Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Importance of External Attack Surface Monitoring
Importance of External Attack Surface Monitoring
The 21st-century modern-day businesses are heavily reliant on technology and various software tools for day-to-day operations. From entertainment to essential services, from online shopping, to travel bookings, healthcare, education, and even automotive operations, everything is conducted via connected systems, cloud servers, and different tools.
Read Time
7 min read
Posted On
Mar 11, 2025
Social Media
The 21st-century modern-day businesses are heavily reliant on technology and various software tools for day-to-day operations. From entertainment to essential services, from online shopping, to travel bookings, healthcare, education, and even automotive operations, everything is conducted via connected systems, cloud servers, and different tools. Using these connected services makes our lives easier and helps us complete tasks within minutes. However, the integration of hyperconnected cloud networks into business systems expands its attack surface exponentially, which requires effective attack surface management efforts. Cloud systems use APIs to connect with different software tools to provide comprehensive services across different tools. As teams across different industries adopt work-from-home and hybrid work cultures, the dependency on these tools for regular operation has also increased. Besides providing convenience, digital dependency also increases asset exposures and system vulnerabilities. The hyper-reliance on API gateways to provide software services also alleviates the risks of misconfiguration and shadow IT, rendering crucial assets volatile to external attacks. An external attack surface monitoring tool can however help your team track, detect, and effectively mitigate hidden vulnerabilities and potential security risks with actionable intelligence.
Thus, continuous threat exposure management and attack surface management initiatives become essential appendages to cyber threat intelligence.
Why Attack Surface Monitoring is Necessary?
In the past, organizations relied on traditional perimeter-based security models, protecting their internal networks with firewalls, intrusion detection systems, and on-premises security solutions. However, this approach is no longer sufficient due to several factors:
Cloud-Based Applications and SaaS Adoption
Businesses increasingly rely on cloud services to offer comprehensive and convenient services to users. As a part of these cloud services, sensitive data, and customer information are stored on cloud storage and Kubernetes networks. Storing the vital databases in decentralized systems increases the security stakes, which may not be handled well by traditional perimeter-based security systems.
Remote Work and BYOD (Bring Your Own Device) Policies
As the work environment shifts towards more flexible work-from-home and hybrid work policies, employees access corporate resources from personal devices and unsecured networks. This exposes the business to vulnerable IP addresses and access points, increasing the attack surface considerably.
Third-party Integrations and Supply Chain Risks
Modern-day businesses require support from several third-party software or SaaS tools like payment gateways or scheduling tools to provide comprehensive service to their clients. These third-party integration creates multiple access points to your business systems, that if left unmonitored, can introduce vulnerabilities and security threats to your system.
Unregistered Digital Assets or Shadow IT
Businesses are required to maintain an updated inventory of all software integration to the system to collect accurate intelligence of threat exposure data. However, employees and departments often access unapproved applications and services without notifying the business, creating security blind spots.
These factors contribute to a growing and often unmanaged attack surface, making it imperative for security teams to gain real-time visibility into their organization’s digital footprint.
Understanding the Risks: Shadow IT & Hidden Vulnerabilities
Hidden vulnerabilities are the hidden threats that live in the system undetected for a long time and can be exploited by attackers to gain access to the system. These vulnerabilities can be present as unfamiliar software integrations, unsecured IP addresses, or misconfigured API gateways. Securing these weaknesses is vital in maintaining a strong security posture for your business system.
What is Shadow IT?
Shadow IT refers to any technology—software, cloud services, or hardware—used by employees without the approval of the IT or security team. While it often arises from the need for efficiency and convenience, it introduces serious security risks as it creates security blind spots, introducing unmonitored access points to your system.
How Shadow IT Creates Security Blind Spots?
