Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Why Enterprises Need Proactive Data Breach Detection in 2025?
Why Enterprises Need Proactive Data Breach Detection in 2025?
Is your enterprise system secured from external risks, zero-day threats, and social engineering attacks? This is a question that every organization needs to find an answer to when sophisticated cyber attacks make regular headlines.
Read Time
7 min read
Posted On
Jul 31, 2025
Social Media
Is your enterprise system secured from external risks, zero-day threats, and social engineering attacks? This is a question that every organization needs to find an answer to when sophisticated cyber attacks make regular headlines. To secure your organizational ecosystem against modern cyber threats, your SOC team needs the power of proactive data breach detection and automated threat response workflows.
Enabling Enterprise data breach detection with real-time threat intelligence and continuous monitoring not only prevents data exposures and breaches but also helps you fortify your infrastructure against ransomware, phishing, zero-day attacks, and other cyber threats. In this article, we will be discussing why you need proactive breach detection and automated data breach management workflows to ensure digital security.
From Reactive to Proactive Data Breach Detection: A Strategic Shift
Cybersecurity was heavily reliant on reactive threat detection and management, even in the last decade. In this type of threat management protocol, the security workflow focuses primarily on identification and containment rather than prevention. Although this kind of protection offers its merits when facing an active breach, the lack of prevention methods allows attackers to gain access and cause business damage before the breaches are identified.
In contrast, proactive threat management modules identify and stop threat vectors from causing damage before they can access your system. Under this security method, the tools monitor your attack surface continuously and detect vulnerabilities across your digital infrastructure as they emerge.
Why Are Proactive Security Measures Important?
Traditional security methods cannot protect your digital environment from stealthy, AI-driven cyberattacks. Proactive security measures help organizations identify and address risks before they can cause any damage to their infrastructure. Here’s why adopting a proactive security approach is crucial in 2025:
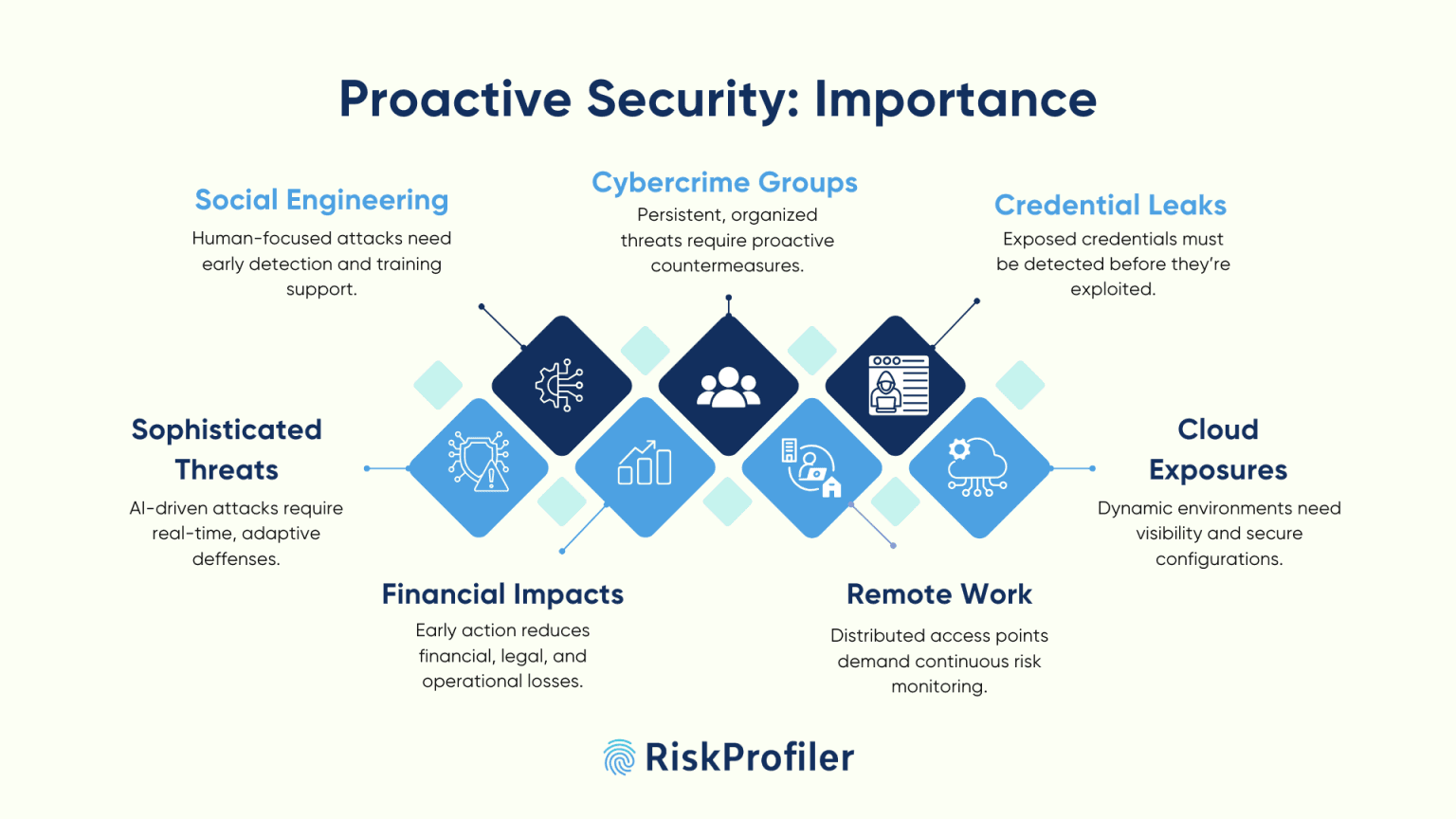
Sophisticated Cyber Threats
Cybercriminals now use advanced tools like AI-generated malware, polymorphic ransomware, and zero-day exploit kits. These threats can map your external attack surface and system weaknesses, easily getting past the detection capabilities of regular firewalls and antivirus solutions. Proactive measures such as real-time cyber threat intelligence, behavior analytics, and anomaly detection are essential to stop these sophisticated threats before they access critical systems.
