Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


Functions of an External Threat Intelligence Framework
Functions of an External Threat Intelligence Framework
The world of technology is witnessing fast-paced evolution in the last few decades. The transition from traditional software systems to cloud services has granted industries more flexibility, accessibility, and scalability.
Read Time
7 min read
Posted On
Mar 13, 2025
Social Media
The world of technology is witnessing fast-paced evolution in the last few decades. The transition from traditional software systems to cloud services has granted industries more flexibility, accessibility, and scalability. However, this hyperconnected modern digital system introduces a substantial number of endpoints and vulnerabilities, intensifying the threat of cyber-attacks across the globe. Organizations must focus on proactive threat detection to protect themselves against external threats that originate beyond their immediate network perimeter. External threat intelligence tools provide critical insights into potential attack vectors, emerging threats, and adversary tactics. Building a comprehensive external threat intelligence framework is essential for enhancing cybersecurity posture, mitigating risks, and responding effectively to cyber incidents.
In this article, we will break down the key components of an external threat intelligence framework, including data sources, analytics, and continuous monitoring to provide comprehensive security support to your business.
What is External Threat Intelligence Framework?
External threat intelligence is the process of cybersecurity that involves collecting, analyzing, and leveraging information about cyber threats that originate outside an organization. This intelligence helps security teams detect, prevent, and respond to potential attacks before they cause significant damage. Collected from a multitude of data sources, the intelligence tends to be detailed and specific to the business requirements. External Threat Intelligence frameworks also allow businesses to get malicious threat data originating from the deep and dark web, enriching the security effort.
Difference Between Internal and External Threat Intelligence
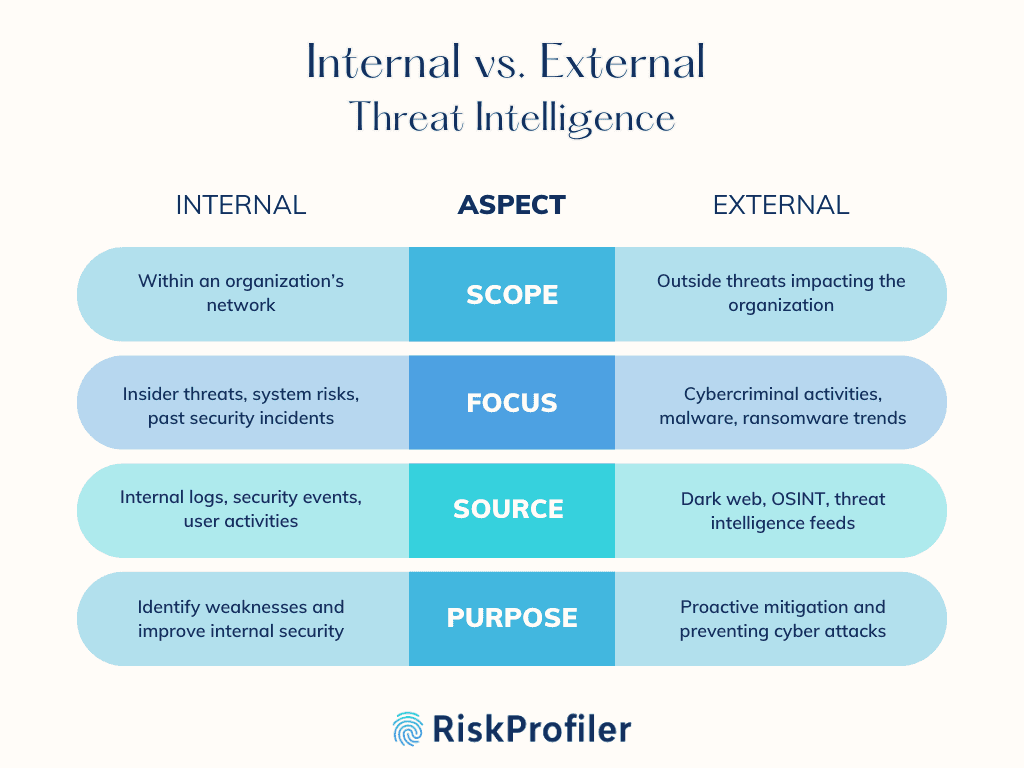
Internal threat intelligence gathers threat data within an organization’s network, including insider threats, system vulnerabilities, and past security incidents. It helps identify weaknesses and improve defenses based on internal data. External threat intelligence, on the other hand, focuses on outside threats, such as cybercriminal activities, emerging malware, and attack trends across industries. It provides insights into potential vulnerabilities before they impact the organization, enabling proactive threat mitigation and strengthening overall cybersecurity posture against evolving external threats.
Benefits of an External Threat Intelligence Framework
Integrating an efficient external threat intelligence framework with your system allows you to protect your system from unknown threats and pre-existing system vulnerabilities. The key benefits of an external threat intelligence framework are:
ETI framework with AI-assisted monitoring capabilities stays vigilant across your system attack surface, aiding you in gathering real-time threat intelligence.
The continuous visibility also allows you to track and record malicious traffic activity or emerging threats with swiftness, allowing you to prepare your system to tackle the attacks.
Continuous threat exposure management aided by external threat intelligence frameworks also helps with attack path analysis, which helps your team detect and mitigate potential risks and vulnerable access paths in your system to prevent risk exposures.
It also helps you reduce the attack surface by fortifying all endpoints while streamlining mitigating strategies with automated workflows.
Key Components of an External Threat Intelligence Framework
Several essential components come together to build an efficient external threat intelligence framework. The process involves data collection from different individual sources, analyzing the information to extract the essential datasets, and data contextualization to build a well-defined mitigation process. In this section, we will discuss the key elements of an external threat intelligence framework.
