Recognized in

®

™ Voice of the Customer 2025 for Brand Protection and External Attack Surface Management


What is Cyber Threat Intelligence?
What is Cyber Threat Intelligence?
In today’s decentralized digital world of cloud systems, Kubernetes, and open-source programs, cyber threats are becoming increasingly sophisticated, making it crucial for organizations to stay ahead of potential attacks.
Read Time
7 min read
Posted On
Mar 19, 2025
Social Media
In today’s decentralized digital world of cloud systems, Kubernetes, and open-source programs, cyber threats are becoming increasingly sophisticated, making it crucial for organizations to stay ahead of potential attacks. In order to offer security advantages to complicated network systems, Cyber Threat Intelligence (CTI) is a powerful tool to anticipate, identify, and mitigate threats before they cause damage. Digital threat intelligence, collected from different sources, enriches the collected data and helps businesses get a broader idea about their security posture and safeguard their network from diverse cyber threats.
Understanding key CTI terms is essential for security teams, decision-makers, and IT professionals who want to safeguard their businesses effectively. Additionally, external threat intelligence, brand threat intelligence, and dark web intelligence are critical components that enhance an organization’s overall security posture. This blog serves as a comprehensive guide to decoding the essential terminology in cyber threat intelligence.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) refers to the collection, analysis, and application of information related to potential cyber threats and attacks. It empowers organizations to make informed security decisions by identifying adversary tactics, techniques, and procedures (TTPs).
Key Components of Cyber Threat Intelligence:
Cyber threat intelligence (CTI) consists of several components to gather detailed information on a business’s security posture, attack probability, and vulnerabilities. Understanding the key components of cyber threat intelligence is essential for effective cybersecurity. These elements help organizations detect, analyze, and respond to threats, ensuring proactive defense against evolving cyber risks and attacks.
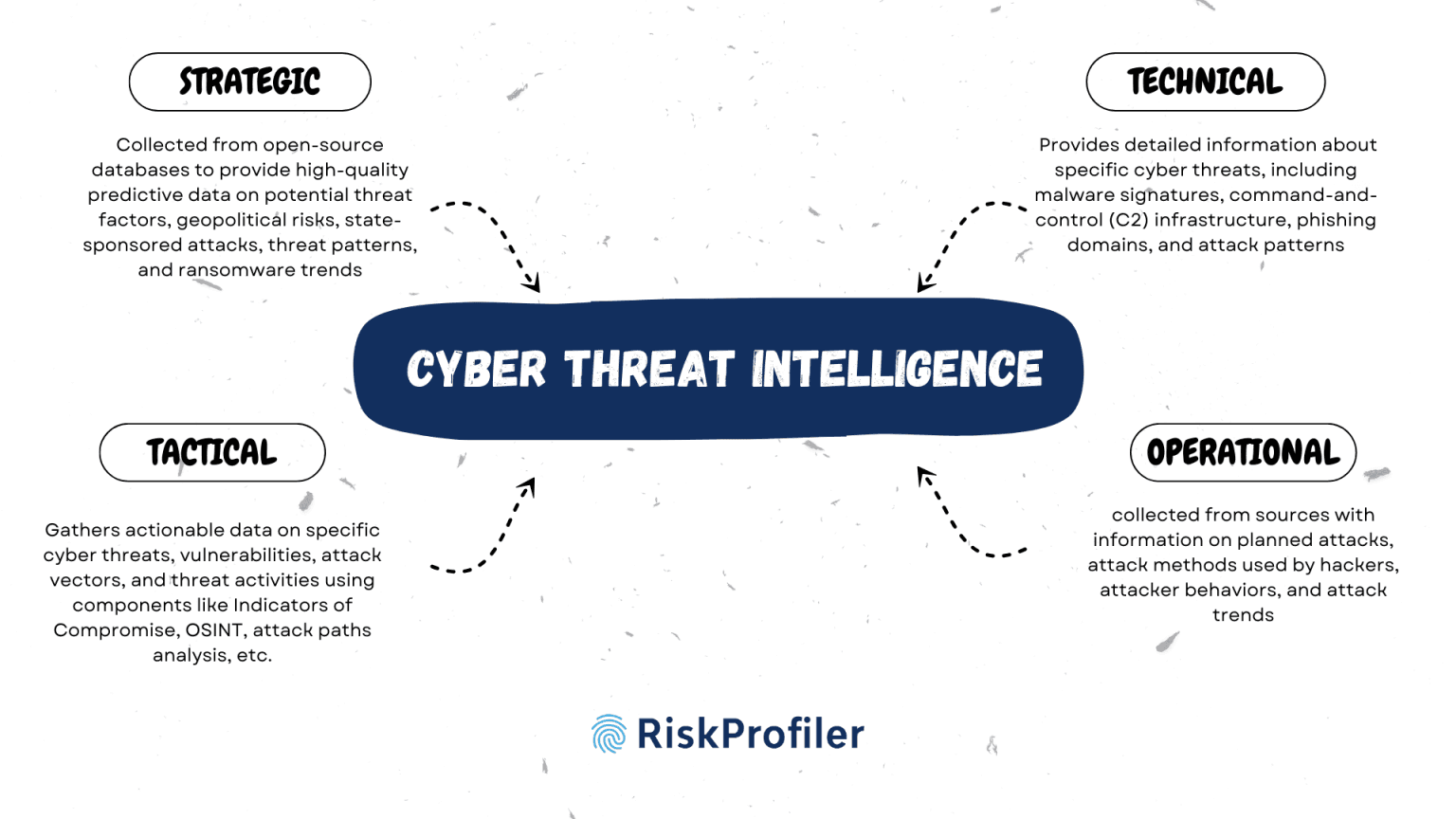
Strategic Intelligence
Strategic intelligence is the sophisticated cyber threat intelligence collected from open-source databases to provide high-quality predictive data on potential threat factors, geopolitical risks, state-sponsored attacks, threat patterns, and ransomware trends. This proactive threat information allows organizations to prepare informed security decisions and align their security strategies based on industry-specific security trends. The strategic intelligence is specifically helpful in protecting a business’s interest and financial security and creating policies that enhance long-term resilience against cyber threats.
