A cycles.
A robust digital executive security monitoring solution must integrate email anomaly detection, multi-factor authentication, and contextual risk analysis. By establishing a baseline of normal activity, this system can instantly detect deviations, flag deceptive communications, and initiate automated take-down procedures.
Securing the Executive’s Digital Identity from Spoofed Accounts and Applications
Spoofed LinkedIn profiles, duplicated email conversations, and fake Slack or Zoom invites have become increasingly common in executive impersonation over the past few years. These are often used to solicit sensitive information or inject malware into enterprise environments. Additionally, such malicious practices can also be used by scammers to gain benefits from the prospective clients or partners of the business, damaging its market reputation.
In a 2024 event, Mark Read, the CEO of WPP PLC, one of the leading UK-based advertising agencies, was the victim of a foiled deepfake scam, according to The Guardian. Scammers used deepfake technology to empower a voice clone during a virtual meeting between the CEO and another WPP executive to collect money and personal information.
Such events are becoming increasingly common in the present evolving threat landscape. Automated scanning of new app sign-ups, suspicious link distributions, and domain impersonation can neutralize threats before they reach the executive inbox.

Continuous Executive Security Monitoring for Threat Conversation
Threat actors often discuss executives on dark web forums before launching attacks. Leaked PII data or financial information related to executives can be sold in illegal marketplaces or released in dark web data dumps. Monitoring these platforms offers early insight into emerging plots or breach chatter.
RiskProfiler’s brand threat intelligence and executive protection protocols monitor the surface and dark web spaces along with social media platforms to detect any malicious or suspicious mention of your executives and stakeholders with NLP and behavioral analysis. We also monitor all dark web data dumps and leak sites to locate mentions of your executive’s credentials and PII details.
RiskProfiler gave us a week’s heads-up on executive impersonation scam circulating in Telegram channels. That insight was crucial in preempting damage.
VP of Operation, US Based Retail Organization
Rising Threat of Deepfake Technology
Although initially introduced as a form of entertainment and creative expression, the use of generative AI is becoming a growing concern for cybersecurity. Some artificial intelligence tools are being used in vishing campaigns, spreading misleading statements on social media, or committing financial fraud. Such synthetic media attacks can sway investor sentiment, manipulate stock prices, or cause severe reputational damage.
To counter such sophisticated brand threats, organizations must deploy real-time detection technologies that leverage natural language processing, voiceprint authentication, and facial behavior analysis. When paired with automated take-down workflows, these tools empower security teams to swiftly identify and remove malicious content before it goes viral.
Integrating Physical and Cybersecurity for Executive Monitoring
Integrating physical and digital security is imperative to ensure comprehensive executive security. A unified threat strategy enables cybersecurity and executive protection teams to collaborate seamlessly, share intelligence, and respond with a coordinated, holistic approach.
Enhanced Physical Security Management for Executives
GPS tracking, route-based threat intelligence, and tailored event security protocols are key elements of modern physical protection strategies. These measures ensure that high-risk individuals, such as executives or public figures, are shielded from location-specific threats, whether during transit or at high-profile events.
However, the security strategies can be made truly effective when they’re integrated into a centralized risk intelligence dashboard, combined with cybersecurity signals. This fusion allows physical security teams to incorporate digital risk signals, such as leaked travel plans, social media chatter, unfavorable public sentiments, or early signs of stalking, into their operational planning. The result is a proactive, intelligence-led security posture that adapts in real-time, aligning physical presence with digital foresight for unmatched executive protection.
Cyber Security Management for Executives
Executives face heightened cyber risk due to their access to critical assets and decision-making authority. Executives must practice strong security hygiene, enabling multi-factor authentication (MFA), changing passwords regularly, and recognizing phishing attempts across email, messaging apps, and personal accounts. When digital behaviors are aligned with robust infrastructure and integrated with physical threat intelligence, organizations gain faster, more contextual threat correlation and response.
