Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Attack Path Analysis: How Hackers Chain Vulnerabilities?
Attack Path Analysis: How Hackers Chain Vulnerabilities?
As cyberattacks grow more sophisticated, security teams are realizing that individual vulnerabilities are rarely the whole story.
Read Time
7 min read
Posted On
Mar 28, 2025
Social Media
As cyberattacks grow more sophisticated, security teams are realizing that individual vulnerabilities are rarely the whole story. Instead, attackers are combining multiple weaknesses across systems to quietly move through networks—undetected—until they reach high-value assets. This strategic, step-by-step exploitation is known as chaining vulnerabilities, and it’s a key component of modern cyberattacks. To stop these threats effectively, businesses must embrace attack path analysis—a method of mapping how attackers could exploit interconnected weaknesses to move laterally within a network. By understanding the full attack path, organizations can proactively disrupt the chain and stop breaches before they escalate.
What is an Attack Path?
An attack path is the route an attacker takes through a network to reach a target. It begins with an initial entry point on the external attack surface—often a low-risk vulnerability—and progresses through a sequence of exploitations, misconfigurations, and compromised credentials. This journey ultimately leads to sensitive data, critical infrastructure, or administrative control.
Unlike isolated vulnerabilities, attack paths reflect how seemingly small issues can escalate when chained together. That’s why attack path analysis is so vital: it reveals the full narrative of a potential breach, not just its opening move.
How Hackers Chain Vulnerabilities?
Vulnerability chaining is a tactic where attackers exploit multiple, seemingly unrelated security gaps to create a clear path toward compromising critical systems. Rather than relying on a single high-impact vulnerability, threat actors piece together a sequence of smaller system weaknesses, each acting as a stepping stone until they reach their target.
A Step-by-Step Example of Vulnerability Chaining:
Let’s break it down with a typical real-world scenario:
Initial Entry: The attacker identifies an exposed, misconfigured cloud storage bucket that grants public read access. On its own, this might not seem dangerous.
Credential Discovery: Within that bucket, they find backup files containing hardcoded credentials.
Privilege Escalation: Using those credentials, they log into a staging server with outdated software. From there, they exploit an unpatched vulnerability to gain administrative privileges.
Lateral Movement: With elevated access, the attacker pivots laterally across systems, searching for sensitive data or critical infrastructure.
Final Impact: They exfiltrate customer data or deploy ransomware, resulting in reputational and financial damage.
Each vulnerability in this chain may appear low-priority in isolation. But when strung together strategically, they form a high-impact attack path—one that is often invisible without proper context.
What Is Lateral Movement?
Once a threat actor breaches the perimeter of your network—whether through phishing, misconfiguration, or a vulnerable exposed asset—their job isn’t done. In fact, it’s just beginning.
Rather than immediately targeting sensitive systems or data, attackers often engage in a stealthy process known as lateral movement. This technique allows them to navigate through the internal network, establish persistence, escalate privileges, and uncover the most valuable assets before launching the final stage of their attack.