Tactical Intelligence
Utilizing specific cyber threat intelligence components like Indicators of Compromise, OSINT, attack paths analysis, etc., tactical intelligence gathers actionable data on specific cyber threats, vulnerabilities, attack vectors, and threat activities. The real-time insights into these specific threat activities allow businesses to improve their security posture, resolve system vulnerabilities, and prepare mitigation strategies in advance to prevent breaches, data loss, and other threat impacts.
Operational Intelligence
Operational intelligence is collected from sources with information on planned attacks, attack methods used by hackers, attacker behaviors, and attack trends. This proactive intelligence allows businesses to improve their defense mechanism and threat response strategies.
Technical Intelligence
Technical intelligence provides detailed information about specific cyber threats, including malware signatures, command-and-control (C2) infrastructure, phishing domains, and attack patterns. It helps security teams detect and block threats by offering indicators of compromise (IoCs) and forensic data. This intelligence is crucial for implementing security measures like firewalls, intrusion detection, and threat hunting.
By leveraging Cyber Threat Intelligence, organizations can enhance their cybersecurity defenses, proactively mitigate risks, and improve incident response times.
Essential Cyber Threat Intelligence Terms: A Glossary
Your organization and tech team will be required to familiarize themselves with a few key cyber threat intelligence terms and concepts. This glossary provides clear definitions of essential cybersecurity terms, helping professionals and organizations navigate the complex landscape of threat detection, analysis, and defense strategies.
What are Indicators of Compromise?
Indicators of Compromise or IoC refers to a set of threat markers like hidden system vulnerabilities, suspicious traffic activity, malware signature, etc., used to identify potential security threats. Security teams utilize Indicators of Compromise to monitor, detect, and analyze security risks,
What are Tactics, Techniques, and Procedures?
Tactics, Techniques, and Procedures (TTPs) in cyber threat intelligence describe how cyber adversaries operate.
Tactics refer to the overall goals of an attack, such as data theft or system disruption.
Techniques describe how attackers achieve their goals, like phishing or malware deployment.
Procedures provide specific details on how a technique is executed, including the tools and steps used.
Understanding TTPs helps security teams anticipate, detect, and defend against cyber threats more effectively.
What are the Cyber Threat Actors?
