Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management

Cloud Attack Surface Management: Building Cloud Resilience
Cloud Attack Surface Management: Building Cloud Resilience
In 2025, the majority of digital infrastructures will be hosted on cloud and containerized environments. As a result, cloud misconfigurations and asset exposures are among the major reasons for cybersecurity incidents and breaches in today’s time.
Read Time
7 min read
Posted On
Oct 9, 2025
Social Media
In 2025, the majority of digital infrastructures will be hosted on cloud and containerized environments. As a result, cloud misconfigurations and asset exposures are among the major reasons for cybersecurity incidents and breaches in today’s time. According to the latest Cost of a Data Breach Report by IBM, 30% of cybersecurity incidents involve the systems in multi-cloud and hybrid environments. The average cost of a data breach on a hybrid or multi-cloud setup is around 5.5 million USD, according to the same report. It reflects on today’s reality of the volatility of cloud environments and also highlights why cloud attack surface management is essential for a resilient security strategy. Where traditional security tools enumerate issues, CASM reduces exposure risks by discovering cloud misconfigurations, validating exploitability, closing the loop with ownership, runbooks, and measurement.
The Risk of External Cloud Exposures
As the entire organizational workflow is hosted in the cloud and containerized spaces, system exposures can result from multiple reasons. Cloud integrations, both listed and shadow assets, use login details that can create exposures due to unhygienic password use and poor MFA protocols. The shadow integrations on a cloud system create major security blind spots as these tools lack the usual supervision of the security team, leaving them out of security audits and patch management.
SaaS databases accessible with old keys or legacy software tied to the digital ecosystem can also expose cloud systems to external threats. Vulnerabilities in CI/CD pipelines, like exposed Git configurations, poisoned DevOps workflows, IaC drifts, overpermissive integration or OAuth connections, are among some of the biggest cloud security concerns. Additionally, unsecured vendor connections or unsafe supply chain integration can also leave an organization’s digital system exposed to adversarial threats.
Top External Cloud Exposure Risks
Although cloud environments add flexibility, scalability, and accessibility to the workflows, the fast-evolving environments add unique complexity and security challenges to the analyst dashboard. In order to stay ahead of these threats, security leaders need to simulate real-world adversary tactics used by threat actors to exfiltrate data, deploy malware payloads, and exploit identity to test the resilience of the cloud ecosystem.
1. Identity and OAuth Token Abuse
Aversaries these days use stolen or compromised tokens by exploiting OAuth consent flows to bypass multi-factor authentication. These intrusions allow silent access to cloud storage and databases. Usual perimeter threat detection modules do not detect these instances of consent abuse and token misuse unless your external threat intelligence module is tailored to detect these shadow drifts.
2. Exposures in Code Repositories and CI/CD Pipelines
Exposures in Git repositories, CI/CD pipelines, and container layers can lead to significant security concerns. Often unnoticed during security audits, attackers can gain access to sensitive credentials, major databases, and cloud environments through these exposures. Thus, it is important to model exposure across development lifecycles to prevent compromises and reduce the blast radius in the event of cloud misconfigurations.