Rising Financial Impact
The financial cost of cyber breaches continues to rise. The average cost of a data breach is expected to exceed $5 million in 2025. Companies face direct revenue loss, regulatory fines, legal liabilities, and damage to their reputation. Early detection and quick response can significantly lower recovery costs and business interruptions. It also helps avoid regulatory issues and reputational damage, providing better protection against cyber threats.
Remote and Hybrid Work Models
The shift to remote and hybrid work has changed the layout of enterprise IT systems. With employees connecting from various locations, using unmanaged devices, unsecured networks, and accessing company data through personal or third-party applications, the traditional network perimeter has disappeared. Each remote endpoint can become a potential breach point, whether it’s a weak home router, an outdated laptop, or an unapproved SaaS tool.
Proactive threat detection tools are crucial in this setting. They allow security teams to continuously monitor and secure each access point, ensuring that operational flexibility does not compromise cybersecurity.
Sprawling Cloud Networks and SaaS Integrations
Companies increasingly rely on complex cloud systems and third-party SaaS tools for efficiency and growth. However, these systems often lead to issues like shadow IT, misconfigurations, and gaps in data visibility. A proactive security strategy enables management of cloud posture, visibility across multi-cloud environments, and ongoing validation of third-party services.
Credential Leaks on the Dark Web
Leaked employee or executive credentials are some of the most common entry points for attackers. Once these credentials are exposed, they can be used for phishing, account takeovers, and navigating through enterprise systems. Proactive monitoring of the dark web and identity intelligence can detect and respond to these leaks before attackers take advantage of them.
Rise in Organized Cyber Crime Groups
In 2025, cybercrime is increasingly driven by coordinated, well-funded groups that operate like businesses. These threat actors conduct consistent and strategic attack campaigns against large organizations. Proactive defense tools such as honeypots, threat actor profiling, and behavioral analytics can help counter these targeted campaigns before they escalate.
Advanced Social Engineering Threats
Social engineering attacks are more convincing than before due to deepfakes, impersonation bots, and AI-generated content. These tactics manipulate human psychology instead of exploiting technical flaws. Proactive solutions that combine detection of executive impersonation, phishing takedown, and behavioral analytics can help prevent these threats before they reach their targets.
Proactive Data Breach Detection Methods in 2025
Modern enterprises are using a range of advanced data breach detection methods to stay ahead of potential breaches. These tools don’t just watch for known indicators. The proactive cyber threat intelligence modules monitor and identify surface anomalies, lure threat actors, and expose security compromises early in the attack lifecycle.