How Lateral Movement Works? Step-by-Step Breakdown
Lateral movement is one of the most critical and dangerous phases in a cyberattack. Unlike brute-force attacks or smash-and-grab techniques, lateral movement is subtle, methodical, and designed to blend in with legitimate user behavior. It allows attackers to navigate through an organization’s network, seeking out high-value assets—often without raising any alarms. Here’s how it typically unfolds:
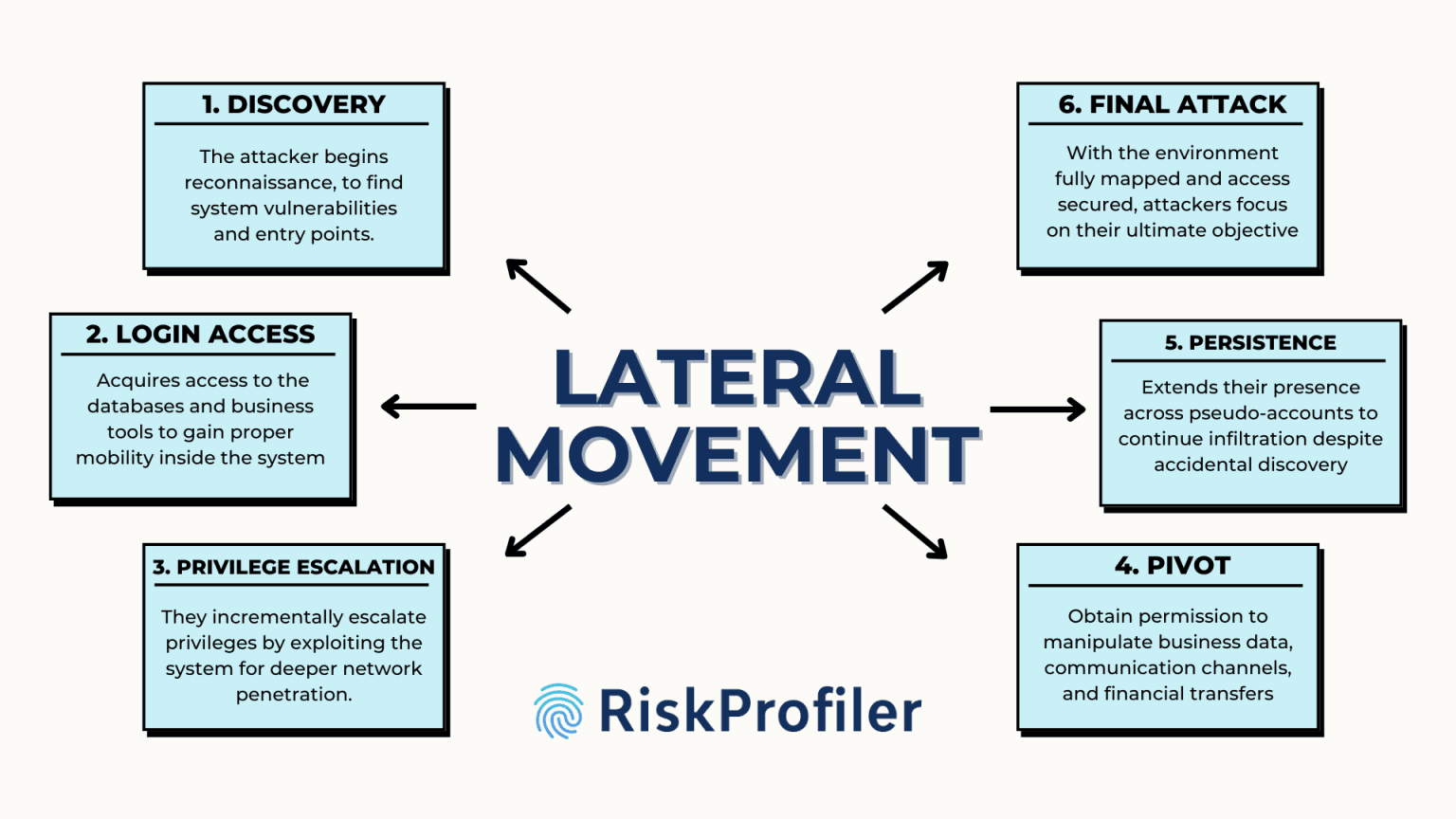
1. Discovery: Scouting the Terrain
Once inside the network—often via a phishing email, compromised VPN, or vulnerable external service—the attacker begins reconnaissance. They survey the internal environment to understand its structure, try to find vulnerable entry points to gain access into the organization’s system. Assets that can be compromised or utilized in this process are:
Nearby hosts and IP ranges
Open ports and running services
Network shares and mapped drives
Active Directory users and group memberships
Logged-in sessions and cached credentials
2. Login Access: Stealing the Keys
Once the attackers gain access to the organization, they try to acquire access to the sensitive databases and business tools to gain proper mobility inside the system. This can be acquired via brute-force attacks, credential harvesting, and other identity theft methods. Credential harvesting, however, can also be conducted using previous data leaks, dark web marketplace credential sales, and via credential dumps. Common techniques include:
Dumping memory from LSASS to extract passwords or hashes (using tools like Mimikatz)
Keylogging or credential scraping
Extracting browser-stored credentials
Capturing NTLM hashes for pass-the-hash or relay attacks
Abusing Single Sign-On (SSO) mechanisms
3. Privilege Escalation: Climbing the Ladder
Gaining access into system accounts does not often offer attackers the mobility and specific visibility that they are aiming for. Hacking into an organization account rarely offers domain admin rights immediately. Instead, they incrementally escalate privileges by exploiting the system and business network. This stage is crucial for enabling deeper network penetration and access to sensitive resources.
