Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


AI-Powered Third-Party Risk Management: Importance in 2025
AI-Powered Third-Party Risk Management: Importance in 2025
In today’s business landscape, no company is an island. We thrive on a complex network of partners, SaaS tools, and contractors that form the digital backbone of our operations.
Read Time
7 min read
Posted On
Aug 14, 2025
Social Media
In today’s business landscape, no company is an island. We thrive on a complex network of partners, SaaS tools, and contractors that form the digital backbone of our operations. This ecosystem now drives nearly 90% of what we do. But this deep integration creates a shared fate: a security gap in one of your vendors can instantly become a critical vulnerability for you. According to Verizon’s Data Breach Investigations Report 2025, the third-party risks went from 15% to 30% in the last year. This reality makes it clear that a modern security strategy must extend beyond our walls. It requires a proactive third-party risk management plan to see and manage the risks across our entire vendor network. In the modern, fast-evolving world, AI-powered frameworks are providing the continuous visibility needed to neutralize these supply chain threats before they can compromise the business we’ve worked so hard to build.
Key Categories in Third-Party Risk Management
The integration of third-party vendors into an organization’s ecosystem introduces a range of significant risks that extend beyond initial technical implementation. A comprehensive Third-Party Risk Management (TPRM) program must identify and continuously monitor several critical risk domains to safeguard the organization, its data, and its reputation.
1. Cybersecurity Risk
A vulnerability within a third-party vendor’s security posture can serve as a direct attack vector into an organization’s network. Instead of attempting to breach heavily fortified perimeter defenses, malicious actors can exploit the trusted connection established with the vendor to gain unauthorized access to internal systems and sensitive data.
2. Information Security Risk
Information security risk stems from a vendor connection when a potential compromise of sensitive data, including Personally Identifiable Information (PII), intellectual property, or corporate financial records, due to a vendor’s inadequate data handling or security controls. A breach originating from a third party can lead to significant data exfiltration, even if the organization’s core systems remain secure.
3. Access Management Risk
This risk arises from the failure to properly de-provision access privileges for vendors, contractors, or their employees after a contract has been terminated. These lingering “digital keys” create persistent, unauthorized entry points to systems and data, which can be exploited long after the formal business relationship has concluded.
4. Financial Risk
This category addresses the potential for a critical vendor to experience financial insolvency, bankruptcy, or other forms of business failure. Such an event can lead to an abrupt cessation of essential services, causing not only direct financial losses but also significant operational disruption as the organization works to secure an alternative solution under emergency conditions.

5. Operational Risk
Operational risk involves the failure or underperformance of a third-party product or service that is integral to daily business functions. The disruption of a critical third-party tool can create a cascading failure across internal workflows, leading to decreased productivity, project delays, and a diminished capacity to serve customers effectively.
6. Reputational Risk
An organization’s brand reputation is intrinsically linked to the conduct and performance of its vendors. Should a third-party partner engage in unethical practices, experience a high-profile data breach, or suffer from negative public perception, the associated brand damage can transfer to the primary organization. This “guilt by association” can erode customer trust, investor confidence, and market standing.
7. Compliance & Legal Risk
Under regulatory frameworks such as GDPR, CCPA, HIPAA, and others, organizations are often held ultimately responsible for the protection of sensitive data, even when that data is managed by a third-party partner. A compliance failure on the part of a vendor can result in significant legal liability, steep regulatory fines, and direct legal action against the organization that owns the data.
What is the role of AI in Third-Party Risk Detection?
Modern digital supply chains are complex, distributed, and digitally interconnected. Besides adding value and operational efficiency, each vendor you onboard expands your external attack surface a little further. In recent years, high-profile breaches, like the Kaseya and SolarWinds incidents, have demonstrated how a single compromised vendor can ripple across industries, affecting thousands of downstream customers.
Traditional vendor risk assessments, often spreadsheet-driven and periodic, fail to keep up with dynamic threat environments. As new vulnerabilities are disclosed and vendor infrastructures change, organizations need real-time monitoring and continuous assessment to detect and respond to emerging risks. This is why AI integration is required.
As an organization integrates AI cybersecurity with its regular monitoring protocol, the internal security team gains the capability to detect, analyze, and address threats faster and effectively.
