Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Brand Protection: Impersonation & Phishing Prevention
Brand Protection: Impersonation & Phishing Prevention
Phishing and impersonation attacks have become a persistent threat to businesses worldwide. Cybercriminals exploit brand trust by mimicking legitimate companies to steal sensitive information, defraud customers, damage reputations, or gain unauthorized access for malware and ransomware attacks.
Read Time
7 min read
Posted On
Mar 24, 2025
Social Media
Phishing and impersonation attacks have become a persistent threat to businesses worldwide. Cybercriminals exploit brand trust by mimicking legitimate companies to steal sensitive information, defraud customers, damage reputations, or gain unauthorized access for malware and ransomware attacks. These attacks leverage brand and domain spoofing techniques, such as fake domains, fraudulent emails, and counterfeit social media profiles, to deceive unsuspecting users, employees, or account admins. As phishing tactics grow more sophisticated, businesses must adopt proactive brand protection strategies to prevent cybercriminals from exploiting their identity. In this article, we’ll explore how threat actors use brand and domain spoofing, the risks posed to businesses, and the most effective measures to combat these attacks.
How Threat Actors Exploit Brand Identity?
Malicious entities often use several illicit strategies to confuse and misdirect users to gather personal information, steal finances, or gain access to commence malware or ransomware attacks. To execute these strategies, these entities might mimic your brand creatives, logo, and design, or create counterfeit domains or social media accounts in order to confuse your audience. Some of the most used exploitation techniques are listed as follows.
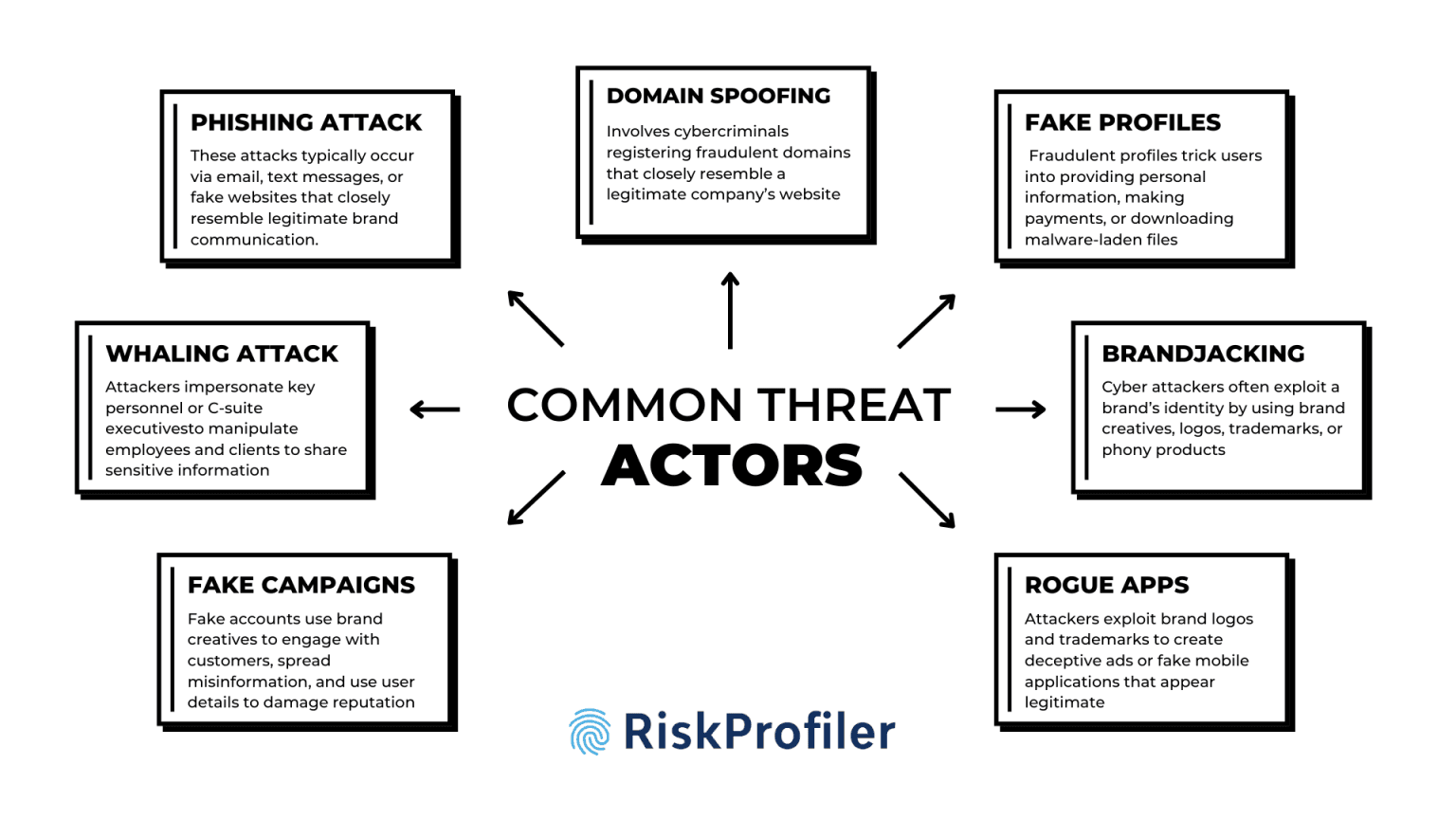
1. Phishing Attacks
Phishing is one of the most common cyber threats, where attackers impersonate a trusted brand to trick individuals into revealing sensitive information, such as login credentials or payment details. These attacks typically occur via email, text messages, or fake websites that closely resemble legitimate brand communication.