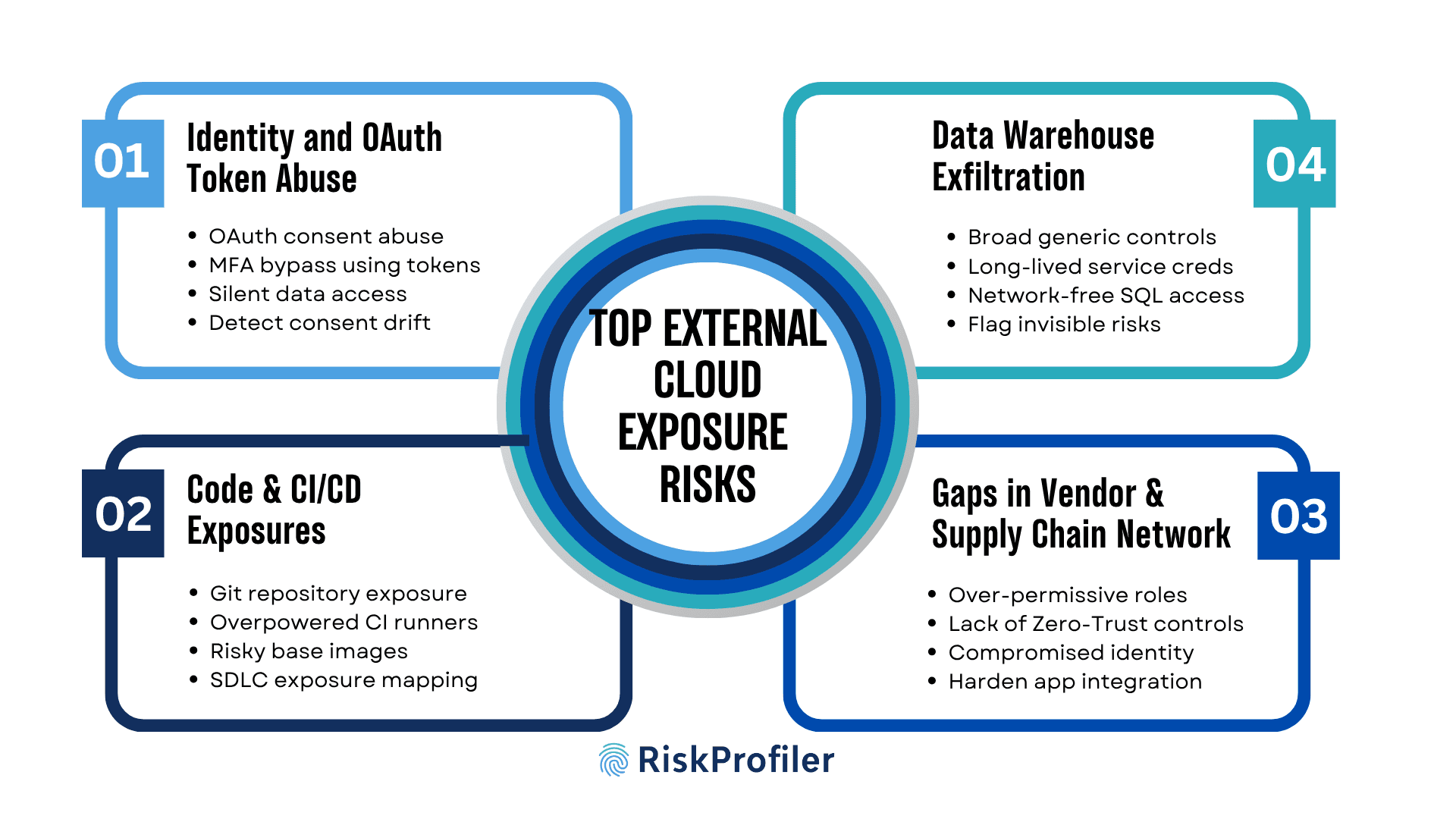
3. Hidden Gaps in Vendor & Supply Chain Network
Cloud environments are easy to integrate, and most tools in these environments operate within an interconnected network. This is why a breach in one system can snowball rapidly with over-permissive roles and a lack of zero-trust architecture. Modelling these paths with strong security guardrails enables security analysts to understand how a single compromised identity can escalate into a multi-cloud breach.
4. Data Warehouse Exfiltration
Cloud data warehouses often hold sensitive datasets but lack tailored security controls. Long-lived credentials and network-independent SQL access make them vulnerable to stealthy exfiltration processes. Modeling how identity misuse leads to data loss is critical, especially when attackers operate within the bounds of legitimate access.
Real-World Cloud Exposure Incidents
Recent cybersecurity incidents have highlighted the gaps in identity governance, token hygiene, and cloud misconfiguration. In this section, we will be talking about a few cloud threat incidents that came to the surface in recent years.
Snowflake Data Breach (2024)
The Snowflake breach campaign (UNC5537) revealed how stolen credentials, unhygienic login practices, and a lack of MFA protocol can lead to massive data exfiltration. The data breach in the Snowflake infrastructure was caused by stolen credentials that were previously exfiltrated by infostealer malware from external systems. In the breach event, around 165 organizations, including Ticketmaster, AT&T, Lending Tree, etc., were affected, leading to their data being sold on dark web marketplaces.
