Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


The Financial Cost of Brand Impersonation: How to Prevent It?
The Financial Cost of Brand Impersonation: How to Prevent It?
Brand reputation and goodwill are assets that directly or indirectly influence your enterprise’s market positioning, investor interest, sales growth, or M&A cycle.
Read Time
7 min read
Posted On
Aug 6, 2025
Social Media
Brand reputation and goodwill are assets that directly or indirectly influence your enterprise’s market positioning, investor interest, sales growth, or M&A cycle. From phishing scams to counterfeit domains, malicious actors increasingly target high-growth and established brands to exploit consumer trust, drain corporate finances, and weaken market presence. Organizations with previous instances of cyber attacks, a history of phishing scam association, or negative brand impersonation campaigns can lose their market positioning and credibility with their investors and clients.
The average cost of a data breach is far greater than its impact on passive business relationships. Direct sales cycle and corporate onboarding can also be greatly impacted by negative campaigns, brand identity duplications, and impersonation attempts. Your organization would need brand protection tools to detect brand spoofing across the internet and dismantle the threat before it can cost your operational viability.
Average Cost of a Data Breach and Brand Impersonation
Earlier, we mentioned how brand impersonation attacks can cost your organization’s reputation and operational continuity. The loss of credibility and operational impact causes active strain on the organization’s financial performance and revenue. Whether through phishing emails that mimic your brand, rogue websites that clone your storefront, or malicious actors leaking documents and PII on the dark web, these threats have direct consequences on your brand revenue.
For CFOs, brand leads, and legal teams, it’s critical to understand how these attacks translate into real costs, whether financial, reputational, or operational, and how the aftermath can ripple across investor relations, acquisition timelines, and long-term brand equity.
Direct Financial Losses from Fraud and Breach Response
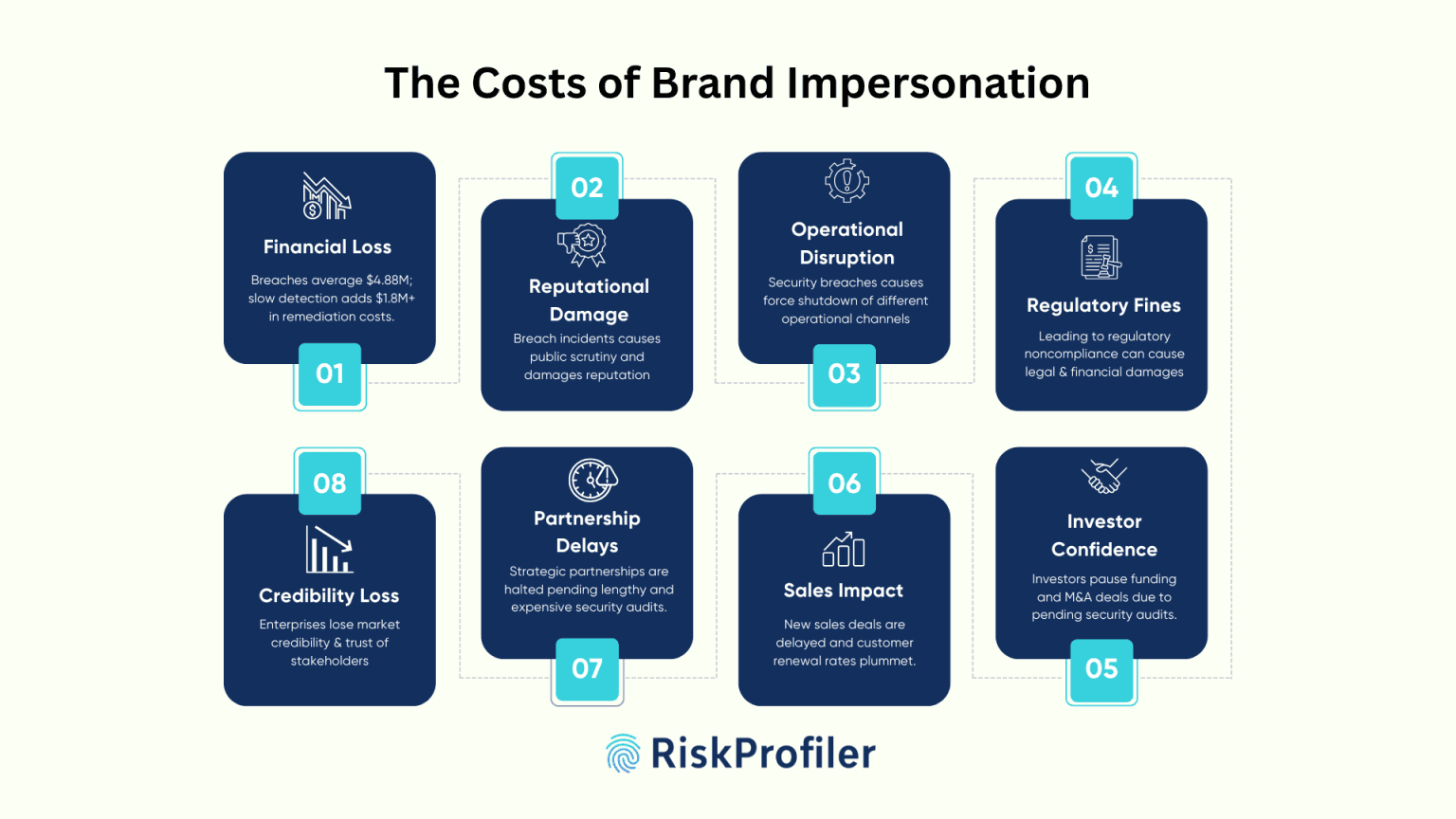
According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach has reached $4.88 million, a 10% surge over the previous year. The study reveals that most of these breaches stem from vectors like phishing, stolen credentials, or social engineering, which are frequently fueled by brand impersonation attacks.