Threat actors in cyber threat intelligence are individuals or groups responsible for cyberattacks. They vary in motives, skills, and targets. Common types include:
Cybercriminals – These are financially motivated attackers who use tactics like ransomware, phishing, and data breaches to steal money, personal data, or valuable business information. They often operate in organized groups and target individuals, businesses, and financial institutions.
Nation-State Actors – Backed by governments, these highly skilled attackers engage in cyber espionage, sabotage, and information warfare. Their goals include political, economic, and military advantages, often targeting critical infrastructure, government agencies, and corporations.
Hacktivists – These threat actors carry out cyberattacks to promote political, social, or ideological causes. They use tactics like website defacements, data leaks, and denial-of-service (DoS) attacks to disrupt organizations or governments they oppose.
Insider Threats – Employees, contractors, or business partners who misuse their access to steal data, sabotage systems, or unintentionally cause security breaches. Insiders can be motivated by financial gain, revenge, coercion, or negligence.
Script Kiddies – Inexperienced individuals who use pre-built hacking tools and scripts without deep technical knowledge. They often launch attacks for fun, recognition, or minor financial gains, but their actions can still cause significant damage.
Understanding these threat actors helps organizations assess risks and develop better cybersecurity strategies to protect their assets.
What is Threat Feed?
Threat feeds are continuously updated streams of data that provide real-time information about emerging cyber threats, vulnerabilities, and malicious activities. They help security teams stay ahead of potential attacks by supplying intelligence on indicators of compromise (IoCs), threat actors, attack methods, and suspicious domains or IP addresses.
What is Threat Hunting?
Threat hunting is a proactive cybersecurity practice where security analysts actively search for hidden threats or malicious activities within an organization’s network before they cause harm. Unlike traditional security measures that rely on automated alerts, threat hunting involves manually investigating suspicious patterns, anomalies, and adversary tactics that may bypass standard defenses. Threat hunters analyze how attackers operate, using frameworks like MITRE ATT&CK to understand adversary behavior.
What is External Threat Intelligence?
External Threat Intelligence allows businesses to uncover hidden threats in their external network. This Cyber threat intelligence method focuses on identifying cybercriminal activity, vulnerabilities, and attack campaigns that can impact the business’s security. By leveraging external threat intelligence and attack surface management, businesses can proactively defend against cyber threats before they materialize.
Benefits of External Threat Intelligence:
External threat intelligence frameworks allow businesses to collect detailed information on their threat and security posture in real-time.
The ETI modules help the security team identify emerging cyber threats before they infiltrate an organization.
External attack surface management provides deeper insights into attacker motives, capabilities, and targets.
The detailed and contextualized information enhances security strategies by offering real-time threat monitoring.
Use Cases of External Threat Intelligence:
Identifying vulnerabilities that cybercriminals might exploit.
Monitoring system traffic to detect suspicious traffic activity.
Detecting misconfiguration, shadow IT assets, malicious IP addresses, etc. for effective risk management.
What is Brand Threat Intelligence?
Brand Threat Intelligence involves monitoring and protecting an organization’s brand identity from cybercriminals who attempt to impersonate or misuse it. Brand protection is critical in today’s digital world, where cybercriminals exploit trusted brands, their creatives, and other copyrighted creatives to deceive unsuspecting victims.
Benefits of Brand Threat Intelligence:
Detects unauthorized use of brand assets, including business logos, creatives, or copyrighted assets.
Safeguard your C-suite executives and other key personnel against impersonation attacks via fake domains and social media accounts that target employees and customers.
It helps take down fraudulent and typosquatted websites that damage brand reputation.
Use Cases of Brand Threat Intelligence:
Monitoring for domain spoofing to prevent phishing attacks.
Identifying counterfeit websites selling fake products under a brand’s name.
Securing executive and employee identities from social engineering attacks.
What is Dark Web Intelligence?
Dark Web Intelligence involves monitoring hidden cybercriminal forums and marketplaces for leaked corporate data, stolen credentials, or planned cyberattacks. Incorporating dark web intelligence with security practices allows businesses to stay informed about cyber threats emerging from underground networks.
Benefits of Dark Web Intelligence:
Detects exposed credentials and sensitive data leaks.
Identifies discussions about upcoming cyberattacks.
Provides insights into underground cybercrime activities.
Use Cases of Dark Web Intelligence:
Tracking stolen employee credentials to prevent unauthorized access.