A. Data Sources: Collecting Actionable Intelligence
ETI frameworks use multiple sources to gather substantial data that can be used to predict or identify possible cyber attacks. These data sources include open-source databases, peer-sourced and commercial intelligence, dark web forums and marketplaces, social media applications, etc. The wide range of data collected from these sources allows the ETI system to extract the essential information through a detailed analysis process. The top sources of external threat intelligence frameworks are:
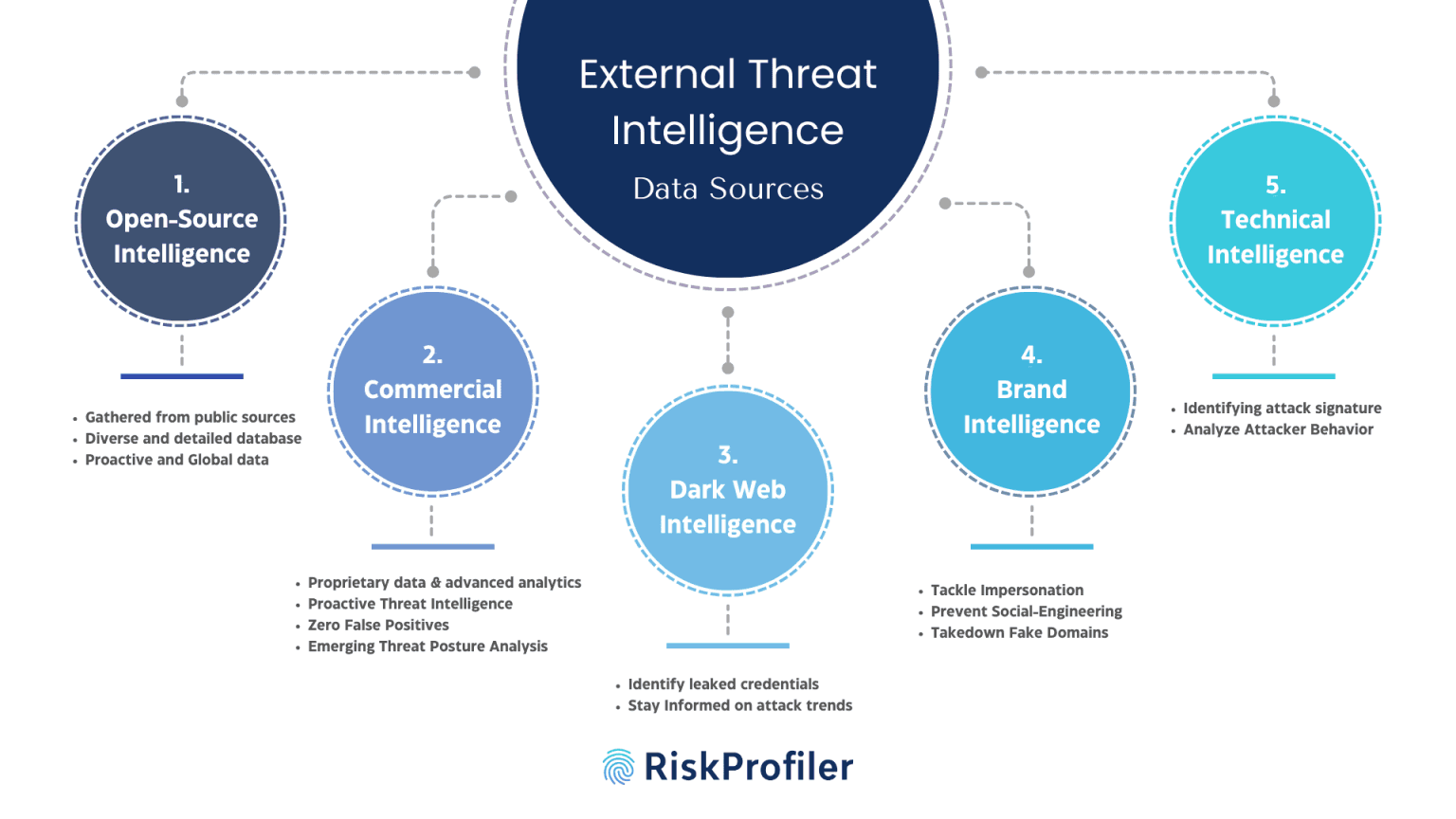
Threat Feeds & Open-Source Intelligence (OSINT)
Open-Source Intelligence (OSINT) is an essential element of an external threat intelligence framework. OSINT tools gather publicly available information from accessible sources such as security blogs, online forums, and government advisories, helping organizations stay informed about the latest cyber threats and vulnerabilities.
Strengths of Open-Source Intelligence or OSINT:
Open-source intelligence is collected from public data sources, making the process cost-effective while allowing visibility to a wider range of databases.
Open-source intelligence or OSINT gathers actionable insights from diverse, global sources, curating a wider and more detailed database for accurate reference.
Due to its diverse and specific reach, OSINT allows organizations to benefit from enhanced threat intelligence and real-time threat detection.
Limitations of Open-Source Intelligence or OSINT:
The large open-source database can be overwhelming due to information overload.
As OSINT collects information from public databases, it requires strict data validation to differentiate credible sources from misinformation.
Information collected via OSINT is mostly time-sensitive, as data can quickly become outdated.
Commercial Intelligence Providers
While OSINT is valuable, it is not completely reliable. The potential inaccuracy of OSINT creates the need for organizations to often invest in paid threat intelligence services to access high-quality, curated threat information specific to their business. Commercial intelligence providers offer real-time insights, expert analysis, and proprietary data to help organizations bolster their security posture.
Why organizations choose commercial intelligence:
Access to proprietary data and advanced analytics.
Timely and actionable insights with reduced false positives.
Expert analysis of evolving threats.
Dark Web Monitoring
The dark and deep web are the hidden parts of the internet where cybercriminals sell stolen data, trade malicious software, and coordinate attacks. Dark web intelligence involves monitoring dark web marketplaces, private messaging platforms, and forums to gather intelligence specific to an organization’s interests. It helps businesses detect the leaked information, find sources, and prepare contingency plans to prevent cyber attacks and data loss.
Importance of Dark Web Intelligence:
It helps security teams identify leaked credentials, exposed sensitive data, and insider threats on time to prevent financial losses and legal proceedings.
Dark Web Intelligence can get information on planned attacks, the sale of sensitive data, system breaches, and other emerging threat attacks.
Dark and Deep Web intelligence is also used to track emerging cybercriminal trends and tactics to stay ahead of malicious attacks.
Tools & Methods for Dark Web Intelligence Gathering:
Web crawlers and scraping tools for dark web forums.
Automated threat intelligence platforms like RiskProfiler monitor activities in deep and dark web forums.
Human analysts engaging in dark web reconnaissance.
Social Media & Brand Monitoring
Social media has become the primary tool for businesses to expand market reach, tap into the target audience base, and improve brand awareness. However, social media platforms are frequently targeted by malicious entities for orchestrating phishing attacks, scams, malicious campaigns, and brand impersonation. In some cases, impersonators also use duplicitous or typosquat domains, fake logos, and other copyrighted information to deceive the target audience or collect user data. Thus, organizations must actively monitor social platforms, domains, and subdomains with efficient brand intelligence services to protect their reputation and prevent malicious actors from deceiving customers and employees.
How adversaries use social media:
Fake profiles impersonating executives for business email compromise (BEC) attacks.
Social engineering tactics to deceive employees or customers.
Fake advertisements and phishing campaigns run by impersonators.