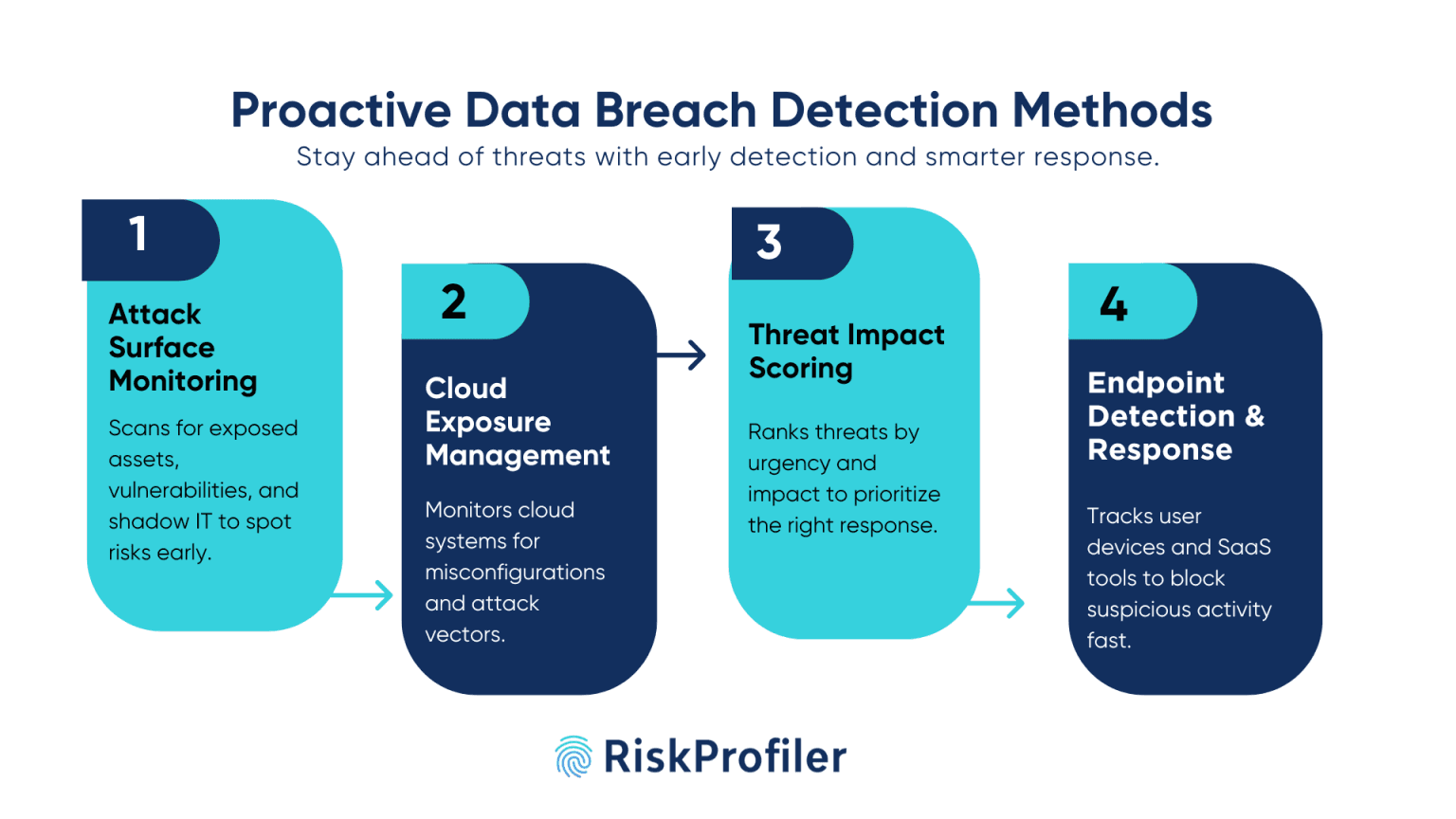
Attack Surface Monitoring and Threat Auditing
Attack surface monitoring is the primary pillar of a proactive data breach detection routine. In this stage, the cyber threat intelligence platform monitors the attack surface for potential threat strains, vulnerabilities, and security gaps. Additionally, the security modules also scan for asset exposures and shadow IT risks that attackers can exploit in an attempt to breach the security protocols.
Cloud Exposure Management
In an organizational workspace where most assets and operations are reliant on cloud services and digital databases, ensuring the safety of the cloud resources is imperative. Thus, cloud threat intelligence tools continuously monitor for cloud asset exposures and attack vectors to ensure threat identification at the initial phase for fast threat response and mitigation.
Threat Impact Scoring
In a sophisticated cyber threat intelligence system, the tool provides the security team with instantaneous alerts of all discovered attack vectors. However, even with proactive detection, it is particularly essential to address the threat most sensitive to time and the organization’s security, along with its financial and reputational impact. Thus, modern data breach detection solutions, such as RiskProfiler, enable threat impact scoring, allowing you to prioritize threats that require immediate attention over the noise.
Endpoint Detection and Response
Cloud ecosystems rely on multiple software tools and services to provide the complete service. However, the integration of numerous SaaS tools and user accounts also introduces a large number of access points to your system. These endpoints, if left unmonitored, can create asset exposure and leave unguarded entryways for attackers to gain access to your system.