Analyzes historical threat data, attack trends, and vulnerabilities
Monitors vendor security posture and asset status
Flag potential threats as soon as they emerge on the attack surface
Correlates threat structures across multiple domains to recognize potential paths of lateral movements
Allow effective prioritization based on threat severity, technical importance, business impact, and legal ramifications
Provides the security team with the crucial hours of advantage to detect and mitigate the threats before they can escalate or be exploited
How can AI be used in third-party risk management?
Artificial Intelligence (AI) provides a significant advantage in modern third-party risk management by accelerating and automating the key functions of risk monitoring, detection, analysis, and reporting. The integration of AI allows organizations to continuously assess the security posture of their third- and fourth-party vendors through streamlined workflows, enhancing overall threat detection capabilities and bridging visibility gaps that typically exist between disparate security systems.
Continuous Third-Party Risk Monitoring
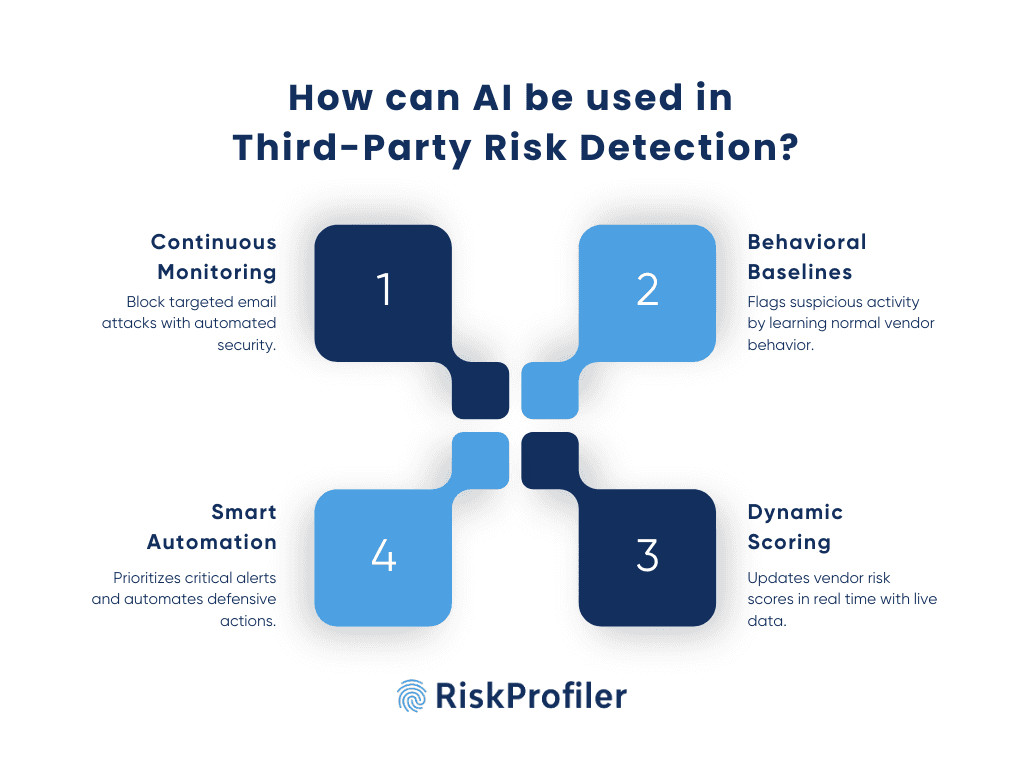
By integrating with AI, organizations can significantly enhance their risk monitoring capabilities across the entire vendor ecosystem. The system performs a comprehensive analysis of diverse data sets, including historical threat intelligence, attack trends, vendor security posture, known vulnerabilities, and asset inventories, to continuously evaluate security preparedness. Furthermore, AI enables security teams to detect emerging threats and potential compromises within the third-party infrastructure in real-time, providing crucial lead time for collaborative incident response.