Exploiting local vulnerabilities (e.g., unpatched software or misconfigured services)
Weak permissions on scripts, services, or scheduled tasks are abused
Leveraging token impersonation or privilege escalation tools
4. Pivoting: Expanding the Foothold
Once the cyber criminals gain access to sensitive account credentials and higher privileges, the attacker begins to move laterally across systems. They can try and obtain permission to manipulate and edit sensitive business data, communication channels, and financial transfers. To establish their system foothold, the attackers continue to expand their control via the following channels:
Use Remote Desktop Protocol (RDP), PsExec, WMI, or WinRM to access other machines
Jump from one compromised host to another, often chaining tools and scripts to automate the process
Exploit trust relationships between systems (e.g., service accounts reused across servers)
5. Persistence: Staying in the Shadows
Once deep into the system, attackers often extend their presence across pseudo-accounts and users to continue their infiltration despite accidental discovery. Persistence mechanisms allow attackers to re-enter the environment even after reboots or account lockouts. To ensure continued system access, attackers establish persistence by:
Creating new user accounts or adding themselves to administrator groups
Installing backdoors, implants, or remote access trojans (RATs)
Modifying registry entries, startup folders, or scheduled tasks
Abusing legitimate tools (Living off the Land Binaries, or LOLBins) to remain undetected
6. Targeting the Crown Jewels: Mission Accomplished
With the environment fully mapped and access secured, attackers focus on their ultimate objective. This final step often comes swiftly—by the time defenders notice something’s wrong, the damage is already done. The final steps, i.e. attackers’ goal, could include:
Exfiltrating sensitive data such as customer records, intellectual property, or financial reports
Deploying ransomware across the environment to extort payment
Sabotaging systems or disrupting operations for financial, political, or competitive reasons
Why Lateral Movement Is So Dangerous?
Lateral movement is one of the most critical—and dangerous—phases in a modern cyberattack. It represents the transition from initial compromise to full-blown breach, enabling attackers to methodically expand their control within an organization. What makes this stage so alarming is not just the techniques used but the stealth and strategy behind them.
It Buys Time: Once inside, attackers often avoid drawing attention by moving slowly and deliberately. They may monitor user behavior, study internal security measures, and wait for the perfect opportunity to escalate access. In many high-profile breaches, attackers remained undetected for weeks or even months, gathering intel and quietly expanding their foothold.
It’s Hard to Detect: Lateral movement often mimics legitimate administrative activity. Threat actors might use authorized tools like PowerShell or Remote Desktop Protocol (RDP), making their behavior appear routine. Without a comprehensive view of the attack path, these actions blend into the background noise of daily IT operations.
Expands the Blast Radius: What begins as a minor endpoint compromise can escalate dramatically. By hopping between systems and harvesting credentials, attackers can reach critical infrastructure, sensitive data stores, or even gain domain admin privileges, giving them control over the entire environment. The longer they move undetected, the greater the potential damage.
Why Do Traditional Tools Fail At Managing These Threats?
Legacy security tools often operate in silos, focusing narrowly on endpoints, firewalls, or individual vulnerabilities. While they may excel at spotting specific issues, they fall short in one critical area: context.
Modern attacks are no longer linear or isolated. They’re multi-vector, adaptive, and designed to exploit the relationships between assets, misconfigurations, and overlooked gaps. Traditional tools don’t surface these connections. Instead:
Vulnerability scans flag issues in isolation, but they fail to show how multiple weaknesses can chain together to create a viable attack path.
Security alerts are generated in high volumes without understanding which ones actually pose the greatest risk to business operations.
Incident response teams are overwhelmed, often chasing symptoms rather than root causes — because they lack a clear view of how an attacker would move through the environment.