For example, cybercriminals may send an email that appears to come from a well-known company, prompting users to click on a malicious link that redirects them to a fake login page. Once the victim enters their credentials, attackers gain access to sensitive accounts, leading to financial fraud or data breaches.
2. Domain Spoofing
Domain spoofing involves cybercriminals registering fraudulent domains that closely resemble a legitimate company’s website. They use subtle misspellings (e.g., g00gle.com instead of google.com) or add extra characters to deceive users. Also known as typosquatting, these counterfeit domains with similar spelling can deceive visitors easily. These fake domains are then used in phishing campaigns or malicious ads to distribute malware or steal data.
Without proactive monitoring, organizations may remain unaware that fake websites are misusing their brand until customers report fraud incidents.
3. Fake Social Media Profiles
Threat actors create counterfeit social media pages that impersonate brands, often targeting customers with fake giveaways, phishing links, or scams. These fraudulent profiles trick users into providing personal information, making payments, or downloading malware-laden files. Additionally, such profiles can also be used to run campaigns harmful to your brand reputation, spreading misinformation about your products, business ethics, or key personnel.
4. Brandjacking
Cyber attackers often exploit a brand’s identity by using brand creatives, logos, trademarks, or phony products. Another popular form of brandjacking in domain spoofing is when cybercriminals create domains with names closely similar to the brand’s name so that a visitor could easily get confused between the two. Using counterfeit websites, brand creatives, copying logos, or other significant identity elements, miscreants can collect sensitive customer data, run phishing campaigns, or sell fake products to bring down your brand image.
5. Malicious Ads & Rogue Mobile Applications
Cybercriminals also exploit brand logos and trademarks to create deceptive ads or fake mobile applications that appear legitimate. Unsuspecting users may download these applications, leading to credential theft, unauthorized transactions, or device compromise. In the long run, it can ruin your brand image, cause damage to your brand reputation, and harm your overall integrity.
6. Whaling Attacks
A whaling attack is a form of phishing attack where cybercriminals mainly target C-suite executives of a business, trying to harm the brand’s reputation. In this kind of attack, malicious actors try to impersonate business CEOs, CTOs, board members, or other key personnel to manipulate business employees and clients to share sensitive information or make unauthorized monetary transactions. In both cases, these kind of attacks can cause severe damage to brand image, result in financial trouble, or leave opening for unsuspecting malware or ransomware attacks.
7. Fraudulent Social Media Campaigns
Malicious actors may also run campaigns that can damage your brand identity and customer reach. The fake accounts use brand creatives to engage with customers, spread misinformation, and use user details that can create confusion in users’ minds and damage your brand identity. Engaging with these fake accounts or dubious content may cause mistrust in your brand and tarnish your brand identity.
Business Risks of Brand & Domain Spoofing
Brand impersonation and domain spoofing are some of the biggest concerns against their public image and brand integrity. Impersonation attempts can dilute audience trust and create a negative impression of the brand while damaging brand integrity. Some of the damages that a brand may incur due to brand impersonation attempts are listed below.
Financial Losses
Cybercriminals leverage domain spoofing and phishing emails to carry out fraudulent activities, causing direct and indirect financial harm to businesses and their customers.