EmeraldWhale Cyberattack (2024)
In October 2024, Sysdig uncovered a major organized malicious cyber campaign by a threat actor, EmeraldWhale. In the campaign, the adversaries were targeting exposed Git configurations, leading to massive credential thefts from more than 15,000 cloud services from their source code and cloned repositories. During an investigation, Sysdig researchers found a suspicious, compromised account with malicious tools and more than a terabyte of data.
Salesforce Drift Compromise (August 2025)
The attack on Cloudflare and several other notable industry names began with a Salesloft Drift compromise, noticed in August 2025, carried out by the threat actor UNC6395. Cyber adversaries used a compromised OAuth token linked to the Salesloft Drift platform to gain access to the Cloudflare Salesforce instance. Using the compromised tokens, attackers exfiltrated sensitive customer and business information present in customer tokens.
External Cloud Attack Surface Management Lifecycle
In external cloud attack surface management, the threat intelligence modules continuously scan the cloud and containerized services to discover underlying gaps, vulnerabilities, and accidental exposures. Once identified, these risk signals are then prioritized based on their impact on operations, technical resilience, and relation to the probable attack chain. A high priority score in this stage dictates the security expert’s focus on the concerned exposure/cloud misconfiguration/vulnerability for effective mitigation.
Scanning for Cloud Misconfigurations and Material Exposure
Cloud attack surface management requires precise and contextual identification of the exposure type that can indicate a serious threat to operational continuity and business integrity. Identity and access exposure, external risk, leaks in the CI/CD pipeline, and shadow SaaS integrations are some of the serious concerns that the CASM modules scan for at this stage.
CASM modules, like RiskProfiler Nyx Cloud AI collect telemetry from cloud APIs, attack surface tools, identity graphs, data lineage systems, and SaaS catalogs. These inputs offer visibility into cloud misconfigurations, permissions, data flows, and third-party integrations for a unified view into possible exposures and security gaps.
Continuous Enumeration for Threat Detection
As the threat intel modules scan for threat signals, they identify anomalous activities, suspicious access requests, unusual system traffic, and other discrepancies to detect cloud exposures. The CASM tools also incorporate findings from dark web scans and infostealer telemetries to pinpoint vulnerable access points, compromised credentials, and exposed email accounts, ensuring visibility into cloud misconfigurations and evolving external threats.