This is where attack path analysis becomes essential. Without it, defenders are flying blind. A seemingly low-priority misconfiguration or forgotten asset can quickly become the starting point for a sophisticated breach. Attackers don’t think in terms of silos — and neither should defenders.
Best Practices to Prevent Chaining and Lateral Movement
Modern attacks exploit chains of vulnerabilities and move laterally across networks. Preventing this requires a proactive defense strategy focused on visibility, segmentation, and identity control—guided by real-time attack path analysis for maximum effectiveness.
1. Continuously Monitor the Attack Surface
The external attack surface is dynamic, constantly changing with new applications, cloud instances, domains, and user behaviors. Continuous discovery and monitoring help businesses detect unknown or unmanaged assets, exposed ports, and risky misconfigurations in real time. Staying vigilant ensures that the security team identifies and mitigates potential entry points across cloud attack surfaces before attackers can exploit them.
2. Apply Zero Trust Principles
Zero Trust adopts a “never trust, always verify” mindset, requiring continuous validation of every access request, regardless of its origin. Ensuring that all users, devices, and services are authenticated and authorized before gaining access it minimizes the attacker’s ability to move laterally across the network if initial compromise occurs.
3. Enforce Network Segmentation
Network segmentation divides your infrastructure into controlled zones, limiting the pathways an attacker can take after breaching a system. It creates boundaries that contain threats and prevent them from spreading unchecked. Even if a device is compromised, segmentation ensures critical systems remain isolated, reducing the blast radius of any breach.
4. Patch Prioritized Vulnerabilities First
Not all vulnerabilities pose the same level of risk. Prioritizing patches based on their location in attack paths, exploitability, and potential security and financial impact helps close off high-leverage weaknesses first. This strategic approach disrupts an attacker’s ability to chain exploits together, protecting the most likely paths they would use to move through your environment.
5. Leverage Threat Modeling
Threat modeling provides insight into how attackers might navigate your systems by simulating potential attack scenarios. It allows teams to think like adversaries, identify vulnerable points, and reinforce security before threats materialize. By proactively mapping likely exploit routes, organizations can harden defenses around critical assets and reduce lateral movement opportunities.
6. Use Access Intelligence
Access intelligence gives visibility into how identities, users, and services interact across environments. It helps identify over-permissioned accounts, stale credentials, and excessive access that attackers often exploit for lateral movement. By analyzing identity behavior and access patterns, you can detect risky privileges and enforce least privilege principles more effectively.
How RiskProfiler Strengthens Security with Attack Path Analysis?
RiskProfiler maps your entire external attack surface, including unknown and shadow IT assets, to continuously monitor for exposures and system vulnerabilities. By leveraging contextual intelligence and attack path modeling, we give security teams the insight they need to understand and disrupt digital attacks before they unfold.
With RiskProfiler’s attack path analysis, you can:
Visualize real-world attack paths across your digital footprint, identifying how an attacker could move laterally or escalate privileges across cloud services, exposed APIs, remote access points, and third-party connections.
Uncover vulnerability chains involving combinations of misconfigurations, outdated software, and exposed assets that form viable paths to critical systems and data.
Detect chokepoints and high-risk nodes in your environment, enabling you to reduce the attacker’s mobility by proactively segmenting or securing weak links.
Prioritize remediation based on actual risk, not just CVSS scores, so your team can focus on high-impact security threats first, improving effectiveness and reducing risks.
By combining external attack surface intelligence with advanced analytics and threat context, RiskProfiler enables organizations to move from reactive to proactive. You gain visibility not just into “what’s vulnerable” but also how attackers could exploit it, empowering you to break the attack chain before the threat materializes or escalates.
Conclusion: Break the Chain Before It Begins
Modern cyberattacks rely on exploiting relationships between systems, not just flaws in isolation. Understanding how attackers think—how they chain weaknesses and move laterally—is the key to stopping them.
That’s why attack path analysis isn’t just a nice-to-have; it’s a must. With RiskProfiler, you gain the clarity and control needed to see threats in context and eliminate them at the source.
Ready to see how RiskProfiler’s attack path analysis can protect your business?