Utilizing AI tools to create deep-fake videos and audio to manipulate customers and employees.
Using typosquat sites, fake domains, and logos to collect customer information.
Threat Intelligence Monitoring Tools:
AI-powered brand threat intelligence solutions like RiskProfiler.
Social listening tools that detect fraudulent accounts and impersonations.
Incident response platforms that automate accounts and domain takedown requests.
Technical Intelligence Sources
The modern business environment is highly reliant on technical tools and software, creating many access points for the exploiters. Technical intelligence identifies cyber threats based on tangible indicators such as malicious IP addresses, misconfigured APIs, file hashes, and attacker techniques. This intelligence helps security teams detect and mitigate threats before they impact the organization.
Key elements:
Indicators of Compromise (IoCs): Technical intelligence uses IoCs to detect malicious DNS, IP addresses, domains, subdomains. APIs, and file hashes linked to cyber threats.
Threat actor Tactics, Techniques, and Procedures (TTPs): Security experts also utilize crucial insights from MITRE ATT&CK that map out attacker behaviors to determine the preventive measures and fortify the security system.
B. Analysis: Extracting Meaningful Insights from Data
As organizations or security tools derive constructive intelligence, they require detailed analysis to extract crucial information. Data analysis also allows the security team to elaborate on the threat contexts, and website traffic history, and detect the source of the vulnerabilities with detailed historical data and timelines.
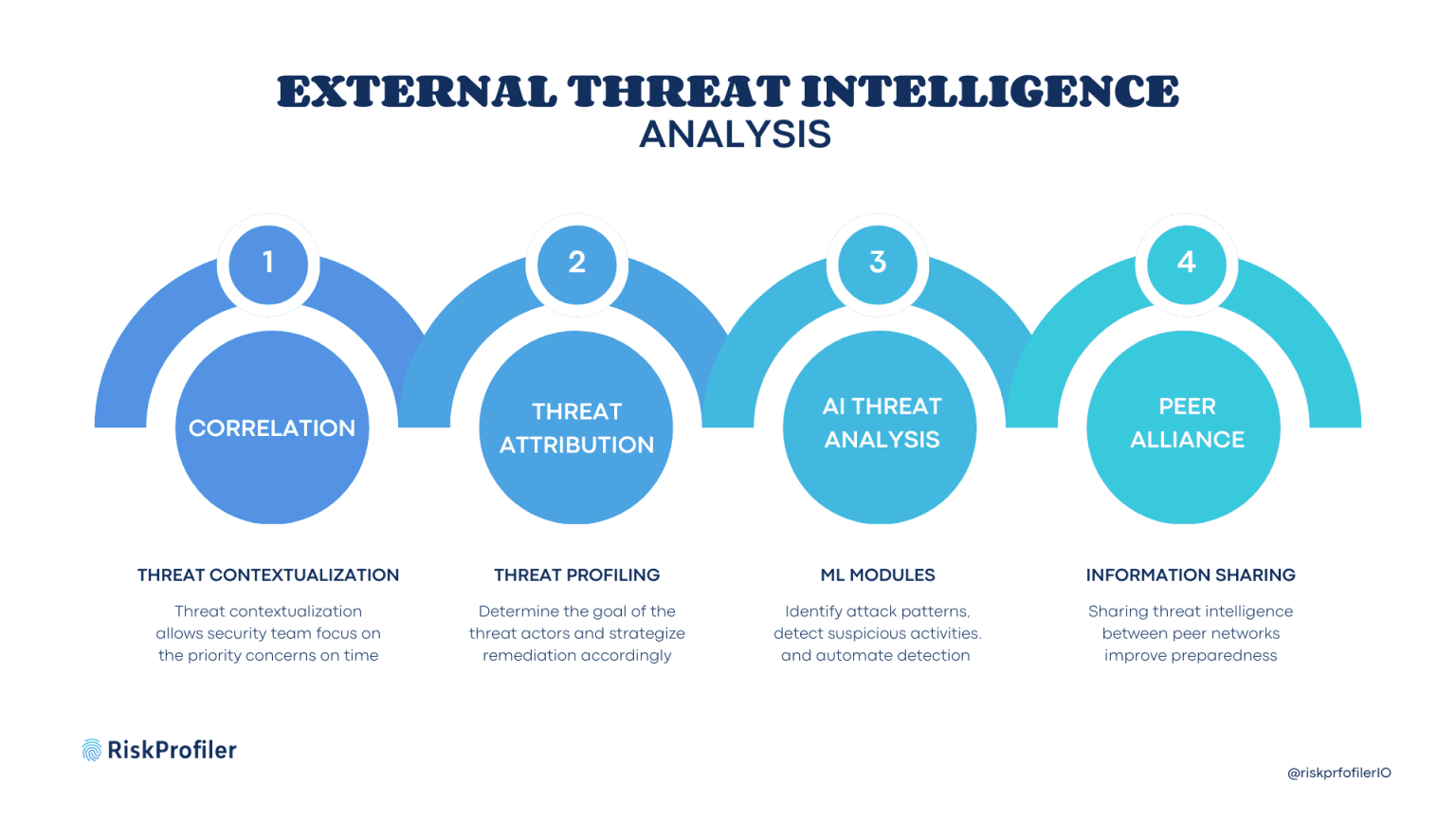
Correlation & Contextualization
Threat intelligence data must be analyzed in context to separate real threats from irrelevant background noise. This requires the use of analytical techniques to correlate threat indicators with existing security data. It allows the experts to view the threat intelligence to determine the characteristics, origins, and timeline of the specific threats.
Methods for Threat Contextualization:
Threat intelligence platforms (TIPs) aggregate and analyze data across multiple sources.
Cross-referencing intelligence with internal security logs.
Automated correlation using AI-driven analytics.
Threat Attribution & Profiling
Attributing cyberattacks to specific threat actors helps organizations understand their adversaries’ motives and strategies. By profiling attackers, security teams can predict future threats and develop appropriate defense mechanisms.
Key considerations in attribution:
Identifying APT groups, ransomware gangs, and cybercriminal networks.
Analyzing past incidents to predict future behaviors.
Using geopolitical intelligence to assess state-sponsored threats.
Machine Learning & AI in Threat Analysis
Artificial Intelligence (AI) and Machine Learning (ML) are transforming the way organizations process large volumes of threat data. These technologies can identify patterns, detect anomalies, and automate threat detection, reducing the burden on human analysts.
Role of AI in intelligence analysis:
Identifying anomalies in large datasets.
Automating threat detection and response workflows.
Limitations of AI:
Struggles with novel attack methods outside of training data.
Prone to generating false positives without human validation.