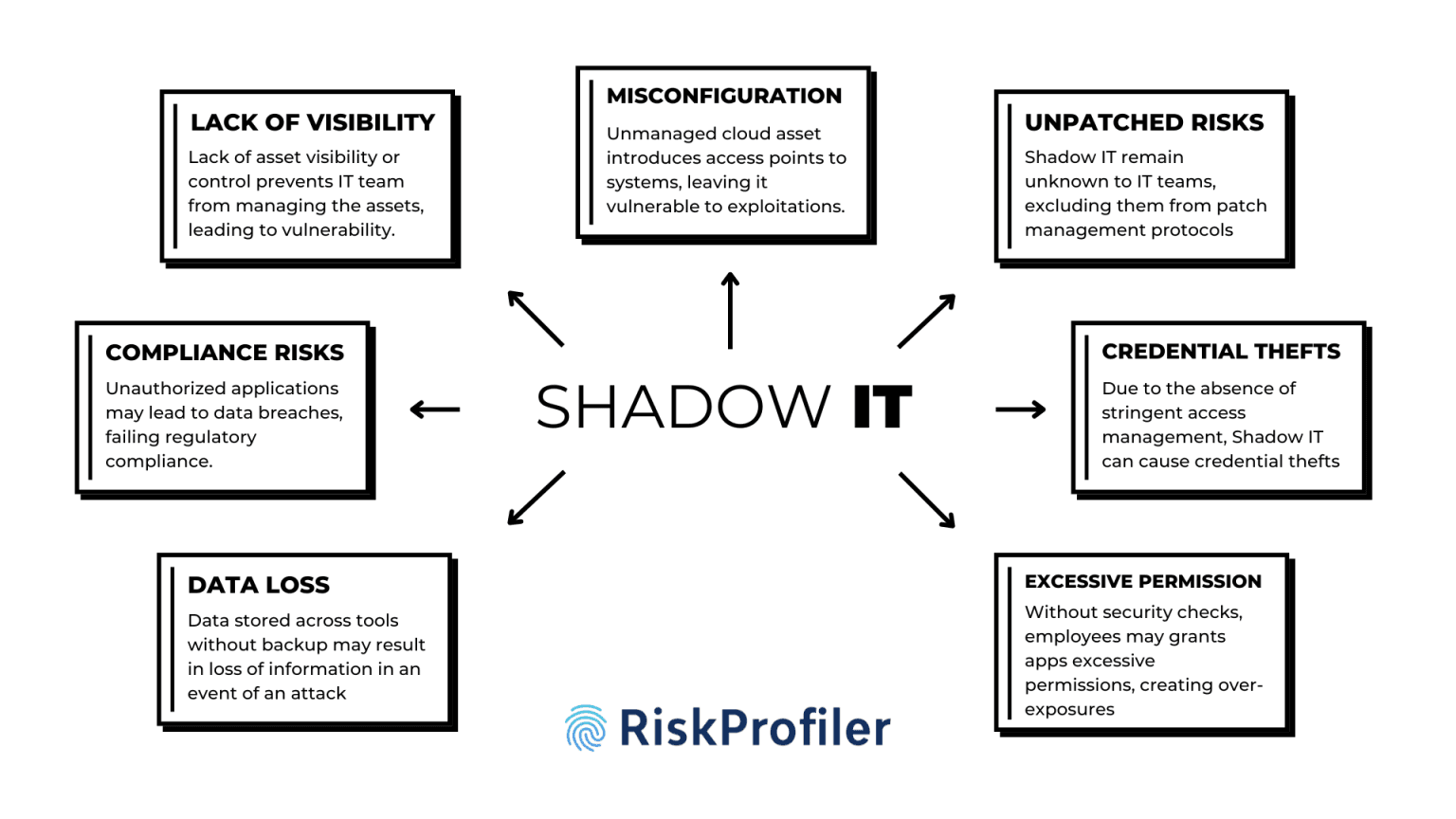
Obscured IT Landscape and Security Gaps – When employees or departments adopt software, cloud services, or hardware without IT approval, these tools operate outside the organization’s security framework. This lack of visibility prevents security teams from monitoring, securing, or enforcing compliance measures on these assets. As a result, unapproved tools create hidden vulnerabilities, increasing the risk of cyberattacks, data breaches, and operational inefficiencies.
