Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Enhance Vendor Intelligence with AI Vendor Assessments
Enhance Vendor Intelligence with AI Vendor Assessments
In today’s interconnected business landscape, vendor security assessments have become more critical than ever. Organizations rely on third-party vendors for essential services, but these partnerships also introduce security and compliance risks to the system, often compromising it.
Read Time
7 min read
Posted On
Mar 21, 2025
Social Media
In today’s interconnected business landscape, vendor security assessments have become more critical than ever. Organizations rely on third-party vendors for essential services, but these partnerships also introduce security and compliance risks to the system, often compromising it. Traditional vendor assessments, often conducted annually or during onboarding, are no longer sufficient to mitigate emerging supply chain risks. Thus, proactive vendor intelligence, a dynamic, automated approach to third-party assessments, becomes a necessity to ensure continuous supply chain risk monitoring and immediate response for real-time remediation. By leveraging automation and advanced analytics, companies can enhance their vendor security assessment accuracy by up to 99%, safeguard data, and maintain regulatory compliance.
Why Businesses Need Continuous Vendor Intelligence?
The advanced technology space and business operations are highly reliant on third-party service providers. Dependency on vendors makes your system vulnerable to external threats and thus requires a constant overview of the extended security posture for comprehensive protection. Implementing efficient third-party security measures allows you to stay ahead of supply chain risks and helps you collaborate with your vendors in the mitigation efforts.
Key Objectives in Supply Chain Risk Management
A robust vendor risk management solution allows your business to monitor, detect, and remediate various security threats originating from your supply chain vendors. The key objectives of these tools are as follows:
Cybersecurity Threats Monitoring and Detection
Vendors often have access to sensitive data and systems, making them prime targets for cyberattacks. An efficient vendor intelligence solution would allow you to monitor your vendor portfolio and detect threats in real-time to aid in the mitigation process. Another important quality of a good third-party risk management tool is the live vendor collaboration support to assist in threat mitigation.
Assistance with Vendor Selection
Vendor intelligence solution also assists you with vendor selection, allowing you to make an informed decision based on security data-backed statistics. Drawing a peer security posture analysis with industry service providers helps you find the right vendor with a secure network. The peer benchmarking feature of your third-party risk management solutions also allows you to view threat details with contextual analysis for better understanding and an informed mitigation process.
Regulatory Compliance
Companies must ensure that vendors adhere to industry-specific regulations such as GDPR, HIPAA, and SOC 2. A good vendor intelligence software will allow you to ensure the regulatory compliance for all your extended vendors to maintain a unified security standard. The security solution would also help you monitor and identify any change in the regulatory compliance for a fast and easy fix to avoid future penalties.
Operational Resilience
Your business continuity depends on vendors maintaining consistent service levels and mitigating risks effectively. With the help of continuous vendor security assessments, your team can detect supply chain risks as they emerge, allowing them ample time to collaborate with the vendor and initiate the mitigation process. It helps you gain control of a threat incident before it fully materializes, ensuring business resilience and operational continuity.
What makes vendor assessments effective in TPRM?
A comprehensive vendor intelligence framework involves multiple layers of risk assessment and continuous monitoring. When followed meticulously and incorporated with automated workflows, these assessment tools allow you to stay vigilant on supply chain risks 24/7, allowing comprehensive security effort. We have listed the key particulars of a vendor assessment framework below.
1. Pre-Onboarding Due Diligence
Before engaging with a vendor, businesses must assess their security posture and compliance standing. This includes:
✔ Reviewing security certifications (ISO, SOC 2, etc.)
✔ Conducting regulatory compliance checks (GDPR, HIPAA, PCI DSS)
✔ Evaluating financial and operational stability
✔ Assessing potential third-party dependencies
2. Ongoing Vendor Monitoring & Risk Detection
After onboarding, continuous monitoring is essential to detect new risks:
✔ Real-time tracking of vendor vulnerabilities and data breaches
✔ Monitoring compliance with updated regulations
✔ Assessing financial health indicators and credit ratings
✔ Identifying operational changes that could impact service delivery
3. Incident Response & Risk Mitigation
When vendor risks emerge, businesses must respond swiftly:
✔ Defining escalation procedures for vendor security incidents
✔ Engaging with vendors to remediate security gaps
✔ Adjusting risk exposure based on dynamic risk assessments
✔ Establishing alternative vendor solutions if necessary
How RiskProfiler Automates Vendor Security Assessments?