Peer Collaboration & Information Sharing
Threat intelligence is most effective when organizations collaborate and share information. Public and private sector partnerships can help detect and mitigate cyber threats on a larger scale.
Key initiatives:
ISACs (Information Sharing and Analysis Centers): Industry-specific intelligence sharing groups.
Public-private partnerships: Collaboration with law enforcement and security agencies to counter cyber threats.
C. Continuous Monitoring & Operationalization
ETI tools incorporate AI modules into their workflows to continuously monitor the external attack surface. It provides with real-time data on system vulnerabilities, data losses, suspicious traffic activity, or other malicious actions across the network to identify potential threats proactively.
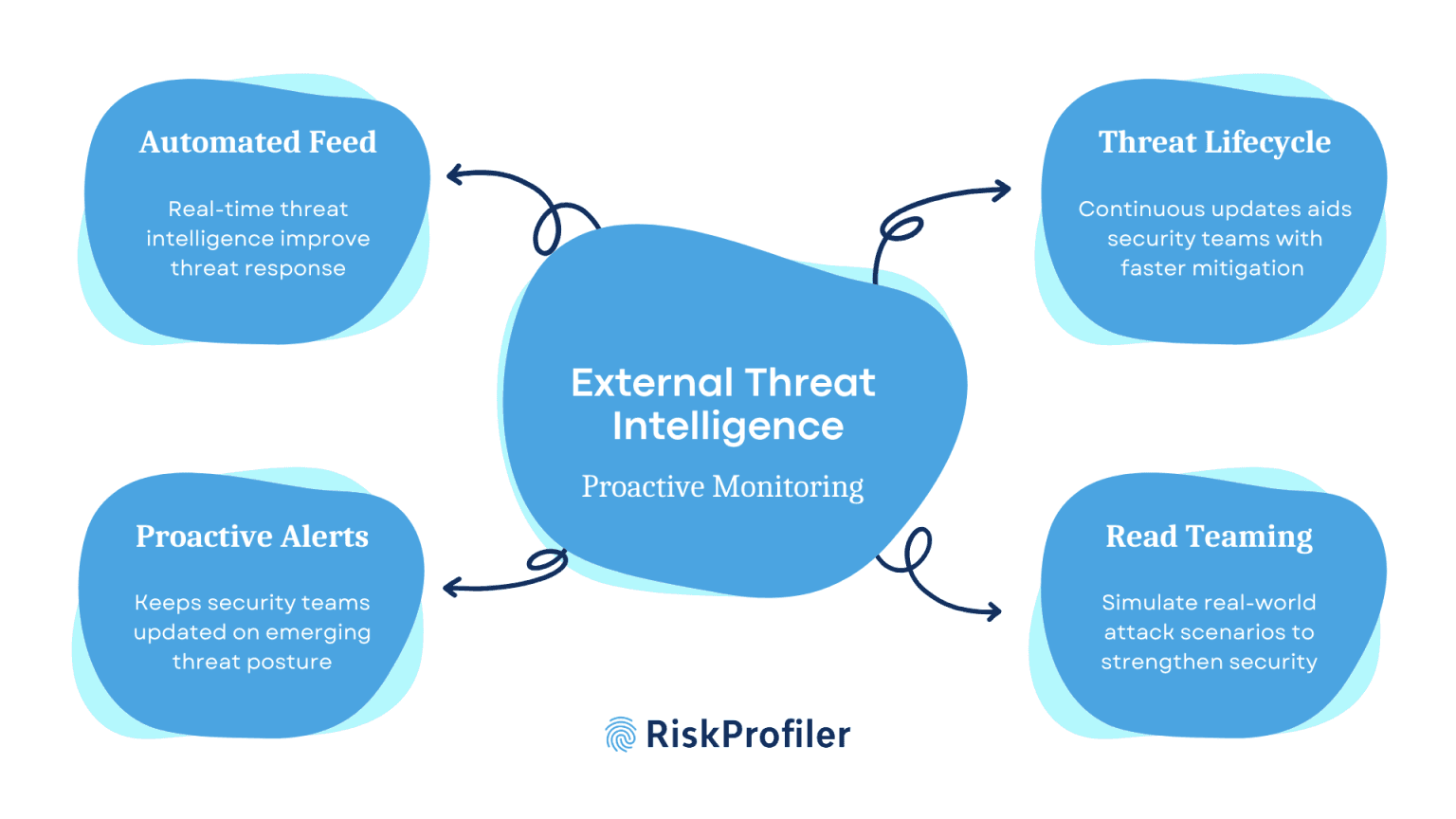
Automated Threat Intelligence Feeds
Organizations need a real-time intelligence framework to respond swiftly to cyber threats. Automated threat feeds allow security teams to integrate external intelligence directly into their security infrastructure for immediate action. It allows the teams to stay updated on the threat posture and take the right course of action on time.
However, like all elements, automated threat intelligence systems face some challenges:
The real-time threat information does not offer much room to edit out false positives and filter irrelevant alerts.
With continuous monitoring and mixed data streams, it can be challenging to maintain up-to-date, accurate threat intelligence feeds.
Real-time Alerting & Response
Security Operations Centers (SOC) rely on external threat intelligence frameworks to quickly detect and mitigate cyber threats. Real-time alerting helps security teams take preemptive action before threats escalate. These notification systems are tweaked to alert the account admins on the most relevant and high-priority concerns to help them focus on the significant risks with a higher potential for causing damage.
The top use cases of the ETI framework’s real-time notification systems are:
The alert system notifies the user of emerging threats on IP addresses, domains, and other endpoints in real time, helping the business proactively block these access points.
In the occasion of malicious traffic activity detection by continuous monitoring, the alert systems automatically flags and trigger immediate analysis of the suspicious network activity to secure the network from external attacks.
Threat Intelligence Lifecycle & Updates
To remain effective, an external threat intelligence framework requires continuous system monitoring instead of scheduled updates. Organizations should regularly refresh their intelligence sources and measure their effectiveness to improve their security strategy. It allows them to detect vulnerabilities and risks on time, leading to a more effective and streamlined threat mitigation process.
Best Practices for threat intelligence lifecycle updates:
Regularly refresh intelligence databases.
Conduct detailed analyses of security incidents to gather historical threat information and breach trends.
Measure intelligence effectiveness using KPIs like threat detection rates and response times.
Red Teaming & Adversary Simulation
By leveraging external threat intelligence in red teaming exercises, organizations can simulate real-world attack scenarios and assess their security posture. This proactive approach helps identify vulnerabilities before they can be exploited by real attackers.
Proactive security strategies:
Conducting penetration tests based on emerging threat actor techniques.