Potential for Misconfigurations – Unmanaged cloud services often have default settings that expose sensitive data to third-party entities. Due to their obscured presence in the system, these access points remain unmanaged during security checks or updates, leaving them vulnerable to future security attacks.
Unpatched Vulnerabilities and Security Exposures – Shadow IT tools and devices often remain unknown to the IT and security teams, meaning they are not included in regular security updates, patch management, or vulnerability assessments. Without proper monitoring, these unpatched assets become prime targets for cybercriminals who exploit outdated software to gain unauthorized access, deploy malware, or exfiltrate sensitive data, significantly increasing the organization’s attack surface.
Compliance and Data Security Risks – Unauthorized tools can lead to business and customer data breaches. Such leaks can lead to vulnerabilities in data security, leading to regulatory compliance breaches and legal penalties.
Increased Risk of Credential Theft and Phishing Attacks – Shadow IT tools often bypass standard authentication protocols, such as multi-factor authentication (MFA) or single sign-on (SSO), making them prime targets for credential theft. Employees using personal accounts or weak passwords for unauthorized applications increase the risk of phishing attacks and credential stuffing.
Data Fragmentation and Loss – Shadow IT leads to data being stored across multiple, unapproved platforms, often without proper backup or integration with the organization’s official IT infrastructure. This fragmentation makes it difficult to track, manage, and recover critical business information.
Inconsistent Access Controls and Privilege Escalation – Without IT oversight, employees may inadvertently grant excessive permissions to unauthorized users or third-party applications, creating security loopholes. This uncontrolled privilege escalation can lead to unauthorized data access, system manipulation, or even full-scale breaches that compromise the organization’s security posture.
Why Continuous Attack Surface Monitoring Matters?
Traditional security assessments, such as annual audits and periodic vulnerability scans, are no longer sufficient. In a hyperconnected world where your business operation relies on the security posture of interconnected systems, cyber threats evolve rapidly. To protect the system and operational integrity from external attacks and vulnerabilities, organizations need real-time visibility into their attack surface to detect and mitigate risks proactively.
Attack Surface Monitoring: Best Practices
Attack surface monitoring assists businesses in staying updated on the threat posture and allows businesses to take proactive measures to contain the cyber threat in real time. The benefits of continuous attack surface monitoring are as follows:
Identifying Unauthorized or Forgotten Assets
Automated cyber threat intelligence systems utilize discovery tools to detect unknown or unmanaged digital assets. RiskProfiler uses its internet inventory tool to continuously monitor and update the digital asset inventory with detailed intelligence to help your team stay informed of your assets and their security health at all times.
Detecting Misconfigurations and Unpatched Vulnerabilities
External attack surface monitoring also aids in real-time threat detection and vulnerability scanning. This proactive threat intelligence allows security teams to have a detailed status report on all system and asset configurations, revealing any potential security gaps before they are exploited.
Strengthening Incident Response
Leveraging proactive attack surface management, organizations can gather threat intelligence on system vulnerabilities or attack attempts as they emerge. This instantaneous threat intelligence allows the security teams to prepare a suitable mitigation plan for improved threat response.
RiskProfiler Attack Surface Monitoring: Key Benefits
Integration of an efficient attack surface monitoring solution to your cyber security program allows you to gain an extensive view of your network. Your organization can utilize the full benefit of attack surface management solutions by following some simple yet crucial steps during the integration process.