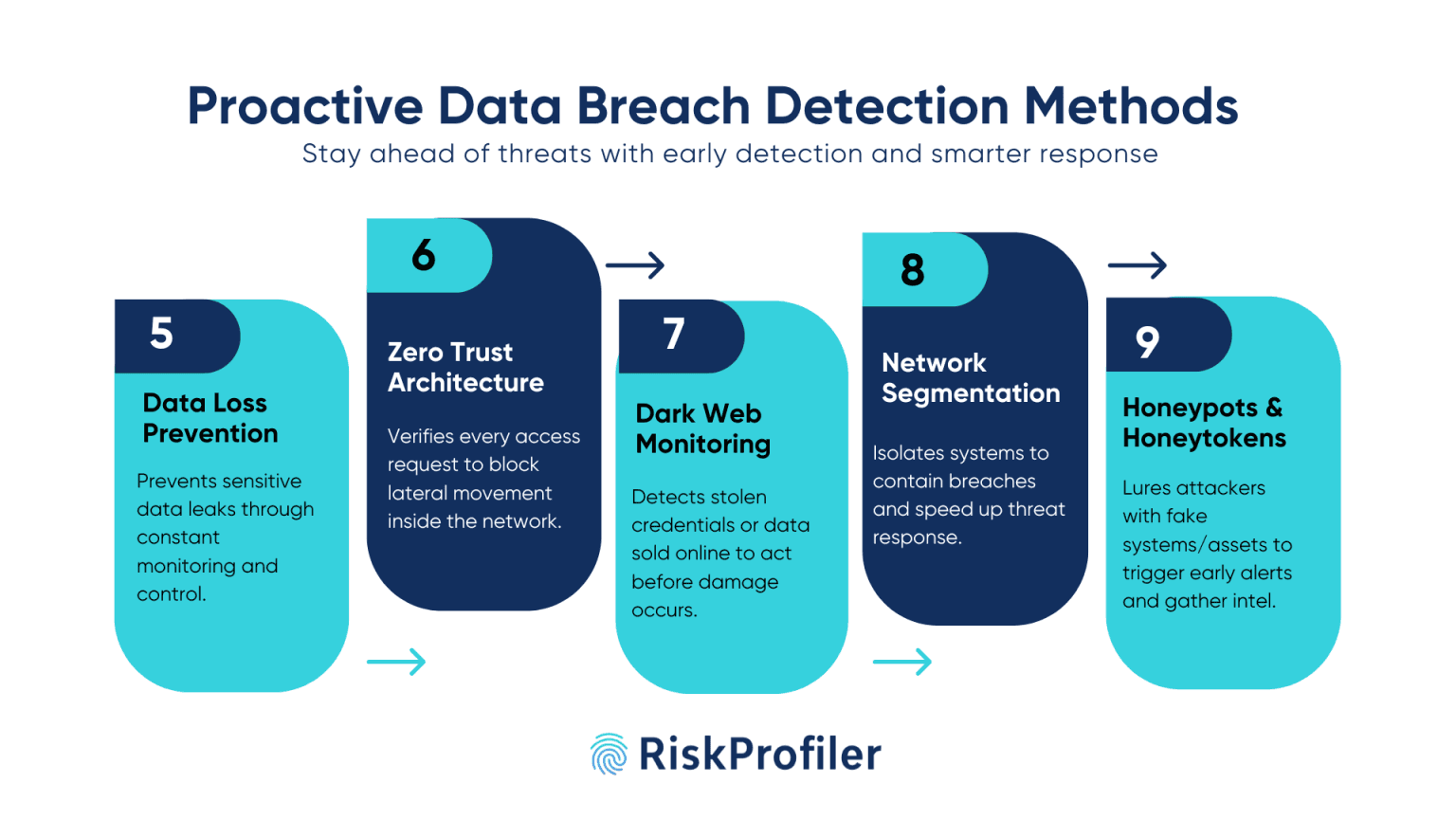
Data Loss Prevention or DLP Solution
Data loss prevention or DLP solutions are systems that ensure your organization’s control over corporate databases and system access. These solutions continuously monitor organizational databases, identify potential data breaches, and alert the system to block further malicious interactions.
Zero Trust Architecture
Zero Trust Architecture or ZTA operates on the principle of “never trust, always verify.” It continuously validates every access request, regardless of its origin, based on identity, context, and device posture. By removing implicit trust, segmenting the network, and applying adaptive access policies, ZTA limits the chances of lateral movement and minimizes breach impact. It ensures that even if attackers gain a foothold, they encounter strict verification at every step, enabling stronger protection for the core assets.
Dark Web Monitoring
Real-time scanning of dark web forums, paste sites, and illicit marketplaces helps detect early signs of stolen credentials, leaked customer data, or internal documents for sale. Fast detection allows the security teams to discover potential exposures in the security system, enabling rapid response to secure the entry points before the threats can exploit them.
Network Segmentation
Segmentation of the corporate network is another useful method for data breach management. Dividing the network into several independent units allows security teams to isolate the affected components at the moment of breach detection, preventing the breach from spreading into other areas of the network. Isolating a particular area also helps the security team to focus their resources better in neutralizing threats, making the mitigation process faster and more effective.
Honeypots and Honeytokens
The use of honeypots and honeytokens is a proactive data breach detection method to identify attack tactics and strategize suitable security plans. Honeypot networks are usually created using pseudo digital assets to monitor and analyze attack movement, strategy, methods, and target when they gain access to a target network.
However, honeytokens are pseudo-assets planted in a network to detect unauthorized access. Any interaction with such items sends alerts to the security system, notifying it of possible intrusion.
The ROI of Early Enterprise Data Breach Detection
The benefits of implementing proactive enterprise data breach detection tools extend far beyond early threat identification and containment. Effective detection of data breaches makes threat management efficient and reduces the chances of penalties.
Reduced Dwell Time
Faster data breach detection allows security teams to contain threats early, or at times before the breach happens. This prevents attackers from gaining access to the organizational database, reducing potential asset corruption, downtime, and recovery costs. Early containment or breach prevention also prevents attackers from stealing large databases, reducing the risk of data leaks.