Monitoring dark web marketplaces for corporate data leaks.
Detecting cybercriminal activities targeting an organization.
Implementing Cyber Threat Intelligence: Best Practices
To maximize the value of Cyber Threat Intelligence (CTI), organizations should integrate it into their security operations strategically. It can help them strengthen their cybersecurity posture, mitigate risks proactively, and improve their overall threat detection and response capabilities. Some of the best cyber threat intelligence practices are listed below.
Adopt a Proactive Security Approach
Rather than reacting to incidents after they occur, organizations should anticipate threats using real-time intelligence. By continuously monitoring attack trends, vulnerabilities, and adversary tactics, businesses can implement preemptive security measures, reducing the risk of breaches and minimizing damage before an attack escalates.
Leverage Multiple Intelligence Sources
A single intelligence source is not enough to combat evolving cyber threats. Organizations should integrate external threat intelligence (monitoring global threats), brand threat intelligence (protecting against impersonation and fraud), and dark web intelligence (detecting stolen data and planned attacks) to gain a holistic security perspective and proactively address potential risks.
Utilize AI & Automation
With the massive volume of cyber threat data generated daily, AI-driven analytics and machine learning algorithms enhance threat detection, pattern recognition, and response times. Automation streamlines intelligence processing, enabling security teams to quickly identify anomalies, prioritize threats, and reduce manual workload for more efficient cybersecurity operations.
Implement Threat Intelligence Sharing
Collaboration strengthens cyber defense. Businesses should share threat intelligence with industry peers, ISACs (Information Sharing and Analysis Centers), law enforcement, and government agencies to collectively detect and counteract emerging threats. Sharing intelligence enhances situational awareness, allowing organizations to defend against cyber adversaries more effectively.
Continuously Update Threat Feeds
Cyber threats evolve rapidly, making outdated intelligence ineffective. Organizations should ensure their threat feeds are continuously refreshed with real-time updates on new malware strains, attack tactics, emerging vulnerabilities, and compromised IPs or domains to stay ahead of adversaries and prevent security gaps in their defenses.
Integrate CTI with Security Tools
Cyber Threat Intelligence should be embedded into Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), and endpoint detection systems to enhance automated threat detection, streamline response actions, and improve security workflows. Integrated intelligence allows security teams to react faster and more efficiently to cyber threats.
Train Security Teams on Cyber Threat Intelligence Utilization
Cyber threat intelligence is only effective when security teams know how to interpret and apply it. Regular training ensures security analysts, IT professionals, and decision-makers understand how to analyze threat reports, use threat indicators, implement risk mitigation strategies, and respond to cyber incidents proactively, strengthening the organization’s overall security posture.
Future Trends in Cyber Threat Intelligence
Artificial intelligence and machine learning have witnessed tremendous progress in the last few years as tools like ChatGPT, Gemini, DeepSeek, etc. emerge as key players in the tech industry. With the evolving nature of the overall threat landscape, the cybersecurity sector has also incorporated AI modules into its workflows for improved efficiency, scalability, and productivity. The inclusion of AI and LLM tools in cyber threat intelligence, however, opens the way for exciting future trends and possibilities.
AI and machine learning tools will be integrated with most, if not all, cybersecurity solutions for faster, error-free, and cost-efficient cyber risk detection and remediation efforts.
Integration of AI and automation techniques with advanced dark web monitoring tools that provide deeper insights into cybercriminal activities across dark web marketplaces, forums, and illegal communication channels.
Cyber Threat Intelligence can also be used with security orchestration, automation, and response (SOAR) systems to enhance efficiency.
Using automation and AI technology, organizations can collect Real-time threat intelligence across different sources and enable data sharing among industries to enhance collective defense.
Final Words
Understanding Cyber Threat Intelligence (CTI) and its essential terminology is crucial for any organization looking to strengthen its cybersecurity defenses. By leveraging external threat intelligence, brand threat intelligence, and dark web intelligence, businesses can proactively identify and mitigate cyber risks before they cause harm.
As cyber threats become more sophisticated, staying informed and adopting a strategic approach to threat intelligence will be the key to protecting digital assets, brand reputation, and sensitive data.
Why Choose RiskProfiler as your External Cyber Threat Intelligence Partner?