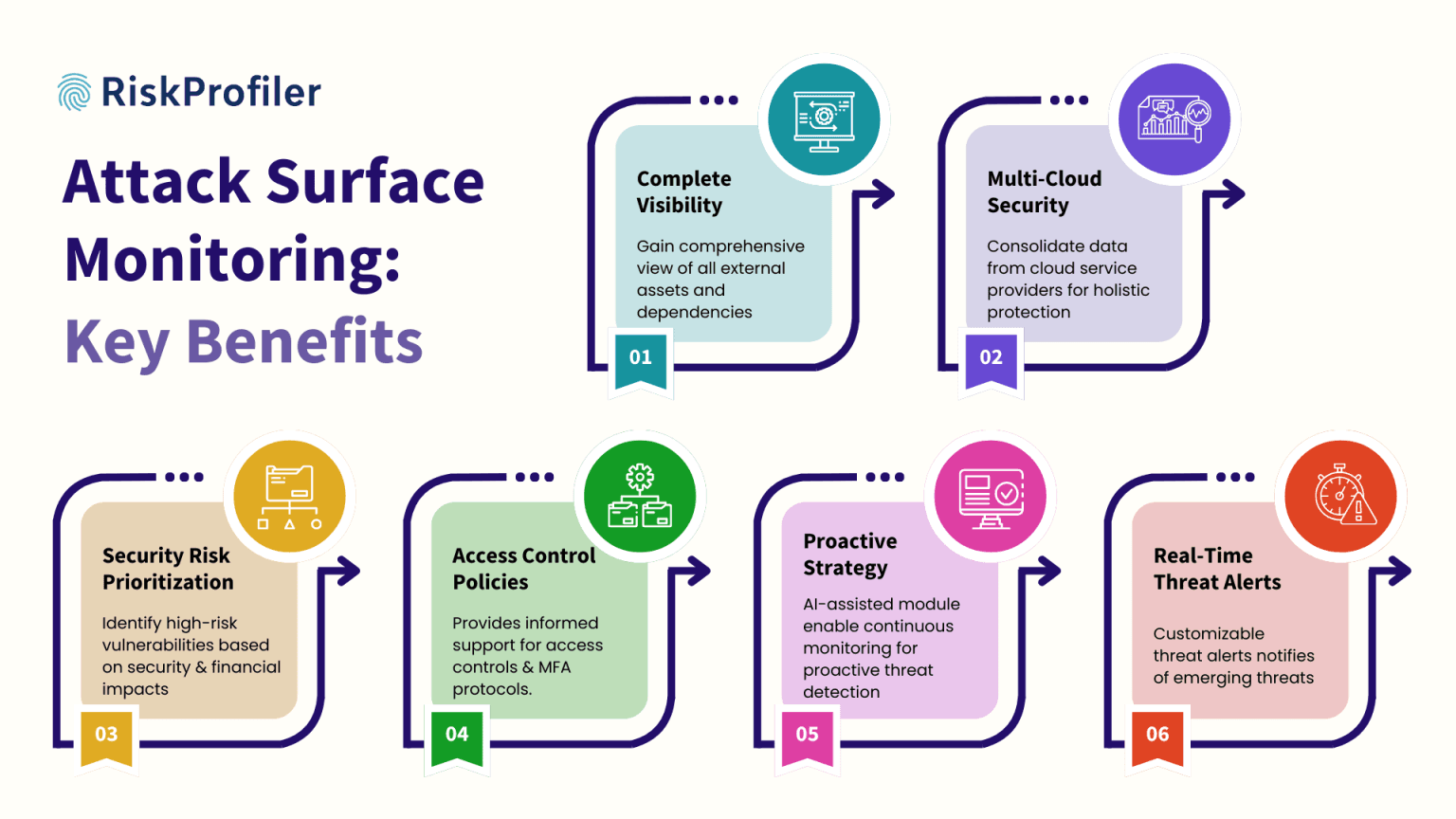
1. Gain Complete Visibility
Attack surface monitoring tools such as the RiskProfiler external attack surface management tool are capable of maintaining an updated asset inventory at all times. Integrating all digital assets, including cloud services, endpoints, and third-party integrations into your threat intelligence tool helps you keep track of the registered assets. External attack surface management tools can also be used to automate the detection of unknown assets and shadow IT. Furthermore, some tools like RiskProfiler, allow you to map your external attack surface to discover potentially vulnerable routes that can lead to future exploitation. This detailed intelligence-backed attack paths analysis allows you to find and secure these vulnerabilities, strengthening your overall security efforts.