Why Should Cyber and Physical Threat Intelligence Be Integrated?
Modern executive protection strategies require the addition of technology and focus on an integrated approach. Decentralized cyber and physical security teams protecting the same executive will result in slower response and lesser protection due to the lack of information sharing.
Physical protection is enhanced in executive protection through cybersecurity measures, including GPS and event-specific security for public appearances. These protection measures mitigate location-based threats seamlessly. In addition, integrating physical protection with real-time online alerts for major information, such as digital security risks, sensitive information sharing, and cyber threats, can bolster preventive measures.
Safeguarding Executive Travel
When executives travel, especially to areas with differing security profiles, security teams can use GPS data alongside area-specific threat intelligence to locate them. Real-time risk geography interfacing with travel logistics allows for an adaptive response to evolving ground threats. Plans can be adjusted proactively rather than reactively.
Guarding Executive Identities Against Spoofing
Spoofing identities poses a critical risk. Fake social media profiles, as well as apps impersonating executives, can inflict damage and mislead people. Phishing impersonation blocks and identity verification tools work hand in hand to ensure that fake accounts are identified and canceled through cyber monitoring tools.
Countering Spear Phishing Attacks
These types of attacks target executives at the organization as the spearhead of the intricate phishing attacks. Organizations can make their phishing defenses better by monitoring behavioral patterns and incorporating phishing detection systems, thus shielding themselves and organizational assets.
Real-Time Monitoring of Threats and Conversations
Hacker forums and the dark web are known sources of information and can lead to an attack. Organizations can monitor executive-focused attacks in these places to receive alerts and act in advance, preventing damage.

Proactive Deepfake Detection and Take Down
Deepfakes don’t just harm reputations. They pose serious physical security risks to executives. Synthetic media can spread false directives, triggering protests, threats, or targeted attacks. Real-time detection using voice and facial biometrics is essential to prevent misinformation from escalating into real-world danger.
Tailored Alert Systems for Each Executive
Every executive has a unique risk profile. Alert systems should calibrate for each executive’s public visibility, role, and geographic area. This custom attention guarantees only the most pertinent threats will be flagged, which enhances precision and expedites response times.
Leveraging Global Threat Intelligence
Security issues can originate from anywhere. Gaining access to international threat intelligence, ranging from breach notifications to intelligence from global politics, provides organizations with a greater scope of emerging threats. This international approach enhances the vigilance and preparedness of both physical and cybersecurity personnel.
Proactive Digital Executive Monitoring and Threat Remediation
Monitoring suspicious activity is the first step in proactively identifying emerging threats. Responding to threats, however, is where the resilience of a security framework is tested. Proactive response entails safeguarding peripheral systems and neutralizing threats that breach the outer defenses. This approach ensures diminished impact.
Security Awareness Training for the Executive
An executive’s awareness is foundational to the organization’s security posture; therefore, training them to identify phishing, spot deepfakes, and report suspicious behavior is a critical line of defense. Such training reduces the likelihood of human errors and cultivates a culture of security.
Safeguarding Data Using Encryption
Encryption serves as a foundational protective measure. Whether it is through complete disk encryption, sharing files securely, or using private messaging services, encryption allows executive information to be protected from adversaries, ensuring it remains secure even when access to it is attempted.
Early Detection of Exposed PII and Credentials
Monitoring the internet for exposed credentials is critical. Through early detection of these exposures, some actions can be taken to reset passwords or even initiate protective legal steps, preventing access to sensitive systems by malicious users.

Automating the Detection of Fake Accounts
Automation is key when impersonators strike. Through automated systems, flagged executive impersonator accounts can be reported to social media platforms such as LinkedIn or Instagram, resulting in the accounts being removed before causing damage to the brand.
