Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


What is Attack Surface Intelligence?
What is Attack Surface Intelligence?
An organization’s digital footprint includes all connected devices, cloud infrastructure, software, and data streams that extend far beyond its internal infrastructure.
Read Time
7 min read
Posted On
Sep 17, 2025
Social Media
An organization’s digital footprint includes all connected devices, cloud infrastructure, software, and data streams that extend far beyond its internal infrastructure. It can be a publicly exposed code repository, a reused password, or a misconfigured storage unit on the cloud system that allows attackers to reach your system. To manage external risks effectively and build attack resilience, it is crucial to view the digital footprint from an adversarial perspective with proactive attack surface intelligence. This is the core principle behind understanding your organization’s “attack surface” and conducting thorough attack path analysis.
In this article, we will define what a modern external attack surface is, detail the methodologies for its systematic evaluation, and define its importance in a comprehensive security program. We will further explore how external exposure risks work in a real-world operational system by evaluating intelligence gathered from global businesses.
What is an external attack surface?
The external attack surface, or the cloud attack surface, encompasses all digital interactions of an organization outside of its internal perimeter that adversaries can exploit in an attack scenario. The key components of external attack surface include web assets such as corporate websites and portals, where every form and login interface can be used as an entry point. It also includes unsanctioned, abandoned, or misconfigured API integrations, which can create significant data exposure.
Additionally, the digital attack surface also includes an organization’s cloud and container environments, where misconfigurations or exposed storage units lead to critical data breaches. Sensitive credentials and essential network infrastructure, such as email servers and VPN gateways, can also be leaked from publicly exposed code repositories, leaving the digital systems vulnerable to external attacks.
What is Attack Surface Management in cybersecurity?
Attack Surface Management (ASM) is a set of security protocols that analyzes all real-time digital interactions and connections of an organizational system. For example, every SaaS login, test sites, and email engagement is part of your attack surface. A modern attack surface analysis workflow is built on several key pillars. It requires continuous discovery to constantly scan all environments and automatically update the asset inventory as the organization evolves. It leverages automated risk assessment to correlate data and provide real-world context and implications for threat signals. Furthermore, an effective attack surface management module provides integrated remediation workflows to streamline and accelerate the fixing process and delivers continuous monitoring and alerting to detect and respond to threats in real time, significantly shrinking the window of opportunity for attackers.
What is Attack Surface Analysis?
A cyber attack surface analysis is a methodical process for identifying, mapping, and rigorously assessing all potential entry points into an organization’s ecosystem. The attack surface analysis in a software development lifecycle is used to identify, analyze, and remediate possible vulnerabilities before they are exploited by attackers. It helps security and development teams map attacker movements in an environment, allowing focused threat mitigation.
Stage 1: Asset Discovery and Inventory
Comprehensive visibility into all digital assets and vendor relationships is important to strengthen cybersecurity across the organization. Lack of transparency into unlisted, abandoned, or forgotten assets created without an IT overview can become an entry point for future breaches. These rogue integrations pose critical security threats if left unchecked for a long time. By streamlining attack surface analysis with automated inventory tools, businesses can stay ahead of external exposure risks.
Stage 2: Vulnerability Scanning and Identification
Once all the listed and unlisted assets are identified, the next stage is to scan all these assets for hidden security flaws. Scanning the external attack surface with all cloud integrations and supply chain connections is critical to providing a complete view of vulnerabilities and unsecured entry points. It also helps security teams understand real-life attacker movement from the possible access points to the target assets.