RiskProfiler stands out as a premier external cyber threat intelligence tool, offering a suite of features designed to safeguard organizations against evolving cyber threats. Integrating RiskProfiler’s external cyber threat intelligence platform with your business will help you continuously monitor your external attack surface and detect threats as they emerge.
Comprehensive External Attack Surface Management
RiskProfiler’s External Attack Surface Management (EASM) provides organizations with a holistic view of their digital footprint. By continuously monitoring and identifying vulnerabilities across internet-facing assets, it enables proactive risk mitigation, ensuring that potential attack vectors are addressed before they can be exploited.
Cloud Security Enhancement
In today’s cloud-centric environment, securing cloud infrastructures is paramount. RiskProfiler’s Cloud External Attack Surface Management offers real-time visibility into publicly exposed cloud assets. It detects misconfigurations and unauthorized exposures, allowing organizations to strengthen their cloud security posture effectively.
Robust Third-Party Risk Management
Understanding that an organization’s security is intertwined with its vendors, RiskProfiler’s Third-Party Risk Management solution continuously assesses the cybersecurity posture of third-party vendors. Implementing AI-assisted automated vendor risk analysis and continuous monitoring, it helps organizations identify and mitigate risks originating from their supply chain, thereby reducing potential vulnerabilities.
Advanced Brand Intelligence
Protecting brand reputation is crucial in the digital age. RiskProfiler’s Brand Intelligence employs proactive monitoring of both surface and dark web platforms to detect unauthorized use of brand assets, counterfeit activities, and potential phishing domains. This early detection mechanism enables swift action to protect brand integrity and maintain customer trust.
Is your organization leveraging threat intelligence effectively? Start integrating RiskProfiler’s Cyber Threat Intelligence today and take a proactive stance against cyber threats!
Secure your organization from cybercriminals. Book a demo now!
In today’s decentralized digital world of cloud systems, Kubernetes, and open-source programs, cyber threats are becoming increasingly sophisticated, making it crucial for organizations to stay ahead of potential attacks. In order to offer security advantages to complicated network systems, Cyber Threat Intelligence (CTI) is a powerful tool to anticipate, identify, and mitigate threats before they cause damage. Digital threat intelligence, collected from different sources, enriches the collected data and helps businesses get a broader idea about their security posture and safeguard their network from diverse cyber threats.
Understanding key CTI terms is essential for security teams, decision-makers, and IT professionals who want to safeguard their businesses effectively. Additionally, external threat intelligence, brand threat intelligence, and dark web intelligence are critical components that enhance an organization’s overall security posture. This blog serves as a comprehensive guide to decoding the essential terminology in cyber threat intelligence.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) refers to the collection, analysis, and application of information related to potential cyber threats and attacks. It empowers organizations to make informed security decisions by identifying adversary tactics, techniques, and procedures (TTPs).
Key Components of Cyber Threat Intelligence:
Cyber threat intelligence (CTI) consists of several components to gather detailed information on a business’s security posture, attack probability, and vulnerabilities. Understanding the key components of cyber threat intelligence is essential for effective cybersecurity. These elements help organizations detect, analyze, and respond to threats, ensuring proactive defense against evolving cyber risks and attacks.

Strategic Intelligence
Strategic intelligence is the sophisticated cyber threat intelligence collected from open-source databases to provide high-quality predictive data on potential threat factors, geopolitical risks, state-sponsored attacks, threat patterns, and ransomware trends. This proactive threat information allows organizations to prepare informed security decisions and align their security strategies based on industry-specific security trends. The strategic intelligence is specifically helpful in protecting a business’s interest and financial security and creating policies that enhance long-term resilience against cyber threats.
Tactical Intelligence
Utilizing specific cyber threat intelligence components like Indicators of Compromise, OSINT, attack paths analysis, etc., tactical intelligence gathers actionable data on specific cyber threats, vulnerabilities, attack vectors, and threat activities. The real-time insights into these specific threat activities allow businesses to improve their security posture, resolve system vulnerabilities, and prepare mitigation strategies in advance to prevent breaches, data loss, and other threat impacts.
Operational Intelligence
Operational intelligence is collected from sources with information on planned attacks, attack methods used by hackers, attacker behaviors, and attack trends. This proactive intelligence allows businesses to improve their defense mechanism and threat response strategies.