Securing Communication Channels
As opposed to voice calls, private messaging applications provide a layer of security. With biometric security options and encrypted end-to-end networks, private conversations can be held without the fear of being accessed by unauthorized individuals. However, it is of utmost importance to avoid disclosing personal passwords and security details in public spaces and changing these credentials in regular intervals for heightened security.
Staying Informed with Threat Awareness Campaigns
The digital threat landscape is always evolving. That is the reason behind the need for set drills and briefings. These strategies not only assist with team training for high-pressure situations but also reveal potential weak spots. Awareness and security training also allow the concerned people to recognize threats and prevent interactions or further escalations.
How Does RiskProfiler Ensure Executive Protection in Real Time?
RiskProfiler’s Executive Risk Monitoring Module is built to preemptively identify, contextualize, and neutralize risks before they impact C-suite leaders. Its methodology is rooted in combining advanced threat analytics with global intelligence sources and automated incident response.
Identifying Credential Exposures via Surface and Dark Web Intelligence
RiskProfiler’s dark web intelligence tool continuously scans paste sites, dark web forums, and underground marketplaces for leaked login credentials, email-password combinations, and exposed authentication tokens associated with executive accounts. Once detected, immediate remediation protocols like credential resets or domain blocking are initiated.
Contextualizing Digital Threats with Executive Intelligence
Advanced algorithms filter out false positives and noise by contextualizing threat intelligence. RiskProfiler executive monitoring matches threats to executive profiles based on their role, exposure level, recent travel, or media coverage, ensuring that teams focus on relevant, high-risk indicators.
Preventing Phishing Attempts Aimed at Leadership
RiskProfiler identifies phishing campaigns and fake accounts that misuse executive identities to send spoofed emails or mimic conversations with clients, prospects, employees, or investors with its brand threat intelligence. Analyzing sender domains, campaign patterns, and impersonation behaviors it prevents reputational damage and stops threats before they escalate.