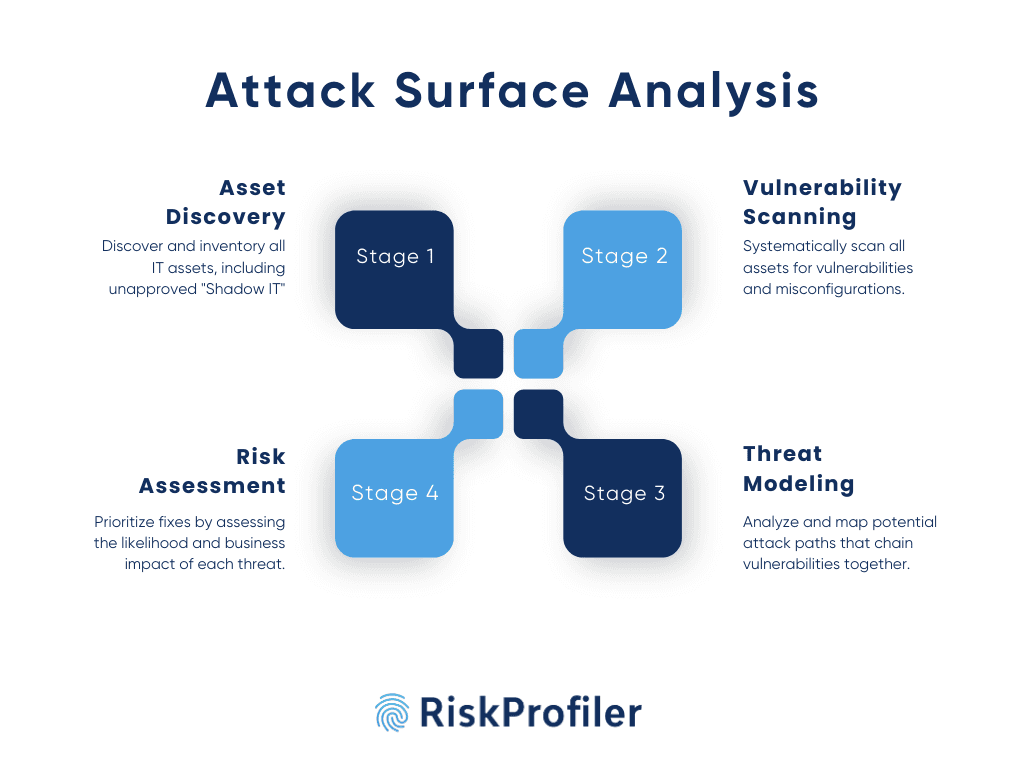
Stage 3: Threat Modeling and Attack Path Analysis
Simulating potential attacker movements by chaining all exposures and system vulnerabilities offers improved clarity of an organizational security posture. Using a structured framework like MITRE ATT&CK, NIST, etc., security teams simulate how an adversary can enter a system, escalate privilege, and reach high-value targets. It helps them identify shadow risks, gaps in MFA protocols, and insecure configurations that can be exploited during a breach incident. Additionally, this method highlights the importance of mitigating some “low-risk” threats that can be linked to a high-impact attack chain.
Stage 4: Risk Assessment and Prioritization
In the final stage, it evaluates the compliance, operational, and reputation risks associated with each vulnerability to ensure that remediation efforts are focused on the most critical threats. Here, the threat management module assesses the attack probability, the chances of a vulnerability being exploited, and analyzes business impacts to determine the financial penalties, losses, and other damages. These factors are then combined to produce a quantifiable risk score to build a prioritized remediation strategy.
The Real-World Threat Landscape
With the sprawling cloud environments and containerized systems, the attack surface is expanding exponentially, leading to increased external exposure risks and breach threats. Additionally, the sophistication of attack methods raises the complications even further.
The Staggering Financial Impact
The financial consequences of cybercrime have reached unprecedented levels. In the USA, the average cost of a single data breach has now climbed to a staggering $10.22 million, according to the IBM Cost of a Data Breach Report, 2025. This includes costs from incident response, regulatory fines, and long-term brand damage.
The Threat of Ransomware
Ransomware continues to be a dominant and devastating threat. According to the IBM report, the average fallout from a ransomware attack is $5.08 million. In another report published by Verizon this year, small and medium-sized businesses are highlighted as the prime targets of ransomware-related breaches. Where only 39% of breaches were attributed to ransomware attacks for large organizations, it was the leading cause in SMBs, with a staggering 89% of causation according to the Verizon Data Breach Investigations Report, 2025.
A Threat to Businesses of All Sizes
Although the commonly perceived notion around cybercrime tends to be, “criminals would attack the large fish for bigger benefits”, it does not stand true in the real world. According to the DBIR report, small-and medium-sized businesses make the 75% of the total cybercrime victims in the past year, 98% of which were caused by external threats.
RiskProfiler Attack Surface Intelligence: How Does It Work?
RiskProfiler threat intelligence platform goes beyond traditional scanning by combining proactive intelligence with actionable insights to deliver an extensive view of your organization’s threat exposure. The platform scans for external exposure risks, cloud misconfigurations, brand threats, third-party risks, and vulnerabilities, and maps the signals for fast response on a single unified platform.