Lower Breach Costs
The cost of a breach in 2025 is projected to exceed $10 trillion globally, with an estimated average cost of $5 million for the affected businesses. In the wake of a data breach, organizations face more than literal financial loss. The loss of operational hours in downtime, the cost of data leaks, and legal fees accumulate on top of the direct losses, creating huge liabilities for businesses. With early data breach detection, enterprises can avoid all these risks.
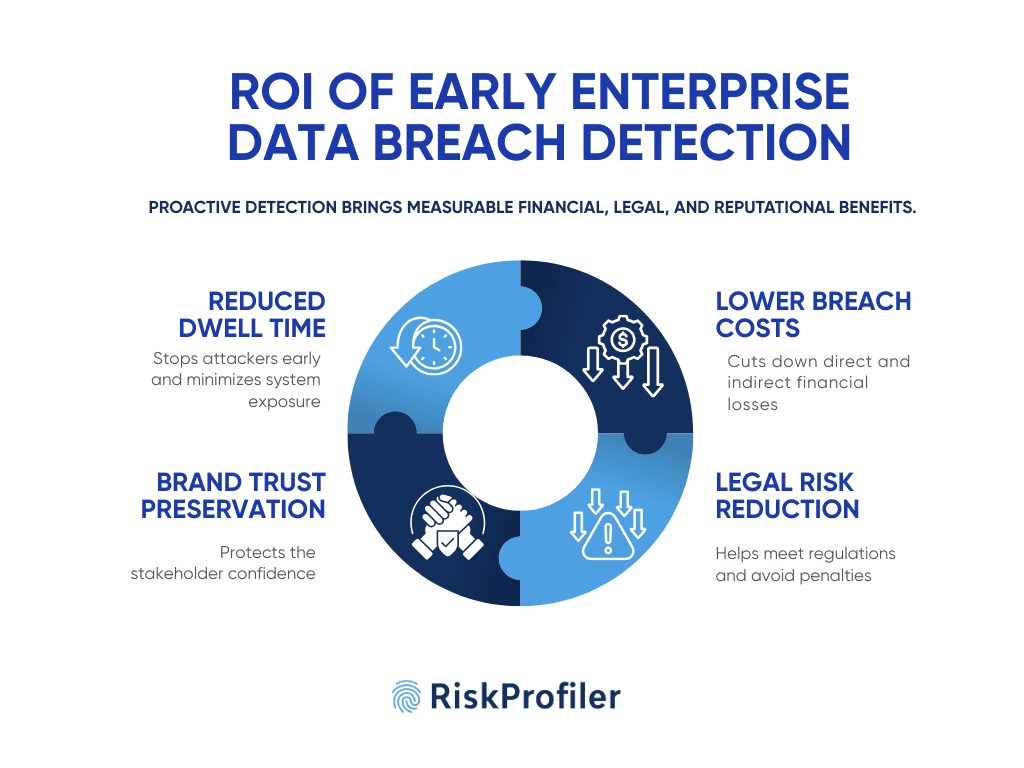
Compliance and Legal Risk Reduction
Regulation frameworks are particularly stringent on data security practices. An incident of data breach or leak will reflect poorly on the organization’s compliance record. A breach due to ignorance will only hike up the penalties, causing severe damage to the brand’s reputation. Proactive breach detection allows fast mitigation, allowing businesses to avoid penalties.
Brand Trust Preservation
An incident of data breach can damage your brand reputation. Your organization’s credibility will sustain considerable damage from both stakeholders and clients, making survival or recovery much more difficult. A proper enterprise data breach detection system allows organizations to avoid these events, allowing them to maintain credibility with customers, partners, and peers.
Proactive Breach Detection & Remediation with RiskProfiler
RiskProfiler provides comprehensive visibility into the attack surface and real-time cyber threat intelligence with contextualized details for advanced data breach detection. By unifying external threat detection across multiple vectors, RiskProfiler enables proactive defense across your entire digital footprint.
1. Proactive Attack Surface Intelligence or ASI
RiskProfiler’s attack surface intelligence continuously monitors your digital footprint across domains and subdomains to exposed ports, shadow IT infrastructure, and forgotten assets. As enterprise environments expand, so do their weak points and security blind spots. RiskProfiler’s EASM modules ensure that new exposures, abandoned assets, shadow IT structures, or misconfigured endpoints are flagged immediately, reducing the window of opportunity for attackers to exploit overlooked vulnerabilities.
2. Cloud Threat Exposure Management or CTEM
The cloud threat exposure management modules from RiskProfiler identify cloud exposures such as unsecured storage buckets, over-permissive access policies, and rogue IP requests that fall outside official governance. Mapping your cloud environment and connecting exposures to likely attack scenarios allows your team to identify the system weaknesses and remediate them on time, before these threats can be discovered or exploited by the adversaries.