2. Fortify Multi-Cloud Security
Cloud attack surface management solutions provide extensive support to secure multi-cloud systems from potential risks, vulnerabilities, misconfiguration, exposures, or attacks. Cyber threat intelligence software like RiskProfiler consolidates data from public cloud resources from various cloud service providers (i.e. AWS, Azure, etc.), allowing you unparalleled visibility into these multi-cloud systems to maintain security resilience.
3. Assess & Prioritize Risks
Continuous monitoring and threat analysis features of a cloud attack surface monitoring tool also help your security team identify high-risk vulnerabilities based on their threat exposure and impact. Continuous assessment of your overall security posture provides assistance with addressing evolving threats and system vulnerabilities.
4. Enforce Security Policies & Governance
Cyber threat intelligence tools also provide ample support for implementing strict access controls and authentication measures. It helps you detect unsecured access points, tools, and software to secure them before external attackers can manipulate them. It also helps you educate employees on shadow IT risks and enforce approved tools to safeguard your organization from unwanted exposures or security threats.
5. Adopt a Proactive Security Strategy
Attack surface management tools utilize AI-driven security analytics for real-time threat detection and contextualization. It allows security teams to identify threats before they materialize while preparing and executing mitigation plans to reduce damage. The threat data collected by related cyber threat intelligence systems can be utilized to regularly update security frameworks and compliance measures.
6. Real-Time Threat Alert
External attack surface management tools also incorporate an effective threat alert system that notifies your security team of any emerging threats in real time based on the priority and threat impact score. This process, while allowing your team to focus on the most sensitive threat concern, also reduces spam alerts and false positives, improving the effectiveness of the remediation process.
Conclusion: Strengthening Security in a Perimeter-less World
In today’s dynamic digital landscape, securing the attack surface requires a shift from traditional security models to external attack surface management. Organizations must prioritize real-time visibility to identify hidden vulnerabilities, mitigate shadow IT risks, and stay ahead of evolving cyber threats.
By proactively monitoring and managing their attack surface, businesses can strengthen their security posture, ensure compliance, and safeguard their critical assets. The key to a secure future is not just protection but also continuous vigilance.
Are you ready to take control of your attack surface? Start by implementing a comprehensive external attack surface management solution today.
The 21st-century modern-day businesses are heavily reliant on technology and various software tools for day-to-day operations. From entertainment to essential services, from online shopping, to travel bookings, healthcare, education, and even automotive operations, everything is conducted via connected systems, cloud servers, and different tools. Using these connected services makes our lives easier and helps us complete tasks within minutes. However, the integration of hyperconnected cloud networks into business systems expands its attack surface exponentially, which requires effective attack surface management efforts. Cloud systems use APIs to connect with different software tools to provide comprehensive services across different tools. As teams across different industries adopt work-from-home and hybrid work cultures, the dependency on these tools for regular operation has also increased. Besides providing convenience, digital dependency also increases asset exposures and system vulnerabilities. The hyper-reliance on API gateways to provide software services also alleviates the risks of misconfiguration and shadow IT, rendering crucial assets volatile to external attacks. An external attack surface monitoring tool can however help your team track, detect, and effectively mitigate hidden vulnerabilities and potential security risks with actionable intelligence.
Thus, continuous threat exposure management and attack surface management initiatives become essential appendages to cyber threat intelligence.
Why Attack Surface Monitoring is Necessary?
In the past, organizations relied on traditional perimeter-based security models, protecting their internal networks with firewalls, intrusion detection systems, and on-premises security solutions. However, this approach is no longer sufficient due to several factors:
Cloud-Based Applications and SaaS Adoption
Businesses increasingly rely on cloud services to offer comprehensive and convenient services to users. As a part of these cloud services, sensitive data, and customer information are stored on cloud storage and Kubernetes networks. Storing the vital databases in decentralized systems increases the security stakes, which may not be handled well by traditional perimeter-based security systems.
Remote Work and BYOD (Bring Your Own Device) Policies
As the work environment shifts towards more flexible work-from-home and hybrid work policies, employees access corporate resources from personal devices and unsecured networks. This exposes the business to vulnerable IP addresses and access points, increasing the attack surface considerably.