When attackers use your logo, executive names, or cloned login portals to deceive customers or employees, the financial fallout is swift and severe. Funds are drained through fraudulent transfers, remediation efforts escalate overnight, and the absence of automated detection only stretches the process further, allowing the damage to multiply in a limited timeframe. Organizations without intelligent response capabilities often spend over $1.8 million more on average to contain such incidents, highlighting how underinvestment in early detection leads to exponential costs later.
Reputational Damage and Customer Attrition
Once the news of a brand impersonation or data breach becomes public, your security strategy, along with your brand integrity, comes under public and expert scrutiny. Consumers, even the most loyal, are likely to sever ties with companies that fail to safeguard their data. The presence of social media heavily amplifies the damage, eroding the trust of your customer base.
Operational Disruption and Business Paralysis
Brand impersonation and phishing campaigns do not just create external confusion; they disrupt your operational workflows. In many cases, email systems are temporarily shut down to halt suspicious activity, or the operations team gets locked out of their system after an attack. Customer portals are often locked down for investigation, and communication protocols are suspended while damage assessments take place.
During this chaos, customer service SLAs are missed, product launches are delayed, regular operational activities come to a standstill, and entire revenue operations grind to a halt. The operational cost of this paralysis can not be simplified to just the loss of revenue or the recovery cost. It is just not about service downtime either. The problem also extends to lost business opportunities, delayed transactions, and a demoralized workforce navigating uncertainty without clear protocols.
Legal and Regulatory Penalties
Regulatory consequences of brand impersonation-related breaches can be both immediate and long-lasting. Data protection laws such as GDPR, CCPA, and HIPAA impose steep penalties for failures in data governance, even when breaches result from impersonation rather than internal negligence. Under GDPR, fines can soar to €20 million or 4% of annual global revenue, whichever is higher. Beyond statutory fines, companies may also face class-action lawsuits, shareholder suits, or forced disclosures that further compound financial risk. When attackers hijack your brand to deceive users, your legal liability may still be triggered, especially if personal data or financial records are involved.
Loss of Stakeholder and Investor Trust
One of the most understated yet relevant impacts of impersonation and breach events is the erosion of investor confidence. Share prices often drop in the wake of a breach, but the more subtle but long-lasting damage occurs behind the scenes. Venture capital firms may delay funding decisions. Strategic acquirers may pause M&A discussions. Institutional investors may request security audits or additional risk disclosures before proceeding. These moments of hesitation can derail momentum during critical fundraising or acquisition cycles. The effect of such delays often lasts for the important decision-making process, at times long after the security issue is resolved.
Impact on Sales, Renewals, and Margins
The sales pipeline is particularly vulnerable to brand-related attacks. When prospects see news of an impersonation scam or dark web data leak involving your brand, they grow wary. Cybersecurity preparedness plays an important role in modern business decisions. Without satisfying security reports and previous brand impersonation history, legal teams can cause a delay.
Additionally, in B2C SaaS or subscription-based businesses, the rate of renewals or returning customers takes a plunge as customers lose their trust in your brand. Similarly, all your potential customers also grow wary of your brand, damaging the chances of acquiring a new customer base to a great extent.
Delays in Acquisition and Strategic Partnerships
Brand impersonation events have a particularly harmful effect on high-value business initiatives. Joint ventures, reseller agreements, and strategic alliances may be delayed as partners reevaluate your security readiness and market impact. You may be asked to conduct third-party audits, provide cyber insurance validation, or implement new safeguards before any commercial agreement can resume. The due diligence process becomes longer and more expensive. These delays affect expansion plans, market entry strategies, and competitive positioning in fast-moving industries.
Long-Term Loss of Credibility
While immediate damage can be quantified, the long-term loss of credibility is harder to measure, but just as dangerous. Customers and partners often remember or check back on cyber incidents, but they also remember the impact and threat response strategies. If the incident response was slow, opaque, or inadequate, the reputational damage and subsequent mistrust deepen. Even after systems are secured and reports are filed, the memory of the breach persists. Competitors often seize the opportunity to position themselves as more secure alternatives. Media narratives and analyst briefings subtly shift. In essence, brand impersonation weakens your strategic voice in the market, often for quarters or even years to come.