3. Third-Party Risk Management
RiskProfiler’s third-party risk intelligence continuously monitors your supply chain ecosystem and highlights exposed assets, leaked data, or active compromises linked to your partners. This allows security teams to respond quickly to indirect threats and reevaluate trust in vendor relationships before damage occurs. RiskProfiler also replaces traditional static vendor risk questionnaires with dynamic vendor risk questionnaires, helping your security team stay ahead of the evolving threat posture in real-time.
4. Identity Intelligence
RiskProfiler proactively uncovers compromised corporate credentials and leaked customer data across underground forums, exposed cloud assets, public code repositories, breach dumps, and deep web sources. It also detects impersonation attempts, such as executive spoofing, online doxxing attempts, and fake login portals designed to trick employees. This kind of insight helps security teams intervene before credentials are weaponized in phishing or lateral movement campaigns.
5. Dark Web Intelligence
RiskProfiler dark web threat intelligence and data breach detection tools crawl illicit forums, paste sites, and hacker marketplaces to identify when your organization’s sensitive data, credentials, or internal documents surface on these sites. Whether it is a malicious conversation mentioning your brand, breach indicators, active targeted attack plans, or exploitation campaigns, RiskProfiler brings this intelligence directly into your SOC’s view, turning obscure risks into actionable signals.
6. Phishing Intelligence
Phishing and social engineering are among the most common causes behind modern breaches and ransomware threats. RiskProfiler tracks phishing infrastructure targeting your organization, identifying cloned login pages, typosquatted domains, and credential harvesting attempts before your users and employees can fall prey to the duplicitous campaigns. Combined with brand impersonation detection, this capability enables early takedown and response, significantly reducing the risk of successful phishing-based compromise.
Final Thoughts
Your business needs continuous vigilance to emerge as a true victor against sophisticated cyber threats. When coupled with advanced threat intelligence and automated remediation workflows, the proactive security tools neutralize threats that can otherwise slip under the nose of traditional security measures. Securing the cloud attack surface, fast detection of credential exposures, abandoned assets, and suspicious traffic requests should be prioritized by every business, regardless of its size or global expansion.
Cyber threats can come from anywhere, anytime, and in all forms and sizes. Why wait for reactive cybersecurity when you can prevent threats even before they reach your domains?
Attackers are fast. It is time to be faster & smarter. Secure your digital ecosystem with RiskProfiler’s proactive threat intelligence today for a safer, more scalable tomorrow.
Want to know more? Book a personalized call with RiskProfiler cybersecurity experts today.
Is your enterprise system secured from external risks, zero-day threats, and social engineering attacks? This is a question that every organization needs to find an answer to when sophisticated cyber attacks make regular headlines. To secure your organizational ecosystem against modern cyber threats, your SOC team needs the power of proactive data breach detection and automated threat response workflows.
Enabling Enterprise data breach detection with real-time threat intelligence and continuous monitoring not only prevents data exposures and breaches but also helps you fortify your infrastructure against ransomware, phishing, zero-day attacks, and other cyber threats. In this article, we will be discussing why you need proactive breach detection and automated data breach management workflows to ensure digital security.
From Reactive to Proactive Data Breach Detection: A Strategic Shift
Cybersecurity was heavily reliant on reactive threat detection and management, even in the last decade. In this type of threat management protocol, the security workflow focuses primarily on identification and containment rather than prevention. Although this kind of protection offers its merits when facing an active breach, the lack of prevention methods allows attackers to gain access and cause business damage before the breaches are identified.
In contrast, proactive threat management modules identify and stop threat vectors from causing damage before they can access your system. Under this security method, the tools monitor your attack surface continuously and detect vulnerabilities across your digital infrastructure as they emerge.
Why Are Proactive Security Measures Important?
Traditional security methods cannot protect your digital environment from stealthy, AI-driven cyberattacks. Proactive security measures help organizations identify and address risks before they can cause any damage to their infrastructure. Here’s why adopting a proactive security approach is crucial in 2025:
Sophisticated Cyber Threats
Cybercriminals now use advanced tools like AI-generated malware, polymorphic ransomware, and zero-day exploit kits. These threats can map your external attack surface and system weaknesses, easily getting past the detection capabilities of regular firewalls and antivirus solutions. Proactive measures such as real-time cyber threat intelligence, behavior analytics, and anomaly detection are essential to stop these sophisticated threats before they access critical systems.
Rising Financial Impact
The financial cost of cyber breaches continues to rise. The average cost of a data breach is expected to exceed $5 million in 2025. Companies face direct revenue loss, regulatory fines, legal liabilities, and damage to their reputation. Early detection and quick response can significantly lower recovery costs and business interruptions. It also helps avoid regulatory issues and reputational damage, providing better protection against cyber threats.
Remote and Hybrid Work Models
The shift to remote and hybrid work has changed the layout of enterprise IT systems. With employees connecting from various locations, using unmanaged devices, unsecured networks, and accessing company data through personal or third-party applications, the traditional network perimeter has disappeared. Each remote endpoint can become a potential breach point, whether it’s a weak home router, an outdated laptop, or an unapproved SaaS tool.