External Attack Surface Analysis
RiskProfiler’s external attack surface management solution continuously monitors all listed and unlisted IT tools, domains, IPs, APIs, and SaaS integrations. This continuous threat visibility helps detect emerging security gaps and cloud attack vectors the moment they appear, enabling rapid response and preventing threat escalations.
Cloud Attack Surface Management
RiskProfiler cloud attack surface management tool integrates directly with leading cloud service providers like AWS, Azure, and GCP, along with regional services, to identify misconfigurations, overly permissive roles, and unmonitored endpoints. It highlights hidden risks across multi-cloud and hybrid environments on a single platform, removing security blind spots. It also helps security teams to implement stronger guardrails and achieve compliance with frameworks such as NIST, CIS, and ISO.
Supply Chain Risk Management
RiskProfiler’s third-party risk management program maps your supply chain ecosystems by continuously profiling security gaps and actor vectors emerging on their infrastructure. It evaluates vendors’ exposures, credential leaks, misconfigurations, and compliance failures, helping you prevent “weak link” scenarios where a partner’s breach becomes your breach.
Additionally, the platform distributes vendor risk questionnaires to the vendors, partners, and extended suppliers on detection of any anomalous activity or emerging exposure risks.
Advanced Vulnerability Intelligence
RiskProfiler’s Vulnerability Intelligence module correlates findings with open-source and proprietary threat intelligence feeds, IOCs, CVE-CVSS scores, and active adversary tactics to determine which vulnerabilities are most likely to be exploited. This prioritization helps security teams move from reactive patching to strategic remediation.
Proactive Cyber Threat Intelligence
RiskProfiler cyber threat intelligence does not just rely on automation. It proactively scans for indicators of compromise, anomalous behaviors, suspicious traffic requests, and hidden entry points across your environment. The use of effective automated open-source and proprietary intelligence uncovers hidden external risks that traditional scanners miss.
Dark Web Intelligence
An organizational risk surface extends far beyond what’s visible on the internet. RiskProfiler dark web monitoring tools scan the dark web forums, marketplaces, and paste sites to detect suspicious mentions about your organization, leaked credentials, and stolen intellectual property. By combining brand intelligence with dark web threat monitoring, RiskProfiler gives you early warning signals of impending attacks or fraud campaigns targeting your brand.
Contextualized Risk Analysis & Threat Prioritization
RiskProfiler assesses vulnerabilities and exposures specific to your business and industry needs and shares only the alerts that your team needs to see. It also highlights risks based on their impact on operational integrity, industry regulations, reputation, and financial implications. This reduces alert fatigue, eliminates the noise, and helps them focus on the sensitive threats effectively.
Strategic Threat Reporting
RiskProfiler provides reports that map risks to business impact, regulatory requirements, and compliance frameworks (GDPR, HIPAA, PCI-DSS, SOC 2) that can assist in boardroom conversations and compliance discussions. This empowers CISOs and business leadership to make informed decisions and demonstrate proactive risk management to auditors and stakeholders.
Attack Surface Intelligence: The Proactive Cyber Defense
Your external attack surface consists of invisible and vulnerable access points to your digital system. Understanding, managing, and proactively securing these entry paths is the most effective strategy for building a resilient and secure organization. Continuous monitoring of your organization’s external and cloud attack surface is no longer an option, but a crucial part of strengthened security and success in the modern digital world.
RiskProfiler’s cyber threat intelligence platform maps your external attack surface, analyzes your risk exposure, and presents contextual threat data with severity scores for prioritized and rapid mitigation.
Analyze your external exposure risks with a personalized demo to enhance security resilience.
An organization’s digital footprint includes all connected devices, cloud infrastructure, software, and data streams that extend far beyond its internal infrastructure. It can be a publicly exposed code repository, a reused password, or a misconfigured storage unit on the cloud system that allows attackers to reach your system. To manage external risks effectively and build attack resilience, it is crucial to view the digital footprint from an adversarial perspective with proactive attack surface intelligence. This is the core principle behind understanding your organization’s “attack surface” and conducting thorough attack path analysis.
In this article, we will define what a modern external attack surface is, detail the methodologies for its systematic evaluation, and define its importance in a comprehensive security program. We will further explore how external exposure risks work in a real-world operational system by evaluating intelligence gathered from global businesses.
What is an external attack surface?