Fraudulent Transactions: Domain spoofing is used to impersonate official business websites, tricking customers into making payments for fake products or services.
Wire Transfer Scams: Attackers send phishing emails from seemingly legitimate corporate domains to deceive employees into authorizing fraudulent wire transfers.
Ransomware & Extortion: Phishing attacks can lead to malware infections that encrypt company data, demanding ransom payments for decryption keys.
Legal Costs & Compensation: Organizations may face lawsuits or be required to compensate affected customers, increasing financial liabilities.
Operational Disruptions: Investigating and mitigating fraud-related incidents diverts resources from core business functions, leading to revenue losses.
Confusing Identities
Brand spoofing creates uncertainty among customers, partners, and even employees, leading to operational inefficiencies and trust erosion.
Customer Confusion: Fake websites and emails closely resembling official communication make it difficult for customers to distinguish between real and fraudulent entities.
Employee Phishing Attacks: Staff members may receive spoofed emails from what appear to be senior executives or IT administrators, leading to unauthorized data sharing or credential leaks.
Supply Chain Attacks: Impersonated domains may be used to deceive suppliers and vendors, leading to incorrect payments, shipment fraud, or disruption of services.
Domain Squatting & Typosquatting: Fraudsters register domains similar to legitimate ones (e.g., “brand-support.com” instead of “brand.com”), leading to misdirected traffic and security vulnerabilities.
Reputation Damage
Brand reputation is one of the most valuable assets of a company, and domain spoofing can significantly harm public perception and customer trust.
Customer Distrust: Victims of phishing scams may associate fraudulent activities with the actual brand, leading to a loss of confidence in its services.
Negative Publicity & Media Coverage: Reports of impersonation-related fraud can tarnish a brand’s image, making it difficult to regain customer loyalty.
Social Media & Review Attacks: Fake accounts impersonating a brand can spread misinformation, damage customer relationships, or post misleading reviews.
Loss of Competitive Edge: If consumers or business partners perceive a brand as insecure or unreliable, they may switch to competitors who have stronger security measures in place.
Data Breaches & Compliance Risks
A successful brand impersonation or phishing attack can lead to unauthorized access to sensitive data, triggering regulatory and legal repercussions.
Customer & Employee Data Theft: Phishing emails can capture login credentials, payment information, and personally identifiable information (PII), exposing individuals to identity theft.
Regulatory Fines & Legal Consequences: Data protection laws, such as the GDPR (General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), impose hefty fines for mishandling or losing sensitive customer data.
Third-Party Compliance Risks: Businesses working with regulated industries (e.g., finance and healthcare) may lose certifications or compliance status due to security breaches.
Intellectual Property Theft: Impersonation attacks targeting executives or R&D teams can lead to the loss of sensitive data such as trade secrets, patents, or strategic business plans.
The longer an impersonation campaign remains undetected, the more damage it can inflict on brand reputation and customer confidence.
Why are Brand Protection Frameworks Necessary?
Integrating a capable brand intelligence tool with good AI and automation support allows your business to stay ahead of phishing, cyber scams, and other impersonation attempts. A good brand risk management tool monitors the surface and dark web to trace any unauthorized mention, product sales, product listing, phishing attempts, domain spoofing, and executive impersonation attempts to ensure brand protection against external threats. An effective brand risk management tool like RiskProfiler monitors the web continuously to detect malicious conversations, collect data on sources, timelines, brand configurations, and executive impersonations, and formulate domain takedown and phishing prevention strategies to enhance brand protection efforts.
Brand Protection and Phishing Prevention: Best Practices
In order to disrupt fraudulent campaigns and prepare practical phishing prevention strategies, organization, and their security teams need to incorporate some advantageous practices into their brand protection efforts. Integrating such practices with strict conditioning allows you to monitor the use of your brand creatives and stay ahead of malicious activities and campaigns at all times, helping you maintain brand integrity and reputation.
1. Domain & Email Security Measures
Your business domain is the main interaction point and trust symbol for your customer and client base. Safeguarding your domain identity from spoofing attempts helps secure your brand legacy from deception.
Implement DMARC, SPF, and DKIM: These email authentication protocols help prevent spoofed emails from being sent on behalf of a brand.
Monitor for Lookalike Domains: Businesses should actively track newly registered domains that mimic their brand name and takedown fraudulent domains and subdomains before they can cause any harm.