Threat Prioritization with Attack Path Mapping
Once threat signals are identified, the modern AI-powered tools analyse the data, correlate the fragmented risks, and simulate possible attacker behaviour and movement across the system, from the access point to data exfiltration. Each threat is scored by its exposure, access privilege, and data sensitivity. This contextual mapping allows the machine to rate exposure based on its real-world impact on operations, finance, and reputation, going beyond the technical dependencies. RiskProfiler’s Nyx Cloud AI autonomously simulates adversarial movement across multi-cloud environments to model exposure probability.
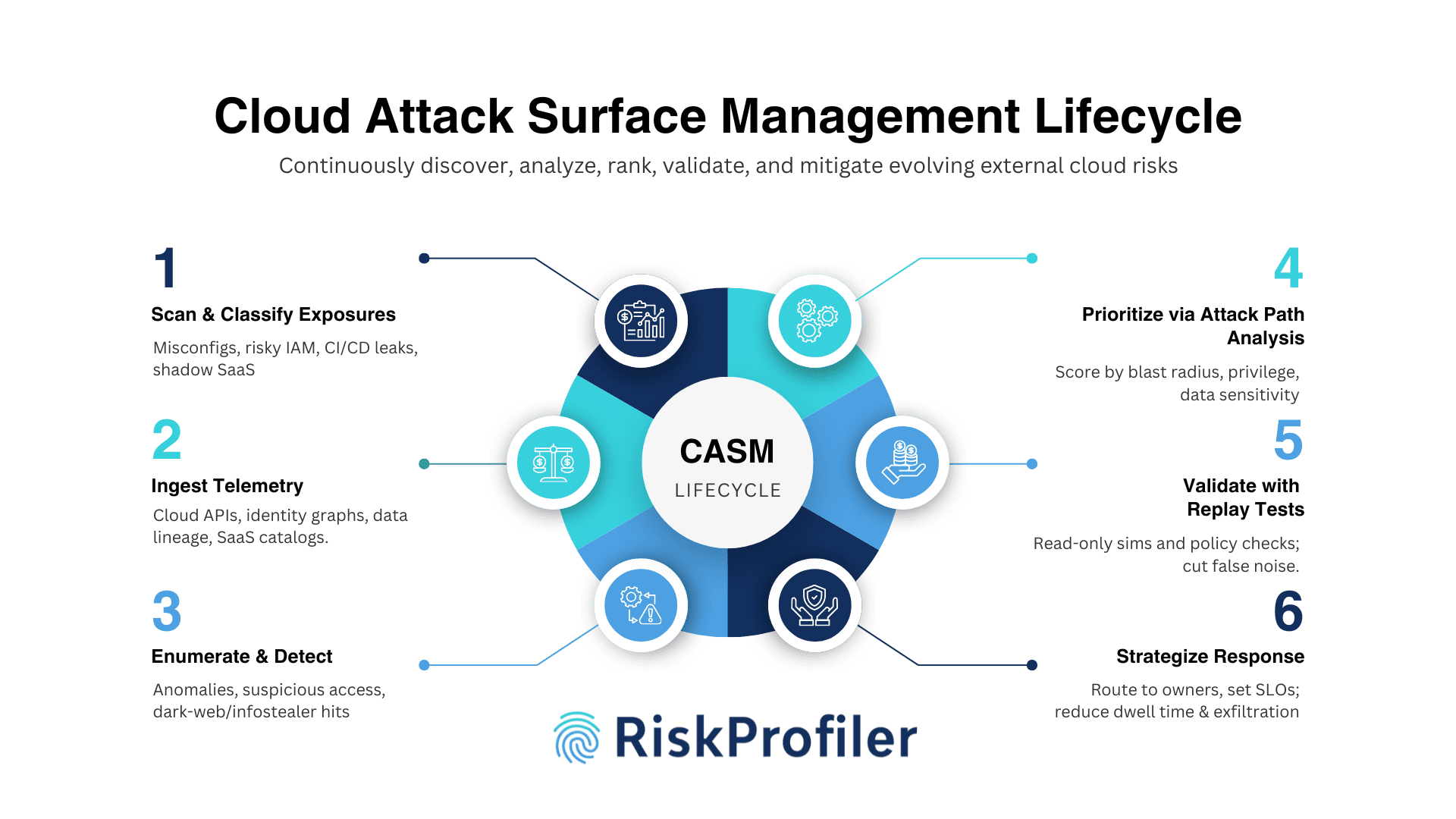
Risk Signal Replay Tests for Validation
Cloud Threat Exposure Modules perform a detailed security evaluation to determine the environment’s exploitability using read-only tokens, policy simulations, and access controls. It allows security analysts to analyze and determine the threat level of each exposure, filter noise from essential threat alerts, and help teams concentrate on only verified risks.
Direct Security Teams with Contextual Action Plan
Upon validation and obtaining the contextual specifics, the alerts are assigned to specific teams based on their access and ownership. Service Level Objectives (SLOs) are set based on exposure materiality, ensuring timely resolution and accountability across business and technical stakeholders.
Fast Response and Risk Reduction
Cloud attack surface management modules with their fast detection, analysis, validation, and action plan enable fast response and reduce dwell time. It improves identity risk scores, OAuth hygiene, and prevents data exfiltration. These indicators help leaders assess progress, justify investments, and align security outcomes with business priorities.
Operationalize CASM at Scale with RiskProfiler
RiskProfiler cloud attack surface management is an AI-powered threat intelligence module that discovers underlying threats hiding in your cloud environment. Its agentic AI-assisted system monitors for risks, analyzes them based on related network connections, blast radius, operational impact, and business concerns, and sends contextual alerts for the security teams.
Comprehensive Monitoring of Cloud Attack Surface
RiskProfiler’s Nyx Agentic AI continuously monitors an organization’s external attack surface for cloud exposures in both the organizational system and third-party relationships. The comprehensive search and discovery allow the security teams to stay ahead of hidden vulnerabilities, cloud misconfigurations, and OAuth token compromises originating in a vendor system.