Behavioral Baselines and Anomaly Detection
Effective anomaly detection requires establishing a baseline of normal operational behavior. This approach involves continuously tracking typical patterns of activity for each vendor, including data access, usage metrics, system updates, and network traffic. Once this behavioral baseline is established, the system can automatically identify and issue alerts for significant deviations, such as unauthorized privilege escalation or anomalous data transfers. For comprehensive risk management, this visibility must extend to fourth-party vendors (subcontractors) and the extended vendors to prevent security incidents originating from indirect dependencies.
Dynamic Risk Scoring
Static, point-in-time third-party risk assessments are insufficient for managing risk in a dynamic threat landscape. A modern vendor risk analysis approach replaces these with dynamic risk scoring, which updates a vendor’s risk posture in real-time. This process continuously ingests and analyzes live data feeds, including open-source and dark web threat intelligence, public breach notifications, and other indicators of compromise. The resulting score provides a current and accurate depiction of vendor risk, enabling security and procurement teams to make informed, timely decisions regarding vendor onboarding, contract renewals, and access control.
Prioritization and Automation
High volume of uncontextualized alerts can lead to alert fatigue and obscure genuine threats. An intelligent risk management system addresses this by automatically correlating risk signals across vendors, industries, and geographies to establish their connection and background. This correlation provides the necessary context to prioritize threats based on severity and potential impact, allowing security teams to focus on the most critical issues. Furthermore, the system can integrate with existing security infrastructure to trigger automated response workflows, such as isolating a compromised vendor’s network access, thereby enabling rapid mitigation without manual intervention.
Third-Party Risk Assessment: How AI Resolves Security Threats?
AI vendor risk detection tools not only detect threats but also help prepare remediation workflows to mitigate them on time. They enable threat prioritization with fast detection, assessment, and containment workflows.
Detect Manipulated Vendor Communication
A seemingly routine software update from a vendor might contain malicious code inserted during a third-party attack. Without proper third-party risk management workflows in place, organizations would fail to detect and prevent such threats on time, allowing them to penetrate their ecosystem. However, with third-party risk detection frameworks in place, such a threat will be detected early, allowing your security team to send customized notifications to your vendor’s security team and initiate mitigation efforts.

Identify Third-Party Breaches and Exposures
If a vendor experiences a breach, AI can rapidly correlate this incident with your internal systems to assess exposure and determine its business and security impact. This process can also scan for risks from third-party providers, showing you hidden dependencies you might not have been aware of. This clarity helps you coordinate a swift and effective cleanup before things spiral.
Vendor Credential Leaks and Data Misuse
A strong monitoring strategy includes keeping an eye on the dark web for early warnings. This allows you to spot leaked vendor credentials or sensitive company documents that have shown up out in the wild. By flagging this kind of suspicious activity early, you can act before it snowballs into a major incident. This early detection means less damage and far fewer headaches for your team. RiskProfiler’s proactive dark web monitoring tool detects such leaks and breaches in real-time, allowing an organizational team to coordinate access remediation before the leaks can be exploited.
Leveraging RiskProfiler’s threat intelligence, we successfully detected exposures of credentials and PII details in advance, while gaining access to an actionalized remediation plan for fast action and threat mitigation, preventing a security incident.
— Chief Technology Officer, US-based Real Estate Development Business
How to Implement AI-Based Vendor Risk Management?
For a successful implementation, an AI-driven vendor risk program should be built on these five essential pillars.

1. Holistic Data Aggregation: Integrate vendor questionnaires with empirical data from threat intelligence, security ratings, and access logs. This creates a validated and holistic view of your actual risk, moving beyond self-reported information.
2. Comprehensive Ecosystem Mapping: Extend visibility beyond your direct vendors to map sub-tier (fourth-party) dependencies. This uncovers hidden risks and critical points of failure within your entire supply chain.
3. Cross-Functional Business Alignment: Align the AI model with input from legal, procurement, and IT. This ensures risk alerts are contextual and tied to strategic business priorities, not just isolated technical findings.
4. Establishing Actionable Risk Thresholds: Translate risk scores into a clear response framework by defining precise thresholds for investigation, escalation, and vendor off-boarding. This empowers your team to act decisively and avoid alert fatigue.
5. Continuous Model Refinement and Optimization: Implement a continuous feedback loop, using data from real-world incidents and vendor performance to refine algorithms. This iterative process ensures the system’s accuracy and effectiveness over time.