Brand Impersonation Detection Techniques
Your organization needs immediate and effective brand impersonation detection techniques that can protect your identity, customer trust, and market positioning from threat actors. In this blog, we will be discussing the top brand impersonation detection strategies that can identify and dismantle brand threats before they can affect your enterprise.
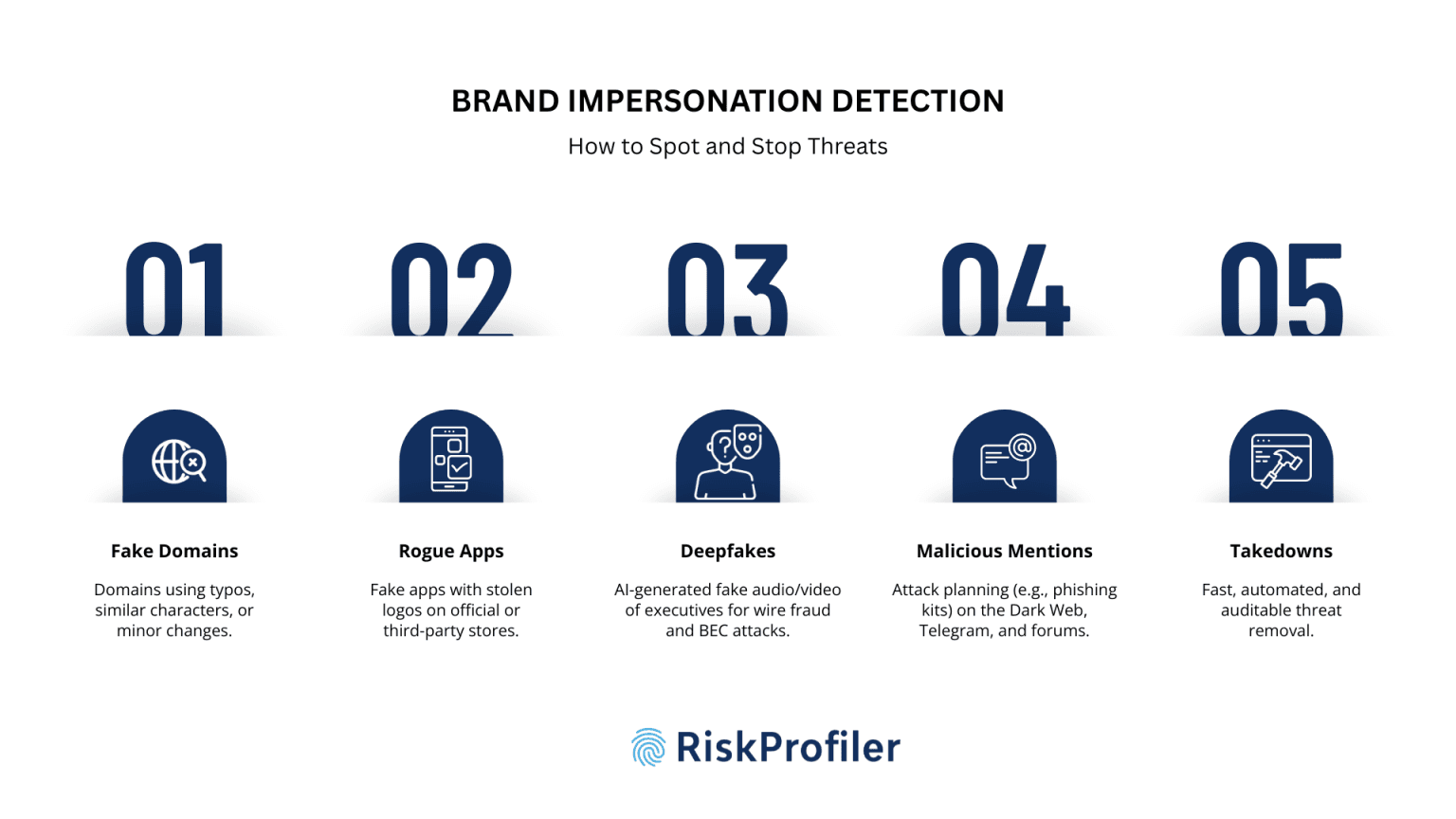
Automated Typosquat & Fake Domain Identification
The creation of lookalike domains is one of the most common ways that people impersonate brands. These could make use of typosquatting (typosquatting, or registering misspellings of an approved domain), homograph assaults (replacing similar-looking characters), or minor character appendages that are likely to be overlooked. For example, in brand papers or email inboxes, a domain such as riskprofiIer.io (with a capital “I” in place of the small letter “l”) may not be visually different from the actual 1763986604-74d06f1bdede78c5.wp-transfer.sgvps.net, making unsuspecting users trust and interact with the phishing kits.