Identity and Accessibility Monitoring
RiskProfiler’s identity intelligence module discovers reused passwords, leaked credentials, and overpermissive roles in cloud integrations, allowing for a fast response. With its dark web monitoring module, Nyx Dark Web AI, RiskProfiler scans for leaked data, credentials, and email details in dark web marketplaces, forums, and paste sites. Advanced knowledge of these security gaps provides ample time to manage exposed systems and tighten security, preventing escalation and unauthorized access.
Correlate Exposed Assets to Data Risks
RiskProfiler’s cloud attack surface management module continuously maps external exposures, stale DNS, leaked repositories, misconfigured buckets, and expired certificates. The AI-powered system correlates external assets and leaked credentials to cloud identities, roles, and crown-jewel data stores to model real attack paths, quantify blast radius, and prioritize fixes that measurably reduce breach likelihood.
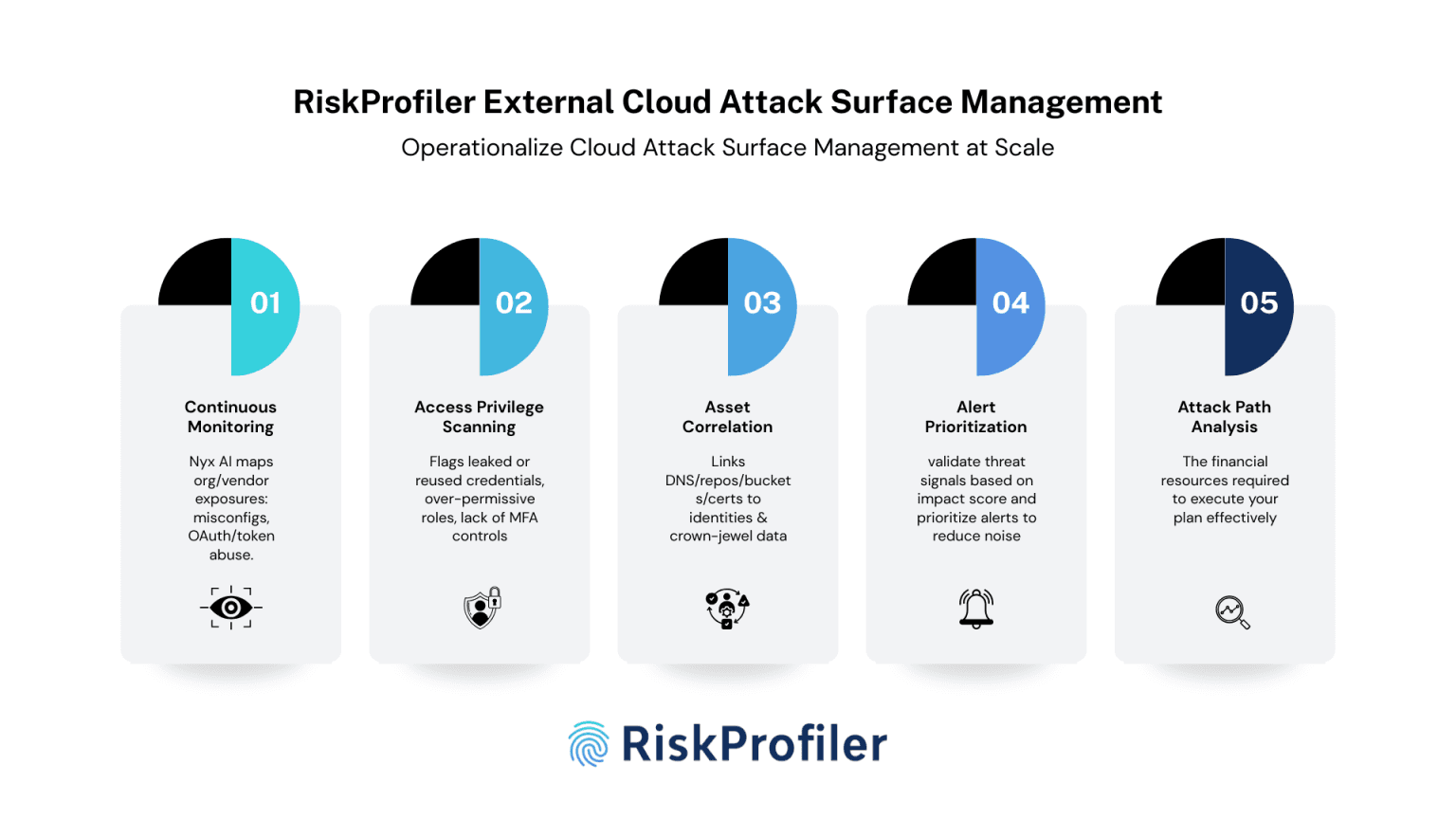
Threat Validation and Alert Prioritization
RiskProfiler’s threat intelligence engine analyzes the threat signals based on read-only probes, policy simulations, access permissions, and blast radium to separate real threats from noise. It also assigns impact scores and security ratings to each threat to help teams prioritize response based on their real-life impact on business, operations, and compliance protocols.