Technical Intelligence
Technical intelligence provides detailed information about specific cyber threats, including malware signatures, command-and-control (C2) infrastructure, phishing domains, and attack patterns. It helps security teams detect and block threats by offering indicators of compromise (IoCs) and forensic data. This intelligence is crucial for implementing security measures like firewalls, intrusion detection, and threat hunting.
By leveraging Cyber Threat Intelligence, organizations can enhance their cybersecurity defenses, proactively mitigate risks, and improve incident response times.
Essential Cyber Threat Intelligence Terms: A Glossary
Your organization and tech team will be required to familiarize themselves with a few key cyber threat intelligence terms and concepts. This glossary provides clear definitions of essential cybersecurity terms, helping professionals and organizations navigate the complex landscape of threat detection, analysis, and defense strategies.
What are Indicators of Compromise?
Indicators of Compromise or IoC refers to a set of threat markers like hidden system vulnerabilities, suspicious traffic activity, malware signature, etc., used to identify potential security threats. Security teams utilize Indicators of Compromise to monitor, detect, and analyze security risks,
What are Tactics, Techniques, and Procedures?
Tactics, Techniques, and Procedures (TTPs) in cyber threat intelligence describe how cyber adversaries operate.
Tactics refer to the overall goals of an attack, such as data theft or system disruption.
Techniques describe how attackers achieve their goals, like phishing or malware deployment.
Procedures provide specific details on how a technique is executed, including the tools and steps used.
Understanding TTPs helps security teams anticipate, detect, and defend against cyber threats more effectively.
What are the Cyber Threat Actors?
Threat actors in cyber threat intelligence are individuals or groups responsible for cyberattacks. They vary in motives, skills, and targets. Common types include:
Cybercriminals – These are financially motivated attackers who use tactics like ransomware, phishing, and data breaches to steal money, personal data, or valuable business information. They often operate in organized groups and target individuals, businesses, and financial institutions.
Nation-State Actors – Backed by governments, these highly skilled attackers engage in cyber espionage, sabotage, and information warfare. Their goals include political, economic, and military advantages, often targeting critical infrastructure, government agencies, and corporations.
Hacktivists – These threat actors carry out cyberattacks to promote political, social, or ideological causes. They use tactics like website defacements, data leaks, and denial-of-service (DoS) attacks to disrupt organizations or governments they oppose.
Insider Threats – Employees, contractors, or business partners who misuse their access to steal data, sabotage systems, or unintentionally cause security breaches. Insiders can be motivated by financial gain, revenge, coercion, or negligence.
Script Kiddies – Inexperienced individuals who use pre-built hacking tools and scripts without deep technical knowledge. They often launch attacks for fun, recognition, or minor financial gains, but their actions can still cause significant damage.
Understanding these threat actors helps organizations assess risks and develop better cybersecurity strategies to protect their assets.
What is Threat Feed?
Threat feeds are continuously updated streams of data that provide real-time information about emerging cyber threats, vulnerabilities, and malicious activities. They help security teams stay ahead of potential attacks by supplying intelligence on indicators of compromise (IoCs), threat actors, attack methods, and suspicious domains or IP addresses.
What is Threat Hunting?
Threat hunting is a proactive cybersecurity practice where security analysts actively search for hidden threats or malicious activities within an organization’s network before they cause harm. Unlike traditional security measures that rely on automated alerts, threat hunting involves manually investigating suspicious patterns, anomalies, and adversary tactics that may bypass standard defenses. Threat hunters analyze how attackers operate, using frameworks like MITRE ATT&CK to understand adversary behavior.
What is External Threat Intelligence?
External Threat Intelligence allows businesses to uncover hidden threats in their external network. This Cyber threat intelligence method focuses on identifying cybercriminal activity, vulnerabilities, and attack campaigns that can impact the business’s security. By leveraging external threat intelligence and attack surface management, businesses can proactively defend against cyber threats before they materialize.
Benefits of External Threat Intelligence:
External threat intelligence frameworks allow businesses to collect detailed information on their threat and security posture in real-time.
The ETI modules help the security team identify emerging cyber threats before they infiltrate an organization.
External attack surface management provides deeper insights into attacker motives, capabilities, and targets.
The detailed and contextualized information enhances security strategies by offering real-time threat monitoring.