The external attack surface, or the cloud attack surface, encompasses all digital interactions of an organization outside of its internal perimeter that adversaries can exploit in an attack scenario. The key components of external attack surface include web assets such as corporate websites and portals, where every form and login interface can be used as an entry point. It also includes unsanctioned, abandoned, or misconfigured API integrations, which can create significant data exposure.
Additionally, the digital attack surface also includes an organization’s cloud and container environments, where misconfigurations or exposed storage units lead to critical data breaches. Sensitive credentials and essential network infrastructure, such as email servers and VPN gateways, can also be leaked from publicly exposed code repositories, leaving the digital systems vulnerable to external attacks.
What is Attack Surface Management in cybersecurity?
Attack Surface Management (ASM) is a set of security protocols that analyzes all real-time digital interactions and connections of an organizational system. For example, every SaaS login, test sites, and email engagement is part of your attack surface. A modern attack surface analysis workflow is built on several key pillars. It requires continuous discovery to constantly scan all environments and automatically update the asset inventory as the organization evolves. It leverages automated risk assessment to correlate data and provide real-world context and implications for threat signals. Furthermore, an effective attack surface management module provides integrated remediation workflows to streamline and accelerate the fixing process and delivers continuous monitoring and alerting to detect and respond to threats in real time, significantly shrinking the window of opportunity for attackers.
What is Attack Surface Analysis?
A cyber attack surface analysis is a methodical process for identifying, mapping, and rigorously assessing all potential entry points into an organization’s ecosystem. The attack surface analysis in a software development lifecycle is used to identify, analyze, and remediate possible vulnerabilities before they are exploited by attackers. It helps security and development teams map attacker movements in an environment, allowing focused threat mitigation.
Stage 1: Asset Discovery and Inventory
Comprehensive visibility into all digital assets and vendor relationships is important to strengthen cybersecurity across the organization. Lack of transparency into unlisted, abandoned, or forgotten assets created without an IT overview can become an entry point for future breaches. These rogue integrations pose critical security threats if left unchecked for a long time. By streamlining attack surface analysis with automated inventory tools, businesses can stay ahead of external exposure risks.
Stage 2: Vulnerability Scanning and Identification
Once all the listed and unlisted assets are identified, the next stage is to scan all these assets for hidden security flaws. Scanning the external attack surface with all cloud integrations and supply chain connections is critical to providing a complete view of vulnerabilities and unsecured entry points. It also helps security teams understand real-life attacker movement from the possible access points to the target assets.

Stage 3: Threat Modeling and Attack Path Analysis
Simulating potential attacker movements by chaining all exposures and system vulnerabilities offers improved clarity of an organizational security posture. Using a structured framework like MITRE ATT&CK, NIST, etc., security teams simulate how an adversary can enter a system, escalate privilege, and reach high-value targets. It helps them identify shadow risks, gaps in MFA protocols, and insecure configurations that can be exploited during a breach incident. Additionally, this method highlights the importance of mitigating some “low-risk” threats that can be linked to a high-impact attack chain.
Stage 4: Risk Assessment and Prioritization
In the final stage, it evaluates the compliance, operational, and reputation risks associated with each vulnerability to ensure that remediation efforts are focused on the most critical threats. Here, the threat management module assesses the attack probability, the chances of a vulnerability being exploited, and analyzes business impacts to determine the financial penalties, losses, and other damages. These factors are then combined to produce a quantifiable risk score to build a prioritized remediation strategy.
The Real-World Threat Landscape
With the sprawling cloud environments and containerized systems, the attack surface is expanding exponentially, leading to increased external exposure risks and breach threats. Additionally, the sophistication of attack methods raises the complications even further.
The Staggering Financial Impact
The financial consequences of cybercrime have reached unprecedented levels. In the USA, the average cost of a single data breach has now climbed to a staggering $10.22 million, according to the IBM Cost of a Data Breach Report, 2025. This includes costs from incident response, regulatory fines, and long-term brand damage.
The Threat of Ransomware
Ransomware continues to be a dominant and devastating threat. According to the IBM report, the average fallout from a ransomware attack is $5.08 million. In another report published by Verizon this year, small and medium-sized businesses are highlighted as the prime targets of ransomware-related breaches. Where only 39% of breaches were attributed to ransomware attacks for large organizations, it was the leading cause in SMBs, with a staggering 89% of causation according to the Verizon Data Breach Investigations Report, 2025.