2. Digital Risk Protection & Threat Intelligence
Integrating modern AI tools and automated workflows with brand intelligence allows businesses to monitor the surface and dark web spaces continuously. Real-time brand threat intelligence provides organizations with the advantage of proactive intelligence, helping them detect risks and prepare mitigation strategies before the attackers damage the business’s reputation.
Use AI-Powered Threat Detection: Modern brand intelligence solutions integrate artificial intelligence to detect and analyze impersonation attempts across the surface web and social media spaces in real time.
Monitor Brand Mentions & Social Media: Automated tools can scan social platforms, forums, and dark web marketplaces for fraudulent activities and threatening conversations involving a company’s brand identity.
3. Employee & Customer Awareness
Cybercriminals often use phishing technology via email, phone calls, or voice messages to steal sensitive data from your employees and customers. It is essential to run mandatory anti-phishing campaigns inside the organization and on public platforms to help your employees and customers recognize the typical signatures of phishing attacks and the best practices to avoid them.
Employee Training: Organizations should regularly educate employees on how to recognize phishing attempts by mimicking C-suite employees or any third-party vendors. Businesses should also create definite pathways for employees to report phishing attempts to alert their teams of the scams and prevention strategies.
Customer Alerts: Brands should inform customers about ongoing impersonation threats and provide guidelines to verify legitimate communication channels through publicized anti-phishing campaigns.
4. Legal & Takedown Actions
Implementing a good brand risk management solution allows businesses to streamline the takedown efforts for faster and more effective threat mitigation. Brand intelligence tools gather threat intelligence with detailed data on the source, timeline, and threat category to curate idle strategies, aiding in swift domain takedown.
Issuing Cease-and-Desist Notices: Legal teams can act against fraudsters by sending cease-and-desist notices to domain registrars or social media platforms hosting fake accounts.
Collaboration with Cybersecurity Firms: Companies specializing in brand protection can assist in identifying and dismantling phishing sites and fraudulent campaigns.
How Does RiskProfiler Secure Your Brand Against Impersonation & Brand Abuse?
In today’s hyper-digital economy, brand risk is no longer confined to isolated incidents—it is continuous, borderless, and increasingly complex. From domain spoofing and phishing to executive impersonation and counterfeit product listings, digital threats now pose strategic risks to brand equity and consumer trust. RiskProfiler offers a next-generation Brand Intelligence solution, purpose-built to help organizations detect, respond to, and neutralize threats before they impact reputation or revenue.