Using adversary emulation frameworks like MITRE CALDERA.
Enhancing blue team preparedness with intelligence-led exercises.
By leveraging a robust external threat intelligence framework, organizations can enhance their cyber resilience, stay ahead of emerging threats, and build a more proactive defense strategy.
External Threat Intelligence: Challenges
Building an effective external threat intelligence framework comes with several challenges that organizations must overcome to ensure the accuracy and usability of threat data.
Overload of Threat Data and False Positives
With the vast amount of threat intelligence available from different sources, organizations often struggle to filter out relevant insights. High volumes of false positives can overwhelm security teams, making it difficult to identify genuine threats.
Lack of Skilled Personnel for Threat Analysis
Threat intelligence requires specialized skills in data analysis, cybersecurity, and adversary tracking. Many organizations face a shortage of trained professionals who can effectively interpret and operationalize threat intelligence.
Integration Challenges with Existing Security Infrastructure
Integrating external cloud threat intelligence into existing security tools, such as SIEM, SOAR, and EDR solutions, can be complex. Compatibility issues, lack of automation, and difficulty in correlating intelligence with internal logs can limit the framework’s effectiveness.
External Threat Intelligence: Best Practices
To address these challenges, organizations should follow best practices that enhance the efficiency and reliability of their external threat intelligence framework. RiskProfiler, a trusted external cybersecurity service provider, offers proactive, AI-assisted threat intelligence that helps you secure your system from external attacks and system vulnerabilities. Implementing RiskProfiler’s External threat intelligence framework offers detailed threat information with contextualization for simpler and effective understanding.
Prioritizing Intelligence Sources Based on Industry Risk
Not all threat intelligence sources are equally relevant. Organizations should prioritize sources based on their industry-specific threats and risk exposure. It allows businesses to focus on intelligence that directly impacts their operations while improving your threat contextualization efforts.
Automating Intelligence Ingestion and Correlation
Automation plays a crucial role in reducing manual effort and improving response times. By leveraging AI-driven analytics and threat intelligence platforms, organizations can efficiently ingest, filter, and correlate intelligence, reducing noise and false positives.
Regularly Assessing and Refining the Framework
Threat intelligence is not static; adversaries constantly evolve their tactics. Organizations must regularly review and refine their intelligence framework by assessing effectiveness metrics, incorporating feedback, and updating intelligence sources to stay ahead of threats.
By addressing these challenges and following best practices, organizations can build a robust external threat intelligence framework that enhances their cybersecurity posture and enables proactive threat mitigation.
Why Choose RiskProfiler for External Attack Surface Management?
In today’s rapidly evolving digital landscape, safeguarding your organization’s external digital assets is paramount. RiskProfiler’s External Attack Surface Management (EASM) solution offers a comprehensive approach to identifying, monitoring, and securing your external-facing assets, ensuring a robust security posture. Here’s why your business should consider implementing RiskProfiler’s External Threat Intelligence Framework:
1. Comprehensive Visibility of External Assets
RiskProfiler provides a centralized and real-time inventory of all external-facing assets, including domains, subdomains, IP addresses, web applications, cloud instances, and third-party services. This ensures no asset is left vulnerable due to lack of oversight. By continuously discovering and mapping assets, businesses can reduce the risks of shadow IT, forgotten infrastructure, misconfigurations, and unauthorized applications. This holistic visibility allows organizations to take a proactive approach in managing and securing their digital footprint.
2. Proactive Vulnerability Detection
Many cyberattacks occur due to unpatched vulnerabilities, exposed credentials, or misconfigurations in externally facing systems. RiskProfiler continuously scans and assesses these assets, identifying security gaps such as outdated software, open ports, weak encryption, and publicly accessible sensitive data. With a proactive approach, organizations can remediate vulnerabilities before they are exploited by cybercriminals. Unlike traditional periodic assessments, continuous monitoring ensures emerging threats and zero-day exploits are detected in real time. This strengthens an organization’s overall security posture and significantly reduces the risk of a data breach.
3. Attack Path Analysis
RiskProfiler uses advanced analytics and attack path mapping to identify how a cybercriminal might chain vulnerabilities across different assets to penetrate a network. By visualizing how an attack might unfold and its security and financial impacts, security teams can prioritize defenses where they matter most. This intelligence helps organizations strengthen defensive layers, disrupt attack chains, and prevent lateral movement, reducing the likelihood of a successful breach.
4. Continuous Monitoring and Real-Time Alerts
Cyber threats evolve daily, making it essential for organizations to detect and respond to security risks in real time. RiskProfiler provides 24/7 monitoring and instant alerts for any newly discovered vulnerabilities, unexpected changes in an organization’s external footprint, or emerging threats targeting their industry. Instead of relying on manual security reviews, businesses receive automated risk notifications, context-driven alerts, and actionable insights that help them quickly remediate potential threats. This reduces response time, minimizes damage, and allows organizations to maintain a strong security posture.
5. Integration with Cloud Environments
The shift to cloud computing introduces new security challenges, including misconfigured storage, publicly accessible APIs, and unauthorized cloud workloads. RiskProfiler seamlessly integrates with leading cloud providers such as AWS, Azure, and Google Cloud, providing continuous visibility into cloud-hosted assets. It identifies exposed cloud services, misconfigured security groups, and compliance violations, ensuring organizations maintain strong cloud security policies. This integration eliminates blind spots in cloud environments and enables security teams to manage both traditional and cloud-based infrastructures from a single platform.
6. Automated Risk Mitigation
Manually addressing security risks can be time-consuming and inefficient, leading to delays in remediation and increased exposure to threats. RiskProfiler automates risk identification, triage, and remediation workflows, significantly reducing the burden on security teams. Leveraging AI-driven threat intelligence, pre-configured remediation playbooks, and auto-prioritization, businesses can swiftly address critical vulnerabilities without manual intervention. This ensures that security gaps are addressed faster, reducing the window of opportunity for attackers while improving incident response times and operational efficiency.
7. Asset Criticality Assessment
RiskProfiler categorizes assets based on business criticality, allowing security teams to focus on high-priority assets such as customer databases, financial systems, and core infrastructure. This risk-based approach ensures that limited resources are allocated effectively, preventing organizations from wasting time and effort on low-risk systems while leaving critical systems vulnerable. By prioritizing security actions based on business impact, organizations can reduce overall cyber risk.
8. Enhanced Compliance and Reporting
Regulatory compliance is a key concern for businesses across industries, with strict mandates such as GDPR, HIPAA, ISO 27001, NIST, and PCI-DSS requiring organizations to monitor and secure their external attack surface. RiskProfiler provides automated compliance tracking, detailed risk reports, and security audits, ensuring businesses can demonstrate compliance with regulatory requirements. The platform generates real-time security posture reports, helping organizations stay compliant, reduce the risk of fines and penalties, and strengthen board-level cybersecurity reporting.