Manual vendor security assessments are time-consuming and prone to gaps. Scheduled vendor risk analysis also results in security gaps as it doesn’t offer constant visibility into the supply chain security environment. RiskProfiler automates the entire vendor assessment process with AI assistance and automation, enabling businesses to stay ahead of supply chain risks with minimal effort.
Key Features of RiskProfiler Vendor Intelligence & Security Assessment:
RiskProfiler’s third-party risk management tool allows continuous comprehensive visibility into your third-party and extended vendor security posture. The top features of the security solution that enhances your supply chain security measures are:
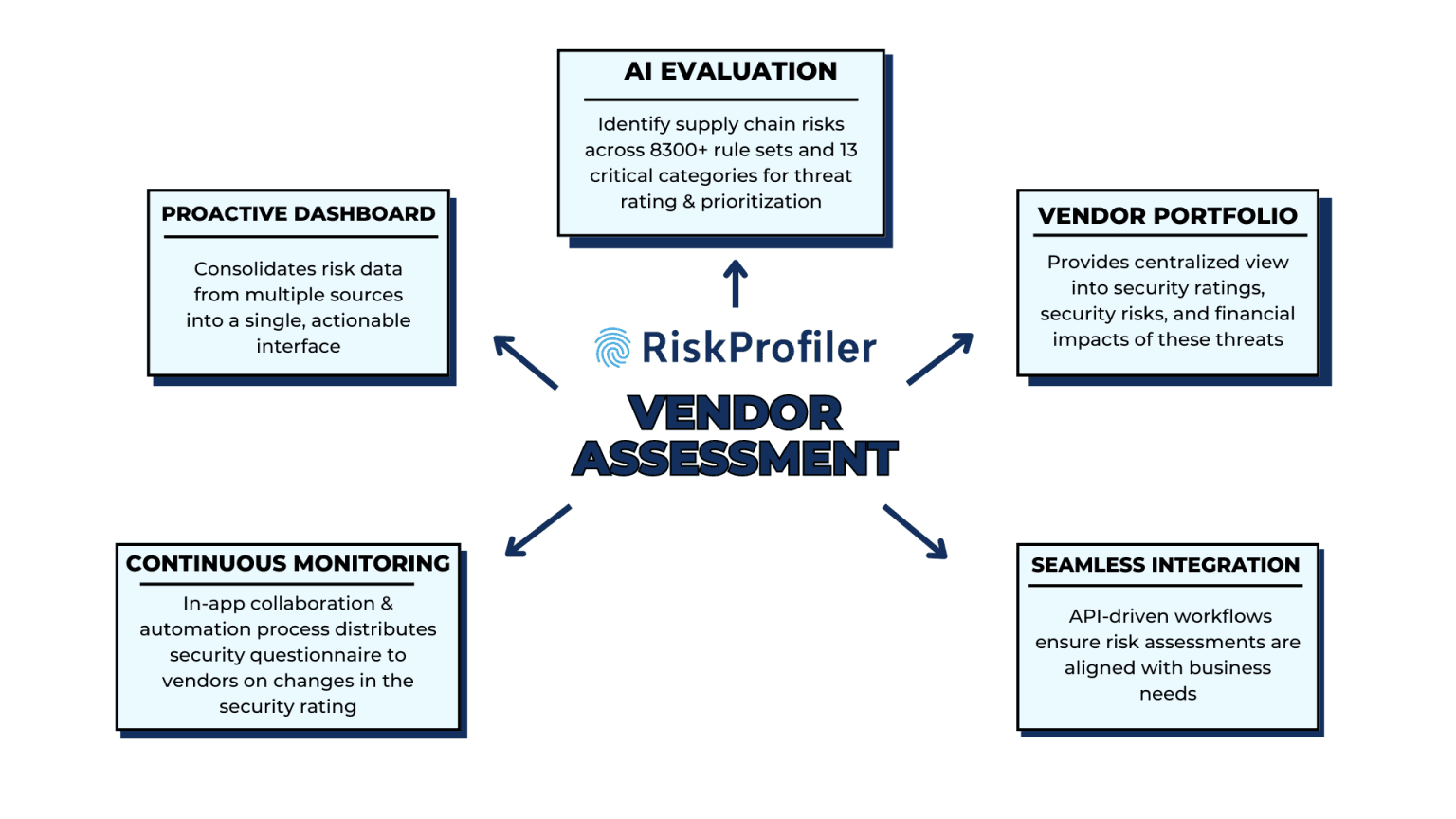
Real-Time Vendor Intelligence Dashboard
Riskprofiler consolidates risk data from multiple sources into a single, actionable interface for ease of accessibility. The vendor intelligence dashboard presents all key security data in simpler terms with visual graphs, charts, and data points for convenient risk evaluation.