Proactive threat detection tools are crucial in this setting. They allow security teams to continuously monitor and secure each access point, ensuring that operational flexibility does not compromise cybersecurity.

Sprawling Cloud Networks and SaaS Integrations
Companies increasingly rely on complex cloud systems and third-party SaaS tools for efficiency and growth. However, these systems often lead to issues like shadow IT, misconfigurations, and gaps in data visibility. A proactive security strategy enables management of cloud posture, visibility across multi-cloud environments, and ongoing validation of third-party services.
Credential Leaks on the Dark Web
Leaked employee or executive credentials are some of the most common entry points for attackers. Once these credentials are exposed, they can be used for phishing, account takeovers, and navigating through enterprise systems. Proactive monitoring of the dark web and identity intelligence can detect and respond to these leaks before attackers take advantage of them.
Rise in Organized Cyber Crime Groups
In 2025, cybercrime is increasingly driven by coordinated, well-funded groups that operate like businesses. These threat actors conduct consistent and strategic attack campaigns against large organizations. Proactive defense tools such as honeypots, threat actor profiling, and behavioral analytics can help counter these targeted campaigns before they escalate.
Advanced Social Engineering Threats
Social engineering attacks are more convincing than before due to deepfakes, impersonation bots, and AI-generated content. These tactics manipulate human psychology instead of exploiting technical flaws. Proactive solutions that combine detection of executive impersonation, phishing takedown, and behavioral analytics can help prevent these threats before they reach their targets.
Proactive Data Breach Detection Methods in 2025
Modern enterprises are using a range of advanced data breach detection methods to stay ahead of potential breaches. These tools don’t just watch for known indicators. The proactive cyber threat intelligence modules monitor and identify surface anomalies, lure threat actors, and expose security compromises early in the attack lifecycle.

Attack Surface Monitoring and Threat Auditing
Attack surface monitoring is the primary pillar of a proactive data breach detection routine. In this stage, the cyber threat intelligence platform monitors the attack surface for potential threat strains, vulnerabilities, and security gaps. Additionally, the security modules also scan for asset exposures and shadow IT risks that attackers can exploit in an attempt to breach the security protocols.
Cloud Exposure Management
In an organizational workspace where most assets and operations are reliant on cloud services and digital databases, ensuring the safety of the cloud resources is imperative. Thus, cloud threat intelligence tools continuously monitor for cloud asset exposures and attack vectors to ensure threat identification at the initial phase for fast threat response and mitigation.
Threat Impact Scoring
In a sophisticated cyber threat intelligence system, the tool provides the security team with instantaneous alerts of all discovered attack vectors. However, even with proactive detection, it is particularly essential to address the threat most sensitive to time and the organization’s security, along with its financial and reputational impact. Thus, modern data breach detection solutions, such as RiskProfiler, enable threat impact scoring, allowing you to prioritize threats that require immediate attention over the noise.
Endpoint Detection and Response
Cloud ecosystems rely on multiple software tools and services to provide the complete service. However, the integration of numerous SaaS tools and user accounts also introduces a large number of access points to your system. These endpoints, if left unmonitored, can create asset exposure and leave unguarded entryways for attackers to gain access to your system.

Data Loss Prevention or DLP Solution
Data loss prevention or DLP solutions are systems that ensure your organization’s control over corporate databases and system access. These solutions continuously monitor organizational databases, identify potential data breaches, and alert the system to block further malicious interactions.
Zero Trust Architecture
Zero Trust Architecture or ZTA operates on the principle of “never trust, always verify.” It continuously validates every access request, regardless of its origin, based on identity, context, and device posture. By removing implicit trust, segmenting the network, and applying adaptive access policies, ZTA limits the chances of lateral movement and minimizes breach impact. It ensures that even if attackers gain a foothold, they encounter strict verification at every step, enabling stronger protection for the core assets.
Dark Web Monitoring
Real-time scanning of dark web forums, paste sites, and illicit marketplaces helps detect early signs of stolen credentials, leaked customer data, or internal documents for sale. Fast detection allows the security teams to discover potential exposures in the security system, enabling rapid response to secure the entry points before the threats can exploit them.
Network Segmentation
Segmentation of the corporate network is another useful method for data breach management. Dividing the network into several independent units allows security teams to isolate the affected components at the moment of breach detection, preventing the breach from spreading into other areas of the network. Isolating a particular area also helps the security team to focus their resources better in neutralizing threats, making the mitigation process faster and more effective.
Honeypots and Honeytokens
The use of honeypots and honeytokens is a proactive data breach detection method to identify attack tactics and strategize suitable security plans. Honeypot networks are usually created using pseudo digital assets to monitor and analyze attack movement, strategy, methods, and target when they gain access to a target network.
However, honeytokens are pseudo-assets planted in a network to detect unauthorized access. Any interaction with such items sends alerts to the security system, notifying it of possible intrusion.
The ROI of Early Enterprise Data Breach Detection
The benefits of implementing proactive enterprise data breach detection tools extend far beyond early threat identification and containment. Effective detection of data breaches makes threat management efficient and reduces the chances of penalties.