Fuzzy logic and Levenshtein distance techniques are used by RiskProfiler to actively monitor global DNS registrations in order to identify these domain modifications at the registration stage. Teams are notified before these domains are utilized in phishing campaigns, ad fraud, or credential harvesting attacks, thanks to proactive monitoring rather than reactive detection. Domain-level detection is one of the most economical ways to prevent brand impersonation because of the low cost of domain registration and the large reward for attackers.
Identification of Rogue Applications
Attackers are increasingly creating rogue mobile applications that mimic legitimate ones outside of domains. In an effort to fool users into installing malware or divulging private information, these impersonations typically have similar names, stolen logos, and mimic real UI/UX elements.
To find these rogue apps on sites like Google Play, the Apple App Store, and third-party APK marketplaces, RiskProfiler combines binary code similarity analysis, certificate comparison, and app store scraping. The platform uses developer platform abuse channels to start takedown operations after detection. This is especially important for financial, retail, and healthcare businesses because customer acquisition and transaction volume are directly impacted by confidence in digital apps.
Identifying Deepfakes in Executive Impersonation
With generative AI tools becoming accessible and operational to all, threat actors can create realistic audio, video, or even live conference calls that mimic the voices and appearances of C-suite executives. These deepfakes are increasingly used in Business Email Compromise (BEC) and executive impersonation campaigns, such as a fabricated video call requesting wire transfers or approval of a confidential transaction.
Discovery of Malicious Brand Mention
Brand impersonation does not always involve technical duplications like fake domains or deepfakes. Often, it begins with small but malicious mentions in hidden corners of the internet or social media conspiracy pages. Attackers frequently discuss scam ideas or offer access to spoof kits before launching full-scale attacks on dark web forums, paste sites, Telegram channels, and social media groups.
RiskProfiler continuously scans these environments for the brand’s name, trademarks, executive references, and associated metadata. Using NLP and entity recognition, it flags potentially harmful mentions, such as phishing templates for sale, social engineering playbooks, or tools crafted to mimic your login page. What sets this apart is the ability to connect these mentions with actual attack attempts, such as correlating a threat actor’s post with a typosquatted domain that appears days later.
By identifying threats at the conversation level, before they mature into infrastructure or campaigns, RiskProfiler delivers predictive threat intelligence, giving organizations a valuable time advantage.
Streamlined Takedown Workflows
Once a brand threat is verified, be it a typosquatted domain, deepfake content, rogue app, or impersonated social handle, organizations must act quickly to minimize risk exposure. Brand intelligence solutions collaborate with hosting sites to streamline the spoofed asset takedown workflow and limit your organization’s threat exposure. That’s where RiskProfiler’s streamlined takedown engine comes into play.
The platform integrates directly with registrar abuse portals, cloud hosting providers, app stores, and social media abuse desks. Each threat type triggers a pre-built workflow: for instance, domain impersonation may launch WHOIS complaints, DMCA filings, or UDRP processes, while rogue app detection initiates developer takedown notices and legal escalations. These workflows are automated, timestamped, and auditable, ensuring compliance and accountability across jurisdictions.