Use Cases of External Threat Intelligence:
Identifying vulnerabilities that cybercriminals might exploit.
Monitoring system traffic to detect suspicious traffic activity.
Detecting misconfiguration, shadow IT assets, malicious IP addresses, etc. for effective risk management.
What is Brand Threat Intelligence?
Brand Threat Intelligence involves monitoring and protecting an organization’s brand identity from cybercriminals who attempt to impersonate or misuse it. Brand protection is critical in today’s digital world, where cybercriminals exploit trusted brands, their creatives, and other copyrighted creatives to deceive unsuspecting victims.
Benefits of Brand Threat Intelligence:
Detects unauthorized use of brand assets, including business logos, creatives, or copyrighted assets.
Safeguard your C-suite executives and other key personnel against impersonation attacks via fake domains and social media accounts that target employees and customers.
It helps take down fraudulent and typosquatted websites that damage brand reputation.
Use Cases of Brand Threat Intelligence:
Monitoring for domain spoofing to prevent phishing attacks.
Identifying counterfeit websites selling fake products under a brand’s name.
Securing executive and employee identities from social engineering attacks.
What is Dark Web Intelligence?
Dark Web Intelligence involves monitoring hidden cybercriminal forums and marketplaces for leaked corporate data, stolen credentials, or planned cyberattacks. Incorporating dark web intelligence with security practices allows businesses to stay informed about cyber threats emerging from underground networks.
Benefits of Dark Web Intelligence:
Detects exposed credentials and sensitive data leaks.
Identifies discussions about upcoming cyberattacks.
Provides insights into underground cybercrime activities.
Use Cases of Dark Web Intelligence:
Tracking stolen employee credentials to prevent unauthorized access.
Monitoring dark web marketplaces for corporate data leaks.
Detecting cybercriminal activities targeting an organization.
Implementing Cyber Threat Intelligence: Best Practices
To maximize the value of Cyber Threat Intelligence (CTI), organizations should integrate it into their security operations strategically. It can help them strengthen their cybersecurity posture, mitigate risks proactively, and improve their overall threat detection and response capabilities. Some of the best cyber threat intelligence practices are listed below.
Adopt a Proactive Security Approach
Rather than reacting to incidents after they occur, organizations should anticipate threats using real-time intelligence. By continuously monitoring attack trends, vulnerabilities, and adversary tactics, businesses can implement preemptive security measures, reducing the risk of breaches and minimizing damage before an attack escalates.
Leverage Multiple Intelligence Sources
A single intelligence source is not enough to combat evolving cyber threats. Organizations should integrate external threat intelligence (monitoring global threats), brand threat intelligence (protecting against impersonation and fraud), and dark web intelligence (detecting stolen data and planned attacks) to gain a holistic security perspective and proactively address potential risks.
Utilize AI & Automation
With the massive volume of cyber threat data generated daily, AI-driven analytics and machine learning algorithms enhance threat detection, pattern recognition, and response times. Automation streamlines intelligence processing, enabling security teams to quickly identify anomalies, prioritize threats, and reduce manual workload for more efficient cybersecurity operations.
Implement Threat Intelligence Sharing
Collaboration strengthens cyber defense. Businesses should share threat intelligence with industry peers, ISACs (Information Sharing and Analysis Centers), law enforcement, and government agencies to collectively detect and counteract emerging threats. Sharing intelligence enhances situational awareness, allowing organizations to defend against cyber adversaries more effectively.
Continuously Update Threat Feeds
Cyber threats evolve rapidly, making outdated intelligence ineffective. Organizations should ensure their threat feeds are continuously refreshed with real-time updates on new malware strains, attack tactics, emerging vulnerabilities, and compromised IPs or domains to stay ahead of adversaries and prevent security gaps in their defenses.
Integrate CTI with Security Tools
Cyber Threat Intelligence should be embedded into Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), and endpoint detection systems to enhance automated threat detection, streamline response actions, and improve security workflows. Integrated intelligence allows security teams to react faster and more efficiently to cyber threats.
Train Security Teams on Cyber Threat Intelligence Utilization
Cyber threat intelligence is only effective when security teams know how to interpret and apply it. Regular training ensures security analysts, IT professionals, and decision-makers understand how to analyze threat reports, use threat indicators, implement risk mitigation strategies, and respond to cyber incidents proactively, strengthening the organization’s overall security posture.