Third-party Integrations and Supply Chain Risks
Modern-day businesses require support from several third-party software or SaaS tools like payment gateways or scheduling tools to provide comprehensive service to their clients. These third-party integration creates multiple access points to your business systems, that if left unmonitored, can introduce vulnerabilities and security threats to your system.
Unregistered Digital Assets or Shadow IT
Businesses are required to maintain an updated inventory of all software integration to the system to collect accurate intelligence of threat exposure data. However, employees and departments often access unapproved applications and services without notifying the business, creating security blind spots.
These factors contribute to a growing and often unmanaged attack surface, making it imperative for security teams to gain real-time visibility into their organization’s digital footprint.
Understanding the Risks: Shadow IT & Hidden Vulnerabilities
Hidden vulnerabilities are the hidden threats that live in the system undetected for a long time and can be exploited by attackers to gain access to the system. These vulnerabilities can be present as unfamiliar software integrations, unsecured IP addresses, or misconfigured API gateways. Securing these weaknesses is vital in maintaining a strong security posture for your business system.
What is Shadow IT?
Shadow IT refers to any technology—software, cloud services, or hardware—used by employees without the approval of the IT or security team. While it often arises from the need for efficiency and convenience, it introduces serious security risks as it creates security blind spots, introducing unmonitored access points to your system.
How Shadow IT Creates Security Blind Spots?

Obscured IT Landscape and Security Gaps – When employees or departments adopt software, cloud services, or hardware without IT approval, these tools operate outside the organization’s security framework. This lack of visibility prevents security teams from monitoring, securing, or enforcing compliance measures on these assets. As a result, unapproved tools create hidden vulnerabilities, increasing the risk of cyberattacks, data breaches, and operational inefficiencies.
Potential for Misconfigurations – Unmanaged cloud services often have default settings that expose sensitive data to third-party entities. Due to their obscured presence in the system, these access points remain unmanaged during security checks or updates, leaving them vulnerable to future security attacks.
Unpatched Vulnerabilities and Security Exposures – Shadow IT tools and devices often remain unknown to the IT and security teams, meaning they are not included in regular security updates, patch management, or vulnerability assessments. Without proper monitoring, these unpatched assets become prime targets for cybercriminals who exploit outdated software to gain unauthorized access, deploy malware, or exfiltrate sensitive data, significantly increasing the organization’s attack surface.
Compliance and Data Security Risks – Unauthorized tools can lead to business and customer data breaches. Such leaks can lead to vulnerabilities in data security, leading to regulatory compliance breaches and legal penalties.
Increased Risk of Credential Theft and Phishing Attacks – Shadow IT tools often bypass standard authentication protocols, such as multi-factor authentication (MFA) or single sign-on (SSO), making them prime targets for credential theft. Employees using personal accounts or weak passwords for unauthorized applications increase the risk of phishing attacks and credential stuffing.
Data Fragmentation and Loss – Shadow IT leads to data being stored across multiple, unapproved platforms, often without proper backup or integration with the organization’s official IT infrastructure. This fragmentation makes it difficult to track, manage, and recover critical business information.
Inconsistent Access Controls and Privilege Escalation – Without IT oversight, employees may inadvertently grant excessive permissions to unauthorized users or third-party applications, creating security loopholes. This uncontrolled privilege escalation can lead to unauthorized data access, system manipulation, or even full-scale breaches that compromise the organization’s security posture.
Why Continuous Attack Surface Monitoring Matters?
Traditional security assessments, such as annual audits and periodic vulnerability scans, are no longer sufficient. In a hyperconnected world where your business operation relies on the security posture of interconnected systems, cyber threats evolve rapidly. To protect the system and operational integrity from external attacks and vulnerabilities, organizations need real-time visibility into their attack surface to detect and mitigate risks proactively.