How RiskProfiler Ensures Brand Protection Against Financial Threats
The purpose of RiskProfiler’s brand protection module is to shield companies from external brand threats and misuse of their brand identity. The module automates takedown procedures, contextualizes the alert, and detects spoofing threats in real-time. The platform defends its brand and confronts financial harm in this way.
Continuous Attack Surface Monitoring
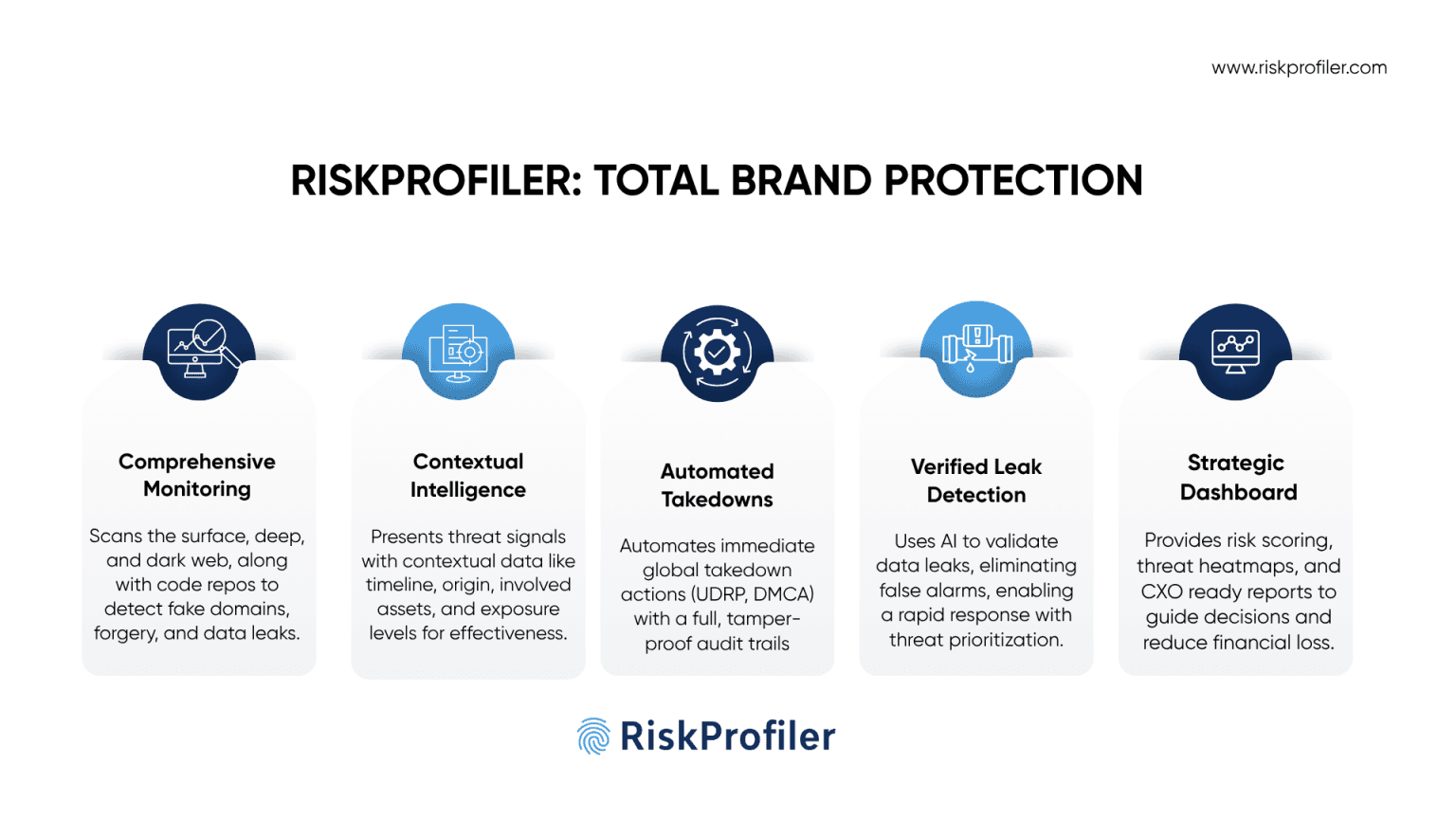
RiskProfiler continuously monitors for signs of malicious intent against your brand, including domain registrations that mimic your name using homoglyphs, typos, or deceptive lookalikes. It detects impersonations of executives, recruiters, or brand pages on social media long before they can mislead your stakeholders.
Additionally, code repositories, public paste sites, and cloud platforms are scrutinized for exposed credentials or sensitive documents that could compromise your security posture. In dark web forums and marketplaces, RiskProfiler flags any mentions of your organization, leaked PII data, internal strategy materials, or stolen databases that could be weaponized. This persistent visibility across the internet enables security teams to detect threats before they escalate into breaches.
Threat Detection with Correlated Insights
Threats are identified by RiskProfiler, which then examines them to determine their cause and correlation. It looks into whether activity on a suspicious domain is related to recent breaches, such as employee credentials being leaked or unauthorized logins on your infrastructure. If malicious file hashes appear on malware-sharing forums around the same time, RiskProfiler analyzes all the involved metrics and finds the associations with emerging threat campaigns.
With a contextual narrative about the attacker, their potential intent, and how to react quickly, the security teams are able to investigate threats holistically.
Automated Takedown Procedures with Full Audit History
RiskProfiler’s takedown workflow allows the security team to automate the attack disruption process with a pre-determined strategy. Whether it’s a WHOIS complaint against malicious registrants, a UDRP action against impersonation websites, or a DMCA complaint for content that has been hijacked, the relevant authorities are immediately notified of legal action. These are carried out all over the world, seamlessly navigating through several jurisdictions and working with hosts and registrars to take down malicious properties. SLA-compliant ticketing systems are used for escalation in cases of social impersonation or brand abuse. Every action has a tamper-resistant audit trail, whether it be legal, technical, or procedural. Legal and compliance teams do use this transparency as evidence when conducting internal audits, regulatory reviews, or even courtroom defense.
Proactive Protection Against Dark Web Data Leaks
RiskProfiler scrapes the illegal corners of the internet to detect mention of your brand, executives, PII, and credentials linked to your employees and customers, and shares detailed threat data on the portal. Unlike generic alerting, RiskProfiler’s dark web intelligence uses pattern analysis and AI-based entity identification to verify the authenticity of leaked materials. This lowers noise and verifies that alerts are grounded in real exposure rather than conjecture. RiskProfiler provides your team with verified intelligence so they can react right away if a sensitive roadmap or sales database is exposed in a leak.
RiskProfiler doesn't alert you when your executive documents or customer records appear on a secret forum; it reacts and take them down.