AI-Powered Threat Evaluation
RiskProfiler’s vendor intelligence AI-assisted module is trained to identify supply chain risks across 8300+ rule sets and 13 critical categories for accurate threat rating and prioritization. It provides comprehensive third-party threat detection coverage, helping you detect security risks across vendor systems, API gateways, authentication processes, email leaks, cloud security, and rouge application detection. The efficient security tool eliminates false positives, enhancing the effectiveness of the threat intelligence and your remediation strategies.
Detailed Vendor Portfolio
The third-party risk management tool maintains an extensive vendor portfolio, allowing a centralized view into vendor security ratings, detected security risks, and potential financial impacts of these threats. The security scoring and threat impact scoring with historing threat trends allow you to identify high-risk vendors.
Continuous Monitoring with Vendor Security Assessments
Automated vendor security assessments with the help of RiskProfiler’s AI-powered vendor risk questionnaire allow you to monitor the supply chain risks at all times and flag vulnerabilities as they emerge. The in-application collaboration and automation process distributes the security questionnaire to the respective vendor on any change in the security rating. The questionnaire provides support for compliance monitoring, helping you maintain regulatory adherence without the need for manual updates.
Seamless Integration with Security & Procurement Teams
RiskProfiler’s third-party management solution comes with simpler integration options. API-driven workflows ensure risk assessments are aligned with business needs. The integration options also allow businesses to select the choices that complement their team specifics. RiskProfiler helps organizations transition from reactive vendor management to a proactive approach, ensuring that vendor risks are identified and mitigated before they escalate.
How to Implement a Proactive Vendor Intelligence Solution?
To effectively manage vendor risks, businesses should integrate effective supply chain risk mitigation solutions. A good third-party risk management tool helps you with risk assessment, decision making, threat scoring, and prioritization, and streamlines vendor collaboration, contributing to an efficient remediation effort.
Step 1: Identify Critical Vendors & Categorize Risk Levels
To begin implementing a proactive vendor intelligence solution, businesses must first identify their critical vendors and categorize risk levels. This means determining which vendors have the most significant impact on operations and assessing their level of access to sensitive data and systems. Vendors that have access to critical business functions or handle confidential information should be given a higher risk classification, allowing for more focused system monitoring and risk management.
Step 2: Implement Automated Tools for Real-Time Assessments
Implementing automated tools for real-time assessments is essential. Deploying RiskProfiler helps businesses continuously evaluate the security posture of their vendors. By leveraging AI-powered insights, companies can efficiently prioritize risk management efforts and focus their attention on vendors that pose the highest level of risk. This automation streamlines risk assessments, ensuring that businesses remain proactive rather than reactive in mitigating potential threats.
Step 3: Establish a Structured Response Plan for Vendor Security Incidents
Establishing a structured response plan for vendor security incidents is another crucial step. It is important to define clear roles and responsibilities within the organization to address security events related to third parties. Automated alert systems should be put in place to detect and respond to emerging threats as they arise. Having a well-structured incident response plan minimizes downtime and prevents security breaches from escalating.
Step 4: Conduct Periodic Reviews & Update Risk Policies
Finally, conducting periodic reviews and updating risk policies ensures that vendor risk management efforts remain effective. Businesses should schedule quarterly vendor security reviews to assess whether vendors continue to meet compliance and security standards. Policies should be adapted based on evolving regulatory requirements and emerging threats to maintain a strong defense against potential vulnerabilities. By continuously refining risk policies and conducting regular evaluations, organizations can stay ahead of potential vendor-related risks.
Conclusion
In a world where supply chain risks continue to grow, businesses can no longer afford to take a passive approach to vendor security assessments. Proactive vendor intelligence ensures continuous risk monitoring, regulatory compliance, and business resilience.
With RiskProfiler, companies can automate vendor assessments, detect threats in real time, and mitigate risks before they impact operations. By leveraging automation and AI, organizations can strengthen their vendor management strategy and build a more secure supply chain.
Ready to transform your vendor assessment process? Book a demo with RiskProfiler and discover how automated vendor intelligence can protect your business from unforeseen risks.