Future Trends in Cyber Threat Intelligence
Artificial intelligence and machine learning have witnessed tremendous progress in the last few years as tools like ChatGPT, Gemini, DeepSeek, etc. emerge as key players in the tech industry. With the evolving nature of the overall threat landscape, the cybersecurity sector has also incorporated AI modules into its workflows for improved efficiency, scalability, and productivity. The inclusion of AI and LLM tools in cyber threat intelligence, however, opens the way for exciting future trends and possibilities.
AI and machine learning tools will be integrated with most, if not all, cybersecurity solutions for faster, error-free, and cost-efficient cyber risk detection and remediation efforts.
Integration of AI and automation techniques with advanced dark web monitoring tools that provide deeper insights into cybercriminal activities across dark web marketplaces, forums, and illegal communication channels.
Cyber Threat Intelligence can also be used with security orchestration, automation, and response (SOAR) systems to enhance efficiency.
Using automation and AI technology, organizations can collect Real-time threat intelligence across different sources and enable data sharing among industries to enhance collective defense.
Final Words
Understanding Cyber Threat Intelligence (CTI) and its essential terminology is crucial for any organization looking to strengthen its cybersecurity defenses. By leveraging external threat intelligence, brand threat intelligence, and dark web intelligence, businesses can proactively identify and mitigate cyber risks before they cause harm.
As cyber threats become more sophisticated, staying informed and adopting a strategic approach to threat intelligence will be the key to protecting digital assets, brand reputation, and sensitive data.
Why Choose RiskProfiler as your External Cyber Threat Intelligence Partner?
RiskProfiler stands out as a premier external cyber threat intelligence tool, offering a suite of features designed to safeguard organizations against evolving cyber threats. Integrating RiskProfiler’s external cyber threat intelligence platform with your business will help you continuously monitor your external attack surface and detect threats as they emerge.
Comprehensive External Attack Surface Management
RiskProfiler’s External Attack Surface Management (EASM) provides organizations with a holistic view of their digital footprint. By continuously monitoring and identifying vulnerabilities across internet-facing assets, it enables proactive risk mitigation, ensuring that potential attack vectors are addressed before they can be exploited.
Cloud Security Enhancement
In today’s cloud-centric environment, securing cloud infrastructures is paramount. RiskProfiler’s Cloud External Attack Surface Management offers real-time visibility into publicly exposed cloud assets. It detects misconfigurations and unauthorized exposures, allowing organizations to strengthen their cloud security posture effectively.
Robust Third-Party Risk Management
Understanding that an organization’s security is intertwined with its vendors, RiskProfiler’s Third-Party Risk Management solution continuously assesses the cybersecurity posture of third-party vendors. Implementing AI-assisted automated vendor risk analysis and continuous monitoring, it helps organizations identify and mitigate risks originating from their supply chain, thereby reducing potential vulnerabilities.
Advanced Brand Intelligence
Protecting brand reputation is crucial in the digital age. RiskProfiler’s Brand Intelligence employs proactive monitoring of both surface and dark web platforms to detect unauthorized use of brand assets, counterfeit activities, and potential phishing domains. This early detection mechanism enables swift action to protect brand integrity and maintain customer trust.
Is your organization leveraging threat intelligence effectively? Start integrating RiskProfiler’s Cyber Threat Intelligence today and take a proactive stance against cyber threats!
Secure your organization from cybercriminals. Book a demo now!
Jump to
Share Article
Share Article
Explore Our
Latest Insights
Stay informed with expert perspectives on cybersecurity, attack surface management,
and building digital resilience.
Enterprise-Grade Security & Trust
Specialized intelligence agents working together toprotect your organization
Ready to Transform
Your Threat Management?
Join hundreds of security teams who trust KnyX to cut through the noise and focus on what matters most.
Book a Demo Today

KnyX Agentic AI transforms external threat intelligence into actionable insights, helping security teams focus on what matters most.
Subscribe to our Newsletter
By submitting your email address, you agree to receive RiskProfiler’s monthly newsletter. For more information, please read our privacy policy. You can always withdraw your consent.
Solutions










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved










© 2026 RiskProfiler | All Rights Reserved