— RiskProfiler CTO Setu Parimi
Contextual Support in the Decision-Making Process
At the heart of RiskProfiler lies a unified dashboard designed for both operational agility and executive oversight. Security teams can track real-time heatmaps showing the origins and nature of threats across platforms and geographies. Meanwhile, decision-makers can evaluate takedown metrics and assess financial exposure through dynamic risk scoring. These scores reflect the evolving footprint of impersonation, credential leaks, and brand abuse.
Additionally, RiskProfiler simplifies reporting with exportable insights tailored for CISOs, CFOs, and compliance leads, bridging the gap between technical depth and strategic clarity. With this dashboard, organizations don’t just react to threats; they orchestrate informed, timely, and coordinated responses that reduce financial loss and reputational damage.
Final Thoughts
Brand impersonation is an active threat to enterprise value and consumer trust. Whether you’re a CFO evaluating budget allocations or a brand lead tasked with reputation management, the message is clear: investing in brand protection delivers tangible financial returns and future-proofs your market credibility.
If your brand is scaling or operating globally, now is the time to audit your exposure and act decisively. Do not become a cybersecurity case study. Be proactive and prevent an incident today.
Brand reputation and goodwill are assets that directly or indirectly influence your enterprise’s market positioning, investor interest, sales growth, or M&A cycle. From phishing scams to counterfeit domains, malicious actors increasingly target high-growth and established brands to exploit consumer trust, drain corporate finances, and weaken market presence. Organizations with previous instances of cyber attacks, a history of phishing scam association, or negative brand impersonation campaigns can lose their market positioning and credibility with their investors and clients.
The average cost of a data breach is far greater than its impact on passive business relationships. Direct sales cycle and corporate onboarding can also be greatly impacted by negative campaigns, brand identity duplications, and impersonation attempts. Your organization would need brand protection tools to detect brand spoofing across the internet and dismantle the threat before it can cost your operational viability.
Average Cost of a Data Breach and Brand Impersonation
Earlier, we mentioned how brand impersonation attacks can cost your organization’s reputation and operational continuity. The loss of credibility and operational impact causes active strain on the organization’s financial performance and revenue. Whether through phishing emails that mimic your brand, rogue websites that clone your storefront, or malicious actors leaking documents and PII on the dark web, these threats have direct consequences on your brand revenue.
For CFOs, brand leads, and legal teams, it’s critical to understand how these attacks translate into real costs, whether financial, reputational, or operational, and how the aftermath can ripple across investor relations, acquisition timelines, and long-term brand equity.
Direct Financial Losses from Fraud and Breach Response
According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach has reached $4.88 million, a 10% surge over the previous year. The study reveals that most of these breaches stem from vectors like phishing, stolen credentials, or social engineering, which are frequently fueled by brand impersonation attacks.
When attackers use your logo, executive names, or cloned login portals to deceive customers or employees, the financial fallout is swift and severe. Funds are drained through fraudulent transfers, remediation efforts escalate overnight, and the absence of automated detection only stretches the process further, allowing the damage to multiply in a limited timeframe. Organizations without intelligent response capabilities often spend over $1.8 million more on average to contain such incidents, highlighting how underinvestment in early detection leads to exponential costs later.
Reputational Damage and Customer Attrition
Once the news of a brand impersonation or data breach becomes public, your security strategy, along with your brand integrity, comes under public and expert scrutiny. Consumers, even the most loyal, are likely to sever ties with companies that fail to safeguard their data. The presence of social media heavily amplifies the damage, eroding the trust of your customer base.
Operational Disruption and Business Paralysis
Brand impersonation and phishing campaigns do not just create external confusion; they disrupt your operational workflows. In many cases, email systems are temporarily shut down to halt suspicious activity, or the operations team gets locked out of their system after an attack. Customer portals are often locked down for investigation, and communication protocols are suspended while damage assessments take place.
During this chaos, customer service SLAs are missed, product launches are delayed, regular operational activities come to a standstill, and entire revenue operations grind to a halt. The operational cost of this paralysis can not be simplified to just the loss of revenue or the recovery cost. It is just not about service downtime either. The problem also extends to lost business opportunities, delayed transactions, and a demoralized workforce navigating uncertainty without clear protocols.
Legal and Regulatory Penalties
Regulatory consequences of brand impersonation-related breaches can be both immediate and long-lasting. Data protection laws such as GDPR, CCPA, and HIPAA impose steep penalties for failures in data governance, even when breaches result from impersonation rather than internal negligence. Under GDPR, fines can soar to €20 million or 4% of annual global revenue, whichever is higher. Beyond statutory fines, companies may also face class-action lawsuits, shareholder suits, or forced disclosures that further compound financial risk. When attackers hijack your brand to deceive users, your legal liability may still be triggered, especially if personal data or financial records are involved.