Attack Surface Monitoring: Best Practices
Attack surface monitoring assists businesses in staying updated on the threat posture and allows businesses to take proactive measures to contain the cyber threat in real time. The benefits of continuous attack surface monitoring are as follows:
Identifying Unauthorized or Forgotten Assets
Automated cyber threat intelligence systems utilize discovery tools to detect unknown or unmanaged digital assets. RiskProfiler uses its internet inventory tool to continuously monitor and update the digital asset inventory with detailed intelligence to help your team stay informed of your assets and their security health at all times.
Detecting Misconfigurations and Unpatched Vulnerabilities
External attack surface monitoring also aids in real-time threat detection and vulnerability scanning. This proactive threat intelligence allows security teams to have a detailed status report on all system and asset configurations, revealing any potential security gaps before they are exploited.
Strengthening Incident Response
Leveraging proactive attack surface management, organizations can gather threat intelligence on system vulnerabilities or attack attempts as they emerge. This instantaneous threat intelligence allows the security teams to prepare a suitable mitigation plan for improved threat response.
RiskProfiler Attack Surface Monitoring: Key Benefits
Integration of an efficient attack surface monitoring solution to your cyber security program allows you to gain an extensive view of your network. Your organization can utilize the full benefit of attack surface management solutions by following some simple yet crucial steps during the integration process.

1. Gain Complete Visibility
Attack surface monitoring tools such as the RiskProfiler external attack surface management tool are capable of maintaining an updated asset inventory at all times. Integrating all digital assets, including cloud services, endpoints, and third-party integrations into your threat intelligence tool helps you keep track of the registered assets. External attack surface management tools can also be used to automate the detection of unknown assets and shadow IT. Furthermore, some tools like RiskProfiler, allow you to map your external attack surface to discover potentially vulnerable routes that can lead to future exploitation. This detailed intelligence-backed attack paths analysis allows you to find and secure these vulnerabilities, strengthening your overall security efforts.
2. Fortify Multi-Cloud Security
Cloud attack surface management solutions provide extensive support to secure multi-cloud systems from potential risks, vulnerabilities, misconfiguration, exposures, or attacks. Cyber threat intelligence software like RiskProfiler consolidates data from public cloud resources from various cloud service providers (i.e. AWS, Azure, etc.), allowing you unparalleled visibility into these multi-cloud systems to maintain security resilience.
3. Assess & Prioritize Risks
Continuous monitoring and threat analysis features of a cloud attack surface monitoring tool also help your security team identify high-risk vulnerabilities based on their threat exposure and impact. Continuous assessment of your overall security posture provides assistance with addressing evolving threats and system vulnerabilities.
4. Enforce Security Policies & Governance
Cyber threat intelligence tools also provide ample support for implementing strict access controls and authentication measures. It helps you detect unsecured access points, tools, and software to secure them before external attackers can manipulate them. It also helps you educate employees on shadow IT risks and enforce approved tools to safeguard your organization from unwanted exposures or security threats.
5. Adopt a Proactive Security Strategy
Attack surface management tools utilize AI-driven security analytics for real-time threat detection and contextualization. It allows security teams to identify threats before they materialize while preparing and executing mitigation plans to reduce damage. The threat data collected by related cyber threat intelligence systems can be utilized to regularly update security frameworks and compliance measures.
6. Real-Time Threat Alert
External attack surface management tools also incorporate an effective threat alert system that notifies your security team of any emerging threats in real time based on the priority and threat impact score. This process, while allowing your team to focus on the most sensitive threat concern, also reduces spam alerts and false positives, improving the effectiveness of the remediation process.
Conclusion: Strengthening Security in a Perimeter-less World
In today’s dynamic digital landscape, securing the attack surface requires a shift from traditional security models to external attack surface management. Organizations must prioritize real-time visibility to identify hidden vulnerabilities, mitigate shadow IT risks, and stay ahead of evolving cyber threats.
By proactively monitoring and managing their attack surface, businesses can strengthen their security posture, ensure compliance, and safeguard their critical assets. The key to a secure future is not just protection but also continuous vigilance.
Are you ready to take control of your attack surface? Start by implementing a comprehensive external attack surface management solution today.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