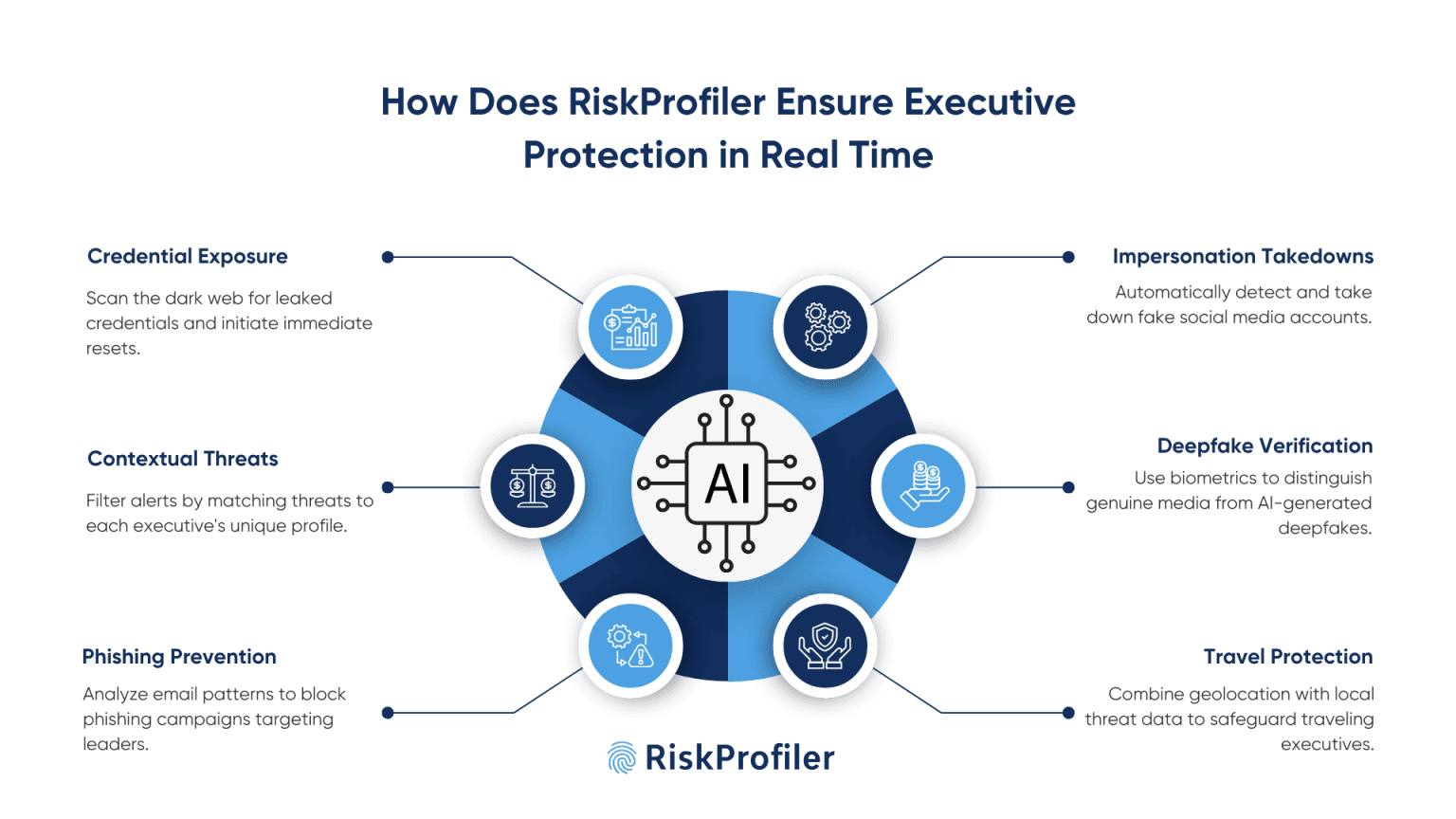
Exposing Social Media Impersonation Campaigns
Impersonation accounts on platforms like LinkedIn, X (formerly Twitter), and Instagram are rapidly identified using image recognition, bio comparison, and posting behavior analytics. RiskProfiler not only detects these accounts but also streamlines threat disruption procedures automatically through its takedown workflows.
Verifying Authenticity Against Malicious Deepfakes
Through voice biometric analysis and facial recognition, RiskProfiler distinguishes genuine executive media from AI-generated content. This capability ensures that manipulated videos or voice messages do not spread disinformation or manipulate market sentiment.
Securing Travel and Event Plans
RiskProfiler’s physical security intelligence tool combines real-time geolocation data with local threat intelligence, protest monitoring, and geopolitical alerts. This allows organizations to safeguard executives during travel or public appearances, often providing advance notice of unrest, surveillance attempts, or potential disruptions.
RiskProfiler also collects data on social media conversations and general trends, which can be aligned with geopolitical alerts to determine the safety and security of your key executives and decision-makers. This proactive and multifaceted approach enables organizations to mitigate executive-specific threats at the earliest point of detection, before any attacker can exploit a vulnerability for gain or disruption.
Final Thought: From Reactive To Resilient Executive Protection
The threats facing high-profile executives in 2025 are real, targeted, and increasingly personal. From AI-enabled phishing to reputational attacks via deepfakes, the risk surface has expanded far beyond the boardroom. Organizations that continue to view executive protection through a narrow lens risk exposing their leadership and brand equity to preventable harm.
Effective executive security today means combining technology, intelligence, and cross-functional collaboration. It’s not just about defending people, it’s about preserving trust, stability, and business continuity at the highest levels.
With solutions like RiskProfiler, security leaders can stop reacting to threats and start predicting them, before a spoofed voicemail, forged email, or public impersonation escalates into a full-blown crisis.