Proactive Third-Party Risk Detection and Mitigation with RiskProfiler
RiskProfiler continuously monitors the external attack surface of all connected third- and fourth-party vendors. By leveraging AI and machine learning, the platform automatically scans for threat indicators, misconfigurations, and data exposures across the entire vendor ecosystem.
Whether it’s a change in DNS configurations, unexpected cloud service behavior, or exposed credentials, RiskProfiler flags these early signals before they escalate into business-impacting incidents, enabling organizations to adopt a proactive rather than reactive approach to vendor risk management.
Third-Party Risk Assessment Enhanced by AI Monitoring
RiskProfiler streamlines vendor security questionnaires with real-time threat visibility. The platform not only automates the distribution, collection, and analysis of vendor questionnaires but also enhances them by detecting security posture changes that may not be disclosed or noticed during manual assessments. By automatically validating questionnaire responses against live threat intelligence, RiskProfiler vendor risk analysis bridges the security lapses and initiates appropriate response workflows.
Third- and Fourth-Party Ecosystem Visibility
Most organizations have visibility into direct (third-party) vendors, but fourth-party risks (vendors and the extended suppliers of direct vendors) often remain hidden. RiskProfiler solves this by mapping indirect vendor relationships, highlighting inherited risks from software dependencies, cloud partners, and managed service providers. Through this expanded visibility, security teams can trace the origin of threats and make smarter containment decisions that extend beyond the immediate vendor.

Real-Time Detection of High-Risk Vendors
RiskProfiler continuously evaluates vendor risk scores based on live data. Using AI-driven risk indicators, such as dark web mentions, phishing domains, vulnerability disclosures, asset exposures, and access pattern anomalies, the platform flags high-risk vendors instantly. Organizations can then trigger custom threat management workflows, such as access restrictions, contract review, or additional validation, ensuring a swift and structured response.
Peer Benchmarking for Informed Decision-Making
To support strategic procurement and security decisions, RiskProfiler’s third-party risk management solution offers peer benchmarking capabilities. It compares the risk profiles of vendors against industry standards and similar organizations in your sector, helping procurement heads and CISOs assess whether a vendor’s risk posture is acceptable or lagging. This comparative insight supports smarter onboarding, prioritization, and even contract negotiations, especially for mission-critical third-party contractors or partners.
Streamlined Compliance and Audit Readiness
RiskProfiler simplifies compliance management with frameworks such as ISO 27001, PCI DSS, GDPR, CCPR, NIS2, SOC 2, GDPR, etc by generating auto-updated audit reports, risk logs, and vendor documentation. The platform tracks regulatory changes and maps vendor performance against relevant frameworks, minimizing manual effort while maximizing oversight. Security and procurement teams can demonstrate due diligence in real-time, maintain audit trails, and avoid fines associated with non-compliance.
Regulators expect proof of ongoing third-party risk management. RiskProfiler gives organizations a live dashboard of compliance management, not just a point-in-time snapshot.
— VP of Operations, US-based Retail Business
Final Thoughts
In 2025, securing the vendor ecosystem is not optional; it’s foundational. As threat actors exploit third and fourth-party weaknesses, organizations must evolve from periodic assessments to intelligent, continuous monitoring and third-party risk detection frameworks. AI brings the capability to detect early signals of compromise, quantify risk dynamically, and stay compliant amid a fast-changing regulatory environment.
For procurement heads, security teams, and CISOs, the path forward is clear: embrace AI not just as a tool, but as a strategic partner in securing the business ecosystem.
In today’s business landscape, no company is an island. We thrive on a complex network of partners, SaaS tools, and contractors that form the digital backbone of our operations. This ecosystem now drives nearly 90% of what we do. But this deep integration creates a shared fate: a security gap in one of your vendors can instantly become a critical vulnerability for you. According to Verizon’s Data Breach Investigations Report 2025, the third-party risks went from 15% to 30% in the last year. This reality makes it clear that a modern security strategy must extend beyond our walls. It requires a proactive third-party risk management plan to see and manage the risks across our entire vendor network. In the modern, fast-evolving world, AI-powered frameworks are providing the continuous visibility needed to neutralize these supply chain threats before they can compromise the business we’ve worked so hard to build.