Conclusion
A robust external threat intelligence framework empowers organizations to stay ahead of cyber adversaries. By leveraging diverse data sources, applying in-depth analysis, and maintaining continuous monitoring, security teams can proactively defend against external threats. As cyber threats continue to evolve, organizations should prioritize intelligence-driven security strategies to enhance resilience and protect critical assets.
By implementing these best practices, businesses can build a comprehensive and effective threat intelligence framework that enables proactive cybersecurity defense.
The world of technology is witnessing fast-paced evolution in the last few decades. The transition from traditional software systems to cloud services has granted industries more flexibility, accessibility, and scalability. However, this hyperconnected modern digital system introduces a substantial number of endpoints and vulnerabilities, intensifying the threat of cyber-attacks across the globe. Organizations must focus on proactive threat detection to protect themselves against external threats that originate beyond their immediate network perimeter. External threat intelligence tools provide critical insights into potential attack vectors, emerging threats, and adversary tactics. Building a comprehensive external threat intelligence framework is essential for enhancing cybersecurity posture, mitigating risks, and responding effectively to cyber incidents.
In this article, we will break down the key components of an external threat intelligence framework, including data sources, analytics, and continuous monitoring to provide comprehensive security support to your business.
What is External Threat Intelligence Framework?
External threat intelligence is the process of cybersecurity that involves collecting, analyzing, and leveraging information about cyber threats that originate outside an organization. This intelligence helps security teams detect, prevent, and respond to potential attacks before they cause significant damage. Collected from a multitude of data sources, the intelligence tends to be detailed and specific to the business requirements. External Threat Intelligence frameworks also allow businesses to get malicious threat data originating from the deep and dark web, enriching the security effort.
Difference Between Internal and External Threat Intelligence

Internal threat intelligence gathers threat data within an organization’s network, including insider threats, system vulnerabilities, and past security incidents. It helps identify weaknesses and improve defenses based on internal data. External threat intelligence, on the other hand, focuses on outside threats, such as cybercriminal activities, emerging malware, and attack trends across industries. It provides insights into potential vulnerabilities before they impact the organization, enabling proactive threat mitigation and strengthening overall cybersecurity posture against evolving external threats.
Benefits of an External Threat Intelligence Framework
Integrating an efficient external threat intelligence framework with your system allows you to protect your system from unknown threats and pre-existing system vulnerabilities. The key benefits of an external threat intelligence framework are:
ETI framework with AI-assisted monitoring capabilities stays vigilant across your system attack surface, aiding you in gathering real-time threat intelligence.
The continuous visibility also allows you to track and record malicious traffic activity or emerging threats with swiftness, allowing you to prepare your system to tackle the attacks.
Continuous threat exposure management aided by external threat intelligence frameworks also helps with attack path analysis, which helps your team detect and mitigate potential risks and vulnerable access paths in your system to prevent risk exposures.
It also helps you reduce the attack surface by fortifying all endpoints while streamlining mitigating strategies with automated workflows.
Key Components of an External Threat Intelligence Framework
Several essential components come together to build an efficient external threat intelligence framework. The process involves data collection from different individual sources, analyzing the information to extract the essential datasets, and data contextualization to build a well-defined mitigation process. In this section, we will discuss the key elements of an external threat intelligence framework.
A. Data Sources: Collecting Actionable Intelligence
ETI frameworks use multiple sources to gather substantial data that can be used to predict or identify possible cyber attacks. These data sources include open-source databases, peer-sourced and commercial intelligence, dark web forums and marketplaces, social media applications, etc. The wide range of data collected from these sources allows the ETI system to extract the essential information through a detailed analysis process. The top sources of external threat intelligence frameworks are:

Threat Feeds & Open-Source Intelligence (OSINT)
Open-Source Intelligence (OSINT) is an essential element of an external threat intelligence framework. OSINT tools gather publicly available information from accessible sources such as security blogs, online forums, and government advisories, helping organizations stay informed about the latest cyber threats and vulnerabilities.
Strengths of Open-Source Intelligence or OSINT:
Open-source intelligence is collected from public data sources, making the process cost-effective while allowing visibility to a wider range of databases.
Open-source intelligence or OSINT gathers actionable insights from diverse, global sources, curating a wider and more detailed database for accurate reference.
Due to its diverse and specific reach, OSINT allows organizations to benefit from enhanced threat intelligence and real-time threat detection.
Limitations of Open-Source Intelligence or OSINT:
The large open-source database can be overwhelming due to information overload.
As OSINT collects information from public databases, it requires strict data validation to differentiate credible sources from misinformation.
Information collected via OSINT is mostly time-sensitive, as data can quickly become outdated.
Commercial Intelligence Providers
While OSINT is valuable, it is not completely reliable. The potential inaccuracy of OSINT creates the need for organizations to often invest in paid threat intelligence services to access high-quality, curated threat information specific to their business. Commercial intelligence providers offer real-time insights, expert analysis, and proprietary data to help organizations bolster their security posture.
Why organizations choose commercial intelligence:
Access to proprietary data and advanced analytics.
Timely and actionable insights with reduced false positives.
Expert analysis of evolving threats.
Dark Web Monitoring
The dark and deep web are the hidden parts of the internet where cybercriminals sell stolen data, trade malicious software, and coordinate attacks. Dark web intelligence involves monitoring dark web marketplaces, private messaging platforms, and forums to gather intelligence specific to an organization’s interests. It helps businesses detect the leaked information, find sources, and prepare contingency plans to prevent cyber attacks and data loss.
Importance of Dark Web Intelligence:
It helps security teams identify leaked credentials, exposed sensitive data, and insider threats on time to prevent financial losses and legal proceedings.
Dark Web Intelligence can get information on planned attacks, the sale of sensitive data, system breaches, and other emerging threat attacks.
Dark and Deep Web intelligence is also used to track emerging cybercriminal trends and tactics to stay ahead of malicious attacks.
Tools & Methods for Dark Web Intelligence Gathering:
Web crawlers and scraping tools for dark web forums.
Automated threat intelligence platforms like RiskProfiler monitor activities in deep and dark web forums.
Human analysts engaging in dark web reconnaissance.
Social Media & Brand Monitoring
Social media has become the primary tool for businesses to expand market reach, tap into the target audience base, and improve brand awareness. However, social media platforms are frequently targeted by malicious entities for orchestrating phishing attacks, scams, malicious campaigns, and brand impersonation. In some cases, impersonators also use duplicitous or typosquat domains, fake logos, and other copyrighted information to deceive the target audience or collect user data. Thus, organizations must actively monitor social platforms, domains, and subdomains with efficient brand intelligence services to protect their reputation and prevent malicious actors from deceiving customers and employees.