Request a demo and take control of your security posture today.
As cyberattacks grow more sophisticated, security teams are realizing that individual vulnerabilities are rarely the whole story. Instead, attackers are combining multiple weaknesses across systems to quietly move through networks—undetected—until they reach high-value assets. This strategic, step-by-step exploitation is known as chaining vulnerabilities, and it’s a key component of modern cyberattacks. To stop these threats effectively, businesses must embrace attack path analysis—a method of mapping how attackers could exploit interconnected weaknesses to move laterally within a network. By understanding the full attack path, organizations can proactively disrupt the chain and stop breaches before they escalate.
What is an Attack Path?
An attack path is the route an attacker takes through a network to reach a target. It begins with an initial entry point on the external attack surface—often a low-risk vulnerability—and progresses through a sequence of exploitations, misconfigurations, and compromised credentials. This journey ultimately leads to sensitive data, critical infrastructure, or administrative control.
Unlike isolated vulnerabilities, attack paths reflect how seemingly small issues can escalate when chained together. That’s why attack path analysis is so vital: it reveals the full narrative of a potential breach, not just its opening move.
How Hackers Chain Vulnerabilities?
Vulnerability chaining is a tactic where attackers exploit multiple, seemingly unrelated security gaps to create a clear path toward compromising critical systems. Rather than relying on a single high-impact vulnerability, threat actors piece together a sequence of smaller system weaknesses, each acting as a stepping stone until they reach their target.
A Step-by-Step Example of Vulnerability Chaining:
Let’s break it down with a typical real-world scenario:
Initial Entry: The attacker identifies an exposed, misconfigured cloud storage bucket that grants public read access. On its own, this might not seem dangerous.
Credential Discovery: Within that bucket, they find backup files containing hardcoded credentials.
Privilege Escalation: Using those credentials, they log into a staging server with outdated software. From there, they exploit an unpatched vulnerability to gain administrative privileges.
Lateral Movement: With elevated access, the attacker pivots laterally across systems, searching for sensitive data or critical infrastructure.
Final Impact: They exfiltrate customer data or deploy ransomware, resulting in reputational and financial damage.
Each vulnerability in this chain may appear low-priority in isolation. But when strung together strategically, they form a high-impact attack path—one that is often invisible without proper context.
What Is Lateral Movement?
Once a threat actor breaches the perimeter of your network—whether through phishing, misconfiguration, or a vulnerable exposed asset—their job isn’t done. In fact, it’s just beginning.
Rather than immediately targeting sensitive systems or data, attackers often engage in a stealthy process known as lateral movement. This technique allows them to navigate through the internal network, establish persistence, escalate privileges, and uncover the most valuable assets before launching the final stage of their attack.
How Lateral Movement Works? Step-by-Step Breakdown
Lateral movement is one of the most critical and dangerous phases in a cyberattack. Unlike brute-force attacks or smash-and-grab techniques, lateral movement is subtle, methodical, and designed to blend in with legitimate user behavior. It allows attackers to navigate through an organization’s network, seeking out high-value assets—often without raising any alarms. Here’s how it typically unfolds:

1. Discovery: Scouting the Terrain
Once inside the network—often via a phishing email, compromised VPN, or vulnerable external service—the attacker begins reconnaissance. They survey the internal environment to understand its structure, try to find vulnerable entry points to gain access into the organization’s system. Assets that can be compromised or utilized in this process are:
Nearby hosts and IP ranges
Open ports and running services
Network shares and mapped drives
Active Directory users and group memberships
Logged-in sessions and cached credentials
2. Login Access: Stealing the Keys
Once the attackers gain access to the organization, they try to acquire access to the sensitive databases and business tools to gain proper mobility inside the system. This can be acquired via brute-force attacks, credential harvesting, and other identity theft methods. Credential harvesting, however, can also be conducted using previous data leaks, dark web marketplace credential sales, and via credential dumps. Common techniques include:
Dumping memory from LSASS to extract passwords or hashes (using tools like Mimikatz)
Keylogging or credential scraping
Extracting browser-stored credentials
Capturing NTLM hashes for pass-the-hash or relay attacks
Abusing Single Sign-On (SSO) mechanisms
3. Privilege Escalation: Climbing the Ladder
Gaining access into system accounts does not often offer attackers the mobility and specific visibility that they are aiming for. Hacking into an organization account rarely offers domain admin rights immediately. Instead, they incrementally escalate privileges by exploiting the system and business network. This stage is crucial for enabling deeper network penetration and access to sensitive resources.