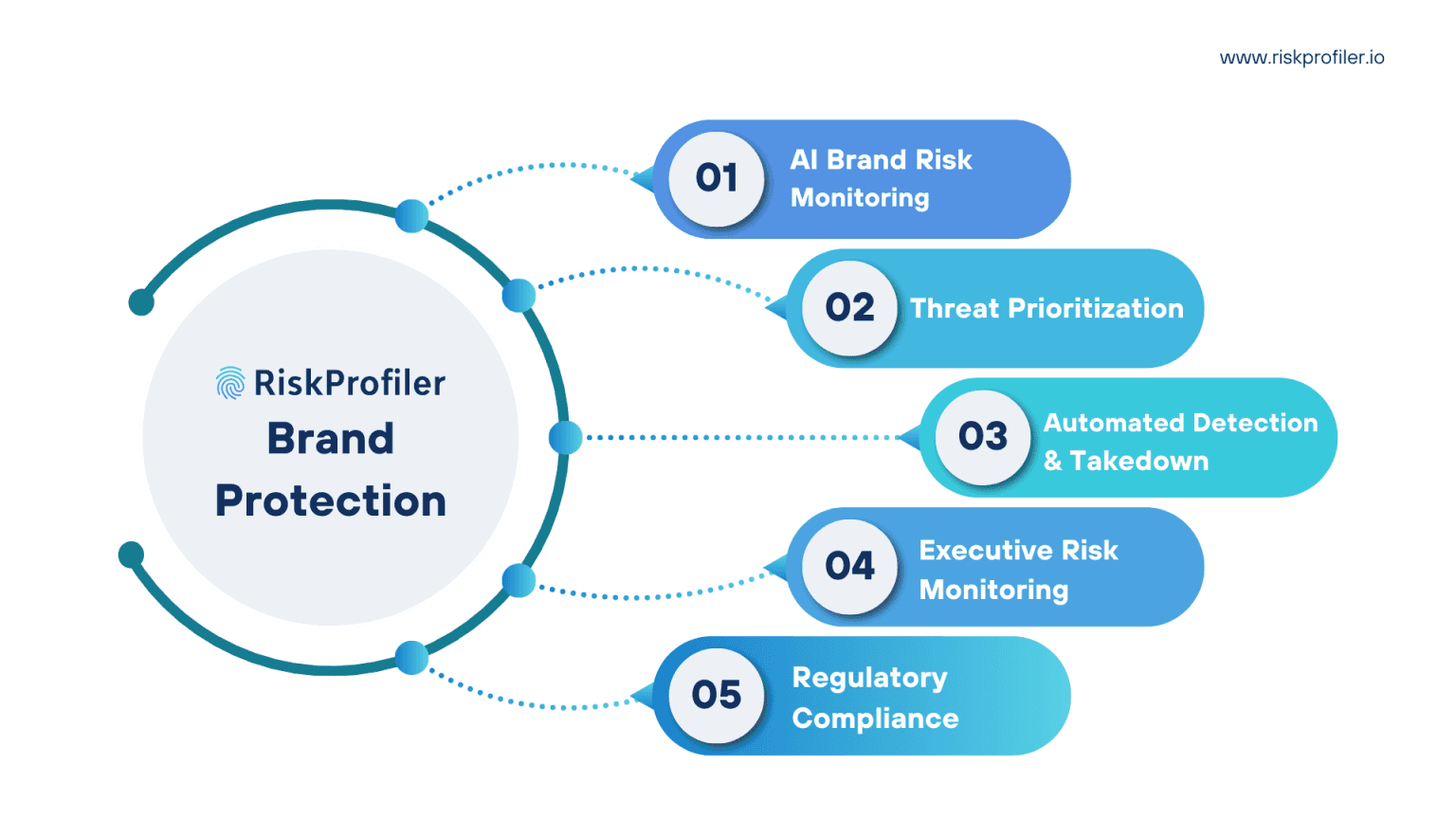
1. Holistic Brand Risk Monitoring
RiskProfiler provides 360-degree visibility into your brand’s digital footprint. The platform continuously monitors websites, social media, online marketplaces, mobile app stores, forums, and the deep/dark web for signs of abuse. Advanced AI models detect patterns across seemingly disconnected threat vectors—ensuring you uncover not just individual incidents but coordinated brand attacks.
2. Real-Time Threat Prioritization
Not all threats are created equal. RiskProfiler intelligently classifies and prioritizes threats using contextual risk scoring—factoring in exposure level, geography, impersonation fidelity, and potential consumer impact. This enables brand protection, legal, and cybersecurity teams to focus on high-impact threats first, optimizing response efforts and resource allocation.
3. Automated Domain Detection & Takedown
Rogue domains are a common tactic in phishing and fraud campaigns. RiskProfiler’s automated domain discovery engine scans millions of new domain registrations daily, using fuzzy logic and visual similarity analysis to detect impersonations. It then orchestrates takedown workflows through registrar partnerships and legal escalation—dramatically reducing response time and operational burden.
4. Executive & VIP Risk Surveillance
The reputational damage caused by executive impersonation, deepfake threats, and doxxing cannot be overstated. RiskProfiler’s Executive Monitoring proactively tracks key personnel across digital and illicit channels, alerting organizations to high-risk mentions, fake profiles, and targeted campaigns.
5. Compliance and Legal Readiness
With built-in documentation support, RiskProfiler enables organizations to gather admissible evidence for enforcement actions. Whether working with law enforcement, UDRP complaints, or litigation, the platform provides a reliable trail of digital forensics to support brand defense.
Conclusion
Brand protection is no longer optional—it is a necessity in today’s cyber threat landscape. As phishing and impersonation attacks continue to evolve, businesses must take a proactive stance in safeguarding their brand identity. By implementing strong domain security measures, leveraging threat intelligence, and educating employees and customers, organizations can significantly reduce the risks posed by brand spoofing.
Investing in brand protection solutions will not only help mitigate financial and reputational damage but also reinforce customer trust in an increasingly digital world.
Book a Demo Today to secure your brand identity and protect your customers from phishing and impersonation attacks with RiskProfiler’s advanced brand threat intelligence and takedown solutions.