Reduced Dwell Time
Faster data breach detection allows security teams to contain threats early, or at times before the breach happens. This prevents attackers from gaining access to the organizational database, reducing potential asset corruption, downtime, and recovery costs. Early containment or breach prevention also prevents attackers from stealing large databases, reducing the risk of data leaks.
Lower Breach Costs
The cost of a breach in 2025 is projected to exceed $10 trillion globally, with an estimated average cost of $5 million for the affected businesses. In the wake of a data breach, organizations face more than literal financial loss. The loss of operational hours in downtime, the cost of data leaks, and legal fees accumulate on top of the direct losses, creating huge liabilities for businesses. With early data breach detection, enterprises can avoid all these risks.

Compliance and Legal Risk Reduction
Regulation frameworks are particularly stringent on data security practices. An incident of data breach or leak will reflect poorly on the organization’s compliance record. A breach due to ignorance will only hike up the penalties, causing severe damage to the brand’s reputation. Proactive breach detection allows fast mitigation, allowing businesses to avoid penalties.
Brand Trust Preservation
An incident of data breach can damage your brand reputation. Your organization’s credibility will sustain considerable damage from both stakeholders and clients, making survival or recovery much more difficult. A proper enterprise data breach detection system allows organizations to avoid these events, allowing them to maintain credibility with customers, partners, and peers.
Proactive Breach Detection & Remediation with RiskProfiler
RiskProfiler provides comprehensive visibility into the attack surface and real-time cyber threat intelligence with contextualized details for advanced data breach detection. By unifying external threat detection across multiple vectors, RiskProfiler enables proactive defense across your entire digital footprint.
1. Proactive Attack Surface Intelligence or ASI
RiskProfiler’s attack surface intelligence continuously monitors your digital footprint across domains and subdomains to exposed ports, shadow IT infrastructure, and forgotten assets. As enterprise environments expand, so do their weak points and security blind spots. RiskProfiler’s EASM modules ensure that new exposures, abandoned assets, shadow IT structures, or misconfigured endpoints are flagged immediately, reducing the window of opportunity for attackers to exploit overlooked vulnerabilities.
2. Cloud Threat Exposure Management or CTEM
The cloud threat exposure management modules from RiskProfiler identify cloud exposures such as unsecured storage buckets, over-permissive access policies, and rogue IP requests that fall outside official governance. Mapping your cloud environment and connecting exposures to likely attack scenarios allows your team to identify the system weaknesses and remediate them on time, before these threats can be discovered or exploited by the adversaries.
3. Third-Party Risk Management
RiskProfiler’s third-party risk intelligence continuously monitors your supply chain ecosystem and highlights exposed assets, leaked data, or active compromises linked to your partners. This allows security teams to respond quickly to indirect threats and reevaluate trust in vendor relationships before damage occurs. RiskProfiler also replaces traditional static vendor risk questionnaires with dynamic vendor risk questionnaires, helping your security team stay ahead of the evolving threat posture in real-time.
4. Identity Intelligence
RiskProfiler proactively uncovers compromised corporate credentials and leaked customer data across underground forums, exposed cloud assets, public code repositories, breach dumps, and deep web sources. It also detects impersonation attempts, such as executive spoofing, online doxxing attempts, and fake login portals designed to trick employees. This kind of insight helps security teams intervene before credentials are weaponized in phishing or lateral movement campaigns.
5. Dark Web Intelligence
RiskProfiler dark web threat intelligence and data breach detection tools crawl illicit forums, paste sites, and hacker marketplaces to identify when your organization’s sensitive data, credentials, or internal documents surface on these sites. Whether it is a malicious conversation mentioning your brand, breach indicators, active targeted attack plans, or exploitation campaigns, RiskProfiler brings this intelligence directly into your SOC’s view, turning obscure risks into actionable signals.
6. Phishing Intelligence
Phishing and social engineering are among the most common causes behind modern breaches and ransomware threats. RiskProfiler tracks phishing infrastructure targeting your organization, identifying cloned login pages, typosquatted domains, and credential harvesting attempts before your users and employees can fall prey to the duplicitous campaigns. Combined with brand impersonation detection, this capability enables early takedown and response, significantly reducing the risk of successful phishing-based compromise.
Final Thoughts
Your business needs continuous vigilance to emerge as a true victor against sophisticated cyber threats. When coupled with advanced threat intelligence and automated remediation workflows, the proactive security tools neutralize threats that can otherwise slip under the nose of traditional security measures. Securing the cloud attack surface, fast detection of credential exposures, abandoned assets, and suspicious traffic requests should be prioritized by every business, regardless of its size or global expansion.
Cyber threats can come from anywhere, anytime, and in all forms and sizes. Why wait for reactive cybersecurity when you can prevent threats even before they reach your domains?
Attackers are fast. It is time to be faster & smarter. Secure your digital ecosystem with RiskProfiler’s proactive threat intelligence today for a safer, more scalable tomorrow.
Want to know more? Book a personalized call with RiskProfiler cybersecurity experts today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