Exploiting local vulnerabilities (e.g., unpatched software or misconfigured services)
Weak permissions on scripts, services, or scheduled tasks are abused
Leveraging token impersonation or privilege escalation tools
4. Pivoting: Expanding the Foothold
Once the cyber criminals gain access to sensitive account credentials and higher privileges, the attacker begins to move laterally across systems. They can try and obtain permission to manipulate and edit sensitive business data, communication channels, and financial transfers. To establish their system foothold, the attackers continue to expand their control via the following channels:
Use Remote Desktop Protocol (RDP), PsExec, WMI, or WinRM to access other machines
Jump from one compromised host to another, often chaining tools and scripts to automate the process
Exploit trust relationships between systems (e.g., service accounts reused across servers)
5. Persistence: Staying in the Shadows
Once deep into the system, attackers often extend their presence across pseudo-accounts and users to continue their infiltration despite accidental discovery. Persistence mechanisms allow attackers to re-enter the environment even after reboots or account lockouts. To ensure continued system access, attackers establish persistence by:
Creating new user accounts or adding themselves to administrator groups
Installing backdoors, implants, or remote access trojans (RATs)
Modifying registry entries, startup folders, or scheduled tasks
Abusing legitimate tools (Living off the Land Binaries, or LOLBins) to remain undetected
6. Targeting the Crown Jewels: Mission Accomplished
With the environment fully mapped and access secured, attackers focus on their ultimate objective. This final step often comes swiftly—by the time defenders notice something’s wrong, the damage is already done. The final steps, i.e. attackers’ goal, could include:
Exfiltrating sensitive data such as customer records, intellectual property, or financial reports
Deploying ransomware across the environment to extort payment
Sabotaging systems or disrupting operations for financial, political, or competitive reasons
Why Lateral Movement Is So Dangerous?
Lateral movement is one of the most critical—and dangerous—phases in a modern cyberattack. It represents the transition from initial compromise to full-blown breach, enabling attackers to methodically expand their control within an organization. What makes this stage so alarming is not just the techniques used but the stealth and strategy behind them.
It Buys Time: Once inside, attackers often avoid drawing attention by moving slowly and deliberately. They may monitor user behavior, study internal security measures, and wait for the perfect opportunity to escalate access. In many high-profile breaches, attackers remained undetected for weeks or even months, gathering intel and quietly expanding their foothold.
It’s Hard to Detect: Lateral movement often mimics legitimate administrative activity. Threat actors might use authorized tools like PowerShell or Remote Desktop Protocol (RDP), making their behavior appear routine. Without a comprehensive view of the attack path, these actions blend into the background noise of daily IT operations.
Expands the Blast Radius: What begins as a minor endpoint compromise can escalate dramatically. By hopping between systems and harvesting credentials, attackers can reach critical infrastructure, sensitive data stores, or even gain domain admin privileges, giving them control over the entire environment. The longer they move undetected, the greater the potential damage.
Why Do Traditional Tools Fail At Managing These Threats?
Legacy security tools often operate in silos, focusing narrowly on endpoints, firewalls, or individual vulnerabilities. While they may excel at spotting specific issues, they fall short in one critical area: context.
Modern attacks are no longer linear or isolated. They’re multi-vector, adaptive, and designed to exploit the relationships between assets, misconfigurations, and overlooked gaps. Traditional tools don’t surface these connections. Instead:
Vulnerability scans flag issues in isolation, but they fail to show how multiple weaknesses can chain together to create a viable attack path.
Security alerts are generated in high volumes without understanding which ones actually pose the greatest risk to business operations.
Incident response teams are overwhelmed, often chasing symptoms rather than root causes — because they lack a clear view of how an attacker would move through the environment.