The rapidly evolving technical and AI advancements are making digital impersonation easier, while the detection process becomes harder. While traditional physical security remains essential, the surge in AI-powered digital threats has made C-suite leaders prime targets across both virtual and real-world domains. Threat actors are deploying generative AI to clone voices, forge identities, launch precision-targeted phishing campaigns, and track executives in real time across platforms. Today, protecting high-profile executives demands far more than firewalls or security personnel; it requires a layered, real-time, intelligence-led monitoring strategy that bridges the gap between physical and digital security. From CFOs facing spear-phishing targeting wire transfers to CEOs being impersonated in deepfake videos, the era of executive risk management is no longer a niche concern but a strategic necessity. Thus, it is now of paramount importance to incorporate executive protection and executive security monitoring protocols for complete threat control and management against hybrid threat signals.
What is Digital Executive Protection?
Executive security monitoring refers to the comprehensive framework for protecting high-profile individuals and stakeholders, especially those in C-suite roles, against both physical and digital threats. This includes proactive cybersecurity practices, physical security protocols, and real-time monitoring to guard against impersonation, espionage, data breaches, and personal safety risks.
It’s a multidimensional discipline that monitors beyond what traditional bodyguards and firewalls can cover. It now integrates threat intelligence, secure communications, and reputation defense to counter adversaries using both traditional methods and modern AI-driven tactics.
Why is Digital Executive Protection Important in 2025?
An executive’s role, which includes board communications, public appearances, and thought leadership, naturally creates a visible and recognizable online presence. Thus, their digital identity becomes one of the important targets for malicious threat actors and fraudulent identities. Executive security monitoring ensures that your executive’s cyber presence remains uncompromised.
Ensure Safety of Personal and Corporate Data
Executives have access to sensitive business data, trade secrets, and high-value access points. A successful breach could result in significant data theft or ransomware attacks. Cybercriminals often take advantage of weak personal device security or use social engineering tactics to obtain this information. Poor password practices, lack of proper authentication, and leaked credential details can heighten various online threats, resulting in unauthorized access, phishing scams, and impersonation attacks on digital platforms. To protect against cyber threats and identity misuse, your brand executives need to understand the importance of cyber hygiene, implement secure access protocols, and use multi-factor authentication (MFA).

Enable Complete PII Protection and Online Reputation
AI technology trains itself using a vast database of open-source information available on the internet. This database includes all types of content, such as social media posts, public relations materials, webinars, and interviews published by companies. As a result, attackers can easily imitate executive speech patterns, recreate public bios, and even hijack their video presence using AI and machine learning tools. These digital identities can then be exploited for targeted scams, fraudulent campaigns, or stock manipulation.
To protect an executive’s digital identity, it is crucial to monitor social media platforms, automatically flag impersonators, and implement rapid take-down protocols. This ensures that the executive’s online presence remains authentic and secure.
Avoid Compliance and Legal Risks
Executive impersonation can lead to a barrage of exposures and privacy losses, including unauthorized access to sensitive customer data, unsanctioned wire transfers, and confidentiality breaches. Such violations of privacy and customer trust can lead to consequences with several regulatory mandates, such as GDPR, CCPA, SOC, ISO, HIPAA, etc. The legal consequences can be dire if an impersonation or breach leads to leaked client data or misinformation.
Comprehensive executive security minimizes this exposure by maintaining compliance-ready digital hygiene and audit trails. Having a proactive executive security monitoring tool helps your team identify impersonation or uncharacteristic behavior, allowing you to take down the malicious campaigns before they can lead to compliance violations.
An attack on an executive is no longer a personal issue. It’s a company-wide event with potential legal, financial, and PR consequences.
Setu Parimi, CTO of RiskProfiler
The Rise of AI-Driven Phishing and Executive Impersonation
AI-powered phishing, executive impersonation, and malicious hate campaigns are rising in the current scenario. With convenient access to AI tools, cybercriminals can synthesize voices, automate spear-phishing, and replicate writing styles even of well-trained staff and customers.