How adversaries use social media:
Fake profiles impersonating executives for business email compromise (BEC) attacks.
Social engineering tactics to deceive employees or customers.
Fake advertisements and phishing campaigns run by impersonators.
Utilizing AI tools to create deep-fake videos and audio to manipulate customers and employees.
Using typosquat sites, fake domains, and logos to collect customer information.
Threat Intelligence Monitoring Tools:
AI-powered brand threat intelligence solutions like RiskProfiler.
Social listening tools that detect fraudulent accounts and impersonations.
Incident response platforms that automate accounts and domain takedown requests.
Technical Intelligence Sources
The modern business environment is highly reliant on technical tools and software, creating many access points for the exploiters. Technical intelligence identifies cyber threats based on tangible indicators such as malicious IP addresses, misconfigured APIs, file hashes, and attacker techniques. This intelligence helps security teams detect and mitigate threats before they impact the organization.
Key elements:
Indicators of Compromise (IoCs): Technical intelligence uses IoCs to detect malicious DNS, IP addresses, domains, subdomains. APIs, and file hashes linked to cyber threats.
Threat actor Tactics, Techniques, and Procedures (TTPs): Security experts also utilize crucial insights from MITRE ATT&CK that map out attacker behaviors to determine the preventive measures and fortify the security system.
B. Analysis: Extracting Meaningful Insights from Data
As organizations or security tools derive constructive intelligence, they require detailed analysis to extract crucial information. Data analysis also allows the security team to elaborate on the threat contexts, and website traffic history, and detect the source of the vulnerabilities with detailed historical data and timelines.

Correlation & Contextualization
Threat intelligence data must be analyzed in context to separate real threats from irrelevant background noise. This requires the use of analytical techniques to correlate threat indicators with existing security data. It allows the experts to view the threat intelligence to determine the characteristics, origins, and timeline of the specific threats.
Methods for Threat Contextualization:
Threat intelligence platforms (TIPs) aggregate and analyze data across multiple sources.
Cross-referencing intelligence with internal security logs.
Automated correlation using AI-driven analytics.
Threat Attribution & Profiling
Attributing cyberattacks to specific threat actors helps organizations understand their adversaries’ motives and strategies. By profiling attackers, security teams can predict future threats and develop appropriate defense mechanisms.
Key considerations in attribution:
Identifying APT groups, ransomware gangs, and cybercriminal networks.
Analyzing past incidents to predict future behaviors.
Using geopolitical intelligence to assess state-sponsored threats.
Machine Learning & AI in Threat Analysis
Artificial Intelligence (AI) and Machine Learning (ML) are transforming the way organizations process large volumes of threat data. These technologies can identify patterns, detect anomalies, and automate threat detection, reducing the burden on human analysts.
Role of AI in intelligence analysis:
Identifying anomalies in large datasets.
Automating threat detection and response workflows.
Limitations of AI:
Struggles with novel attack methods outside of training data.
Prone to generating false positives without human validation.
Peer Collaboration & Information Sharing
Threat intelligence is most effective when organizations collaborate and share information. Public and private sector partnerships can help detect and mitigate cyber threats on a larger scale.
Key initiatives:
ISACs (Information Sharing and Analysis Centers): Industry-specific intelligence sharing groups.
Public-private partnerships: Collaboration with law enforcement and security agencies to counter cyber threats.
C. Continuous Monitoring & Operationalization
ETI tools incorporate AI modules into their workflows to continuously monitor the external attack surface. It provides with real-time data on system vulnerabilities, data losses, suspicious traffic activity, or other malicious actions across the network to identify potential threats proactively.

Automated Threat Intelligence Feeds
Organizations need a real-time intelligence framework to respond swiftly to cyber threats. Automated threat feeds allow security teams to integrate external intelligence directly into their security infrastructure for immediate action. It allows the teams to stay updated on the threat posture and take the right course of action on time.
However, like all elements, automated threat intelligence systems face some challenges:
The real-time threat information does not offer much room to edit out false positives and filter irrelevant alerts.
With continuous monitoring and mixed data streams, it can be challenging to maintain up-to-date, accurate threat intelligence feeds.
Real-time Alerting & Response
Security Operations Centers (SOC) rely on external threat intelligence frameworks to quickly detect and mitigate cyber threats. Real-time alerting helps security teams take preemptive action before threats escalate. These notification systems are tweaked to alert the account admins on the most relevant and high-priority concerns to help them focus on the significant risks with a higher potential for causing damage.
The top use cases of the ETI framework’s real-time notification systems are:
The alert system notifies the user of emerging threats on IP addresses, domains, and other endpoints in real time, helping the business proactively block these access points.
In the occasion of malicious traffic activity detection by continuous monitoring, the alert systems automatically flags and trigger immediate analysis of the suspicious network activity to secure the network from external attacks.
Threat Intelligence Lifecycle & Updates
To remain effective, an external threat intelligence framework requires continuous system monitoring instead of scheduled updates. Organizations should regularly refresh their intelligence sources and measure their effectiveness to improve their security strategy. It allows them to detect vulnerabilities and risks on time, leading to a more effective and streamlined threat mitigation process.
Best Practices for threat intelligence lifecycle updates:
Regularly refresh intelligence databases.
Conduct detailed analyses of security incidents to gather historical threat information and breach trends.
Measure intelligence effectiveness using KPIs like threat detection rates and response times.
Red Teaming & Adversary Simulation
By leveraging external threat intelligence in red teaming exercises, organizations can simulate real-world attack scenarios and assess their security posture. This proactive approach helps identify vulnerabilities before they can be exploited by real attackers.
Proactive security strategies:
Conducting penetration tests based on emerging threat actor techniques.
Using adversary emulation frameworks like MITRE CALDERA.
Enhancing blue team preparedness with intelligence-led exercises.
By leveraging a robust external threat intelligence framework, organizations can enhance their cyber resilience, stay ahead of emerging threats, and build a more proactive defense strategy.
External Threat Intelligence: Challenges
Building an effective external threat intelligence framework comes with several challenges that organizations must overcome to ensure the accuracy and usability of threat data.
Overload of Threat Data and False Positives
With the vast amount of threat intelligence available from different sources, organizations often struggle to filter out relevant insights. High volumes of false positives can overwhelm security teams, making it difficult to identify genuine threats.