Loss of Stakeholder and Investor Trust
One of the most understated yet relevant impacts of impersonation and breach events is the erosion of investor confidence. Share prices often drop in the wake of a breach, but the more subtle but long-lasting damage occurs behind the scenes. Venture capital firms may delay funding decisions. Strategic acquirers may pause M&A discussions. Institutional investors may request security audits or additional risk disclosures before proceeding. These moments of hesitation can derail momentum during critical fundraising or acquisition cycles. The effect of such delays often lasts for the important decision-making process, at times long after the security issue is resolved.
Impact on Sales, Renewals, and Margins
The sales pipeline is particularly vulnerable to brand-related attacks. When prospects see news of an impersonation scam or dark web data leak involving your brand, they grow wary. Cybersecurity preparedness plays an important role in modern business decisions. Without satisfying security reports and previous brand impersonation history, legal teams can cause a delay.
Additionally, in B2C SaaS or subscription-based businesses, the rate of renewals or returning customers takes a plunge as customers lose their trust in your brand. Similarly, all your potential customers also grow wary of your brand, damaging the chances of acquiring a new customer base to a great extent.
Delays in Acquisition and Strategic Partnerships
Brand impersonation events have a particularly harmful effect on high-value business initiatives. Joint ventures, reseller agreements, and strategic alliances may be delayed as partners reevaluate your security readiness and market impact. You may be asked to conduct third-party audits, provide cyber insurance validation, or implement new safeguards before any commercial agreement can resume. The due diligence process becomes longer and more expensive. These delays affect expansion plans, market entry strategies, and competitive positioning in fast-moving industries.
Long-Term Loss of Credibility
While immediate damage can be quantified, the long-term loss of credibility is harder to measure, but just as dangerous. Customers and partners often remember or check back on cyber incidents, but they also remember the impact and threat response strategies. If the incident response was slow, opaque, or inadequate, the reputational damage and subsequent mistrust deepen. Even after systems are secured and reports are filed, the memory of the breach persists. Competitors often seize the opportunity to position themselves as more secure alternatives. Media narratives and analyst briefings subtly shift. In essence, brand impersonation weakens your strategic voice in the market, often for quarters or even years to come.
Brand Impersonation Detection Techniques
Your organization needs immediate and effective brand impersonation detection techniques that can protect your identity, customer trust, and market positioning from threat actors. In this blog, we will be discussing the top brand impersonation detection strategies that can identify and dismantle brand threats before they can affect your enterprise.
Automated Typosquat & Fake Domain Identification
The creation of lookalike domains is one of the most common ways that people impersonate brands. These could make use of typosquatting (typosquatting, or registering misspellings of an approved domain), homograph assaults (replacing similar-looking characters), or minor character appendages that are likely to be overlooked. For example, in brand papers or email inboxes, a domain such as riskprofiIer.io (with a capital “I” in place of the small letter “l”) may not be visually different from the actual 1763986604-74d06f1bdede78c5.wp-transfer.sgvps.net, making unsuspecting users trust and interact with the phishing kits.
Fuzzy logic and Levenshtein distance techniques are used by RiskProfiler to actively monitor global DNS registrations in order to identify these domain modifications at the registration stage. Teams are notified before these domains are utilized in phishing campaigns, ad fraud, or credential harvesting attacks, thanks to proactive monitoring rather than reactive detection. Domain-level detection is one of the most economical ways to prevent brand impersonation because of the low cost of domain registration and the large reward for attackers.
Identification of Rogue Applications
Attackers are increasingly creating rogue mobile applications that mimic legitimate ones outside of domains. In an effort to fool users into installing malware or divulging private information, these impersonations typically have similar names, stolen logos, and mimic real UI/UX elements.
To find these rogue apps on sites like Google Play, the Apple App Store, and third-party APK marketplaces, RiskProfiler combines binary code similarity analysis, certificate comparison, and app store scraping. The platform uses developer platform abuse channels to start takedown operations after detection. This is especially important for financial, retail, and healthcare businesses because customer acquisition and transaction volume are directly impacted by confidence in digital apps.
Identifying Deepfakes in Executive Impersonation
With generative AI tools becoming accessible and operational to all, threat actors can create realistic audio, video, or even live conference calls that mimic the voices and appearances of C-suite executives. These deepfakes are increasingly used in Business Email Compromise (BEC) and executive impersonation campaigns, such as a fabricated video call requesting wire transfers or approval of a confidential transaction.

Discovery of Malicious Brand Mention
Brand impersonation does not always involve technical duplications like fake domains or deepfakes. Often, it begins with small but malicious mentions in hidden corners of the internet or social media conspiracy pages. Attackers frequently discuss scam ideas or offer access to spoof kits before launching full-scale attacks on dark web forums, paste sites, Telegram channels, and social media groups.
RiskProfiler continuously scans these environments for the brand’s name, trademarks, executive references, and associated metadata. Using NLP and entity recognition, it flags potentially harmful mentions, such as phishing templates for sale, social engineering playbooks, or tools crafted to mimic your login page. What sets this apart is the ability to connect these mentions with actual attack attempts, such as correlating a threat actor’s post with a typosquatted domain that appears days later.