External Cloud Attack Path Analysis
RiskProfiler helps your security teams stay ahead of evolving threats and external exposures through AI-generated attack path simulations. It helps you see your external attack surface from an adversarial perspective, providing a detailed view into possible vulnerability chains and paths of lateral movement with probability scores assigned to each simulated path. It allows you to prioritize mitigation based on real-life impact and accessibility, going beyond only technical implications.
Conclusion
Cloud breaches are one of the prime concerns in the current cybersecurity scenario. The modern cloud exposures are more complex than simple cloud misconfigurations or accidental asset exposures. Adversaries now exploit access and identities, manipulate OAuth tokens, CI/CD secrets, ephemeral services, and databases. This is why it is imperative to implement continuous cloud attack surface management modules for comprehensive monitoring and proactive exposure detection.
Secure your cloud environment by continuously monitoring external attack surface, supply chain integrations, access management, and OAuth catalogs with unified cyber threat intelligence modules like RiskProfiler. With continuous vigilance across systems, it identifies security gaps, analyzes the exposures, and prioritizes threats for fast mitigation.
Explore how the RiskProfiler CASM module surfaces your cloud exposures and hidden security gaps in real-time. Book a demo with our experts today.
In 2025, the majority of digital infrastructures will be hosted on cloud and containerized environments. As a result, cloud misconfigurations and asset exposures are among the major reasons for cybersecurity incidents and breaches in today’s time. According to the latest Cost of a Data Breach Report by IBM, 30% of cybersecurity incidents involve the systems in multi-cloud and hybrid environments. The average cost of a data breach on a hybrid or multi-cloud setup is around 5.5 million USD, according to the same report. It reflects on today’s reality of the volatility of cloud environments and also highlights why cloud attack surface management is essential for a resilient security strategy. Where traditional security tools enumerate issues, CASM reduces exposure risks by discovering cloud misconfigurations, validating exploitability, closing the loop with ownership, runbooks, and measurement.
The Risk of External Cloud Exposures
As the entire organizational workflow is hosted in the cloud and containerized spaces, system exposures can result from multiple reasons. Cloud integrations, both listed and shadow assets, use login details that can create exposures due to unhygienic password use and poor MFA protocols. The shadow integrations on a cloud system create major security blind spots as these tools lack the usual supervision of the security team, leaving them out of security audits and patch management.
SaaS databases accessible with old keys or legacy software tied to the digital ecosystem can also expose cloud systems to external threats. Vulnerabilities in CI/CD pipelines, like exposed Git configurations, poisoned DevOps workflows, IaC drifts, overpermissive integration or OAuth connections, are among some of the biggest cloud security concerns. Additionally, unsecured vendor connections or unsafe supply chain integration can also leave an organization’s digital system exposed to adversarial threats.
Top External Cloud Exposure Risks
Although cloud environments add flexibility, scalability, and accessibility to the workflows, the fast-evolving environments add unique complexity and security challenges to the analyst dashboard. In order to stay ahead of these threats, security leaders need to simulate real-world adversary tactics used by threat actors to exfiltrate data, deploy malware payloads, and exploit identity to test the resilience of the cloud ecosystem.
1. Identity and OAuth Token Abuse
Aversaries these days use stolen or compromised tokens by exploiting OAuth consent flows to bypass multi-factor authentication. These intrusions allow silent access to cloud storage and databases. Usual perimeter threat detection modules do not detect these instances of consent abuse and token misuse unless your external threat intelligence module is tailored to detect these shadow drifts.