Building Executive Protection against Spear Phishing Campaigns
Executives are vulnerable to targeted phishing campaigns due to their public visibility and high-level access. A single compromised email can result in massive financial losses or credential leaks. In a more direct attack, spear phishing can target a business’s investors and major stakeholders, causing severe damage during the funding or M&A cycles.
A robust digital executive security monitoring solution must integrate email anomaly detection, multi-factor authentication, and contextual risk analysis. By establishing a baseline of normal activity, this system can instantly detect deviations, flag deceptive communications, and initiate automated take-down procedures.
Securing the Executive’s Digital Identity from Spoofed Accounts and Applications
Spoofed LinkedIn profiles, duplicated email conversations, and fake Slack or Zoom invites have become increasingly common in executive impersonation over the past few years. These are often used to solicit sensitive information or inject malware into enterprise environments. Additionally, such malicious practices can also be used by scammers to gain benefits from the prospective clients or partners of the business, damaging its market reputation.
In a 2024 event, Mark Read, the CEO of WPP PLC, one of the leading UK-based advertising agencies, was the victim of a foiled deepfake scam, according to The Guardian. Scammers used deepfake technology to empower a voice clone during a virtual meeting between the CEO and another WPP executive to collect money and personal information.
Such events are becoming increasingly common in the present evolving threat landscape. Automated scanning of new app sign-ups, suspicious link distributions, and domain impersonation can neutralize threats before they reach the executive inbox.

Continuous Executive Security Monitoring for Threat Conversation
Threat actors often discuss executives on dark web forums before launching attacks. Leaked PII data or financial information related to executives can be sold in illegal marketplaces or released in dark web data dumps. Monitoring these platforms offers early insight into emerging plots or breach chatter.
RiskProfiler’s brand threat intelligence and executive protection protocols monitor the surface and dark web spaces along with social media platforms to detect any malicious or suspicious mention of your executives and stakeholders with NLP and behavioral analysis. We also monitor all dark web data dumps and leak sites to locate mentions of your executive’s credentials and PII details.
RiskProfiler gave us a week’s heads-up on executive impersonation scam circulating in Telegram channels. That insight was crucial in preempting damage.
VP of Operation, US Based Retail Organization
Rising Threat of Deepfake Technology
Although initially introduced as a form of entertainment and creative expression, the use of generative AI is becoming a growing concern for cybersecurity. Some artificial intelligence tools are being used in vishing campaigns, spreading misleading statements on social media, or committing financial fraud. Such synthetic media attacks can sway investor sentiment, manipulate stock prices, or cause severe reputational damage.
To counter such sophisticated brand threats, organizations must deploy real-time detection technologies that leverage natural language processing, voiceprint authentication, and facial behavior analysis. When paired with automated take-down workflows, these tools empower security teams to swiftly identify and remove malicious content before it goes viral.
Integrating Physical and Cybersecurity for Executive Monitoring
Integrating physical and digital security is imperative to ensure comprehensive executive security. A unified threat strategy enables cybersecurity and executive protection teams to collaborate seamlessly, share intelligence, and respond with a coordinated, holistic approach.
Enhanced Physical Security Management for Executives
GPS tracking, route-based threat intelligence, and tailored event security protocols are key elements of modern physical protection strategies. These measures ensure that high-risk individuals, such as executives or public figures, are shielded from location-specific threats, whether during transit or at high-profile events.
However, the security strategies can be made truly effective when they’re integrated into a centralized risk intelligence dashboard, combined with cybersecurity signals. This fusion allows physical security teams to incorporate digital risk signals, such as leaked travel plans, social media chatter, unfavorable public sentiments, or early signs of stalking, into their operational planning. The result is a proactive, intelligence-led security posture that adapts in real-time, aligning physical presence with digital foresight for unmatched executive protection.