By identifying threats at the conversation level, before they mature into infrastructure or campaigns, RiskProfiler delivers predictive threat intelligence, giving organizations a valuable time advantage.
Streamlined Takedown Workflows
Once a brand threat is verified, be it a typosquatted domain, deepfake content, rogue app, or impersonated social handle, organizations must act quickly to minimize risk exposure. Brand intelligence solutions collaborate with hosting sites to streamline the spoofed asset takedown workflow and limit your organization’s threat exposure. That’s where RiskProfiler’s streamlined takedown engine comes into play.
The platform integrates directly with registrar abuse portals, cloud hosting providers, app stores, and social media abuse desks. Each threat type triggers a pre-built workflow: for instance, domain impersonation may launch WHOIS complaints, DMCA filings, or UDRP processes, while rogue app detection initiates developer takedown notices and legal escalations. These workflows are automated, timestamped, and auditable, ensuring compliance and accountability across jurisdictions.
How RiskProfiler Ensures Brand Protection Against Financial Threats
The purpose of RiskProfiler’s brand protection module is to shield companies from external brand threats and misuse of their brand identity. The module automates takedown procedures, contextualizes the alert, and detects spoofing threats in real-time. The platform defends its brand and confronts financial harm in this way.
Continuous Attack Surface Monitoring
RiskProfiler continuously monitors for signs of malicious intent against your brand, including domain registrations that mimic your name using homoglyphs, typos, or deceptive lookalikes. It detects impersonations of executives, recruiters, or brand pages on social media long before they can mislead your stakeholders.
Additionally, code repositories, public paste sites, and cloud platforms are scrutinized for exposed credentials or sensitive documents that could compromise your security posture. In dark web forums and marketplaces, RiskProfiler flags any mentions of your organization, leaked PII data, internal strategy materials, or stolen databases that could be weaponized. This persistent visibility across the internet enables security teams to detect threats before they escalate into breaches.
Threat Detection with Correlated Insights
Threats are identified by RiskProfiler, which then examines them to determine their cause and correlation. It looks into whether activity on a suspicious domain is related to recent breaches, such as employee credentials being leaked or unauthorized logins on your infrastructure. If malicious file hashes appear on malware-sharing forums around the same time, RiskProfiler analyzes all the involved metrics and finds the associations with emerging threat campaigns.
With a contextual narrative about the attacker, their potential intent, and how to react quickly, the security teams are able to investigate threats holistically.

Automated Takedown Procedures with Full Audit History
RiskProfiler’s takedown workflow allows the security team to automate the attack disruption process with a pre-determined strategy. Whether it’s a WHOIS complaint against malicious registrants, a UDRP action against impersonation websites, or a DMCA complaint for content that has been hijacked, the relevant authorities are immediately notified of legal action. These are carried out all over the world, seamlessly navigating through several jurisdictions and working with hosts and registrars to take down malicious properties. SLA-compliant ticketing systems are used for escalation in cases of social impersonation or brand abuse. Every action has a tamper-resistant audit trail, whether it be legal, technical, or procedural. Legal and compliance teams do use this transparency as evidence when conducting internal audits, regulatory reviews, or even courtroom defense.
Proactive Protection Against Dark Web Data Leaks
RiskProfiler scrapes the illegal corners of the internet to detect mention of your brand, executives, PII, and credentials linked to your employees and customers, and shares detailed threat data on the portal. Unlike generic alerting, RiskProfiler’s dark web intelligence uses pattern analysis and AI-based entity identification to verify the authenticity of leaked materials. This lowers noise and verifies that alerts are grounded in real exposure rather than conjecture. RiskProfiler provides your team with verified intelligence so they can react right away if a sensitive roadmap or sales database is exposed in a leak.
RiskProfiler doesn't alert you when your executive documents or customer records appear on a secret forum; it reacts and take them down.
— RiskProfiler CTO Setu Parimi
Contextual Support in the Decision-Making Process
At the heart of RiskProfiler lies a unified dashboard designed for both operational agility and executive oversight. Security teams can track real-time heatmaps showing the origins and nature of threats across platforms and geographies. Meanwhile, decision-makers can evaluate takedown metrics and assess financial exposure through dynamic risk scoring. These scores reflect the evolving footprint of impersonation, credential leaks, and brand abuse.
Additionally, RiskProfiler simplifies reporting with exportable insights tailored for CISOs, CFOs, and compliance leads, bridging the gap between technical depth and strategic clarity. With this dashboard, organizations don’t just react to threats; they orchestrate informed, timely, and coordinated responses that reduce financial loss and reputational damage.
Final Thoughts
Brand impersonation is an active threat to enterprise value and consumer trust. Whether you’re a CFO evaluating budget allocations or a brand lead tasked with reputation management, the message is clear: investing in brand protection delivers tangible financial returns and future-proofs your market credibility.
If your brand is scaling or operating globally, now is the time to audit your exposure and act decisively. Do not become a cybersecurity case study. Be proactive and prevent an incident today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