2. Exposures in Code Repositories and CI/CD Pipelines
Exposures in Git repositories, CI/CD pipelines, and container layers can lead to significant security concerns. Often unnoticed during security audits, attackers can gain access to sensitive credentials, major databases, and cloud environments through these exposures. Thus, it is important to model exposure across development lifecycles to prevent compromises and reduce the blast radius in the event of cloud misconfigurations.

3. Hidden Gaps in Vendor & Supply Chain Network
Cloud environments are easy to integrate, and most tools in these environments operate within an interconnected network. This is why a breach in one system can snowball rapidly with over-permissive roles and a lack of zero-trust architecture. Modelling these paths with strong security guardrails enables security analysts to understand how a single compromised identity can escalate into a multi-cloud breach.
4. Data Warehouse Exfiltration
Cloud data warehouses often hold sensitive datasets but lack tailored security controls. Long-lived credentials and network-independent SQL access make them vulnerable to stealthy exfiltration processes. Modeling how identity misuse leads to data loss is critical, especially when attackers operate within the bounds of legitimate access.
Real-World Cloud Exposure Incidents
Recent cybersecurity incidents have highlighted the gaps in identity governance, token hygiene, and cloud misconfiguration. In this section, we will be talking about a few cloud threat incidents that came to the surface in recent years.
Snowflake Data Breach (2024)
The Snowflake breach campaign (UNC5537) revealed how stolen credentials, unhygienic login practices, and a lack of MFA protocol can lead to massive data exfiltration. The data breach in the Snowflake infrastructure was caused by stolen credentials that were previously exfiltrated by infostealer malware from external systems. In the breach event, around 165 organizations, including Ticketmaster, AT&T, Lending Tree, etc., were affected, leading to their data being sold on dark web marketplaces.
EmeraldWhale Cyberattack (2024)
In October 2024, Sysdig uncovered a major organized malicious cyber campaign by a threat actor, EmeraldWhale. In the campaign, the adversaries were targeting exposed Git configurations, leading to massive credential thefts from more than 15,000 cloud services from their source code and cloned repositories. During an investigation, Sysdig researchers found a suspicious, compromised account with malicious tools and more than a terabyte of data.
Salesforce Drift Compromise (August 2025)
The attack on Cloudflare and several other notable industry names began with a Salesloft Drift compromise, noticed in August 2025, carried out by the threat actor UNC6395. Cyber adversaries used a compromised OAuth token linked to the Salesloft Drift platform to gain access to the Cloudflare Salesforce instance. Using the compromised tokens, attackers exfiltrated sensitive customer and business information present in customer tokens.
External Cloud Attack Surface Management Lifecycle
In external cloud attack surface management, the threat intelligence modules continuously scan the cloud and containerized services to discover underlying gaps, vulnerabilities, and accidental exposures. Once identified, these risk signals are then prioritized based on their impact on operations, technical resilience, and relation to the probable attack chain. A high priority score in this stage dictates the security expert’s focus on the concerned exposure/cloud misconfiguration/vulnerability for effective mitigation.
Scanning for Cloud Misconfigurations and Material Exposure
Cloud attack surface management requires precise and contextual identification of the exposure type that can indicate a serious threat to operational continuity and business integrity. Identity and access exposure, external risk, leaks in the CI/CD pipeline, and shadow SaaS integrations are some of the serious concerns that the CASM modules scan for at this stage.
CASM modules, like RiskProfiler Nyx Cloud AI collect telemetry from cloud APIs, attack surface tools, identity graphs, data lineage systems, and SaaS catalogs. These inputs offer visibility into cloud misconfigurations, permissions, data flows, and third-party integrations for a unified view into possible exposures and security gaps.
Continuous Enumeration for Threat Detection
As the threat intel modules scan for threat signals, they identify anomalous activities, suspicious access requests, unusual system traffic, and other discrepancies to detect cloud exposures. The CASM tools also incorporate findings from dark web scans and infostealer telemetries to pinpoint vulnerable access points, compromised credentials, and exposed email accounts, ensuring visibility into cloud misconfigurations and evolving external threats.
Threat Prioritization with Attack Path Mapping
Once threat signals are identified, the modern AI-powered tools analyse the data, correlate the fragmented risks, and simulate possible attacker behaviour and movement across the system, from the access point to data exfiltration. Each threat is scored by its exposure, access privilege, and data sensitivity. This contextual mapping allows the machine to rate exposure based on its real-world impact on operations, finance, and reputation, going beyond the technical dependencies. RiskProfiler’s Nyx Cloud AI autonomously simulates adversarial movement across multi-cloud environments to model exposure probability.