Key Categories in Third-Party Risk Management
The integration of third-party vendors into an organization’s ecosystem introduces a range of significant risks that extend beyond initial technical implementation. A comprehensive Third-Party Risk Management (TPRM) program must identify and continuously monitor several critical risk domains to safeguard the organization, its data, and its reputation.
1. Cybersecurity Risk
A vulnerability within a third-party vendor’s security posture can serve as a direct attack vector into an organization’s network. Instead of attempting to breach heavily fortified perimeter defenses, malicious actors can exploit the trusted connection established with the vendor to gain unauthorized access to internal systems and sensitive data.
2. Information Security Risk
Information security risk stems from a vendor connection when a potential compromise of sensitive data, including Personally Identifiable Information (PII), intellectual property, or corporate financial records, due to a vendor’s inadequate data handling or security controls. A breach originating from a third party can lead to significant data exfiltration, even if the organization’s core systems remain secure.
3. Access Management Risk
This risk arises from the failure to properly de-provision access privileges for vendors, contractors, or their employees after a contract has been terminated. These lingering “digital keys” create persistent, unauthorized entry points to systems and data, which can be exploited long after the formal business relationship has concluded.
4. Financial Risk
This category addresses the potential for a critical vendor to experience financial insolvency, bankruptcy, or other forms of business failure. Such an event can lead to an abrupt cessation of essential services, causing not only direct financial losses but also significant operational disruption as the organization works to secure an alternative solution under emergency conditions.

5. Operational Risk
Operational risk involves the failure or underperformance of a third-party product or service that is integral to daily business functions. The disruption of a critical third-party tool can create a cascading failure across internal workflows, leading to decreased productivity, project delays, and a diminished capacity to serve customers effectively.
6. Reputational Risk
An organization’s brand reputation is intrinsically linked to the conduct and performance of its vendors. Should a third-party partner engage in unethical practices, experience a high-profile data breach, or suffer from negative public perception, the associated brand damage can transfer to the primary organization. This “guilt by association” can erode customer trust, investor confidence, and market standing.
7. Compliance & Legal Risk
Under regulatory frameworks such as GDPR, CCPA, HIPAA, and others, organizations are often held ultimately responsible for the protection of sensitive data, even when that data is managed by a third-party partner. A compliance failure on the part of a vendor can result in significant legal liability, steep regulatory fines, and direct legal action against the organization that owns the data.
What is the role of AI in Third-Party Risk Detection?
Modern digital supply chains are complex, distributed, and digitally interconnected. Besides adding value and operational efficiency, each vendor you onboard expands your external attack surface a little further. In recent years, high-profile breaches, like the Kaseya and SolarWinds incidents, have demonstrated how a single compromised vendor can ripple across industries, affecting thousands of downstream customers.
Traditional vendor risk assessments, often spreadsheet-driven and periodic, fail to keep up with dynamic threat environments. As new vulnerabilities are disclosed and vendor infrastructures change, organizations need real-time monitoring and continuous assessment to detect and respond to emerging risks. This is why AI integration is required.
As an organization integrates AI cybersecurity with its regular monitoring protocol, the internal security team gains the capability to detect, analyze, and address threats faster and effectively.
Analyzes historical threat data, attack trends, and vulnerabilities
Monitors vendor security posture and asset status
Flag potential threats as soon as they emerge on the attack surface
Correlates threat structures across multiple domains to recognize potential paths of lateral movements
Allow effective prioritization based on threat severity, technical importance, business impact, and legal ramifications
Provides the security team with the crucial hours of advantage to detect and mitigate the threats before they can escalate or be exploited
How can AI be used in third-party risk management?
Artificial Intelligence (AI) provides a significant advantage in modern third-party risk management by accelerating and automating the key functions of risk monitoring, detection, analysis, and reporting. The integration of AI allows organizations to continuously assess the security posture of their third- and fourth-party vendors through streamlined workflows, enhancing overall threat detection capabilities and bridging visibility gaps that typically exist between disparate security systems.