Lack of Skilled Personnel for Threat Analysis
Threat intelligence requires specialized skills in data analysis, cybersecurity, and adversary tracking. Many organizations face a shortage of trained professionals who can effectively interpret and operationalize threat intelligence.
Integration Challenges with Existing Security Infrastructure
Integrating external cloud threat intelligence into existing security tools, such as SIEM, SOAR, and EDR solutions, can be complex. Compatibility issues, lack of automation, and difficulty in correlating intelligence with internal logs can limit the framework’s effectiveness.
External Threat Intelligence: Best Practices
To address these challenges, organizations should follow best practices that enhance the efficiency and reliability of their external threat intelligence framework. RiskProfiler, a trusted external cybersecurity service provider, offers proactive, AI-assisted threat intelligence that helps you secure your system from external attacks and system vulnerabilities. Implementing RiskProfiler’s External threat intelligence framework offers detailed threat information with contextualization for simpler and effective understanding.
Prioritizing Intelligence Sources Based on Industry Risk
Not all threat intelligence sources are equally relevant. Organizations should prioritize sources based on their industry-specific threats and risk exposure. It allows businesses to focus on intelligence that directly impacts their operations while improving your threat contextualization efforts.
Automating Intelligence Ingestion and Correlation
Automation plays a crucial role in reducing manual effort and improving response times. By leveraging AI-driven analytics and threat intelligence platforms, organizations can efficiently ingest, filter, and correlate intelligence, reducing noise and false positives.
Regularly Assessing and Refining the Framework
Threat intelligence is not static; adversaries constantly evolve their tactics. Organizations must regularly review and refine their intelligence framework by assessing effectiveness metrics, incorporating feedback, and updating intelligence sources to stay ahead of threats.
By addressing these challenges and following best practices, organizations can build a robust external threat intelligence framework that enhances their cybersecurity posture and enables proactive threat mitigation.
Why Choose RiskProfiler for External Attack Surface Management?
In today’s rapidly evolving digital landscape, safeguarding your organization’s external digital assets is paramount. RiskProfiler’s External Attack Surface Management (EASM) solution offers a comprehensive approach to identifying, monitoring, and securing your external-facing assets, ensuring a robust security posture. Here’s why your business should consider implementing RiskProfiler’s External Threat Intelligence Framework:
1. Comprehensive Visibility of External Assets
RiskProfiler provides a centralized and real-time inventory of all external-facing assets, including domains, subdomains, IP addresses, web applications, cloud instances, and third-party services. This ensures no asset is left vulnerable due to lack of oversight. By continuously discovering and mapping assets, businesses can reduce the risks of shadow IT, forgotten infrastructure, misconfigurations, and unauthorized applications. This holistic visibility allows organizations to take a proactive approach in managing and securing their digital footprint.
2. Proactive Vulnerability Detection
Many cyberattacks occur due to unpatched vulnerabilities, exposed credentials, or misconfigurations in externally facing systems. RiskProfiler continuously scans and assesses these assets, identifying security gaps such as outdated software, open ports, weak encryption, and publicly accessible sensitive data. With a proactive approach, organizations can remediate vulnerabilities before they are exploited by cybercriminals. Unlike traditional periodic assessments, continuous monitoring ensures emerging threats and zero-day exploits are detected in real time. This strengthens an organization’s overall security posture and significantly reduces the risk of a data breach.
3. Attack Path Analysis
RiskProfiler uses advanced analytics and attack path mapping to identify how a cybercriminal might chain vulnerabilities across different assets to penetrate a network. By visualizing how an attack might unfold and its security and financial impacts, security teams can prioritize defenses where they matter most. This intelligence helps organizations strengthen defensive layers, disrupt attack chains, and prevent lateral movement, reducing the likelihood of a successful breach.
4. Continuous Monitoring and Real-Time Alerts
Cyber threats evolve daily, making it essential for organizations to detect and respond to security risks in real time. RiskProfiler provides 24/7 monitoring and instant alerts for any newly discovered vulnerabilities, unexpected changes in an organization’s external footprint, or emerging threats targeting their industry. Instead of relying on manual security reviews, businesses receive automated risk notifications, context-driven alerts, and actionable insights that help them quickly remediate potential threats. This reduces response time, minimizes damage, and allows organizations to maintain a strong security posture.
5. Integration with Cloud Environments
The shift to cloud computing introduces new security challenges, including misconfigured storage, publicly accessible APIs, and unauthorized cloud workloads. RiskProfiler seamlessly integrates with leading cloud providers such as AWS, Azure, and Google Cloud, providing continuous visibility into cloud-hosted assets. It identifies exposed cloud services, misconfigured security groups, and compliance violations, ensuring organizations maintain strong cloud security policies. This integration eliminates blind spots in cloud environments and enables security teams to manage both traditional and cloud-based infrastructures from a single platform.
6. Automated Risk Mitigation
Manually addressing security risks can be time-consuming and inefficient, leading to delays in remediation and increased exposure to threats. RiskProfiler automates risk identification, triage, and remediation workflows, significantly reducing the burden on security teams. Leveraging AI-driven threat intelligence, pre-configured remediation playbooks, and auto-prioritization, businesses can swiftly address critical vulnerabilities without manual intervention. This ensures that security gaps are addressed faster, reducing the window of opportunity for attackers while improving incident response times and operational efficiency.
7. Asset Criticality Assessment
RiskProfiler categorizes assets based on business criticality, allowing security teams to focus on high-priority assets such as customer databases, financial systems, and core infrastructure. This risk-based approach ensures that limited resources are allocated effectively, preventing organizations from wasting time and effort on low-risk systems while leaving critical systems vulnerable. By prioritizing security actions based on business impact, organizations can reduce overall cyber risk.
8. Enhanced Compliance and Reporting
Regulatory compliance is a key concern for businesses across industries, with strict mandates such as GDPR, HIPAA, ISO 27001, NIST, and PCI-DSS requiring organizations to monitor and secure their external attack surface. RiskProfiler provides automated compliance tracking, detailed risk reports, and security audits, ensuring businesses can demonstrate compliance with regulatory requirements. The platform generates real-time security posture reports, helping organizations stay compliant, reduce the risk of fines and penalties, and strengthen board-level cybersecurity reporting.
Conclusion
A robust external threat intelligence framework empowers organizations to stay ahead of cyber adversaries. By leveraging diverse data sources, applying in-depth analysis, and maintaining continuous monitoring, security teams can proactively defend against external threats. As cyber threats continue to evolve, organizations should prioritize intelligence-driven security strategies to enhance resilience and protect critical assets.
By implementing these best practices, businesses can build a comprehensive and effective threat intelligence framework that enables proactive cybersecurity defense.
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