A Threat to Businesses of All Sizes
Although the commonly perceived notion around cybercrime tends to be, “criminals would attack the large fish for bigger benefits”, it does not stand true in the real world. According to the DBIR report, small-and medium-sized businesses make the 75% of the total cybercrime victims in the past year, 98% of which were caused by external threats.
RiskProfiler Attack Surface Intelligence: How Does It Work?
RiskProfiler threat intelligence platform goes beyond traditional scanning by combining proactive intelligence with actionable insights to deliver an extensive view of your organization’s threat exposure. The platform scans for external exposure risks, cloud misconfigurations, brand threats, third-party risks, and vulnerabilities, and maps the signals for fast response on a single unified platform.
External Attack Surface Analysis
RiskProfiler’s external attack surface management solution continuously monitors all listed and unlisted IT tools, domains, IPs, APIs, and SaaS integrations. This continuous threat visibility helps detect emerging security gaps and cloud attack vectors the moment they appear, enabling rapid response and preventing threat escalations.
Cloud Attack Surface Management
RiskProfiler cloud attack surface management tool integrates directly with leading cloud service providers like AWS, Azure, and GCP, along with regional services, to identify misconfigurations, overly permissive roles, and unmonitored endpoints. It highlights hidden risks across multi-cloud and hybrid environments on a single platform, removing security blind spots. It also helps security teams to implement stronger guardrails and achieve compliance with frameworks such as NIST, CIS, and ISO.
Supply Chain Risk Management
RiskProfiler’s third-party risk management program maps your supply chain ecosystems by continuously profiling security gaps and actor vectors emerging on their infrastructure. It evaluates vendors’ exposures, credential leaks, misconfigurations, and compliance failures, helping you prevent “weak link” scenarios where a partner’s breach becomes your breach.
Additionally, the platform distributes vendor risk questionnaires to the vendors, partners, and extended suppliers on detection of any anomalous activity or emerging exposure risks.
Advanced Vulnerability Intelligence
RiskProfiler’s Vulnerability Intelligence module correlates findings with open-source and proprietary threat intelligence feeds, IOCs, CVE-CVSS scores, and active adversary tactics to determine which vulnerabilities are most likely to be exploited. This prioritization helps security teams move from reactive patching to strategic remediation.
Proactive Cyber Threat Intelligence
RiskProfiler cyber threat intelligence does not just rely on automation. It proactively scans for indicators of compromise, anomalous behaviors, suspicious traffic requests, and hidden entry points across your environment. The use of effective automated open-source and proprietary intelligence uncovers hidden external risks that traditional scanners miss.
Dark Web Intelligence
An organizational risk surface extends far beyond what’s visible on the internet. RiskProfiler dark web monitoring tools scan the dark web forums, marketplaces, and paste sites to detect suspicious mentions about your organization, leaked credentials, and stolen intellectual property. By combining brand intelligence with dark web threat monitoring, RiskProfiler gives you early warning signals of impending attacks or fraud campaigns targeting your brand.
Contextualized Risk Analysis & Threat Prioritization
RiskProfiler assesses vulnerabilities and exposures specific to your business and industry needs and shares only the alerts that your team needs to see. It also highlights risks based on their impact on operational integrity, industry regulations, reputation, and financial implications. This reduces alert fatigue, eliminates the noise, and helps them focus on the sensitive threats effectively.
Strategic Threat Reporting
RiskProfiler provides reports that map risks to business impact, regulatory requirements, and compliance frameworks (GDPR, HIPAA, PCI-DSS, SOC 2) that can assist in boardroom conversations and compliance discussions. This empowers CISOs and business leadership to make informed decisions and demonstrate proactive risk management to auditors and stakeholders.
Attack Surface Intelligence: The Proactive Cyber Defense
Your external attack surface consists of invisible and vulnerable access points to your digital system. Understanding, managing, and proactively securing these entry paths is the most effective strategy for building a resilient and secure organization. Continuous monitoring of your organization’s external and cloud attack surface is no longer an option, but a crucial part of strengthened security and success in the modern digital world.
RiskProfiler’s cyber threat intelligence platform maps your external attack surface, analyzes your risk exposure, and presents contextual threat data with severity scores for prioritized and rapid mitigation.
Analyze your external exposure risks with a personalized demo to enhance security resilience.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