Phishing and impersonation attacks have become a persistent threat to businesses worldwide. Cybercriminals exploit brand trust by mimicking legitimate companies to steal sensitive information, defraud customers, damage reputations, or gain unauthorized access for malware and ransomware attacks. These attacks leverage brand and domain spoofing techniques, such as fake domains, fraudulent emails, and counterfeit social media profiles, to deceive unsuspecting users, employees, or account admins. As phishing tactics grow more sophisticated, businesses must adopt proactive brand protection strategies to prevent cybercriminals from exploiting their identity. In this article, we’ll explore how threat actors use brand and domain spoofing, the risks posed to businesses, and the most effective measures to combat these attacks.
How Threat Actors Exploit Brand Identity?
Malicious entities often use several illicit strategies to confuse and misdirect users to gather personal information, steal finances, or gain access to commence malware or ransomware attacks. To execute these strategies, these entities might mimic your brand creatives, logo, and design, or create counterfeit domains or social media accounts in order to confuse your audience. Some of the most used exploitation techniques are listed as follows.

1. Phishing Attacks
Phishing is one of the most common cyber threats, where attackers impersonate a trusted brand to trick individuals into revealing sensitive information, such as login credentials or payment details. These attacks typically occur via email, text messages, or fake websites that closely resemble legitimate brand communication.
For example, cybercriminals may send an email that appears to come from a well-known company, prompting users to click on a malicious link that redirects them to a fake login page. Once the victim enters their credentials, attackers gain access to sensitive accounts, leading to financial fraud or data breaches.
2. Domain Spoofing
Domain spoofing involves cybercriminals registering fraudulent domains that closely resemble a legitimate company’s website. They use subtle misspellings (e.g., g00gle.com instead of google.com) or add extra characters to deceive users. Also known as typosquatting, these counterfeit domains with similar spelling can deceive visitors easily. These fake domains are then used in phishing campaigns or malicious ads to distribute malware or steal data.
Without proactive monitoring, organizations may remain unaware that fake websites are misusing their brand until customers report fraud incidents.
3. Fake Social Media Profiles
Threat actors create counterfeit social media pages that impersonate brands, often targeting customers with fake giveaways, phishing links, or scams. These fraudulent profiles trick users into providing personal information, making payments, or downloading malware-laden files. Additionally, such profiles can also be used to run campaigns harmful to your brand reputation, spreading misinformation about your products, business ethics, or key personnel.
4. Brandjacking
Cyber attackers often exploit a brand’s identity by using brand creatives, logos, trademarks, or phony products. Another popular form of brandjacking in domain spoofing is when cybercriminals create domains with names closely similar to the brand’s name so that a visitor could easily get confused between the two. Using counterfeit websites, brand creatives, copying logos, or other significant identity elements, miscreants can collect sensitive customer data, run phishing campaigns, or sell fake products to bring down your brand image.
5. Malicious Ads & Rogue Mobile Applications
Cybercriminals also exploit brand logos and trademarks to create deceptive ads or fake mobile applications that appear legitimate. Unsuspecting users may download these applications, leading to credential theft, unauthorized transactions, or device compromise. In the long run, it can ruin your brand image, cause damage to your brand reputation, and harm your overall integrity.
6. Whaling Attacks
A whaling attack is a form of phishing attack where cybercriminals mainly target C-suite executives of a business, trying to harm the brand’s reputation. In this kind of attack, malicious actors try to impersonate business CEOs, CTOs, board members, or other key personnel to manipulate business employees and clients to share sensitive information or make unauthorized monetary transactions. In both cases, these kind of attacks can cause severe damage to brand image, result in financial trouble, or leave opening for unsuspecting malware or ransomware attacks.
7. Fraudulent Social Media Campaigns
Malicious actors may also run campaigns that can damage your brand identity and customer reach. The fake accounts use brand creatives to engage with customers, spread misinformation, and use user details that can create confusion in users’ minds and damage your brand identity. Engaging with these fake accounts or dubious content may cause mistrust in your brand and tarnish your brand identity.
Business Risks of Brand & Domain Spoofing
Brand impersonation and domain spoofing are some of the biggest concerns against their public image and brand integrity. Impersonation attempts can dilute audience trust and create a negative impression of the brand while damaging brand integrity. Some of the damages that a brand may incur due to brand impersonation attempts are listed below.
Financial Losses
Cybercriminals leverage domain spoofing and phishing emails to carry out fraudulent activities, causing direct and indirect financial harm to businesses and their customers.
Fraudulent Transactions: Domain spoofing is used to impersonate official business websites, tricking customers into making payments for fake products or services.
Wire Transfer Scams: Attackers send phishing emails from seemingly legitimate corporate domains to deceive employees into authorizing fraudulent wire transfers.