In today’s interconnected business landscape, vendor security assessments have become more critical than ever. Organizations rely on third-party vendors for essential services, but these partnerships also introduce security and compliance risks to the system, often compromising it. Traditional vendor assessments, often conducted annually or during onboarding, are no longer sufficient to mitigate emerging supply chain risks. Thus, proactive vendor intelligence, a dynamic, automated approach to third-party assessments, becomes a necessity to ensure continuous supply chain risk monitoring and immediate response for real-time remediation. By leveraging automation and advanced analytics, companies can enhance their vendor security assessment accuracy by up to 99%, safeguard data, and maintain regulatory compliance.
Why Businesses Need Continuous Vendor Intelligence?
The advanced technology space and business operations are highly reliant on third-party service providers. Dependency on vendors makes your system vulnerable to external threats and thus requires a constant overview of the extended security posture for comprehensive protection. Implementing efficient third-party security measures allows you to stay ahead of supply chain risks and helps you collaborate with your vendors in the mitigation efforts.
Key Objectives in Supply Chain Risk Management
A robust vendor risk management solution allows your business to monitor, detect, and remediate various security threats originating from your supply chain vendors. The key objectives of these tools are as follows:
Cybersecurity Threats Monitoring and Detection
Vendors often have access to sensitive data and systems, making them prime targets for cyberattacks. An efficient vendor intelligence solution would allow you to monitor your vendor portfolio and detect threats in real-time to aid in the mitigation process. Another important quality of a good third-party risk management tool is the live vendor collaboration support to assist in threat mitigation.
Assistance with Vendor Selection
Vendor intelligence solution also assists you with vendor selection, allowing you to make an informed decision based on security data-backed statistics. Drawing a peer security posture analysis with industry service providers helps you find the right vendor with a secure network. The peer benchmarking feature of your third-party risk management solutions also allows you to view threat details with contextual analysis for better understanding and an informed mitigation process.
Regulatory Compliance
Companies must ensure that vendors adhere to industry-specific regulations such as GDPR, HIPAA, and SOC 2. A good vendor intelligence software will allow you to ensure the regulatory compliance for all your extended vendors to maintain a unified security standard. The security solution would also help you monitor and identify any change in the regulatory compliance for a fast and easy fix to avoid future penalties.
Operational Resilience
Your business continuity depends on vendors maintaining consistent service levels and mitigating risks effectively. With the help of continuous vendor security assessments, your team can detect supply chain risks as they emerge, allowing them ample time to collaborate with the vendor and initiate the mitigation process. It helps you gain control of a threat incident before it fully materializes, ensuring business resilience and operational continuity.
What makes vendor assessments effective in TPRM?
A comprehensive vendor intelligence framework involves multiple layers of risk assessment and continuous monitoring. When followed meticulously and incorporated with automated workflows, these assessment tools allow you to stay vigilant on supply chain risks 24/7, allowing comprehensive security effort. We have listed the key particulars of a vendor assessment framework below.
1. Pre-Onboarding Due Diligence
Before engaging with a vendor, businesses must assess their security posture and compliance standing. This includes:
✔ Reviewing security certifications (ISO, SOC 2, etc.)
✔ Conducting regulatory compliance checks (GDPR, HIPAA, PCI DSS)
✔ Evaluating financial and operational stability
✔ Assessing potential third-party dependencies
2. Ongoing Vendor Monitoring & Risk Detection
After onboarding, continuous monitoring is essential to detect new risks:
✔ Real-time tracking of vendor vulnerabilities and data breaches
✔ Monitoring compliance with updated regulations
✔ Assessing financial health indicators and credit ratings
✔ Identifying operational changes that could impact service delivery
3. Incident Response & Risk Mitigation
When vendor risks emerge, businesses must respond swiftly:
✔ Defining escalation procedures for vendor security incidents
✔ Engaging with vendors to remediate security gaps
✔ Adjusting risk exposure based on dynamic risk assessments
✔ Establishing alternative vendor solutions if necessary
How RiskProfiler Automates Vendor Security Assessments?
Manual vendor security assessments are time-consuming and prone to gaps. Scheduled vendor risk analysis also results in security gaps as it doesn’t offer constant visibility into the supply chain security environment. RiskProfiler automates the entire vendor assessment process with AI assistance and automation, enabling businesses to stay ahead of supply chain risks with minimal effort.