Continuous Third-Party Risk Monitoring
By integrating with AI, organizations can significantly enhance their risk monitoring capabilities across the entire vendor ecosystem. The system performs a comprehensive analysis of diverse data sets, including historical threat intelligence, attack trends, vendor security posture, known vulnerabilities, and asset inventories, to continuously evaluate security preparedness. Furthermore, AI enables security teams to detect emerging threats and potential compromises within the third-party infrastructure in real-time, providing crucial lead time for collaborative incident response.
Behavioral Baselines and Anomaly Detection
Effective anomaly detection requires establishing a baseline of normal operational behavior. This approach involves continuously tracking typical patterns of activity for each vendor, including data access, usage metrics, system updates, and network traffic. Once this behavioral baseline is established, the system can automatically identify and issue alerts for significant deviations, such as unauthorized privilege escalation or anomalous data transfers. For comprehensive risk management, this visibility must extend to fourth-party vendors (subcontractors) and the extended vendors to prevent security incidents originating from indirect dependencies.

Dynamic Risk Scoring
Static, point-in-time third-party risk assessments are insufficient for managing risk in a dynamic threat landscape. A modern vendor risk analysis approach replaces these with dynamic risk scoring, which updates a vendor’s risk posture in real-time. This process continuously ingests and analyzes live data feeds, including open-source and dark web threat intelligence, public breach notifications, and other indicators of compromise. The resulting score provides a current and accurate depiction of vendor risk, enabling security and procurement teams to make informed, timely decisions regarding vendor onboarding, contract renewals, and access control.
Prioritization and Automation
High volume of uncontextualized alerts can lead to alert fatigue and obscure genuine threats. An intelligent risk management system addresses this by automatically correlating risk signals across vendors, industries, and geographies to establish their connection and background. This correlation provides the necessary context to prioritize threats based on severity and potential impact, allowing security teams to focus on the most critical issues. Furthermore, the system can integrate with existing security infrastructure to trigger automated response workflows, such as isolating a compromised vendor’s network access, thereby enabling rapid mitigation without manual intervention.
Third-Party Risk Assessment: How AI Resolves Security Threats?
AI vendor risk detection tools not only detect threats but also help prepare remediation workflows to mitigate them on time. They enable threat prioritization with fast detection, assessment, and containment workflows.
Detect Manipulated Vendor Communication
A seemingly routine software update from a vendor might contain malicious code inserted during a third-party attack. Without proper third-party risk management workflows in place, organizations would fail to detect and prevent such threats on time, allowing them to penetrate their ecosystem. However, with third-party risk detection frameworks in place, such a threat will be detected early, allowing your security team to send customized notifications to your vendor’s security team and initiate mitigation efforts.

Identify Third-Party Breaches and Exposures
If a vendor experiences a breach, AI can rapidly correlate this incident with your internal systems to assess exposure and determine its business and security impact. This process can also scan for risks from third-party providers, showing you hidden dependencies you might not have been aware of. This clarity helps you coordinate a swift and effective cleanup before things spiral.
Vendor Credential Leaks and Data Misuse
A strong monitoring strategy includes keeping an eye on the dark web for early warnings. This allows you to spot leaked vendor credentials or sensitive company documents that have shown up out in the wild. By flagging this kind of suspicious activity early, you can act before it snowballs into a major incident. This early detection means less damage and far fewer headaches for your team. RiskProfiler’s proactive dark web monitoring tool detects such leaks and breaches in real-time, allowing an organizational team to coordinate access remediation before the leaks can be exploited.
Leveraging RiskProfiler’s threat intelligence, we successfully detected exposures of credentials and PII details in advance, while gaining access to an actionalized remediation plan for fast action and threat mitigation, preventing a security incident.
— Chief Technology Officer, US-based Real Estate Development Business
How to Implement AI-Based Vendor Risk Management?
For a successful implementation, an AI-driven vendor risk program should be built on these five essential pillars.

1. Holistic Data Aggregation: Integrate vendor questionnaires with empirical data from threat intelligence, security ratings, and access logs. This creates a validated and holistic view of your actual risk, moving beyond self-reported information.
2. Comprehensive Ecosystem Mapping: Extend visibility beyond your direct vendors to map sub-tier (fourth-party) dependencies. This uncovers hidden risks and critical points of failure within your entire supply chain.