Ransomware & Extortion: Phishing attacks can lead to malware infections that encrypt company data, demanding ransom payments for decryption keys.
Legal Costs & Compensation: Organizations may face lawsuits or be required to compensate affected customers, increasing financial liabilities.
Operational Disruptions: Investigating and mitigating fraud-related incidents diverts resources from core business functions, leading to revenue losses.
Confusing Identities
Brand spoofing creates uncertainty among customers, partners, and even employees, leading to operational inefficiencies and trust erosion.
Customer Confusion: Fake websites and emails closely resembling official communication make it difficult for customers to distinguish between real and fraudulent entities.
Employee Phishing Attacks: Staff members may receive spoofed emails from what appear to be senior executives or IT administrators, leading to unauthorized data sharing or credential leaks.
Supply Chain Attacks: Impersonated domains may be used to deceive suppliers and vendors, leading to incorrect payments, shipment fraud, or disruption of services.
Domain Squatting & Typosquatting: Fraudsters register domains similar to legitimate ones (e.g., “brand-support.com” instead of “brand.com”), leading to misdirected traffic and security vulnerabilities.
Reputation Damage
Brand reputation is one of the most valuable assets of a company, and domain spoofing can significantly harm public perception and customer trust.
Customer Distrust: Victims of phishing scams may associate fraudulent activities with the actual brand, leading to a loss of confidence in its services.
Negative Publicity & Media Coverage: Reports of impersonation-related fraud can tarnish a brand’s image, making it difficult to regain customer loyalty.
Social Media & Review Attacks: Fake accounts impersonating a brand can spread misinformation, damage customer relationships, or post misleading reviews.
Loss of Competitive Edge: If consumers or business partners perceive a brand as insecure or unreliable, they may switch to competitors who have stronger security measures in place.
Data Breaches & Compliance Risks
A successful brand impersonation or phishing attack can lead to unauthorized access to sensitive data, triggering regulatory and legal repercussions.
Customer & Employee Data Theft: Phishing emails can capture login credentials, payment information, and personally identifiable information (PII), exposing individuals to identity theft.
Regulatory Fines & Legal Consequences: Data protection laws, such as the GDPR (General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), impose hefty fines for mishandling or losing sensitive customer data.
Third-Party Compliance Risks: Businesses working with regulated industries (e.g., finance and healthcare) may lose certifications or compliance status due to security breaches.
Intellectual Property Theft: Impersonation attacks targeting executives or R&D teams can lead to the loss of sensitive data such as trade secrets, patents, or strategic business plans.
The longer an impersonation campaign remains undetected, the more damage it can inflict on brand reputation and customer confidence.
Why are Brand Protection Frameworks Necessary?
Integrating a capable brand intelligence tool with good AI and automation support allows your business to stay ahead of phishing, cyber scams, and other impersonation attempts. A good brand risk management tool monitors the surface and dark web to trace any unauthorized mention, product sales, product listing, phishing attempts, domain spoofing, and executive impersonation attempts to ensure brand protection against external threats. An effective brand risk management tool like RiskProfiler monitors the web continuously to detect malicious conversations, collect data on sources, timelines, brand configurations, and executive impersonations, and formulate domain takedown and phishing prevention strategies to enhance brand protection efforts.
Brand Protection and Phishing Prevention: Best Practices
In order to disrupt fraudulent campaigns and prepare practical phishing prevention strategies, organization, and their security teams need to incorporate some advantageous practices into their brand protection efforts. Integrating such practices with strict conditioning allows you to monitor the use of your brand creatives and stay ahead of malicious activities and campaigns at all times, helping you maintain brand integrity and reputation.
1. Domain & Email Security Measures
Your business domain is the main interaction point and trust symbol for your customer and client base. Safeguarding your domain identity from spoofing attempts helps secure your brand legacy from deception.
Implement DMARC, SPF, and DKIM: These email authentication protocols help prevent spoofed emails from being sent on behalf of a brand.
Monitor for Lookalike Domains: Businesses should actively track newly registered domains that mimic their brand name and takedown fraudulent domains and subdomains before they can cause any harm.
2. Digital Risk Protection & Threat Intelligence
Integrating modern AI tools and automated workflows with brand intelligence allows businesses to monitor the surface and dark web spaces continuously. Real-time brand threat intelligence provides organizations with the advantage of proactive intelligence, helping them detect risks and prepare mitigation strategies before the attackers damage the business’s reputation.