Key Features of RiskProfiler Vendor Intelligence & Security Assessment:
RiskProfiler’s third-party risk management tool allows continuous comprehensive visibility into your third-party and extended vendor security posture. The top features of the security solution that enhances your supply chain security measures are:

Real-Time Vendor Intelligence Dashboard
Riskprofiler consolidates risk data from multiple sources into a single, actionable interface for ease of accessibility. The vendor intelligence dashboard presents all key security data in simpler terms with visual graphs, charts, and data points for convenient risk evaluation.
AI-Powered Threat Evaluation
RiskProfiler’s vendor intelligence AI-assisted module is trained to identify supply chain risks across 8300+ rule sets and 13 critical categories for accurate threat rating and prioritization. It provides comprehensive third-party threat detection coverage, helping you detect security risks across vendor systems, API gateways, authentication processes, email leaks, cloud security, and rouge application detection. The efficient security tool eliminates false positives, enhancing the effectiveness of the threat intelligence and your remediation strategies.
Detailed Vendor Portfolio
The third-party risk management tool maintains an extensive vendor portfolio, allowing a centralized view into vendor security ratings, detected security risks, and potential financial impacts of these threats. The security scoring and threat impact scoring with historing threat trends allow you to identify high-risk vendors.
Continuous Monitoring with Vendor Security Assessments
Automated vendor security assessments with the help of RiskProfiler’s AI-powered vendor risk questionnaire allow you to monitor the supply chain risks at all times and flag vulnerabilities as they emerge. The in-application collaboration and automation process distributes the security questionnaire to the respective vendor on any change in the security rating. The questionnaire provides support for compliance monitoring, helping you maintain regulatory adherence without the need for manual updates.
Seamless Integration with Security & Procurement Teams
RiskProfiler’s third-party management solution comes with simpler integration options. API-driven workflows ensure risk assessments are aligned with business needs. The integration options also allow businesses to select the choices that complement their team specifics. RiskProfiler helps organizations transition from reactive vendor management to a proactive approach, ensuring that vendor risks are identified and mitigated before they escalate.
How to Implement a Proactive Vendor Intelligence Solution?
To effectively manage vendor risks, businesses should integrate effective supply chain risk mitigation solutions. A good third-party risk management tool helps you with risk assessment, decision making, threat scoring, and prioritization, and streamlines vendor collaboration, contributing to an efficient remediation effort.
Step 1: Identify Critical Vendors & Categorize Risk Levels
To begin implementing a proactive vendor intelligence solution, businesses must first identify their critical vendors and categorize risk levels. This means determining which vendors have the most significant impact on operations and assessing their level of access to sensitive data and systems. Vendors that have access to critical business functions or handle confidential information should be given a higher risk classification, allowing for more focused system monitoring and risk management.
Step 2: Implement Automated Tools for Real-Time Assessments
Implementing automated tools for real-time assessments is essential. Deploying RiskProfiler helps businesses continuously evaluate the security posture of their vendors. By leveraging AI-powered insights, companies can efficiently prioritize risk management efforts and focus their attention on vendors that pose the highest level of risk. This automation streamlines risk assessments, ensuring that businesses remain proactive rather than reactive in mitigating potential threats.
Step 3: Establish a Structured Response Plan for Vendor Security Incidents
Establishing a structured response plan for vendor security incidents is another crucial step. It is important to define clear roles and responsibilities within the organization to address security events related to third parties. Automated alert systems should be put in place to detect and respond to emerging threats as they arise. Having a well-structured incident response plan minimizes downtime and prevents security breaches from escalating.
Step 4: Conduct Periodic Reviews & Update Risk Policies
Finally, conducting periodic reviews and updating risk policies ensures that vendor risk management efforts remain effective. Businesses should schedule quarterly vendor security reviews to assess whether vendors continue to meet compliance and security standards. Policies should be adapted based on evolving regulatory requirements and emerging threats to maintain a strong defense against potential vulnerabilities. By continuously refining risk policies and conducting regular evaluations, organizations can stay ahead of potential vendor-related risks.
Conclusion
In a world where supply chain risks continue to grow, businesses can no longer afford to take a passive approach to vendor security assessments. Proactive vendor intelligence ensures continuous risk monitoring, regulatory compliance, and business resilience.
With RiskProfiler, companies can automate vendor assessments, detect threats in real time, and mitigate risks before they impact operations. By leveraging automation and AI, organizations can strengthen their vendor management strategy and build a more secure supply chain.
Ready to transform your vendor assessment process? Book a demo with RiskProfiler and discover how automated vendor intelligence can protect your business from unforeseen risks.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