Cyber Security Management for Executives
Executives face heightened cyber risk due to their access to critical assets and decision-making authority. Executives must practice strong security hygiene, enabling multi-factor authentication (MFA), changing passwords regularly, and recognizing phishing attempts across email, messaging apps, and personal accounts. When digital behaviors are aligned with robust infrastructure and integrated with physical threat intelligence, organizations gain faster, more contextual threat correlation and response.
Why Should Cyber and Physical Threat Intelligence Be Integrated?
Modern executive protection strategies require the addition of technology and focus on an integrated approach. Decentralized cyber and physical security teams protecting the same executive will result in slower response and lesser protection due to the lack of information sharing.
Physical protection is enhanced in executive protection through cybersecurity measures, including GPS and event-specific security for public appearances. These protection measures mitigate location-based threats seamlessly. In addition, integrating physical protection with real-time online alerts for major information, such as digital security risks, sensitive information sharing, and cyber threats, can bolster preventive measures.
Safeguarding Executive Travel
When executives travel, especially to areas with differing security profiles, security teams can use GPS data alongside area-specific threat intelligence to locate them. Real-time risk geography interfacing with travel logistics allows for an adaptive response to evolving ground threats. Plans can be adjusted proactively rather than reactively.
Guarding Executive Identities Against Spoofing
Spoofing identities poses a critical risk. Fake social media profiles, as well as apps impersonating executives, can inflict damage and mislead people. Phishing impersonation blocks and identity verification tools work hand in hand to ensure that fake accounts are identified and canceled through cyber monitoring tools.
Countering Spear Phishing Attacks
These types of attacks target executives at the organization as the spearhead of the intricate phishing attacks. Organizations can make their phishing defenses better by monitoring behavioral patterns and incorporating phishing detection systems, thus shielding themselves and organizational assets.
Real-Time Monitoring of Threats and Conversations
Hacker forums and the dark web are known sources of information and can lead to an attack. Organizations can monitor executive-focused attacks in these places to receive alerts and act in advance, preventing damage.

Proactive Deepfake Detection and Take Down
Deepfakes don’t just harm reputations. They pose serious physical security risks to executives. Synthetic media can spread false directives, triggering protests, threats, or targeted attacks. Real-time detection using voice and facial biometrics is essential to prevent misinformation from escalating into real-world danger.
Tailored Alert Systems for Each Executive
Every executive has a unique risk profile. Alert systems should calibrate for each executive’s public visibility, role, and geographic area. This custom attention guarantees only the most pertinent threats will be flagged, which enhances precision and expedites response times.
Leveraging Global Threat Intelligence
Security issues can originate from anywhere. Gaining access to international threat intelligence, ranging from breach notifications to intelligence from global politics, provides organizations with a greater scope of emerging threats. This international approach enhances the vigilance and preparedness of both physical and cybersecurity personnel.
Proactive Digital Executive Monitoring and Threat Remediation
Monitoring suspicious activity is the first step in proactively identifying emerging threats. Responding to threats, however, is where the resilience of a security framework is tested. Proactive response entails safeguarding peripheral systems and neutralizing threats that breach the outer defenses. This approach ensures diminished impact.
Security Awareness Training for the Executive
An executive’s awareness is foundational to the organization’s security posture; therefore, training them to identify phishing, spot deepfakes, and report suspicious behavior is a critical line of defense. Such training reduces the likelihood of human errors and cultivates a culture of security.
Safeguarding Data Using Encryption
Encryption serves as a foundational protective measure. Whether it is through complete disk encryption, sharing files securely, or using private messaging services, encryption allows executive information to be protected from adversaries, ensuring it remains secure even when access to it is attempted.
Early Detection of Exposed PII and Credentials
Monitoring the internet for exposed credentials is critical. Through early detection of these exposures, some actions can be taken to reset passwords or even initiate protective legal steps, preventing access to sensitive systems by malicious users.

Automating the Detection of Fake Accounts
Automation is key when impersonators strike. Through automated systems, flagged executive impersonator accounts can be reported to social media platforms such as LinkedIn or Instagram, resulting in the accounts being removed before causing damage to the brand.