3. Cross-Functional Business Alignment: Align the AI model with input from legal, procurement, and IT. This ensures risk alerts are contextual and tied to strategic business priorities, not just isolated technical findings.
4. Establishing Actionable Risk Thresholds: Translate risk scores into a clear response framework by defining precise thresholds for investigation, escalation, and vendor off-boarding. This empowers your team to act decisively and avoid alert fatigue.
5. Continuous Model Refinement and Optimization: Implement a continuous feedback loop, using data from real-world incidents and vendor performance to refine algorithms. This iterative process ensures the system’s accuracy and effectiveness over time.
Proactive Third-Party Risk Detection and Mitigation with RiskProfiler
RiskProfiler continuously monitors the external attack surface of all connected third- and fourth-party vendors. By leveraging AI and machine learning, the platform automatically scans for threat indicators, misconfigurations, and data exposures across the entire vendor ecosystem.
Whether it’s a change in DNS configurations, unexpected cloud service behavior, or exposed credentials, RiskProfiler flags these early signals before they escalate into business-impacting incidents, enabling organizations to adopt a proactive rather than reactive approach to vendor risk management.
Third-Party Risk Assessment Enhanced by AI Monitoring
RiskProfiler streamlines vendor security questionnaires with real-time threat visibility. The platform not only automates the distribution, collection, and analysis of vendor questionnaires but also enhances them by detecting security posture changes that may not be disclosed or noticed during manual assessments. By automatically validating questionnaire responses against live threat intelligence, RiskProfiler vendor risk analysis bridges the security lapses and initiates appropriate response workflows.
Third- and Fourth-Party Ecosystem Visibility
Most organizations have visibility into direct (third-party) vendors, but fourth-party risks (vendors and the extended suppliers of direct vendors) often remain hidden. RiskProfiler solves this by mapping indirect vendor relationships, highlighting inherited risks from software dependencies, cloud partners, and managed service providers. Through this expanded visibility, security teams can trace the origin of threats and make smarter containment decisions that extend beyond the immediate vendor.

Real-Time Detection of High-Risk Vendors
RiskProfiler continuously evaluates vendor risk scores based on live data. Using AI-driven risk indicators, such as dark web mentions, phishing domains, vulnerability disclosures, asset exposures, and access pattern anomalies, the platform flags high-risk vendors instantly. Organizations can then trigger custom threat management workflows, such as access restrictions, contract review, or additional validation, ensuring a swift and structured response.
Peer Benchmarking for Informed Decision-Making
To support strategic procurement and security decisions, RiskProfiler’s third-party risk management solution offers peer benchmarking capabilities. It compares the risk profiles of vendors against industry standards and similar organizations in your sector, helping procurement heads and CISOs assess whether a vendor’s risk posture is acceptable or lagging. This comparative insight supports smarter onboarding, prioritization, and even contract negotiations, especially for mission-critical third-party contractors or partners.
Streamlined Compliance and Audit Readiness
RiskProfiler simplifies compliance management with frameworks such as ISO 27001, PCI DSS, GDPR, CCPR, NIS2, SOC 2, GDPR, etc by generating auto-updated audit reports, risk logs, and vendor documentation. The platform tracks regulatory changes and maps vendor performance against relevant frameworks, minimizing manual effort while maximizing oversight. Security and procurement teams can demonstrate due diligence in real-time, maintain audit trails, and avoid fines associated with non-compliance.
Regulators expect proof of ongoing third-party risk management. RiskProfiler gives organizations a live dashboard of compliance management, not just a point-in-time snapshot.
— VP of Operations, US-based Retail Business
Final Thoughts
In 2025, securing the vendor ecosystem is not optional; it’s foundational. As threat actors exploit third and fourth-party weaknesses, organizations must evolve from periodic assessments to intelligent, continuous monitoring and third-party risk detection frameworks. AI brings the capability to detect early signals of compromise, quantify risk dynamically, and stay compliant amid a fast-changing regulatory environment.
For procurement heads, security teams, and CISOs, the path forward is clear: embrace AI not just as a tool, but as a strategic partner in securing the business ecosystem.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