This is where attack path analysis becomes essential. Without it, defenders are flying blind. A seemingly low-priority misconfiguration or forgotten asset can quickly become the starting point for a sophisticated breach. Attackers don’t think in terms of silos — and neither should defenders.
Best Practices to Prevent Chaining and Lateral Movement
Modern attacks exploit chains of vulnerabilities and move laterally across networks. Preventing this requires a proactive defense strategy focused on visibility, segmentation, and identity control—guided by real-time attack path analysis for maximum effectiveness.
1. Continuously Monitor the Attack Surface
The external attack surface is dynamic, constantly changing with new applications, cloud instances, domains, and user behaviors. Continuous discovery and monitoring help businesses detect unknown or unmanaged assets, exposed ports, and risky misconfigurations in real time. Staying vigilant ensures that the security team identifies and mitigates potential entry points across cloud attack surfaces before attackers can exploit them.
2. Apply Zero Trust Principles
Zero Trust adopts a “never trust, always verify” mindset, requiring continuous validation of every access request, regardless of its origin. Ensuring that all users, devices, and services are authenticated and authorized before gaining access it minimizes the attacker’s ability to move laterally across the network if initial compromise occurs.
3. Enforce Network Segmentation
Network segmentation divides your infrastructure into controlled zones, limiting the pathways an attacker can take after breaching a system. It creates boundaries that contain threats and prevent them from spreading unchecked. Even if a device is compromised, segmentation ensures critical systems remain isolated, reducing the blast radius of any breach.
4. Patch Prioritized Vulnerabilities First
Not all vulnerabilities pose the same level of risk. Prioritizing patches based on their location in attack paths, exploitability, and potential security and financial impact helps close off high-leverage weaknesses first. This strategic approach disrupts an attacker’s ability to chain exploits together, protecting the most likely paths they would use to move through your environment.
5. Leverage Threat Modeling
Threat modeling provides insight into how attackers might navigate your systems by simulating potential attack scenarios. It allows teams to think like adversaries, identify vulnerable points, and reinforce security before threats materialize. By proactively mapping likely exploit routes, organizations can harden defenses around critical assets and reduce lateral movement opportunities.
6. Use Access Intelligence
Access intelligence gives visibility into how identities, users, and services interact across environments. It helps identify over-permissioned accounts, stale credentials, and excessive access that attackers often exploit for lateral movement. By analyzing identity behavior and access patterns, you can detect risky privileges and enforce least privilege principles more effectively.
How RiskProfiler Strengthens Security with Attack Path Analysis?
RiskProfiler maps your entire external attack surface, including unknown and shadow IT assets, to continuously monitor for exposures and system vulnerabilities. By leveraging contextual intelligence and attack path modeling, we give security teams the insight they need to understand and disrupt digital attacks before they unfold.
With RiskProfiler’s attack path analysis, you can:
Visualize real-world attack paths across your digital footprint, identifying how an attacker could move laterally or escalate privileges across cloud services, exposed APIs, remote access points, and third-party connections.
Uncover vulnerability chains involving combinations of misconfigurations, outdated software, and exposed assets that form viable paths to critical systems and data.
Detect chokepoints and high-risk nodes in your environment, enabling you to reduce the attacker’s mobility by proactively segmenting or securing weak links.
Prioritize remediation based on actual risk, not just CVSS scores, so your team can focus on high-impact security threats first, improving effectiveness and reducing risks.
By combining external attack surface intelligence with advanced analytics and threat context, RiskProfiler enables organizations to move from reactive to proactive. You gain visibility not just into “what’s vulnerable” but also how attackers could exploit it, empowering you to break the attack chain before the threat materializes or escalates.
Conclusion: Break the Chain Before It Begins
Modern cyberattacks rely on exploiting relationships between systems, not just flaws in isolation. Understanding how attackers think—how they chain weaknesses and move laterally—is the key to stopping them.
That’s why attack path analysis isn’t just a nice-to-have; it’s a must. With RiskProfiler, you gain the clarity and control needed to see threats in context and eliminate them at the source.
Ready to see how RiskProfiler’s attack path analysis can protect your business?
Request a demo and take control of your security posture today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