Securing Communication Channels
As opposed to voice calls, private messaging applications provide a layer of security. With biometric security options and encrypted end-to-end networks, private conversations can be held without the fear of being accessed by unauthorized individuals. However, it is of utmost importance to avoid disclosing personal passwords and security details in public spaces and changing these credentials in regular intervals for heightened security.
Staying Informed with Threat Awareness Campaigns
The digital threat landscape is always evolving. That is the reason behind the need for set drills and briefings. These strategies not only assist with team training for high-pressure situations but also reveal potential weak spots. Awareness and security training also allow the concerned people to recognize threats and prevent interactions or further escalations.
How Does RiskProfiler Ensure Executive Protection in Real Time?
RiskProfiler’s Executive Risk Monitoring Module is built to preemptively identify, contextualize, and neutralize risks before they impact C-suite leaders. Its methodology is rooted in combining advanced threat analytics with global intelligence sources and automated incident response.
Identifying Credential Exposures via Surface and Dark Web Intelligence
RiskProfiler’s dark web intelligence tool continuously scans paste sites, dark web forums, and underground marketplaces for leaked login credentials, email-password combinations, and exposed authentication tokens associated with executive accounts. Once detected, immediate remediation protocols like credential resets or domain blocking are initiated.
Contextualizing Digital Threats with Executive Intelligence
Advanced algorithms filter out false positives and noise by contextualizing threat intelligence. RiskProfiler executive monitoring matches threats to executive profiles based on their role, exposure level, recent travel, or media coverage, ensuring that teams focus on relevant, high-risk indicators.
Preventing Phishing Attempts Aimed at Leadership
RiskProfiler identifies phishing campaigns and fake accounts that misuse executive identities to send spoofed emails or mimic conversations with clients, prospects, employees, or investors with its brand threat intelligence. Analyzing sender domains, campaign patterns, and impersonation behaviors it prevents reputational damage and stops threats before they escalate.

Exposing Social Media Impersonation Campaigns
Impersonation accounts on platforms like LinkedIn, X (formerly Twitter), and Instagram are rapidly identified using image recognition, bio comparison, and posting behavior analytics. RiskProfiler not only detects these accounts but also streamlines threat disruption procedures automatically through its takedown workflows.
Verifying Authenticity Against Malicious Deepfakes
Through voice biometric analysis and facial recognition, RiskProfiler distinguishes genuine executive media from AI-generated content. This capability ensures that manipulated videos or voice messages do not spread disinformation or manipulate market sentiment.
Securing Travel and Event Plans
RiskProfiler’s physical security intelligence tool combines real-time geolocation data with local threat intelligence, protest monitoring, and geopolitical alerts. This allows organizations to safeguard executives during travel or public appearances, often providing advance notice of unrest, surveillance attempts, or potential disruptions.
RiskProfiler also collects data on social media conversations and general trends, which can be aligned with geopolitical alerts to determine the safety and security of your key executives and decision-makers. This proactive and multifaceted approach enables organizations to mitigate executive-specific threats at the earliest point of detection, before any attacker can exploit a vulnerability for gain or disruption.
Final Thought: From Reactive To Resilient Executive Protection
The threats facing high-profile executives in 2025 are real, targeted, and increasingly personal. From AI-enabled phishing to reputational attacks via deepfakes, the risk surface has expanded far beyond the boardroom. Organizations that continue to view executive protection through a narrow lens risk exposing their leadership and brand equity to preventable harm.
Effective executive security today means combining technology, intelligence, and cross-functional collaboration. It’s not just about defending people, it’s about preserving trust, stability, and business continuity at the highest levels.
With solutions like RiskProfiler, security leaders can stop reacting to threats and start predicting them, before a spoofed voicemail, forged email, or public impersonation escalates into a full-blown crisis.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