Use AI-Powered Threat Detection: Modern brand intelligence solutions integrate artificial intelligence to detect and analyze impersonation attempts across the surface web and social media spaces in real time.
Monitor Brand Mentions & Social Media: Automated tools can scan social platforms, forums, and dark web marketplaces for fraudulent activities and threatening conversations involving a company’s brand identity.
3. Employee & Customer Awareness
Cybercriminals often use phishing technology via email, phone calls, or voice messages to steal sensitive data from your employees and customers. It is essential to run mandatory anti-phishing campaigns inside the organization and on public platforms to help your employees and customers recognize the typical signatures of phishing attacks and the best practices to avoid them.
Employee Training: Organizations should regularly educate employees on how to recognize phishing attempts by mimicking C-suite employees or any third-party vendors. Businesses should also create definite pathways for employees to report phishing attempts to alert their teams of the scams and prevention strategies.
Customer Alerts: Brands should inform customers about ongoing impersonation threats and provide guidelines to verify legitimate communication channels through publicized anti-phishing campaigns.
4. Legal & Takedown Actions
Implementing a good brand risk management solution allows businesses to streamline the takedown efforts for faster and more effective threat mitigation. Brand intelligence tools gather threat intelligence with detailed data on the source, timeline, and threat category to curate idle strategies, aiding in swift domain takedown.
Issuing Cease-and-Desist Notices: Legal teams can act against fraudsters by sending cease-and-desist notices to domain registrars or social media platforms hosting fake accounts.
Collaboration with Cybersecurity Firms: Companies specializing in brand protection can assist in identifying and dismantling phishing sites and fraudulent campaigns.
How Does RiskProfiler Secure Your Brand Against Impersonation & Brand Abuse?
In today’s hyper-digital economy, brand risk is no longer confined to isolated incidents—it is continuous, borderless, and increasingly complex. From domain spoofing and phishing to executive impersonation and counterfeit product listings, digital threats now pose strategic risks to brand equity and consumer trust. RiskProfiler offers a next-generation Brand Intelligence solution, purpose-built to help organizations detect, respond to, and neutralize threats before they impact reputation or revenue.

1. Holistic Brand Risk Monitoring
RiskProfiler provides 360-degree visibility into your brand’s digital footprint. The platform continuously monitors websites, social media, online marketplaces, mobile app stores, forums, and the deep/dark web for signs of abuse. Advanced AI models detect patterns across seemingly disconnected threat vectors—ensuring you uncover not just individual incidents but coordinated brand attacks.
2. Real-Time Threat Prioritization
Not all threats are created equal. RiskProfiler intelligently classifies and prioritizes threats using contextual risk scoring—factoring in exposure level, geography, impersonation fidelity, and potential consumer impact. This enables brand protection, legal, and cybersecurity teams to focus on high-impact threats first, optimizing response efforts and resource allocation.
3. Automated Domain Detection & Takedown
Rogue domains are a common tactic in phishing and fraud campaigns. RiskProfiler’s automated domain discovery engine scans millions of new domain registrations daily, using fuzzy logic and visual similarity analysis to detect impersonations. It then orchestrates takedown workflows through registrar partnerships and legal escalation—dramatically reducing response time and operational burden.
4. Executive & VIP Risk Surveillance
The reputational damage caused by executive impersonation, deepfake threats, and doxxing cannot be overstated. RiskProfiler’s Executive Monitoring proactively tracks key personnel across digital and illicit channels, alerting organizations to high-risk mentions, fake profiles, and targeted campaigns.
5. Compliance and Legal Readiness
With built-in documentation support, RiskProfiler enables organizations to gather admissible evidence for enforcement actions. Whether working with law enforcement, UDRP complaints, or litigation, the platform provides a reliable trail of digital forensics to support brand defense.
Conclusion
Brand protection is no longer optional—it is a necessity in today’s cyber threat landscape. As phishing and impersonation attacks continue to evolve, businesses must take a proactive stance in safeguarding their brand identity. By implementing strong domain security measures, leveraging threat intelligence, and educating employees and customers, organizations can significantly reduce the risks posed by brand spoofing.
Investing in brand protection solutions will not only help mitigate financial and reputational damage but also reinforce customer trust in an increasingly digital world.
Book a Demo Today to secure your brand identity and protect your customers from phishing and impersonation attacks with RiskProfiler’s advanced brand threat intelligence and takedown solutions.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