Risk Signal Replay Tests for Validation
Cloud Threat Exposure Modules perform a detailed security evaluation to determine the environment’s exploitability using read-only tokens, policy simulations, and access controls. It allows security analysts to analyze and determine the threat level of each exposure, filter noise from essential threat alerts, and help teams concentrate on only verified risks.
Direct Security Teams with Contextual Action Plan
Upon validation and obtaining the contextual specifics, the alerts are assigned to specific teams based on their access and ownership. Service Level Objectives (SLOs) are set based on exposure materiality, ensuring timely resolution and accountability across business and technical stakeholders.
Fast Response and Risk Reduction
Cloud attack surface management modules with their fast detection, analysis, validation, and action plan enable fast response and reduce dwell time. It improves identity risk scores, OAuth hygiene, and prevents data exfiltration. These indicators help leaders assess progress, justify investments, and align security outcomes with business priorities.
Operationalize CASM at Scale with RiskProfiler
RiskProfiler cloud attack surface management is an AI-powered threat intelligence module that discovers underlying threats hiding in your cloud environment. Its agentic AI-assisted system monitors for risks, analyzes them based on related network connections, blast radius, operational impact, and business concerns, and sends contextual alerts for the security teams.
Comprehensive Monitoring of Cloud Attack Surface
RiskProfiler’s Nyx Agentic AI continuously monitors an organization’s external attack surface for cloud exposures in both the organizational system and third-party relationships. The comprehensive search and discovery allow the security teams to stay ahead of hidden vulnerabilities, cloud misconfigurations, and OAuth token compromises originating in a vendor system.
Identity and Accessibility Monitoring
RiskProfiler’s identity intelligence module discovers reused passwords, leaked credentials, and overpermissive roles in cloud integrations, allowing for a fast response. With its dark web monitoring module, Nyx Dark Web AI, RiskProfiler scans for leaked data, credentials, and email details in dark web marketplaces, forums, and paste sites. Advanced knowledge of these security gaps provides ample time to manage exposed systems and tighten security, preventing escalation and unauthorized access.
Correlate Exposed Assets to Data Risks
RiskProfiler’s cloud attack surface management module continuously maps external exposures, stale DNS, leaked repositories, misconfigured buckets, and expired certificates. The AI-powered system correlates external assets and leaked credentials to cloud identities, roles, and crown-jewel data stores to model real attack paths, quantify blast radius, and prioritize fixes that measurably reduce breach likelihood.

Threat Validation and Alert Prioritization
RiskProfiler’s threat intelligence engine analyzes the threat signals based on read-only probes, policy simulations, access permissions, and blast radium to separate real threats from noise. It also assigns impact scores and security ratings to each threat to help teams prioritize response based on their real-life impact on business, operations, and compliance protocols.
External Cloud Attack Path Analysis
RiskProfiler helps your security teams stay ahead of evolving threats and external exposures through AI-generated attack path simulations. It helps you see your external attack surface from an adversarial perspective, providing a detailed view into possible vulnerability chains and paths of lateral movement with probability scores assigned to each simulated path. It allows you to prioritize mitigation based on real-life impact and accessibility, going beyond only technical implications.
Conclusion
Cloud breaches are one of the prime concerns in the current cybersecurity scenario. The modern cloud exposures are more complex than simple cloud misconfigurations or accidental asset exposures. Adversaries now exploit access and identities, manipulate OAuth tokens, CI/CD secrets, ephemeral services, and databases. This is why it is imperative to implement continuous cloud attack surface management modules for comprehensive monitoring and proactive exposure detection.
Secure your cloud environment by continuously monitoring external attack surface, supply chain integrations, access management, and OAuth catalogs with unified cyber threat intelligence modules like RiskProfiler. With continuous vigilance across systems, it identifies security gaps, analyzes the exposures, and prioritizes threats for fast mitigation.
Explore how the RiskProfiler CASM module surfaces your cloud exposures and hidden security gaps in real-time. Book a demo with our experts today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



